Abstract
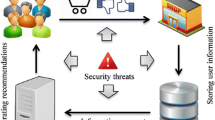
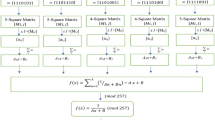
The strength of cryptography encryption is strongly depended upon the substitution box (S-box), hence highly non-linear S-box is appreciated in cryptography. In this work, we proposed a scheme to select the optimized values for control parameters (a, b, c, d) of linear fractional transform (LFT) to achieve an S-box with non-linearity of 112. For dynamic parameter values, we used location of chaotic sequences. The proposed s-box tested on different criteria such as non-linearity method (NL), probability methods (linear approximation (LP), differential approximation (DP), strictly avalanche criteria (SAC) and bit independence criteria (BIC). Our result shows that proposed s-box achieves better or equal to cryptographic strength as compared with state-of-the-art techniques. Moreover, we tested the proposed s-box based encryption method in recommendation system scenario with the idea of text-to-image conversion. The statistical analysis of this image encryption shows the bright prospects of the proposed method.






Similar content being viewed by others
References
Abd-El-Atty B, El-Latif AAA, Venegas-Andraca SE (2019) An encryption protocol for NEQR images based on one-particle quantum walks on a circle. Quantum Inf Process 18(9):272
Abdullah S, Amin NU (2015) Analysis of S-box image encryption based on generalized fuzzy soft expert set. Nonlinear Dyn 79:1679–1692
Aboytes-González JA, Murguía JS, Mejía-Carlos M, González-Aguilar H, Ramírez-Torres MT (2018) Design of a strong S-box based on a matrix approach. Nonlinear Dyn 94:2003–2012
Ahmad A, Mohammad T, Almimi HM (2014) Distributed text-to-image encryption algorithm. Int J Comput Appl 106:1
Al Solami E, Ahmad M, Volos C, Doja M, Beg M (2018) A new hyper chaotic system-based design for efficient bijective substitution-boxes. Entropy 20(7):525
Amin M, El-Latif AAA (2010) Efficient modified RC5 based on chaos adapted to image encryption. J Electron Imaging 19(1):013012
Belazi A, El-Latif AAA (2017) A simple yet efficient S-box method based on chaotic sine map. Optik 130:1438–1444
Belazi A, El-Latif AAA, Rhouma R, Belghith S (2015) Selective image encryption scheme based on DWT, AES S-box and chaotic permutation. In: international wireless communications and Mobile computing conference (IWCMC) IEEE. pp. 606–610
Belazi A, El-Latif AAA, Belghith S (2016) A novel image encryption scheme based on substitution-permutation network and chaos. Signal Process 128:155–170
Belazi A, Khan M, El-Latif AAA, Belghith S (2017) Efficient cryptosystem approaches: S-boxes and permutation–substitution-based encryption. Nonlinear Dyn 87(1):337–361
Belazi A, El-Latif AAA, Diaconu AV, Rhouma R, Belghith S (2017) Chaos-based partial image encryption scheme based on linear fractional and lifting wavelet transforms. Opt Lasers Eng 88:37–50
Benrhouma O, Hermassi H, El-Latif AAA, Belghith S (2015) Cryptanalysis of a video encryption method based on mixing and permutation operations in the DCT domain. SIViP 9(6):1281–1286
Bibi N, Farwa S, Muhammad N, Jahngir A, Usman M (2018) A novel encryption scheme for high-contrast image data in the Fresnelet domain. PLoS One 13
Biham E, Shamir A (1991) Differential cryptanalysis of DES-like cryptosystems. J Cryptol 4:3–72
Çavuşoğlu Ü, Zengin A, Pehlivan I, Kaçar S (2017) A novel approach for strong S-box generation algorithm design based on chaotic scaled Zhongtang system. Nonlinear Dyn 87:1081–1094
Cui L, Cao Y (2007) A new S-box structure named affine-power-affine. Int J Innov Comput Inf Control 3:751–759
Daemen J, Rijmen V (2002) The Design of Rijndael. Springer, Berlin Heidelberg. https://doi.org/10.1007/978-3-662-04722-4
EL-Latif AAA, Abd-El-Atty B, Venegas-Andraca SE (2019) A novel image steganography technique based on quantum substitution boxes. Opt Laser Technol 116:92–102
El-Latif AAA, Yan X, Li L, Wang N, Peng JL, Niu X (2013) A new meaningful secret sharing scheme based on random grids, error diffusion and chaotic encryption. Opt Laser Technol 54:389–400
El-Latif AAA, Wang N, Peng JL, Li Q, Niu X (2013) A new encryption scheme for color images based on quantum chaotic system in transform domain. In: 5th International Conference on Digital Image Processing (ICDIP 2013). Int Soc Opt Photon 8878:88781S
El-Latif AAA, Li L, Wang N, Han Q, Niu X (2013) A new approach to chaotic image encryption based on quantum chaotic system, exploiting color spaces. Signal Process 93(11):2986–3000
El-Latif AAA, Li L, Niu X (2014) A new image encryption scheme based on cyclic elliptic curve and chaotic system. Multimed Tools Appl 70(3):1559–1584
El-Latif AAA, Abd-El-Atty B, Talha M (2017) Robust encryption of quantum medical images. IEEE Access 6:1073–1081
Farwa S, Shah T, Idrees L (2016) A highly nonlinear S-box based on a fractional linear transformation. Springerplus 5:1658
Hussain I, Shah T, Gondal MA, Mahmood H (2012) Generalized Majority Logic Criterion to Analyze the Statistical Strength of S-Boxes. Z Naturforsch A 67
