Abstract
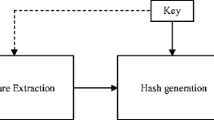
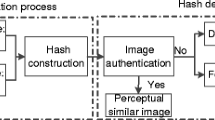
Perceptual image hashing methods utilize the visual phenomenon of the images and produce a fixed-length hash function and this hash value can be utilized for digital signature of an image. It can be used to show robustness against the digital manipulations done on the image and hence can be of use in different applications, viz., image indexing, tamper detection, etc. But to generate an efficient hash function is scarce as there is an inverse relationship of perceptual robustness and discrimination capability criteria. In this paper, we propose a robust and discrimination capable hash function by considering KAZE point feature descriptor for combinatorial manipulations. The KAZE detectors are used to find the stable key points of the image and then the three strongest regions are considered based on the strongest three key points of the image. Using these points, the features are generated and finally, the local features are used to generate the hash function and this hash function not only provides a good discrimination capable value with good robustness but also shows good results for double attacks and multiple combinations of attacks. Moreover, it outperforms the state-of-the-art algorithms in consideration for performances between discrimination capability and perceptual robustness.













Similar content being viewed by others
Code Availability
Not applicable
References
https://www.petitcolas.net/watermarking/image_database/, Accessed: 2019 June
https://homepages.cae.wisc.edu/~ece533/images/, Accessed: 2019 June
Ahmed F, Siyal M Y, Abbas V U (2010) A secure and robust hash-based scheme for image authentication. Signal Process 90(5):1456–1470
Alcantarilla P F, Bartoli A, Davison A J (2012) Kaze features. In: European conference on computer vision. Springer, pp 214–227
Choi Y S, Park J H (2012) Image hash generation method using hierarchical histogram. Multimed Tools Appl 61(1):181–194
Christoph Z (2010) Implementation and benchmarking of perceptual image hash functions. In: Upper Austria University of Applied Sciences. Hagenberg Campus
Du L, Chen Z, Ho ATS (2020) Binary multi-view perceptual hashing for image authentication. Multimed Tools Appl:1–23
Fridrich J, Goljan M (2000) Robust hash functions for digital watermarking. In: International conference on information technology: coding and computing. IEEE, pp 178–183
Gharde N D, Thounaojam D M, Soni B, Biswas S K (2018) Robust perceptual image hashing using fuzzy color histogram. Multimed Tools Appl 77(23):30815–30840
Hamid H, Ahmed F, Ahmad J (2020) Robust image hashing scheme using laplacian pyramids. Comput Electr Eng 84:106648
Harris C G, Stephens M, et al. (1988) A combined corner and edge detector. In: Alvey vision conference, vol 15. Citeseer, pp 10–5244
Hassan E, Chaudhury S, Gopal M (2012) Feature combination in kernel space for distance based image hashing. IEEE Trans Multimed 14(4):1179–1195
Hernandez R A P, Miyatake M N, Kurkoski B M (2011) Robust image hashing using image normalization and svd decomposition. In: International midwest symposium on circuits and systems. IEEE, pp 1–4
Hong W, Chang Y-T, Qin H, Hung W-C, Tsai Y-H, Yang M-H (2020) Image hashing via linear discriminant learning. In: Proceedings of the IEEE/CVF winter conference on applications of computer vision, pp 2531–2539
Huang Z, Liu S (2020) Perceptual image hashing with texture and invariant vector distance for copy detection. IEEE Transactions on Multimedia
Jie Z (2013) A novel block-dct and pca based image perceptual hashing algorithm. arXiv:1306.4079
Karsh R K, Saikia A, Laskar R H (2018) Image authentication based on robust image hashing with geometric correction. Multimed Tools Appl 77 (19):25409–25429
Khelaifi F, He H (2020) Perceptual image hashing based on structural fractal features of image coding and ring partition. Multimed Tools Appl:1–20
Lefebvre F, Macq B, Legat J-D (2002) Rash: Radon soft hash algorithm. In: European Signal Processing Conference. IEEE, pp 1–4
Leutenegger S, Chli M, Siegwart R Y (2011) Brisk: Binary robust invariant scalable keypoints. In: International conference on computer vision. IEEE, pp 2548–2555
