Abstract
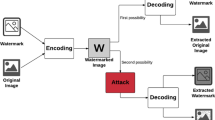
The present era is paving huge expansion to the transmission of digital data in fields like health, military intelligence, scientific research, and publication media, etc. The nature of digital data makes it more vulnerable to various intentional and unintentional attacks and hence increases the necessity of verifying its integrity and authenticity. In this paper, a novel image watermarking method for tamper detection and recovery of color images has been proposed. The color image is primarily separated into three planes, and then each plane is divided into four equal halves. We sub-divide each half into 4 × 4 non-overlapping blocks. Further, from a group of four corresponding sub-blocks, a 32-bit watermark comprising of the arithmetic mean value along with the 8-bit data containing the location of the mapped block is generated. This 32-bit generated watermark is embedded into the two least significant bits (LSB) of the mapped block after being encrypted using gray code. The information is embedded in such a way using chaotic sequence such that a full restoration process can be carried out, even if 75% of blocks in any of the three planes get tampered with. This method obtains a high-quality restored image with an average PSNR value of 39.22 dB for the RGB model and 39.37 dB for the YCbCr model. The performance of the proposed method for various collage attacks shows its efficacy over other state-of-art techniques, making it a suitable candidate for the recovery of tampered color images.


















Similar content being viewed by others
References
Alsmirat AM, Alem FA, Ayyoub MA, Jararweh Y, Gupta BB (2019) Impact of digital fingerprint image quality on the fingerprint recognition accuracy. Multimed Tools Appl 78:3649–3688. https://doi.org/10.1007/s11042-017-5537-5
Anand A, Singh AK (2020) An improved DWT-SVD domain watermarking for medical information security. Comput Commun 152:72–80. https://doi.org/10.1016/j.comcom.2020.01.038
Ansari IA, Pant M, Ahn CW (2015) SVD based fragile watermarking scheme for tamper localization and self-recovery. Int J Mach Learn Cybern 7(6):1225–1239
Azeroual A, Karim A (2017) Real-time image tamper localization based on fragile watermarking and Faber-Schauder wavelet. AEU-Int J Electron Commun 79:207–218
Bhalerao S, Ansari IA, Kumar AA (2020) Secure image watermarking for tamper detection and localization. J Ambient Intell Humaniz Comput 12:1057–1068. https://doi.org/10.1007/s12652-020-02135-3
Rogelio RR, Cruz-Ramos C, Ponomarvoy V, Garcia-Salgado BP et al., (2021) Color image self recovery and tampering detection scheme based on fragile watermarking with high recovery capability. Applies Sciences, 11(7): 3189
Bravo SS, Calderon F, Li TC, Nandi AK (2020) Fast fragile watermark embedding and iterative mechanism with high self-restoration performance. Digital Signal Processing 73:83–92
Cao F et al (2017) Hierarchical recovery for tampered images based on watermark self-embedding. Displays 46:52–60
Chamlawi R, Khan A, Usman I (2010) Authentication and recovery of images using multiple watermarks. Comput Electr Eng 36(3):578–584
Dadkhah S, Manaf AA, Sadeghi S (2014) An efficient image self-recovery and tamper detection using fragile watermarking. International Conference Image Analysis and Recognition. Springer, Cham, 504–513
Dadkhah S, Abd Manaf A, Hori Y, Ella Hassanien A, Sadeghi S (2014) An effective SVD-based image tampering detection and self-recovery using active watermarking. Signal Process Image Commun 29(10):1197–1210
Fan MQ, Wang HX (2018) An enhanced fragile watermarking scheme to digital image protection and self-recovery. Signal Process Image Commun 66:19–29
Feng B, Li X, Jie Y, Guo C, Fu H (2020) A novel semi-fragile digital watermarking scheme for scrambled image authentication and restoration. Mobile Netw Appl 25:82–94. https://doi.org/10.1007/s11036-018-1186-9
