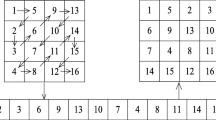
Abstract
This paper proposes an encryption algorithm that uses the initial values and parameters of the chaotic system as the key, and mainly uses the similar deoxyribonucleic acid (DNA-like) coding method and the similar Zigzag (Zigzag-like) transform to encrypt the image. Firstly, the image is pre-scrambled by the method of Zigzag-like transformation, and then the second scrambling is performed by a sorting scrambling algorithm with identification value. Secondly, the image is diffused by DNA-like coding method. Finally, the image is again diffused using the ortho exclusive OR (XOR) method with chaotic perturbation terms. The experimental results show that the chaotic image encryption algorithm proposed in this paper has satisfactory results. In addition, the algorithm is compared to the previously proposed chaotic image encryption algorithm for the Zigzag transform method or the deoxyribonucleic acid (DNA) coding method. The contribution is to improve the Zigzag transformation method and the DNA coding method, so that it has the advantages of higher security and higher sensitivity. It can also effectively resist exhaustive and differential attacks with better statistical characteristics.








Similar content being viewed by others
References
Abdo AA, Lian SG, Ismail IA et al (2013) A cryptosystem based on elementary cellular automata. Commun Nonlinear Sci Numer Simul 18(1):136–147
Bakhshandeh A, Eslami Z (2013) An authenticated image encryption scheme based on chaotic maps and memory cellular automata. Optics & Lasers in Engineering 51(6):665–673
Chai X (2017) An image encryption algorithm based on bit level Brownian motion and new chaotic systems. Multimedia Tools & Applications 76(1):1–17
Chen J, Han F, Qian W et al (2018) Cryptanalysis and improvement in an image encryption scheme using combination of the 1D chaotic map. Nonlinear Dynamics 93:2399–2413
Dhawan S, Saini A (2012) A new DNA encryption technique for secure data transmission. International Journal of Emerging Technologies in Computational and Applied Sciences 2(1):36–42
Dong HS, Lu P, Ma XH (2013) Image encryption algorithm based on CNN hyper chaotic system and extended zigzag transformation. Computer Applications and Software 30(5):132–136
Guesmi R, Farah MAB, Kachouri A et al (2016) A novel chaos-based image encryption using DNA sequence operation and secure hash algorithm SHA-2. Nonlinear Dynamics 83(3):1123–1136
Guo Y, Shao LP, Yang L (2015) Bit-level image encryption algorithm based on Josephus and Henon chaotic map. Application research of computer 32(4):1131–1137
Hermassi H, Belazi A, Rhouma R et al (2014) Security analysis of an image encryption algorithm based on a DNA addioton combining with chaotic maps. Multimed Tools Appl 72(3):2211–2224
Huang XL, Ye GD (2014) An image encryption algorithm based on hyper-chaos and DNA sequence. Multimed Tools Appl 72(1):57–70
Khellat F, Ghaderi A, Vasegh N (2011) Li-Yorke chaos and synchronous chaos in a globally nonlocal coupled map lattice. Chaos, Solitons Fractals 44(11):934–939
Ling WK (2011) Controlling Chaos: suppression, synchronization and Chaotification (Zhang, H. et al; 2009) [book review]. IEEE Comput Intell Mag 6(1):68–69
Liu G, Jiang TF, Jiang W (2013) Color image scrambling based on zigzag transformation. Computer Engineering and Science 35(5):106–111
Ma J, Ye RS (2015) Cryptanalysis on an image encryption scheme. Journal of Network New Media 4(6):37–42
Niu Y, Zhang X (2017) Chaotic image encryption algorithm based on bit permutation and DNA sequence. Computer Engineering and Application 53(17):130–136
Peng J, Jin SZ, Lei L et al (2013) Research on a novel image encryption algorithm based on the hybrid of chaotic maps and DNA encoding. IEEE Conference Publications:403–408
Seyedzadeh SM, Norouzi B, Mosavi MR et al (2015) A novel color image encryption algorithm based on spatial permutation and quantum chaotic map. Nonlinear Dynamics 81(1-2):511–529
Wang XY (2014) Xu D H. Anovel image encrypfion scheme based on Brownian motion and PWLCM chaotic system. Nonlinear Dynamics 75(1):345–353
Wang XY, Zhang YQ (2015) A new image encryption algorithm based on non-adjacent coupled map lattices. Appl Soft Comput 26(1):10–20
Wei X, Guo L, Zhang Q et al (2012) A novel color image encryption algorithm based on DNA sequence operation and hyper-chaotic system. J Syst Softw 85(2):290–299
Wu X, Kan H, Kurths J (2015) A new color image encryption scheme based on DNA sequences and multiple improved 1D chaotic maps. Appl Soft Comput 37(C):24–39
Xu X, Feng J (2010) Research and implementation of image encryption algorithm based on zigzag transformation and inner product polarization vector. IEEE International Conference on Granular Computing:556–561
Xu L, Li Z, Li J et al (2016) A novel bit-level image encryption algorithm based on chaotic maps. Optics & Lasers in Engineering 78(21):17–25
Yang YY, Jiang TL et al Method of digital image scrambling based on extended zigzag transformation. Netinfo Security 2011(11):57–58
Ye G, Zhao H, Chai H (2015) Chaotic image encryption algorithm using wave-line permutation and block diffusion. Nonlinear Dynamics 83:2067–2077
Zhang Y (2016) The image encryption algorithm with plaintext-related shuffling. IETE Tech Rev 33(3):310–322
Zhang Y, Tang Y (2018) A plaintext-related image encryption algorithm based on chaos. Multimedia Tools & Applications 77(6):1–23
Zhang YQ, Wang XY, Liu J et al (2016) An image encryption scheme based on the MLNCML system using DNA sequences. Opt Lasers Eng 82:95–103
Zhao J, Wang S, Chang Y et al (2015) A novel image encryption scheme based on an improper fractional-order chaotic system. Nonlinear Dynamics 80(4):1721–1729
Zhou C, Wei X, Zhang Q et al (2010) DNA sequence splicing with chaotic maps for image encryption. J Comput Theor Nanosci 7(10):1904–1910
Acknowledgements
This research is supported by the National Natural Science Foundation of China (Nos: 61672124, and 61370145), the Password Theory Project of the 13th Five-Year Plan National Cryptography Development Fund (No: MMJJ20170203).
Author information
Authors and Affiliations
Corresponding authors
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Wang, X., Sun, H. A chaotic image encryption algorithm based on zigzag-like transform and DNA-like coding. Multimed Tools Appl 78, 34981–34997 (2019). https://doi.org/10.1007/s11042-019-08085-z
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-019-08085-z