Abstract
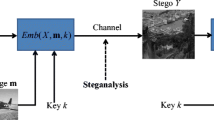
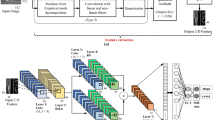
Camouflaged communication using a media is known as Steganography. It is different than encryption as the presence of message is also concealed in case of steganography. The message however can be encrypted before hiding in a media. Detection of concealed exchange being carried out or unraveling the details of such transmission is known as Steganalysis. Steganalysis can be detected by classifying the given media file as cover media file or stego media file. Blind steganalysis detects presence of hidden content without any knowledge about the cover media file and steganography algorithm used. Steganalysis plays a vital role in forensics of various media such as text, audio, image, video and network packets. Machine learning techniques have been widely used for steganalysis in literature. These techniques use a three step approach consisting of Feature Extraction, Training and Testing Phases. Deep learning techniques, a subset of machine learning techniques are preferred by researchers over machine learning techniques as (i) they consist of Training and Testing Phases with the feature extraction step done automatically, (ii) they give better accuracy when trained with huge amount of data. This paper proposes novel multi class blind steganalysis technique for images. Convolutional Neural Network (CNN) is one of the best known architecture used with image steganalysis. But as the depth of CNN architecture increases, problem of vanishing descent arise which affects the accuracy. In order to solve the problem of the vanishing/exploding gradient in CNN, concept called Residual Network which use a technique called skip connections is being used. The skip connection skips training from few layers and connects directly to the output. A deep residual network helps to automatically capture complex statistical features of images and preserve weak stego signal in image content making it suitable for multi class blind steganalysis. This paper uses deep residual network for multi-class blind steganalysis. Proposed DRN has been successfully applied for multi class blind steganalysis in spatial and JPEG images. Experimental results demonstrate proposed network is comparable to state or art techniques present in literature.













Similar content being viewed by others
References
Avcibas I, Memon N, Sankur B (2001) Steganalysis Using Image Quality Metrics. Proc SPIE Electron Imaging Secur Watermark Multimed Contents 4314(II):523–531
Bas P, Filler T, Pevny T (2011) Break our Steganographic system: the ins and outs of organizing BOSS. Springer, Berlin, pp 59–70
Bedi P, Bhasin V, Mittal N, Chatterjee T (2014) FS-SDS: Feature selection for JPEG steganalysis using stochastic diffusion search. SMC, Noida, pp 3797–3802
Bhasin V, Bedi P (2013) Multi-class jpeg steganalysis using extreme learning machine. In Advances in Computing, Communications and Informatics (ICACCI), pp 1948–1952
Bhasin V, Bedi P, Singhal A (2014) Feature selection for steganalysis based on modified Stochastic Diffusion Search using Fisher score. ICACCI, Noida, pp 2323–2330
Bhasin V, Bedi P, Goel A, Gupta S (2015) StegTrack: Tracking images with hidden content in WCI, pp 318–323
Bhasin V, Bedi P, Singh N, Aggarwal C (2015) FS-EHS: Harmony Search Based Feature Selection Algorithm for Steganalysis Using ELM. in IBICA, pp 393–402
Bianchini M, Scarselli F (2014) On the complexity of neural network classifiers: a comparison between shallow and deep architectures. IEEE Trans Neural Networks Learn Syst 25(8):1553–1565
Boroumand M, Chen M, Fridrich J (2019) Deep residual network for steganalysis of digital images. IEEE Trans Information Forensics Secur 14:1181–1193
Chaumont M (2019) Deep Learning in steganography and steganalysis from 2015 to 2018. , arXiv preprint arXiv:1904.01444
Chaumont M (2020) Deep learning in steganography and steganalysis., in Digital Media Steganography. Principles, Algorithms, and Advances.: Academic Press, pp 321–349
Chiew KL, Pieprzyk J (2010) Binary image steganographic techniques classification based on multi-class steganalysis. In: InInternational Conference on Information Security Practice and Experience, Springer, Berlin, pp 341–358
Dong J, Wang W, Tan T (2009) Multi-class blind steganalysis based on image run-length analysis. In: In International Workshop on Digital Watermarking. Springer, Berlin, pp 199–210
Fridrich J, Kodovsk J (2013) Steganalysis of LSB replacement using parity-aware features. Inf Hiding 7692(Lecture Notes Comput Sci):31–45
Fridrich J, Kodovsky J (2009) Calibration revisited. 11th ACM Multimedia & Security Workshop, Princeton
Fridrich J and Kodovsky J, "Rich models for steganalysis of digital images.," IEEE Trans Information Forensics Secur. vol. 3, pp. 868–882, Jun 7 2012.
