Abstract
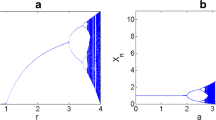
In the current decade, chaos based image encryption has distinctly captured a remarkable position in multimedia data security. In this paper, a hybrid chaos based image encryption scheme has been developed. A two-dimensional ecological chaotic map, namely Beddington, Free and Lawton (BFL) map has been combined with logistic map and Chebyshev map to generate a pseudo-random keystream for image encryption. In addition, an image substitution technique based on logistic map has been proposed. The random nature of keystream has been successfully tested by employing DIEHARD and NIST randomness test suites. Furthermore, the scheme has also been verified by histogram, correlation, global entropy, local entropy, key sensitivity and differential attack analyses. The proposed scheme achieves average \(41.6\%\) and \(8.5\%\) improvement in correlation value of cipher image and plaintext sensitivity, respectively, compared to Sheela et al.’s scheme.
















Similar content being viewed by others
References
Alvarez G, Li S (2006) Some basic cryptographic requirements for chaos-based cryptosystems. International Journal of Bifurcation and Chaos 16(8):2129–2151
Beddington JR, Free CA, Lawton JH (1975) Dynamic complexity in predator-prey models framed in difference equations. Nature 255:58–60
Chen JX, Zhu ZL, Fu C, Yu H, Zhang LB (2015) An efficient image encryption scheme using gray code based permutation approach. Optics and Lasers in Engineering 67:191–204
Chen JX, Zhu ZL, Fu C, Yu H (2015) Optical image encryption scheme using 3-D chaotic map based joint image scrambling and random encoding in gyrator domains. Optics Communications 341:263–270
Dey D, Giri D, Jana B, Maitra T, Mohapatra RN (2018) Linear-feedback shift register-based multi-ant cellular automation and chaotic map-based image encryption. Security and Privacy 1(6):1–11
Fu C, Chen JJ, Zou H, Meng WH, Zhan YF, Yu YW (2012) A chaos-based digital image encryption scheme with an improved diffusion strategy. Optics Express 20(3):2363–2378
Funt, et al. HDR Dataset Computational Vision Lab Computing Science, Simon Fraser University, Burnaby, BC, Canada. http://www.cs.sfu.ca/ colour/data/funt_hdr/. Accessed 02 May 2017
Geisel T, Fairen V (1984) Statistical Properties of Chaos in Chebyshev Maps. Physics Letters A 105(6):263–266
Hikal NA, Eid MM (2020) A new approach for palmprint image encryption based on hybrid chaotic maps. Journal of King Saud University - Computer and Information Sciences 32(7):870–882
Hua Z, Zhou Y, Huang H (2019) Cosine-transform-based chaotic system for image encryption. Information Sciences 480:403–419
Huang X (2012) Image encryption algorithm using chaotic Chebyshev generator. Nonlinear Dynamics 67:2411–2417
Li C, Luo G, Li C (2018) A parallel image encryption algorithm based on chaotic Duffing oscillators. Multimed Tools Appl 77:19193–19208
Mendoza SA, Matt EW, Guimarães-Blandón DR (2018) Parrondo’s paradox or chaos control in discrete two-dimensional dynamic systems. Chaos, Solitons & Fractals 106:86–93
Nicholson AJ, Bailey VA (1935) The balance of animal populations - Part I. Proc Zool Soc London 105(3):551–598
Nottingham Trent University, UK, “UCID Image Database”. http://jasoncantarella.com/downloads/ucid.v2.tar.gz. Accessed 02 May 2018
Ricker WE (1954) Stock and recruitment. Journal of the Fisheries Research Board of Canada 11(5):559–623
Seyedzadeh SM, Norouzi B, Mosavi MR, Mirzakuchaki S (2015) A novel color image encryption algorithm based on spatial permutation and quantum chaotic map. Nonlinear Dynamics 81(1–2):511–529
Sheela SJ, Suresh KV, Tandur D (2018) Image encryption based on modified Henon map using hybrid chaotic shift transform. Multimed Tools Appl 77:25223–25251
Stinson D (2002) Cryptography: Theory and Practice. Second ed. CRC/C&H
Taneja N, Raman B, Gupta I (2011) Selective image encryption in fractional wavelet domain. International Journal of Electronics and Communications 65(4):338–344
Taneja N, Raman B, Gupta I (2011) Chaos Based Partial Encryption of SPIHT Compressed Images. International Journal of Wavelets, Multiresolution and Information Processing 9(2):317–331
Taneja N, Raman B, Gupta I (2012) Combinational domain encryption for still visual data. Multimed Tools Appl 59:775–793
Taneja N, Raman B, Gupta I (2012) Chaos based cryptosystem for still visual data. Multimed Tools Appl 61:281–298
Tong XJ, Wang Z, Zhang M, Liu Y, Xu H, Ma J (2015) An image encryption algorithm based on the perturbed high-dimensional chaotic map. Nonlinear Dynamics 80:1493–1508
University of California, San Diego, “STARE Image Database”. https://cecas.clemson.edu/ ahoover/stare/. Accessed 02 May 2018
University of Southern California, “The USC-SIPI Image Database”. http://sipi.usc.edu/database/database.php. Accessed 02 May 2018
Wang X, Xu D (2015) A novel image encryption scheme using chaos and Langton’s Ant cellular automaton. Nonlinear Dynamics 79:2449–2456
Wu Y Noonan JP Agaian S (2011) NPCR and UACI randomness tests for image encryption. Cyber Journals: Multidisciplinary Journals in Science and Technology, Journal of Selected Areas in Telecommunications (JSAT) : 31–38
Wu Y, Zhou Y, Saveriades G, Agaian S, Noonan JP, Natarajan P (2013) Local Shannon entropy measure with statistical tests for image randomness. Information Sciences 222:323–342
Zhang X, Mao Y, Zhao Z (2014) An efficient chaotic image encryption based on alternate circular S-boxes. Nonlinear Dynamics 78:359–369
Zhang X, Zhao Z, Wang J (2014) Chaotic image encryption based on circular substitution box and key stream buffer. Signal Processing: Image Communication 29(8):902–913
Zhu S, Zhu C (2018) Image encryption algorithm with an avalanche effect based on a six-dimensional discrete chaotic system. Multimed Tools Appl 77:29119–29142
Author information
Authors and Affiliations
Additional information
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
De, S., Bhaumik, J. & Giri, D. A secure image encryption scheme based on three different chaotic maps. Multimed Tools Appl 81, 5485–5514 (2022). https://doi.org/10.1007/s11042-021-11696-0
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-021-11696-0