Neelima A, Singh K M (2016) Perceptual hash function based on scale-invariant feature transform and singular value decomposition. Comput J 59 (9):1275–1281
Olmos A, Kingdom FAA (2004) A biologically inspired algorithm for the recovery of shading and reflectance images. Perception 33(12):1463–1473
Patil V, Sarode T K (2019) Image hashing using dwt-cslbp. JCP 14(3):210–222
Qin C, Hu Y, Yao H, Duan X, Gao L (2019) Perceptual image hashing based on weber local binary pattern and color angle representation. IEEE Access 7:45460–45471
Rosten E, Drummond T (2005) Fusing points and lines for high performance tracking. In: International Conference on Computer Vision (ICCV’05) Volume 1, vol 2. IEEE, pp 1508–1515
Sajjad M, Haq I U, Lloret J, Ding W, Muhammad K (2019) Robust image hashing based efficient authentication for smart industrial environment. IEEE Trans Ind Inf 15(12):6541–6550
Singh K M, Neelima A, Tuithung T, Singh K M (2019) Robust perceptual image hashing using sift and svd. Curr Sci 117(8):1340
Slaney M, Casey M (2008) Locality-sensitive hashing for finding nearest neighbors [lecture notes]. IEEE Signal Process Mag 25(2):128–131
Tang Z, Dai Y, Zhang X, Huang L, Yang F (2013) Robust image hashing via colour vector angles and discrete wavelet transform. IET Image Process 8(3):142–149
Tang Z, Wang S, Zhang X, Wei W, Su S (2008) Robust image hashing for tamper detection using non-negative matrix factorization. J Ubiquit Conver Technol 2(1):pp–18
Tang Z, Yang F, Huang L, Zhang X (2014) Robust image hashing with dominant dct coefficients. Optik 125(18):5102–5107
Tang Z, Zhang X, Dai X, Yang J, Wu T (2013) Robust image hash function using local color features. AEU-Int J Electron Commun 67 (8):717–722
Tang Z, Zhang X, Huang L, Dai Y (2013) Robust image hashing using ring-based entropies. Signal Process 93(7):2061–2069
Tang Z, Zhang X, Li X, Zhang S (2015) Robust image hashing with ring partition and invariant vector distance. IEEE Trans Inf Forensic Secur 11 (1):200–214
Tang Z, Zhang X, Zhang S (2013) Robust perceptual image hashing based on ring partition and nmf. IEEE Trans Knowl Data Eng 26(3):711–724
Tang ZJ, Zhang XQ, Dai YM, Lan WW (2013) Perceptual image hashing using local entropies and dwt. The Imaging Sci J 61(2):241–251
Wang X, Zhou X, Zhang Q, Xu B, Xue J (2020) Image alignment based perceptual image hash for content authentication. Signal Process Image Commun 80:115642
Weber A G (2018) The usc-sipi image database version 6. USC-SIPI Report 432:1–24
Weng L, Preneel B (2009) Shape-based features for image hashing. In: International Conference on Multimedia and Expo. IEEE, pp 1074–1077
Xiang S, Kim H-J, Huang J (2007) Histogram-based image hashing scheme robust against geometric deformations. In: Proceedings of the 9th workshop on Multimedia & security. ACM, pp 121–128
Xue M, Yuan C, Liu Z, Wang J (2019) Ssl: A novel image hashing technique using sift keypoints with saliency detection and lbp feature extraction against combinatorial manipulations. Security and Communication Networks
Yang B, Gu F, Niu X (2006) Block mean value based image perceptual hashing. In: International conference on intelligent information hiding and multimedia. IEEE, pp 167–172
Zhao Y, Wang S, Zhang X, Yao H (2012) Robust hashing for image authentication using zernike moments and local features. IEEE Trans Inf Forensic Secur 8(1):55–63
Zhao Y, Yuan X (2020) Perceptual image hashing based on color structure and intensity gradient. IEEE Access 8:26041–26053
Funding
This study has not received any funding
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of Interests
The authors declare that they have no conflict of interest.
Additional information
Availability of Data and Material
The datasets used to support the findings of this study are available from the public repositories mentioned in the manuscript- [1, 2, 38]
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Roy, M., Thounaojam, D.M. & Pal, S. Perceptual hashing scheme using KAZE feature descriptors for combinatorial manipulations. Multimed Tools Appl 81, 29045–29073 (2022). https://doi.org/10.1007/s11042-022-12626-4
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-12626-4