Abstract
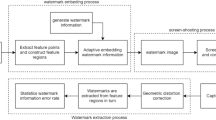
This paper proposes a new watermarking scheme that is screen-shooting resilient. We try to design a watermarking scheme that can resist the distortion generated during the screen-shooting process while has a good invisibility. While embedding, we utilize the stability of the singular value matrix in terms of sign invariance to improve the robustness of our watermarking scheme. We use scale-invariant feature transform (SIFT) algorithm to help with locating different embedding regions to embed repeatedly to further improve robustness. While extracting, we located more regions compared with embedding process to enhance the error-tolerant rate. Compared with the previous method, our watermarking scheme has a larger embedding capacity while performing better in terms of robustness and invisibility.








Similar content being viewed by others
References
Arora M, Kumar M (2021) AutoFER: PCA and PSO based automatic facial emotion recognition. Multimed Tools Appl 80(2):3039–3049
Bansal M, Kumar M, Kumar M (2020) 2D Object recognition techniques: state-of-the-art work. Archives of Computational Methods in Engineering, 1-15
Bansal M, Kumar M, Kumar M et al (2021) An efficient technique for object recognition using Shi-Tomasi corner detection algorithm. Soft Comput 25 (6):4423–4432
Barni M, Bartolini F, Cappellini V, et al. (1998) A DCT-domain system for robust image watermarking. Signal processing, 1998 66(3):357–372
Chandra DVS (2002) Digital image watermarking using singular value decomposition
Chang CC, Tsai P, Lin CC (2005) SVD-Based digital image watermarking scheme. Pattern Recogn Lett 26(10):1577–1586
Chhabra P, Garg NK, Kumar M (2020) Content-based image retrieval system using ORB and SIFT features. Neural Comput & Applic 32(7):2725–2733
Chu WC (2003) DCT-Based image watermarking using subsampling. IEEE Transactions on Multimedia 5(1):34–38. https://doi.org/10.1109/TMM.2003.808816
Chung KL, Yang WN, Huang YH, Wu ST, Hsu YC (2007) On SVD-based watermarking algorithm. Appl Math Comput, 54–57
Ganic E, Eskicioglu AM (2004) Robust DWT-SVD domain image watermarking: embedding data in all frequencies. In: Proceedings of the 2004 workshop on multimedia and security, vol 2004, pp 166–174
Gupta S, Kumar M (2020) Forensic document examination system using boosting and bagging methodologies. Soft Comput 24(7):5409–5426
Gupta S, Mohan. N, Kumar M (2020) A Study on Source Device Attribution Using Still Images. Arch Computat Methods Eng
Hai T, Li CM, Zain JM, Abdalla AN (2014) Robust Image watermarking theories and techniques: A review. J Appl Res Technol 12(1):122–138
Han F, Zhang WM, Zhou H et al (2018) Screen-shooting resilient watermarking. IEEE Transactions on Information Forensics and Security 14(6):1403–1418
Hsu CT, Wu JL (1999) Hidden Digital watermarks in images. IEEE Trans Image Process 8(1):58–68. https://doi.org/10.1109/83.736686
Kang X, Huang J, Zeng W (2010) Efficient General print-scanning resilient data hiding based on uniform log-polar mapping. IEEE Transactions on Information Forensics and Security 5(1):1–12
Kaur RP, Jindal MK, Kumar M (2020) Text and graphics segmentation of newspapers printed in Gurmukhi script: a hybrid approach. Vis Comput, 1–23
Kumar M, Chhabra P, Garg NK (2018) An efficient content based image retrieval system using BayesNet and k-NN. Multimed Tools Appl 77 (16):21557–21570
Kumar M, Kumar M (2021) XGBOost: 2D-Object Recognition Using Shape Descriptors and Extreme Gradient Boosting Classifier. Computational Methods and Data Engineering. Springer, Singapore, pp 207–222
Kumar A, Kumar M, Kaur A (2021) Face detection in still images under occlusion and non-uniform illumination. Multimed Tools Appl 80(10):14565–14590
Liu RZ, Tan TN (2002) An SVD-based watermarking scheme for protecting rightful ownership. IEEE Transactions on Multimedia 4(1):121–128
Liu X, Wang Y, Du J, et al. (2019) Robust hybrid image watermarking scheme based on KAZE features and IWT-SVD. Multimed Tools Appl 78 (5):6355–6384
Lowe DG (1999) Object recognition from local scale-invariant features. Proceedings of the seventh. IEEE International Conference on Computer Vision. Ieee 1999(2):1150–1157
Lowe DG (2004) (2004) Distinctive Image features from scale-invariant keypoints. Int J Comput Vis 60(2):91–110
Mezirow J (1978) Perspective transformation. Adult Education 28 (2):100–110
Poonam ASM (2018) A DWT-SVD based Robust Digital Watermarking for Digital Images. Procedia Computer Science, 1441–1448, vol 132
Premaratne P, Ko CC (1999) A novel watermark embedding and detection scheme for images in DFT domain. In: 7th international conference on image processing and its applications, vol 1999, pp 780–783
Prins JP, Erkin Z, Lagendijk RL (2007) Anonymous fingerprinting with robust QIM watermarking techniques. EURASIP Journal on Information Security, 2007 2007(1):031340
Raval MS, Rege PP (2003) Discrete wavelet transform based multiple watermarking scheme. TENCON 2003. Conference on Convergent Technologies for Asia-Pacific Region IEEE 2003(3):935–938
Tao PN, Eskicioglu AM (2004) A robust multiple watermarking scheme in the discrete wavelet transform domain. Internet Multimedia Management Systems V. International Society for Optics and Photonics 2004(5601):133–144
Tirkel AZ, Rankin GA, Schyndel RMV, Ho WJ, Mee NRA, Osborne CF (1993) Electronic Watermark. Digital Image Computing. Technology and Applications (DICTA’93), 666–673
Urvoy M, Goudia D, Autrusseau F (2014) Perceptual DFT watermarking with improved detection and robustness to geometrical distortions. IEEE Transactions on Information Forensics and Security 9(7):1108–1119
Wengrowski E, Dana K (2019) Light field messaging with deep photographic steganography. In: Proceedings of the IEEE conference on computer vision and pattern recognition, vol 2019, pp 1515–1524
Wolfgang RB, Delp IIIEJ (1999) Fragile watermarking using the VW2d watermark. Security and Watermarking of Multimedia Contents. International Society for Optics and Photonics 1999(3657):204–213
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Deng, B., Li, S. & Qian, Z. An SVD-based screen-shooting resilient watermarking scheme. Multimed Tools Appl 81, 32841–32855 (2022). https://doi.org/10.1007/s11042-022-12738-x
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-12738-x