Fridrich J, Pevny T (2007) Merging Markov and DCT features for multiclass JPEG steganalysis. In Proc SPIE Electronic Imaging, Security, Steganography, and Watermarking of Multimedia, San Jose
Fridrich J, Goljan M, Du R (2001) Detecting LSB steganography in color and gray-scale images. IEEE Multimed Special Issue Secur 8(4):22–28
Glorot X, Bordes A, Bengio Y (2011 June) Deep sparse rectifier neural networks. In: Proceedings of the Fourteenth International Conference on Artificial Intelligence and Statistics, pp 315–323
Goodfellow I, Bengio Y, Courville A (2016) Deep learning.: MIT Press
He K, Zhang X, Ren S, Sun J (2016) Deep residual learning for image recognition. In: Proceedings of the IEEE conference on computer vision and pattern recognition, pp 770–778
Holub V, Fridrich J (2012) Designing steganographic distortion using directional filters. IEEE International workshop on information forensics and security (WIFS), pp 234–239
Holub V, Fridrich J, Denemark T (2014) Universal distortion function for steganography in an arbitrary domain. EURASIP J Information Secur 1
Ioffe S, Szegedy C (2015) Batch normalization: Accelerating deep network training by reducing internal covariate shift, preprint arXiv, vol 1502.03167
Jindal H, Kasana SS, Saxena S (2016) A novel image zooming technique using wavelet coefficients. In: Proceedings of the International Conference on Recent Cognizance in Wireless Communication & Image Processing. Springer, New Delhi, pp 1–7
Jindal H, Kasana SS, Saxena S (2018) Underwater pipelines panoramic image transmission and refinement using acoustic sensors. Int J Wavelets Multiresolution Information Process 16(03):1850013
Kaur S, Jindal H (2017) Enhanced image watermarking technique using wavelets and interpolation. International Journal of Image, Graphics and Signal Processing 11(7):23
Kodovsky J, Fridrich J, Holub V (2011) Ensemble classifiers for steganalysis of digital media. IEEE Trans Inf Forensics Secur 7(2):432–444
Kodovsky J, Fridrich J, Holub V (2012) Ensemble classifiers for Steganalysis of digital media. IEEE Trans Information Forensics Secur 7:432–444
Krizhevsky A (2012) Ilya Sutskever, and Geoffrey E Hinton, "Imagenet classification with deep convolutional neural, In Advances in neural information processing systems, pp 1097–1105
LeCun Y, Bengio Y, Hinton G (2015) Deep learning. Nature 521(7553):436–444
Li B, Wang M, Huang J, Li X (2014) A new cost function for spatial image steganography. In: 2014 IEEE International Conference on Image Processing (ICIP). IEEE, pp 4206–4210
Li Q, Feng G, Wu H, Zhang X (2019) Ensemble steganalysis based on deep residual network. In: International Workshop on Digital Watermarking. Springer, Cham, pp 84–95
Liu H, Wang X (2010) Color image encryption based on one-time keys and robust chaotic maps. Comput Mathematics Appl 59(10):3320–3327
Liu H, Wang X (2011) Color image encryption using spatial bit-level permutation and high-dimension chaotic system. Opt Commun 284(16–17):3895–3903
Liu H, Wang X (2012) Image encryption using DNA complementary rule and chaotic maps. Appl Soft Comput 12(5):1457–1466
Lu JC, Liu FL, Luo XY (2014) Selection of image features for steganalysis based on the fisher criterion. Digit Investig 11(1):57–66
Lubenko I, Ker AD (2011) Steganalysis using logistic regression. In Media Watermarking, Security, and Forensics III, vol 7880. International Society for Optics and Photonics, p 78800K
Lyu S, Farid H (2006) Steganalysis using higher-order image statistics. IEEE Trans Inf Forensics Secur 1(1):111–119
Mander K, Jindal H (2017) An improved image compression-decompression technique using block truncation and wavelets. International Journal of Image, Graphics and Signal Processing 9(8):17
Mittal A, Jindal H (2017) Novelty in Image Reconstruction using DWT and CLAHE. International Journal of Image, Graphics and Signal Processing 9(5):28
Nissar A, Mir AH (2010) Classification of steganalysis techniques: a study. Digit Signal Process 20(6):1758–1770
Pevný T, Fridrich J (2005) Towards multi-class blind steganalyzer for JPEG images. International Workshop on Digital Watermarking, Berlin, pp 39–53
Pevny T, Fridrich J (2007) Merging Markov and DCT features for multi-class JPEG steganalysis, InSecurity, Steganography, and Watermarking of Multimedia Contents, International Society for Optics and Photonics., vol 6505
Pevný T, Filler T, Bas P (2010) Using high-dimensional image models to perform highly undetectable steganography. In: International Workshop on Information Hiding. Springer, Berlin, Heidelberg, pp 161–177
Qian Y, Dong J, Wang W, Tan T (2015) Deep learning for steganalysis via convolutional neural networks. In Media Watermarking, Security, and Forensics 2015, vol 9409, no 9409
