Abstract
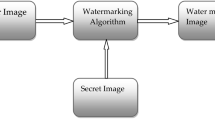
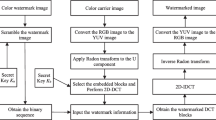
This article presents a recent blind and robust fingerprint image watermarking scheme based on a two-dimensional discrete cosine transform (2D-DCT). The main focus is to compress the fingerprint image watermarked data for the purpose of reducing the volume of storage or sending over the network. The fingerprint features might be affected by the embedded watermark, compression of fingerprint images and the sending across network, thereby leading to various sets of features or watermark data. In order to address this goal in a differential way, the watermark sequence bit two sub-vectors were utilized. The two sub-vectors were achieved by the two-dimensional discrete cosine transform of the host image. Throughout the extraction stage, the essential distinction between the corresponding sub-vectors of the watermarked fingerprint image resulted explicitly in an embedded watermark sequence. The advantage of the proposed method is that it can develop a new simple blind and robust watermarking scheme by 2D-DCT frequency domain on the whole image. Accomplished results relative to other reliable compression schemes showed that the proposed scheme has greater or equivalent robustness to common image processing and geometric attacks, such as cropping, resizing, and rotation. To extract watermark data, the initial fingerprint image was not necessary. The proposed study was tested using 80 fingerprint images from 10 persons, for each from CASIA-FingerprintV5 and FVC2002 fingerprint databases. Eight fingerprint images for each individual were set as the format at which the watermark was embedded in each one.










Similar content being viewed by others
References
Alkhathami M, Han F, Van Schyndel R (1717–1723) Fingerprint image watermarking approach using DTCWT without corrupting minutiae, in: 2013 6th international congress on image and signal processing (CISP), 2013: pp. https://doi.org/10.1109/CISP.2013.6743953
Benoraira A, Benmahammed K, Boucenna N (2015) Blind image watermarking technique based on differential embedding in DWT and DCT domains. EURASIP J Advanc Signal Process 2015:1–11
Bousnina N, Ghouzali S, Lafkih M, Nafea O, Mikram M, Abdul W, Aboutajdine D (2016) Watermarking for protected fingerprint authentication:127–131. https://doi.org/10.1109/INNOVATIONS.2016.7880039
Dixit A, Dixit R (2017) A review on digital image watermarking techniques. Int J Image, Graph Signal Process 9
K.K.A. Ghany, G. Hassan, A.E. Hassanien, H.A. Hefny, G. Schaefer, M.A.R. Ahad, A hybrid biometric approach embedding DNA data in fingerprint images, in: 2014 International Conference on Informatics, Electronics & Vision (ICIEV), 2014: pp. 1–5. https://doi.org/10.1109/ICIEV.2014.6850836.
Haddada LR, Dorizzi B, Ben Amara NE (2017) A combined watermarking approach for securing biometric data. Signal Process Image Commun 55:23–31
Hamghalam M, Mirzakuchaki S, Akhaee MA (2014) Geometric modelling of the wavelet coefficients for imagewatermarking using optimum detector. IET Image Process 8(3):162–172
Huang H-C, Chu S-C, Pan J-S, Huang C-Y, Liao B-Y (2011) Tabu search based multi-watermarks embedding algorithm with multiple description coding. Inf Sci 181:3379–3396. https://doi.org/10.1016/j.ins.2011.04.007
Islam M, Roy A, Laskar RH (2018) Neural network based robust image watermarking technique in LWT domain. J Intell Fuzzy Syst 34:1691–1700. https://doi.org/10.3233/JIFS-169462
Jain AK, Prabhakar S, Hong L, Pankanti S (2000) Filterbank-based fingerprint matching. IEEE Trans Image Process 9:846–859
Kasana G, Kasana SS (2017) Reference based semi blind image watermarking scheme in wavelet domain. Optik 142:191–204
Kundur D, Hatzinakos D (2004) Toward robust logo watermarking using multiresolution image fusion principles. IEEE Trans Multimed 6:185–198. https://doi.org/10.1109/TMM.2003.819747
Lebcir M, Awang S, Benziane A (2020) Robust blind watermarking technique against geometric attacks for fingerprint image using DTCWT-DCT. Iraqi J Sci 61:2715–2739
Lin SD, Shie S-C, Guo JY (2010) Improving the robustness of DCT-based image watermarking against JPEG compression. Comput Stand Interfaces 32:54–60
Mansouri H, Pourreza H (2017) Extreme compression of fingerprint image databases using the model-based transform, signal. Image Video Process 11:1543–1550
Mehta R, Rajpal N, Vishwakarma VP (2016) LWT-QR decomposition based robust and efficient image watermarking scheme using Lagrangian SVR. Multimed Tools Appl 75(7):4129–4150
Mousavi SM, Naghsh A, Abu-Bakar SAR (2014) Watermarking techniques used in medical images: a survey. J Digit Imaging 27:714–729
Noore A, Singh R, Vatsa M, Houck MM (2007) Enhancing security of fingerprints through contextual biometric watermarking. Forensic Sci Int 169:188–194
Peralta D, Galar M, Triguero I, Paternain D, Garcia S, Barrenechea E, Benitez JM, Bustince H, Herrera F (2015) A survey on fingerprint minutiae-based local matching for verification and identification: taxonomy and experimental evaluation. Inf Sci (Ny) 315:67–87
Qadir G, Zhao X, Ho ATS (2010) Estimating JPEG2000 compression for image forensics using Benford’s Law. Optics, Photonics, Digital Technol Multimedia Appl:77230J. https://doi.org/10.1117/12.855085
Shih FY, Wu SYT (2003) Combinational image watermarking in the spatial and frequency domains. Pattern Recogn 36:969–975
Verma VS, Jha RK, Ojha A (2015) Digital watermark extrac- tion using support vector machine with principal component analysis based feature reduction. J Visual Comm Image Repres 31:75–85
Wang XY, Liu YN, Xu H, Wang AL, Yang HY (2016) Blind optimum detector for robust image watermarking in non-subsampled shearlet domain. Inf Sci 372:634–654
Zhao Y, Campisi P, Kundur D (2004) Dual domain watermarking for authentication and compression of cultural heritage images. IEEE Trans Image Process 13:430–448. https://doi.org/10.1109/TIP.2003.821552
Acknowledgments
The researcher would like to show gratitude to Universiti Malaysia Pahang (RDU vote number RDU180380) for supporting this study.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Lebcir, M., Awang, S. & Benziane, A. Robust blind watermarking approach against the compression for fingerprint image using 2D-DCT. Multimed Tools Appl 81, 20561–20583 (2022). https://doi.org/10.1007/s11042-022-12365-6
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-12365-6