Gull S, Parah SA, Khan M (2020) Reversible data hiding exploiting Huffman encoding with dual images for IoMT based healthcare. Comput Commun 163:134–149
Gull S, Loan NA, Parah SA, Sheikh JA, Bhat GM (2020) An efficient watermarking technique for tamper detection and localization of medical images. J Ambient Intell Humaniz Comput 11(5):1799–1808
Gull S, Mansour RF, Aljehane NO, Parah SA (2021) A self-embedding technique for tamper detection and localization of medical images for smart-health. Multimed Tools Appl 80(19):29939–29964
Hassan FS, Gutub AA (2021) Improving data hiding within colour images using hue component of HSV colour space. CAAI Trans Intell Technol 7:56–68. https://doi.org/10.1049/cit2.12053
He H, Chen F, Tai HM, Kalker T, Zhang J (2011) Performance analysis of a block-neighborhood-based self-recovery fragile watermarking scheme. IEEE Trans Inf Forensics Secur 7(1):185–196
Huang SC, Jiang CF (2012) A color image authentication and recovery method using block truncation code embedding. J Mar Sci Technol 20(1):49–55
Hurrah NN, Parah SA, Loan NA, Sheikh JA, Elhoseny M, Muhammad K (2018) Dual watermarking framework for privacy protection and content authentication of multimedia. Futur Gener Comput Syst 94:654–673. https://doi.org/10.1016/j.future02018.12.036
Hurrah NN, Parah SA, Sheikh JA (2020) Embedding in medical images: an efficient scheme for authentication and tamper localization. Multimed Tools Appl 79:21441–21470. https://doi.org/10.1007/s11042-020-08988-2
Hussan M et al (2021) Tamper detection and self-recovery of medical imagery for smart health. Arab J Sci Eng:1–17. https://doi.org/10.1007/s13369-020-05135-9AJSE-D-20-03588R1
Kabir MA (2021) An efficient low bit rate image watermarking and tamper detection for image authentication. SN Appl Sci 3:400. https://doi.org/10.1007/s42452-021-04387-w
Kiatpapan S, Kondo T (2015) An image tamper detection and recovery method based on self-embedding dual watermarking. 2015 12th International Conference on Electrical Engineering/Electronics, Computer, Telecommunications and Information Technology (ECTI-CON). IEEE, 1–6
Kishore RR (2020) A novel and efficient blind domain image watermarking in transform domain. Procedia Comput Sci 167:1505–1514
Kodak image dataset is available on http://r0k.us/graphics/kodak. Accessed 7 June 2021
Korus P, Dziech A (2012) Efficient method for content reconstruction with self-embedding. IEEE Trans Image Process 22(3):1134–1147
Korus P, Dziech A (2013) Adaptive self-embedding scheme with controlled reconstruction performance. IEEE Trans Inf Forensics Secur 9(2):169–181
Kumar A, Ghrera SP, Tyagi V (2017) An ID-based secure and flexible buyer-seller watermarking protocol for copyright protection.
UCID Image Dataset is available on http://homepages.lboro.ac.uk/cogs/datasets/ucid/data/ucid.v2.tar.gz. Accessed 24 Aug 2020
Lee TY, Shinfeng DL (2008) Dual watermark for image tamper detection and recovery. Pattern Recogn 41(11):3497–3506
Li Y, Song W, Zhao X, Wang J, Zhao L (2019) A novel image tamper detection and self-recovery algorithm based on watermarking and chaotic system. Mathematics 7:955. https://doi.org/10.3390/math7100955
Lin ET, Christine IP, Edward JD (2000) Detection of image alterations using semifragile watermarks. Security and Watermarking of Multimedia Contents II (Vol. 3971, pp. 152-163). International Society for Optics and Photonics
Lin PL, Chung KH, Po WH (2005) A hierarchical digital watermarking method for image tamper detection and recovery. Pattern Recogn 38(12):2519–2529
Loan NA, Hurrah NN, Parah SA, Lee JW, Sheikh JA, Bhat GM (2018) Secure and robust digital image watermarking using coefficient differencing and chaotic encryption. IEEE Access 6:19876–19897
Mehta R, Rajpal N, Virendra PV (2018) Robust image watermarking scheme in lifting wavelet domain using GA-LSVR hybridization. Int J Mach Learn Cybern 9(1):145–161