Savoldi A, Gubian P (2007) Blind multi-class steganalysis system using wavelet statistics. Third International Conference on Intelligent Information Hiding and Multimedia Signal Processing (IIH-MSP 2007, vol 2, pp 93–96
Sedighi V, Cogranne R, Fridrich J (2015) Content-adaptive steganography by minimizing statistical detectability. in IEEE Transactions on Information Forensics and Security, pp 221–234
Solanki K, Sarkar A, Manjunath BS (2007 Jun 11) YASS: Yet another steganographic scheme that resists blind steganalysis. In: In International Workshop on Information Hiding. Springer, Berlin, pp 16–31
Soukal D, Fridrich J, Goljan M (2005) Maximum likelihood estimation of secret message length embedded using steganography in spatial domain. Proc SPIE Electron Imaging Secur 5681(Jan. 16–20):595–606
Sun Z, Hui M, Guan C (2008) Steganalysis based on co-occurrence matrix of differential image. In International conference on intelligent information hiding and multimedia signal processing, pp 1097–1100
Szegedy C, Ioffe S, Vanhoucke V, Alemi A (2017 Feb) Inception-v4, inception-resnet and the impact of residual connections on learning. In: Proceedings of the AAAI Conference on Artificial Intelligence 31(1)
Tan S, Li B (2014 Dec) Stacked convolutional auto-encoders for steganalysis of digital images. In Signal and Information Processing Association Annual Summit and Conference (APSIPA), 2014 Asia-Pacific. IEEE, pp 1–4
Tang W, Li H, Luo W, Huang J (2015) Adaptive steganalysis based on embedding probabilities of pixels. IEEE Trans Information Forensics Secur 11(3):734–745
Wang X, Gao S., "Image encryption algorithm for synchronously updating Boolean networks based on matrix semi-tensor product theory. ," Information Sci. , vol. 507, pp. 16–36, Jan 1 2020.
Wang XY, Yang L, Liu R, Kadir A (2010) A chaotic image encryption algorithm based on perceptron model. Nonlinear Dynamics 62(3):615–621
Wang X, Feng L, Zhao H (2019) Fast image encryption algorithm based on parallel computing system. Information Sci 486:340–358
Wang C, Wang X, Xia Z, Ma B, Shi YQ (2019) Image description with polar harmonic Fourier moments. IEEE Trans Circuits Syst Video Technol
Wang C, Wang X, Xia Z, Zhang C (2019) Ternary radial harmonic Fourier moments based robust stereo image zero-watermarking algorithm. Inf Sci 470:109–120
Wu S, Zhong SH, Liu Y (2016) Steganalysis via deep residual network. In IEEE 22nd International Conference on Parallel and Distributed Systems (ICPADS), pp 1233–1236
Wu S, Zhong SH, Liu Y (2017) Residual convolution network based steganalysis with adaptive content suppression. In IEEE International Conference on Multimedia and Expo (ICME), pp 241–246
Wu S, Zhong S, Liu Y (2018) Deep residual learning for image steganalysis. Multimed Tools Appl 77(9):10437–10453
Xu G, Wu HZ, Shi YQ (2016 June) Ensemble of CNNs for steganalysis: an empirical study. In: Proceedings of the 4th ACM Workshop on Information Hiding and Multimedia Security 20:103–107
Xu G, Wu HZ, Shi YQ (2016) Structural design of convolutional neural networks for steganalysis. IEEE Signal Process Lett 23(5):708–712
Yamashita R, Nishio M, Do RK, Togashi K (2018) Convolutional neural networks: an overview and application in radiology. Insights Imaging 9(4):611–629
Ye J, Ni J, Yi Y (2017) Deep learning hierarchical representations for image steganalysis. IEEE Trans Inf Forensics Secur 12(11):2545–2557
Yedroudj M, Comby F, Chaumont M (2018) Yedroudj-Net:An Efficient CNN for Spatial Steganalysis. In2018 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), pp. 2092-2096
Zeng L, Lu W, Liu W, Chen J (2020) Deep residual network for halftone image steganalysis with stego-signal diffusion. Signal Process 107576
Zhang Z, Hu D, Yang Y, Su B (2013) A universal digital image steganalysis method based on sparse representation. In: 2013 Ninth International Conference on Computational Intelligence and Security. IEEE, pp 437–441
Zhang S, Zhang H, Zhao X, Yu H (2018) A deep residual multi-scale convolutional network for spatial steganalysis. In: International Workshop on Digital Watermarking. Springer, Cham, pp 40–52
Zhao H, Wang H, Khan MK (2011) Steganalysis for palette-based images using generalized difference image and color correlogram. Signal Process 91(11):2595–2605
Zong H, Liu FL, Luo XY (2012) Blind image steganalysis based on wavelet coefficient correlation. Digit Investig 9(1):58–68
Acknowledgments
We seriously thank the editor and anonymous reviewers for their valuable comments and suggestions which have immensely helped in improving the quality of our paper.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Singhal, A., Bedi, P. Multi-class blind steganalysis using deep residual networks. Multimed Tools Appl 80, 13931–13956 (2021). https://doi.org/10.1007/s11042-020-10353-2
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-020-10353-2