Abstract
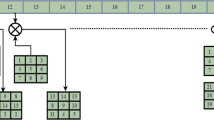
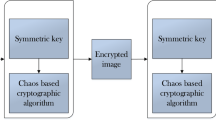
Securing digital medical images is increasingly becoming a major concern due to the rapid growth of the amount of medical images transferred over a network and stored on the web servers. However, the enormous size of multimedia and the huge volume of exchanging medical images have motivated the development of low computational complexity methods. This paper presents a lightweight selective encryption scheme to encrypt the edge maps of medical images. The edge map is firstly extracted by an edge detection method. Then, a chaotic map is used to generate a large key space. We propose a one-time pad algorithm to respectively encrypt the significant detected image blocks. The experimental results have proven that the proposed encryption scheme provides an acceptable percentage of encrypted image data. It can also effectively perform image encryption and decryption in a lightweight manner, which makes the scheme a good candidate for real time applications. Moreover, the security analysis demonstrates that our scheme has a robust resistance against various security attacks.







Similar content being viewed by others
References
Abdmouleh, MK, Khalfallah, A, and Bouhlel, MS (2017). A novel selective encryption dwt-based algorithm for medical images. In 2017 14th International Conference on Computer Graphics, Imaging and Visualization, pages 79–84. IEEE
Akkasaligar PT, Biradar S (2020) Selective medical image encryption using dna cryptography. Information Security Journal: A Global Perspective 29(2):91–101
AlShaikh M, Laouamer L, Nana L, Pascu AC (2017) Efficient and robust encryption and watermarking technique based on a new chaotic map approach. Multimed Tools Appl 76(6):8937–8950
Bhatnagar G, Wu QJ (2012) Selective image encryption based on pixels of interest and singular value decomposition. Digital signal processing 22(4):648–663
Cao W, Zhou Y, Chen CP, Xia L (2017) Medical image encryption using edge maps. Signal Process 132:96–109
Chabaud F, Vaudenay S (1994) Links between differential and linear cryptanalysis. In: Workshop on the Theory and Application of of Cryptographic Techniques. Springer, pp 356–365
Chen L, Wang S (2015) Di_erential cryptanalysis of a medical image cryptosystem with multiple rounds. Comput Biol Med 65:69–75
Darwish SM (2019) A modifed image selective encryption-compression technique based on 3d chaotic maps and arithmetic coding. Multimed Tools Appl 78(14):19229–19252
Hua Z, Zhou Y, Huang H (2019) Cosine-transform-based chaotic system for image encryption. Inf Sci 480:403–419
Huynh-Thu Q, Ghanbari M (2008) Scope of validity of psnr in image/video quality assessment. Electron Lett 44(13):800–801
Jain B, Taylor A (2003) Cross-correlation tomography: measuring dark energy evolution with weak lensing. Phys Rev Lett 91(14):141302
Juels A, Weis SA (2005) Authenticating pervasive devices with human protocols. In: Annual international cryptology conference. Springer, pp 293–308
Kar M, Kumar A, Nandi D, Mandal M (2020) Image encryption using dna coding and hyperchaotic system. IETE Tech Rev 37(1):12–23
Khan JS, Ahmad J (2019) Chaos based e_cient selective image encryption. Multidim Syst Sign Process 30(2):943–961
Khan MA, Ahmad J, Javaid Q, Saqib NA (2017) An e_cient and secure partial image encryption for wireless multimedia sensor networks using discrete wavelet transform, chaotic maps and substitution box. J Mod Opt 64(5):531–540
Khashan OA, Khafajah NM (2018) Secure stored images using transparent crypto filter driver. IJ Network Security 20(6):1053–1060
Khashan OA, Zin AM (2013) An efficient adaptive of transparent spatial digital image encryption. Procedia technology 11:288–297
Khashan OA, Zin AM, Sundararajan EA (2014) Performance study of selective encryption in comparison to full encryption for still visual images. Journal of Zhejiang University SCIENCE C 15(6):435–444
Khashan OA, Zin AM, Sundararajan EA (2015) Imgfs: a transparent cryptography for stored images using a filesystem in userspace. Frontiers of Information Technology & Electronic Engineering 16(1):28–42
Krishnamoorthi R, Murali P (2017) A selective image encryption based on square-wave shu_ing with orthogonal polynomials transformation suitable for mobile devices. Multimed Tools Appl 76(1):1217–1246
Kulsoom A, Xiao D, Abbas SA et al (2016) An efficient and noise resistive selective image encryption scheme for gray images based on chaotic maps and dna complementary rules. Multimed Tools Appl 75(1):1–23
Laouamer L, AlShaikh M, Nana L, Pascu AC (2015) Robust watermarking scheme and tamper detection based on threshold versus intensity. Journal of Innovation in Digital Ecosystems 2(1–2):1–12
