Abstract
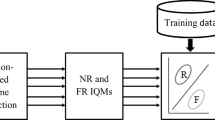
Biometric authentication poses a significant problem as reconstructed sample or fake self-manufactured samples used by intruders for accessing the actual real legitimate traits. The other prime concern for biometrics is the increasing demand for safety in mobile devices, such as smartphones and tablets etc. So, in the present scenario security for biometrics has gained considerable attention due to various inherent qualities of biometrics. For detection of valid user in a face recognition system with photographs, videos, and 3D models, face liveness detection system is a great technique against spoofing attacks for differentiating between the fake traits from the real traits. In this paper, a novel fake biometric detection technique utilizing liveness detection is proposed for detecting deceitful access attempts in the biometric face system. The prime objective of the paper is to propose a low-complexity fake biometric detection using different image quality assessment parameters i.e. Mean Square Error, Signal to Noise Ratio,SC etc. on the extracted features of the images. The authenticity of the proposed model is confirmed by analyzing the values of MSE, which are 5.8% and 8.49% more than the threshold value of nose and eye features. The same results have also been shown for other 11 different image quality assessment parameters. The experiments were done on the database prepared using the image samples of the 500 male and female students having age between 20 to 30 years.










Similar content being viewed by others
References
Avcibas et al (2003) Steganalysis using image quality metrics. IEEE Trans Image Process 12(2):221–229
Bayram S et al (2006) Image manipulation detection. J Electron Imaging 15(4):041102–041102
Bledsoe WW (1964) The model method in facial recognition, Panoramic Research Inc., Palo Alto. CA, Technical Report, Technical Report PRI: 15
Boulkenafet Z et al (2017) A competition on generalized software-based face presentation attack detection in mobile scenarios. 2017 IEEE International Joint Conference on Biometrics (IJCB). IEEE
Chakka MM et al (2011) Competition on countermeasures to 2-d facial spoofing attacks." Biometrics (IJCB), 2011 International Joint Conference on. IEEE
Champod C et al (2014) Forgeries of fingerprints in forensic science. Handbook of Biometric Anti-Spoofing. Springer, London, pp 13–34
Chan PPK et al (2017) Face liveness detection using a flash against 2D spoofing attack. IEEE Trans Inform Forensics Secur 13(2):521–534
Chen H et al (2019) EchoFace: acoustic sensor-based media attack detection for face authentication. IEEE Internet Things J 7(3):2152–2159
Davis et al (1952) Automatic recognition of spoken digits. J Acoustical Soc Am 24(6):637–642
Galbally J et al (2012) Iris liveness detection based on quality related features." Biometrics (ICB), 2012 5th IAPR International Conference on. IEEE
Galbally J, Alonso-Fernandez F, Fierrez J, Ortega-Garcia J (2012) A high-performance fingerprint liveness detection method based on quality related features. Futur Gener Comput Syst 28(1):311–321
Galbally et al (2014) Biometric antispoofing methods: a survey in face recognition. IEEE Access 2:1530–1552
Galbally J, Marcel S, Fierrez J (2014) Image quality assessment for fake biometric detection: application to iris, fingerprint, and face recognition. IEEE Trans Image Process 23(2):710–724
Ghiani L et al (2013) Livdet 2013 fingerprint liveness detection competition 2013. Biometrics (ICB), 2013 International Conference on. IEEE
Goswami G et al (2012) Face recognition captcha." 2012 IEEE Fifth International Conference on Biometrics: Theory, Applications, and Systems (BTAS). IEEE
Jain AK, Ross A, Prabhakar S (2004) An introduction to biometric recognition. IEEE Trans Circuits Syst Video Technol 14(1):4–20
Jain AK, Ross A, Pankanti S (2006) Biometrics: a tool for information security. IEEE Trans Inform Forensics Secur 1(2):125–143
Kelly, et al (1970) Visual identification of people by computer. No. CS-168. Stanford University, Calif Dept of Computer Science
Kim Y, Yoo J-H, Choi K (2011) A motion and similarity-based fake detection method for biometric face recognition systems. IEEE Trans Consum Electron 57(2):756–762