Hussain I, Shah T, Mahmood H, Gondal MA (2013) A projective general linear group based algorithm for the construction of substitution box for block ciphers. Neural Comput Appl 22:1085–1093
Hussain I, Anees A, AlKhaldi AH, Algarni A, Aslam M (2018) Construction of chaotic quantum magnets and matrix Lorenz systems S-boxes and their applications. Chin J Phys 56:1609–1621
Jhajharia S (2016) Using cell division for text to image encryption. In: 10th IEEE international conference on intelligent systems and control (ISCO), IEEE. pp. 1–7
Khan M, Asghar Z (2018) A novel construction of substitution box for image encryption applications with Gingerbreadman chaotic map and S8 permutation. Neural Comput Appl 29:993–999
Khan MA, Ali A, Jeoti V, Manzoor S (2018) A Chaos-based substitution box (S-box) design with improved differential approximation probability (DP). Iran J Sci Technol Trans Electr Eng 42:219–238
Khan MF, Ahmed A, Saleem K (2019). A novel cryptographic substitution box design using Gaussian distribution. IEEE Access
Kim J, Phan RC-W (2009) Advanced differential-style cryptanalysis of the NSA’s skipjack block cipher. Cryptologia 33:246–270
Lam S, Frankowski D, Riedl J (2006) Do you trust your recommendations? An exploration of security and privacy issues in recommender systems. Emerg Trends Inf Commun Secur 2006:14–29
Lambić D (2014) A novel method of S-box design based on chaotic map and composition method. Chaos, Solitons Fractals 58:16–21
Lambić D (2017) A novel method of S-box design based on discrete chaotic map. Nonlinear Dyn 87(4):2407–2413
Liu H, Kadir A, Niu Y (2014) Chaos-based color image block encryption scheme using S-box. AEU-Int J Electron Commun 68(7):676–686
Liu G, Yang W, Liu W, Dai Y (2015) Designing S-boxes based on 3-D four-wing autonomous chaotic system. Nonlinear Dyn 82(4):1867–1877
Matsui M (1993) Linear cryptanalysis method for DES cipher. In: Adv. Cryptol. — EUROCRYPT ‘93. Springer, Berlin Heidelberg, pp 386–397
Özkaynak F, Çelik V, Özer AB (2017) A new S-box construction method based on the fractional-order chaotic Chen system. Sig Image Video Process 11:659–664
Peng J, El-Latif AAA, Belazi A, Kotulski Z (2017) Efficient chaotic nonlinear component for secure cryptosystems. In: 9th International Conference on Ubiquitous and Future Networks (ICUFN), IEEE. pp. 989–993
Picek S, Batina L, Jakobović D, Ege B, Golub M (2014) S-box, SET, match: A toolbox for S-box analysis. pp. 140–149
Tran MT, Bui DK, Duong AD (2008) Gray S-box for advanced encryption standard. Int. Conf. Comput. Intell. Secur., IEEE. pp. 253–258
ul Islam F, Liu G (2017) Designing s-box based on 4D-4wing hyperchaotic system. 3D Res. 8:9.
Ullah A, Jamal SS, Shah T (2018) A novel scheme for image encryption using substitution box and chaotic system. Nonlinear Dyn 91:359–370
Wang Y, Xie Q, Wu Y, Du B (2009) A software for S-box performance analysis and test. Int. Conf. Electron. Commer. Bus. Intell., IEEE. pp. 125–128
Wang C, Zheng Y, Jiang J, Ren K (2018) Toward privacy-preserving personalized recommendation services. Engineering
Webster AF, Tavares SE (1985) On the design of S-boxes. In: Adv. Cryptol. — CRYPTO ‘85 Proc. Springer, Berlin Heidelberg, pp 523–534
Xu K, Yan Z (2016) Privacy protection in mobile recommender systems: a survey. In: Wang G, Ray I, Alcaraz Calero J, Thampi S (eds) Security, Privacy, and Anonymity in Computation, Communication, and Storage. SpaCCS 2016. Lecture notes in computer science, vol 10066. Springer, Cham, pp 305–318
Ye T, Zhimao L (2018) Chaotic S-box: six-dimensional fractional Lorenz–Duffing chaotic system and O-shaped path scrambling. Nonlinear Dyn 94:2115–2126
Yi X, Cheng SX, You XH, Lam KY (1997) A method for obtaining cryptographically strong 8×8 S-boxes. In: GLOBECOM 97. IEEE Glob. Telecommun. Conf. Conf. Rec., IEEE. pp 689–693
Zaghloul A, Zhang T, Amin M, El-Latif AAA (2014l) Color encryption scheme based on adapted quantum logistic map. In 6th International Conference on Digital Image Processing (ICDIP 2014). Int Soc Opt Photon 9159:915922
Zhang TJ, El-Latif AAA, Amin M, Zaghloul A (2014) Diffusion-substitution mechanism for color image encryption based on multiple chaotic systems. Adv Mater Res Trans Tech Publ 981:327–330
Zhang X, Zhao Z, Wang J (2014) Chaotic image encryption based on circular substitution box and key stream buffer. Signal Process Image Commun 29(8):902–913
Zhang T, El-Fatyany A, Li L, Amin M, El-Latif AAA (2015) Secret sharing-based chaotic image encryption. Int J Secur Appl 9(7):217–224
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
Mentioned authors have no conflict of interest in this article.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Beg, S., Ahmad, N., Anjum, A. et al. S-box design based on optimize LFT parameter selection: a practical approach in recommendation system domain. Multimed Tools Appl 79, 11667–11684 (2020). https://doi.org/10.1007/s11042-019-08464-6
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-019-08464-6