Abstract
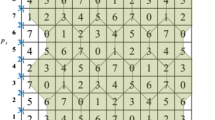
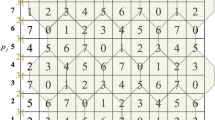
This paper proposes a novel visual secret sharing scheme based on a turtle shell structure matrix (TSSM) with reversibility and lightweight authentication. With the assistance of TSSM, the secret data is embedded into the original cover image and three meaningful shadow images are generated. To increase the image quality of the generated shadows, the proposed scheme designs an embedding structure that will be used to embed a secret image into shadows based on the TSSM, rather than by directly embedding authentication codes. The designed embedding structure offers a robust authentication capability at the cost of lightweight computation. Moreover, the hidden secret data can be extracted completely and the cover image can be restored losslessly through the collaboration of the three received shadows. Experimental results, on various grayscale test images, confirmed that our proposed scheme provides high visual quality and excellent authentication.













Similar content being viewed by others
References
Bender W, Gruhl D, Morimoto N, Lu A (1996) Techniques for data hiding. IBM Syst J 35(3&4):313–336
Blakley GR (1979) Safeguarding cryptographic keys. In: Proceedings of American Federation of Information Processing Societies National Computer Conference, New York, USA, vol,48, pp 313–317
Chan CK, Cheng LM (2004) Hiding data in images by simple LSB substitution. In:. Pattern Recogn 37(3):474–496
Chang CC, Chen TS, Chung LZ (2002) A steganographic method based upon JPEG and quantization table modification. In: Inf. SCI 141(1&2):123–138
Chang CC, Chan CS, Fan YH (2006) Image hiding scheme with modulus function and dynamic programming. In:. Pattern Recogn 39(5):1155–1167
Chang CC, Chou YC, Kieu TD (2008) An information hiding scheme using sudoku. In: Proc. Third Int. Conf. Innovative Computing, Information and Control, Dalian, China, 2008. pp 17–22
Chang CC, Hsieh YP, Lin CH (2008) Sharing secrets in stego images with authentication. Pattern Recogn 41(10):3130–3137
Chang CC, Lin PY, Wang ZH, Li MC (2010) A sudoku-based secret image sharing scheme with reversibility. In:. J Commun 5(1):5–12
Chang CC, Liu YJ, Nguyen TS (2014) A novel turtle shell based scheme for data hiding. In: Proc. Tenth Int. Conf. Intelligent Information Hiding and Multimedia Signal Processing (IIHMSP ‘14), Kitakyushu, Japan, 27–29, pp 89–93
Chang CC, Chen YH, Chuang LY (2014) Meaningful shadows for image secret sharing with steganography and authentication techniques. In:. Journal of Information Hiding and Multimedia Signal Processing 5(3):342–352
Chang CC, Liu Y, Wu HL (2016) Distortion-free secret image sharing method with two meaningful shadows. In:. IET Image Process 10(8):590–597
Cimato S, Prisco RDE, Santis ADE (2005) Probabilistic visual cryptography schemes. In:. Comput J 49(1):97–107
Cimato S, Prisco RDE, Santis ADE (2006) Probabilistic visual cryptography schemes. In:. Comput J 49(1):97–107
Hsu CT, Wu JL (1999) Hidden digital watermarks in images. In:. IEEE Transactions of Image Processing 8(1):58–68
Kundur D, Hatzinakos D (1999) Digital watermarking for telltale tamper proofing and authentication. In:. Proc IEEE 87(7):1167–1180
Lin ET, Delp EJ (1999) A review of fragile image watermarks. In: Multimedia and Security Workshop in ACM Multimedia, 99, Orlando
Lin C, Tsai W (2004) Secret image sharing with steganography and authentication. In:. The Journal of Systems and Software 73(3):405–414
Liu YJ, Chang CC (2018) A turtle shell-based visual secret sharing scheme with reversibility and authentication. In: Multimedia Tools and Applications 1–16
Noar N, Shamir A (1995) Visual cryptography. In: Proceedings of Eurocrypt '94, Perugia. 905, pp 1–12
Qin C, Chang CC, Hsu TJ (2015) Reversible data hiding scheme based on exploiting modification direction with two steganographic images. In:. Multimed Tools Appl 74(15):5861–5872
Shamir A (1979) How to share a secret. In:. Commun ACM 22(11):612–613
Shyu SJ (2006) Efficient visual secret sharing scheme for color images. In:. Pattern Recogn 39(5):866–880
Stinson DR (1999) Visual cryptography and threshold schemes. In:. IEEE Potentials 18(1):13–16
Thien CC, Lin JC (2003) An image-sharing method with user-friendly shadow images. In:. IEEE Trans on Circuits and Systems for Video Technology 13(12):1161–1169
Thien CC, Lin JC (2003) A simple and high-hiding capacity method for hiding digit-by-digit data in images based on modulus function. In:. Pattern Recogn 36(12):2875–2881
Wu XT, Sun W (2013) Generalized random grid and its applications in visual cryptography. In:. IEEE Transactions on Information Forensics and Security 8(9):1541–1553
Wu DC, Tsai WH (2003) A steganographic method for images by pixel-value differencing. In:. Pattern Recognition Lett 24(9&10):1613–1626
Yang CN (2004) New visual secret sharing schemes using probabilistic method. In:. Pattern Recogn Lett 25(4):481–494
Yang CN, Chen TS (2005) Aspect ratio invariant visual secret sharing schemes with minimum pixel expansion. In:. Pattern Recogn 26(2):193–206
Yang CN, Yu KH, Lukac R (2007) User-friendly image sharing using polynomials with different primes. In:. Int J Imaging Systems Technol 17(1):40–47
Yang CN, Chen TS, Yu KH, Wang CC (2007) Improvements of image sharing with steganography and authentication. In:. J Syst Softw 80(7):1070–1078
Zhang XP, Wang SZ (2006) Efficient steganographic embedding by exploiting modification direction. In:. IEEE Commun Lett 10(11):781–783
Acknowledgments
This research is funded by: (1) National Natural Science Foundation of China (nos.U143310218); (2) Chunhui Project of Education Ministry of China (nos.Z2014045); (3) Science and Education and Technology Bureau Project of Cheng-du Municipality (nos.2016-XT00-00015-GX); (4) Graduate Innovation Fund Project of Xi Hua University (nos.ycjj2018003); (5) Civil aviation administration of China (nos.PSDSA201802).
Author information
Authors and Affiliations
Corresponding authors
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Li, XS., Chang, CC., He, MX. et al. A lightweight authenticable visual secret sharing scheme based on turtle shell structure matrix. Multimed Tools Appl 79, 453–476 (2020). https://doi.org/10.1007/s11042-019-08077-z
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-019-08077-z