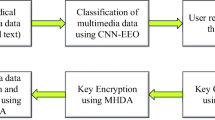
Abstract
Data is undoubtedly one of the most significant assets in the current competitive era and to ensure its value is retained, data safety emerges as a principle concern. Another technology asset is the cloud that is proficient in storing data at very little cost or even no cost at all. There are two main challenges that come with storing data in the cloud, safe storage of data and another is encryption of data with as little time and storage space as possible. These challenges have come in the way of various financial and government organizations tapping the benefits of the cloud. A two-step solution is illustrated in this research study in response to the raised issue. The initial part of this study discusses the classification of data into sensitive data and non-sensitive data. This is done to ensure that precious resources are used only to encrypt sensitive data and are not wasted on encryption data that doesn’t require encryption. To implement this, a mechanism based on Convolutional Neural Network with Logistic Regression(CNN-LR) is proposed. The next phase of this research work discusses the encryption method that is mainly focused on ensuring time and space complexity while encrypting data. For this, Ellipticcurve Diffie Hellman and Shifted Adaption Homomorphism Encryption (ECDH-SAHE) has been used and for decryption of data, Elliptic-curve DiffieHellman-Shifted Adaption Homomorphism Decryption (ECDH-SAHD) has been used. The proposed approach is titled Sensitive Encrypted Storage (SES). The results from the proposed methods are highly motivating and present great efficiency and capability which shall provide new dimension to the researchers in the future.












Similar content being viewed by others
References
Abdul-Mageed M, Diab M, Korayem M (2011) Subjectivity and sentiment analysis of modern standard arabic, pp 587–591
Almorsy M, Grundy J, Ibrahim A S (2011) Collaboration-based cloud computing security management framework. In: 2011 IEEE 4th international conference on cloud computing. IEEE, pp 364–371
Antonopoulos N, Gillam L (2010) Cloud computing. Springer
Arora R, Parashar A, Transforming C C I (2013) Secure user data in cloud computing using encryption algorithms. Int J Eng Res Appl 3(4):1922–1926
Balachandran L, Kirupananda A (2017) Online reviews evaluation system for higher education institution: an aspect based sentiment analysis tool. In: 2017 11th international conference on software, knowledge, information management and applications (SKIMA). IEEE, pp 1–7
Benkhelifa E, Welsh T, Tawalbeh L, Jararweh Y, Basalamah A (2015) User profiling for energy optimisation in mobile cloud computing. Procedia Comput Sci 52:1159–1165
Cao D, Ji R, Lin D, Li S (2016) Visual sentiment topic model based microblog image sentiment analysis. Multimed Tools Appl 75(15):8955–8968
Cao D, Ji R, Lin D, Li S (2016) Visual sentiment topic model based microblog image sentiment analysis. Multimed Tools Appl 75(15):8955–8968
Chauhan A, Gupta J (2017) A novel technique of cloud security based on hybrid encryption by blowfish and md5. In: 2017 4th International conference on signal processing, computing and control (ISPCC). IEEE, pp 349–355
Coppersmith D, Johnson D B, Matyas S M (1996) A proposed mode for triple-des encryption. IBM J Res Dev 40(2):253–262
Diwan V, Malhotra S, Jain R (2014) Cloud security solutions: Comparison among various cryptographic algorithms. IJARCSSE
Dreiseitl S, Ohno-Machado L (2002) Logistic regression and artificial neural network classification models: a methodology review. J Biomed Inf 35 (5-6):352–359
Elliott C (2004) Quantum cryptography. IEEE Secur Privacy 2 (4):57–61
Gardner M W, Dorling SR (1998) Artificial neural networks (the multilayer perceptron)—a review of applications in the atmospheric sciences. Atmosph Environ 32(14-15):2627–2636
Gehlot P, Biradar SR, Singh BP (2013) Implementation of modified twofish algorithm using 128 and 192-bit keys on vhdl. Int J Comput Appl 70(13)
Gitanjali K L (2019) A novel approach of sensitive data classification using convolution neural network and logistic regression
Guo G, Wang H, Bell D, Bi Y, Greer K (2003) Knn model-based approach in classification. In: OTM confederated international conferences” on the move to meaningful internet systems”. Springer, pp 986–996
Hagge M, von Hoffen M, Betzing J, Becker J (2017) Design and implementation of a toolkit for the aspect-based sentiment analysis of tweets, pp 379–387
Han Y, Brezany P, Janciak I (2009) Cloud-enabled scalable decision tree construction. Int Conf Semant Knowl Grid 0:128–135. https://doi.org/10.1109/SKG.2009.83