Leng L, Li M, Kim C, Bi X (2017) Dual-source discrimination power analysis for multi-instance contactless palmprint recognition. Multimed Tools Appl 76(1):333–354
Li C, Lin D, Feng B, Lu J, Hao F (2018) Cryptanalysis of a chaotic image encryption algorithm based on information entropy. IEEE Access 6:75834–75842
Liao X, Yin J, Guo S, Li X, Sangaiah AK (2018) Medical jpeg image steganography based on preserving inter-block dependencies. Comput Electr Eng 67:320–329
Liu H, Wang X, Kadir A (2012) Image encryption using dna complementary rule and chaotic maps. Appl Soft Comput 12(5):1457–1466
Liu, Y, Ma, Z, Liu, X, Ma, S, and Ren, K (2019). Privacy-preserving object detection for medical images with faster r-cnn. IEEE Trans Inf Forensics Secur, 1
Mou, J, Yang, F, Chu, R, and Cao, Y\ (2019). Image compression and encryption algorithm based on hyper-chaotic map. Mobile Networks and Applications, pages 1-13
Moumen A, Bouye M, Sissaoui H (2015) New secure partial encryption method for medical images using graph coloring problem. Nonlinear Dynamics 82(3):1475–1482
Noura M, Noura H, Chehab A, Mansour MM, Sleem L, Couturier R (2018) A dynamic approach for a lightweight and secure cipher for medical images. Multimed Tools Appl 77(23):31397–31426
Pavithra, V and Chandrasekaran, J. (2020). Developing security solutions for telemedicine applications: medical image encryption and watermarking. In Smart Medical Data Sensing and IoT Systems Design in Healthcare, pages 76–96. IGI Global
Prabhu P, Manjunath K (2019) Secured transmission of medical images in radiology using aes technique. In: Computer Aided Intervention and Diagnostics in Clinical and Medical Images. Springer, pp 103–112
Prewitt JM (1970) Object enhancement and extraction. Picture processing and Psychopictorics 10(1):15–19
Rehman A u, Liao X, Kulsoom A, Abbas SA (2015) Selective encryption for gray images based on chaos and dna complementary rules. Multimed Tools Appl 74(13):4655–4677
Riad K, Hamza R, Yan H (2019) Sensitive and energetic iot access control for managing cloud electronic health records. IEEE Access 7:86384–86393
Som S, Mitra A, Palit S, Chaudhuri B (2019) A selective bitplane image encryption scheme using chaotic maps. Multimed Tools Appl 78(8):10373–10400
Steinebach M, Petitcolas FA, Raynal F, Dittmann J, Fontaine C, Seibel S, Fates N, Ferri LC (2001) Stirmark benchmark: audio watermarking attacks. In: Proceedings international conference on information technology: coding and computing. IEEE, pp 49–54
Tang Z, Yang Y, Xu S, Yu C, Zhang X (2019) Image encryption with double spiral scans and chaotic maps. Security and Communication Networks 2019:1–15
Tong X, Zhang M, Wang Z (2015) A new image encryption algorithm based on the high-dimensional chaotic map. The Imaging Science Journal 63(5):263–272
Ullah I, Iqbal W, Masood A (2013) Selective region based images encryption. In: 2013 2nd National conference on information assurance (NCIA), pages 125–128. IEEE
Wang L-T, Hoover NE, Porter EH, Zasio JJ (1987) Ssim: a software levelized compiled-code simulator. In: Proceedings of the 24th ACM/IEEE Design Automation Conference, pages 2-8. ACM
Wen W, Zhang Y, Fang Z, Chen J-X (2015) Infrared targetbased selective encryption by chaotic maps. Opt Commun 341:131–139
Wilks DS (2011) Statistical methods in the atmospheric sciences, volume 100. Academic press
Wolf A, Swift JB, Swinney HL, Vastano JA (1985) Determining lyapunov exponents from a time series. Physica D: Nonlinear Phenomena 16(3):285–317
Wu Y, Noonan JP, Agaian S et al (2011) Npcr and uaci randomness tests for image encryption. Cyber journals: multidisciplinary journals in science and technology, Journal of Selected Areas in Telecommunications (JSAT) 1(2):31–38
Wu L, Xu Z, He D, Wang X (2018) New certi_cateless aggregate signature scheme for healthcare multimedia social network on cloud environment. Security and Communication Networks 2018:1–13
Zhang Y, Xiao D, Wen W, Tian Y (2013) Edge-based lightweight image encryption using chaos-based reversible hidden transform and multipleorder discrete fractional cosine transform. Opt Laser Technol 54:1–6
Zhang L-B, Zhu Z-L, Yang B-Q, Liu W-Y, Zhu H-F, Zou M-Y (2015) Cryptanalysis and improvement of an e_cient and secure medical image protection scheme. Math Probl Eng 2015
Zhou Y, Panetta K, Agaian S (2009) A lossless encryption method for medical images using edge maps. In: 2009 Annual International Conference of the IEEE Engineering in Medicine and Biology Society, pages 3707–3710. IEEE
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Khashan, O.A., AlShaikh, M. Edge-based lightweight selective encryption scheme for digital medical images. Multimed Tools Appl 79, 26369–26388 (2020). https://doi.org/10.1007/s11042-020-09264-z
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-020-09264-z