Molina GJ et al (2020) An effective fragile watermarking scheme for color image tampering detection and self-recovery. Signal Process Image Commun 81:115725
Mustafa M, Mustafa G, Parah SA, Sheikh JA (2010) Field programmable gate array (FPGA) implementation of novel complex PN-code-generator-based data scrambler and descrambler. Maejo Int J Sci Technol 4:125–135
Parah SA, Bhat GM, Sheikh JA (2014) A secure and efficient data hiding technique based on pixel adjustment. Am J Eng Technol Res 14:38–44
Patra B, Patra JC (2012) Crt-based fragile self-recovery watermarking scheme for image authentication and recovery. 2012 international symposium on intelligent signal processing and communications systems. IEEE, 430–435
Prasad S, Pal AK (2020) A tamper detection suitable fragile watermarking scheme based on novel payload embedding strategy. Multimed Tools Appl 79:1673–1705. https://doi.org/10.1007/s11042-019-08144-5
Qi X, Xin XA (2015) Singular-value-based semi-fragile watermarking scheme for image content authentication with tamper localization. J Visual Commun 30:312–327
Qian Z, Feng G, Zhang X, Wang S (2011) Image self-embedding with high-quality restoration capability. Digit Signal Process 21(2):278–286
Rajput V, Ansari IA (2019) Image tamper detection and self-recovery using multiple median watermarking. Multimed Tools Appl 79(47):35519–35535. https://doi.org/10.1007/s11042-019-07971-w
Saeed S, Mohammad AA (2015) A source-channel coding approach to digital image protection and self-recovery. IEEE Trans Image Process 24(7):2266–2277
Sahu AK (2021) A logistic map based blind and fragile watermarking for tamper detection and localization in images. J Ambient Intell Humaniz Comput. https://doi.org/10.1007/s12652-021-03365-9
Sarreshtedari S, Akhaee MA (2015) A Source-Channel coding approach to digital image protection and self-recovery. IEEE Trans Image Process 24:2266–2277
Shivendra S, Singh D, Agarwal S (2013) DCT based approach for tampered image detection and recovery using block wise fragile watermarking scheme. Iberian Conference on Pattern Recognition and Image Analysis. Springer, Berlin, Heidelberg, 640–647
Singh D, Singh SK (2017) DCT based efficient fragile watermarking scheme for image authentication and restoration. Multimed Tools Appl 76(1):953–977
Stergiou CL, Psannis KE, Gupta BB (1 April1, 2021) IoT-Based Big Data Secure Management in the Fog Over a 6G Wireless Network. IEEE Internet Things J 8(7):5164–5171. https://doi.org/10.1109/JIOT.2020.3033131
Tai WW, Zi JL (2018) Image self-recovery with watermark self-embedding. Signal Process Image Commun 65:11–25
Tong X, Liu Y, Zhang M, Chen Y (2013) A novel chaos-based fragile watermarking for image tampering detection and self-recovery. Signal Process Image Commun 28(3):301–308
Yu C, Li J, Li X, Ren X, Gupta BB (2018) Four-image encryption scheme based on quaternion Fresnel transform, chaos and computer generated hologram. Multimed Tools Appl 77:4585–4608. https://doi.org/10.1007/s11042-017-4637-6
Zhang X, Xiao Y, Zhao Z (2015) Self-embedding fragile watermarking based on DCT and fast fractal coding. Multimed Tools Appl 74(15):5767–5786
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
• The authors have no relevant financial or non-financial interests to disclose.
• The authors have no competing interests to declare that are relevant to the content of this article.
• All authors certify that they have no affiliations with or involvement in any organization or entity with any financial interest or non-financial interest in the subject matter or materials discussed in this manuscript.
• The authors have no financial or proprietary interests in any material discussed in this article.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Hussan, M., Parah, S.A., Jan, A. et al. Self-embedding framework for tamper detection and restoration of color images. Multimed Tools Appl 81, 18563–18594 (2022). https://doi.org/10.1007/s11042-022-12545-4
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-12545-4