Kalpana G, Kumar P V, Aljawarneh S, Krishnaiah RV (2018) Shifted adaption homomorphism encryption for mobile and cloud learning. Comput Electr Eng 65:178–195
Li Y, Gai K, Qiu L, Qiu M, Zhao H (2016) Intelligent cryptography approach for secure distributed big data storage in cloud computing. Inf Sci 387. https://doi.org/10.1016/j.ins.2016.09.005
Li Y, Carriere K C (2013) Assessing goodness of fit of exponential random graph models. Int J Stat Probab 2(4):64
Li Y, Carriere K C (2013) Assessing goodness of fit of exponential random graph models. Int J Stat Probab 2(4):64
Liu B, Blasch E, Chen Y, Shen D, Chen G (2013) Scalable sentiment classification for big data analysis using naive bayes classifier. In: 2013 IEEE international conference on big data. IEEE, pp 99–104
Moghaddam F F, Yezdanpanah M, Khodadadi T, Ahmadi M, Eslami M (2014) Vdci: Variable data classification index to ensure data protection in cloud computing environments. In: 2014 IEEE Conference on Systems, Process and Control (ICSPC 2014). IEEE, pp 53–57
Pannala N U, Nawarathna C P, Jayakody JTK, Rupasinghe L, Krishnadeva K (2016) Supervised learning based approach to aspect based sentiment analysis. In: 2016 IEEE International Conference on Computer and Information Technology (CIT). IEEE, pp 662–666
Pappas N, Popescu-Belis A (2014) Explaining the stars: Weighted multiple-instance learning for aspect-based sentiment analysis. In: Proceedings of the 2014 Conference on Empirical Methods In Natural Language Processing (EMNLP), pp 455–466
Prabhakar D MANOJ, Joseph K SURESH (2013) A new approach for providing data security and secure data transfer in cloud computing. International Journal of Computer Trends and Technology (IJCTT) pp 1202–120
Rewagad P, Pawar Y (2013) Use of digital signature with diffie hellman key exchange and aes encryption algorithm to enhance data security in cloud computing, pp 437–439
Sachdev A, Bhansali M (2013) Enhancing cloud computing security using aes algorithm. Int J Comput Appl 67(9)
Sengupta N (2013) Designing of cryptography based security system for cloud computing
Shaikh R, Mukundan S (2015) Data classification for achieving security in cloud computing. Procedia Comput Sci 45:493–498. https://doi.org/10.1016/j.procs.2015.03.087
Shrestha P, Saxena N (2018) Listening watch: Wearable two-factor authentication using speech signals resilient to near-far attacks. In: Proceedings of the 11th ACM conference on security & privacy in wireless and mobile networks, pp 99–110
Singh Sehra S, Singh J, et al. (2013) Policy specification in role based access control on clouds, pp arXiv–1308
Socher R, Perelygin A, Wu J, Chuang J, Manning C D, Ng A Y, Potts C (2013) Recursive deep models for semantic compositionality over a sentiment treebank. In: Proceedings of the 2013 conference on empirical methods in natural language processing, pp 1631–1642
Somani U, Lakhani K, Mundra M (2010) Implementing digital signature with rsa encryption algorithm to enhance the data security of cloud in cloud computing. In: 2010 first international conference On parallel, distributed and grid computing (PDGC 2010). IEEE, pp 211–216
Sood S (2012) A combined approach to ensure data security in cloud computing. J Netw Comput Appl 35:1831–1838. https://doi.org/10.1016/j.jnca.2012.07.007
Soutar C, Roberge D, Stoianov A, Gilroy R, Kumar BVKV (1999) Biometric encryption. In: ICSA guide to Cryptography, vol 22. McGraw-Hill
Turney P D (2002) Thumbs up or thumbs down? semantic orientation applied to unsupervised classification of reviews. arXiv:cs/0212032
Zardari M A, Jung L T (2015) Data classification with k-nn using novel character frequency-direct word frequency (cf-dwf) similarity formula. In: 2015 International Symposium on Mathematical Sciences and Computing Research (iSMSC). IEEE, pp 280–285
Zardari M A, Jung L T, Zakaria N (2014) K-nn classifier for data confidentiality in cloud computing. In: 2014 International Conference on Computer and Information Sciences (ICCOINS). IEEE, pp 1–6
Zhou X, Tang X (2011) Research and implementation of rsa algorithm for encryption and decryption. In: Proceedings of 2011 6th international forum on strategic technology, vol 2. IEEE, pp 1118–1121
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Gupta, G., Lakhwani, K. An enhanced approach to improve the encryption of big data using intelligent classification technique. Multimed Tools Appl 81, 25171–25204 (2022). https://doi.org/10.1007/s11042-022-12401-5
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-12401-5