Kim W, Suh S, Han J-J (2015) Face liveness detection from a single image via diffusion speed model. IEEE Trans Image Process 24(8):2456–2465
Kollreider K, Fronthaler H, Faraj MI, Bigun J (2007) Real-time face detection and motion analysis with application in “liveness” assessment. IEEE Trans Inform Forensics Secur 2(3):548–558
Korshunov P et al (2016) Overview of BTAS 2016 speaker anti-spoofing competition. 2016 IEEE 8th international conference on biometrics theory, applications, and systems (BTAS). IEEE
Le C et al (2009) A survey of biometrics security systems. EEUU. Washington University in St. Louis
Lyu et al (2006) Steganalysis using higher-order image statistics. IEEE Trans Inform Forensics Secur 1(1):111–119
Maltoni D et al (2009) Handbook of fingerprint recognition. Springer Science & Business Media
Marcel S et al (2014) Li. Handbook of biometric anti-spoofing, vol 1. Springer, New York
Marcel S et al (2014) Handbook of biometric anti-spoofing, vol 1. Springer, New York
Marcialis S et al (2009) Liveness detection competition 2009. Biometric Technol Today 17(3):7–9
Nguyen MH et al (2008) Image-based shaving. Computer graphics forum. Vol. 27. No. 2. Blackwell Publishing Ltd, Oxford
O'Brien J 2013 The scientific Sherlock Holmes: cracking the case with science and forensics. Oxford University Press
Pan G et al (2007) Eyeblink-based anti-spoofing in face recognition from a generic web camera. 2007 IEEE 11th International Conference on Computer Vision. IEEE
Phillips PJ et al. (2003.) Face recognition vendor test (FRVT) 2002: Overview and summary." Online: http://www.rvt.Org/FRVT2002/documents.htm
Ravibabu V et al (2014) A vary approach to face veritable recognition mechanisms for Android mobile against spoofing. 2014 IEEE Int Confer Computational Intelligence and Computing Research. IEEE
Smith DF et al (2015) Binary watermarks: a practical method to address face recognition replay attacks on consumer mobile devices." IEEE International Conference on Identity, Security, and Behavior Analysis (ISBA 2015). IEEE
Sun W, Song Y, Chen C, Huang J, Kot AC (2020) Face spoofing detection based on local ternary label supervision in fully convolutional networks. IEEE Trans Inform Forensics Secur 15:3181–3196
Yambay D, et al (2012) LivDet 2011—Fingerprint liveness detection competition 2011. Biometrics (ICB), 2012 5th IAPR International Conference on. IEEE
Yambay D et al (2014) Livdet-iris 2013-iris liveness detection competition 2013. Biometrics (IJCB), 2014 IEEE International Joint Conference on. IEEE
Yambay D et al (2017) LivDet-Iris 2015-Iris Liveness Detection Competition 2015. 2017 IEEE International Conference on Identity, Security, and Behavior Analysis (ISBA). IEEE
Yambay D et al (2017) LivDet iris 2017—Iris liveness detection competition 2017." 2017 IEEE International Joint Conference on Biometrics (IJCB). IEEE
Yambay D et al (2018) LivDet 2017-Fingerprint Systems Liveness Detection Competition. 2018 IEEE 9th International Conference on Biometrics Theory, Applications and Systems (BTAS). IEEE
Zhang D, Shu W (1999) Two novel characteristics in palmprint verification: datum point invariance and line feature matching. Pattern Recogn 32(4):691–702
Zhang Y, Shi D, Zhan X, Cao D, Zhu K, Li Z (2019) Slim-ResCNN: a deep residual convolutional neural network for fingerprint Liveness detection. IEEE Access 7:91476–91487
Author information
Authors and Affiliations
Contributions
The major author contributions are following:
Aditya Bakshi carried out the all research work and wrote this manuscript.
Dr. Sunanda has suggested some changes in formatting of the manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The author declares that there is no conflict of interest regarding the publication of this paper.
Data availability
No data were used to support this study.
Code availability
There is no significant code available for this paper.
Ethics approval
Not applicable.
Consent for publication
Yes. Consent has been given by an individual for the publication of their data or image.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Bakshi, A., Gupta, S. An efficient face anti-spoofing and detection model using image quality assessment parameters. Multimed Tools Appl 81, 35047–35068 (2022). https://doi.org/10.1007/s11042-020-10045-x
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-020-10045-x