Abstract
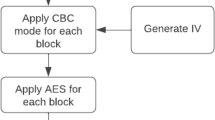
Recently, many image encryptions models have been proposed using elliptic curve cryptography and magic matrix. But with security being the highest priority while transferring sensitive information, models nowadays are required to withstand robust hacking without compromising on the speed of the system. This work proposes an image encryption scheme using a combination of elliptic curves, magic matrix, and AES (Advanced Encryption Standard) to provide greater security to the image encryption operation. The pixel intensity values of the image are first transformed by a substitution method utilizing elliptic curves. These pixels are subjected to another round of value transformation before being scrambled according to the magic matrix algorithm in the second stage of the encryption process. The scrambling process ensures position transformation of the pixels in the image. The last encryption stage uses the AES technique to generate a 128-bit key and encrypt the entire image in a block-by-block manner. This was done to provide an additional layer of security and obtain better results when compared to other encryption models. The proposed technique is simulated using MATLAB. After the process of image encryption and decryption, the model’s performance was assessed using parameters like mean square error, correlation coefficient, entropy, NPCR (Number of pixels change rate), and UACI (Unified average changing intensity).














Similar content being viewed by others
References
Abd-El-Hafiz SK, Radwan AG, Abdel Haleem SH, Barakat ML (2014) A fractal-based image encryption system. IET Image Process 8(12):742–752
Adam B (2013) Advanced encryption standard by example V. 1.5. AB Software development
Afify E, Khalil AT, El Sobky WI, Alez RA (May 2020) Performance analysis of advanced encryption standard (AES) S-boxes. Int J Recent Technol Eng (IJRTE) 9(1):2214–2218
AL-Hashemy RH, Mehdi SA (2019) A new algorithm based on Magic Square and a novel chaotic system for image encryption. J Intell Syst 29(1):1202–1215, Feb.
Amalarethinam DG, Geetha JS (Feb 2015) Image encryption and decryption in public key cryptography based on MR. IEEE International Conference on Computing and Communications Technologies (ICCCT), pp. 133–138, Chennai, India
Ankur K, Piyush K, Murtaza A, Shalini S (2016) An intelligent and fast chaotic encryption using digital logic circuits for ad-hoc and ubiquitous computing. Entropy 18:201
Aydos M, Yanik T, Kog CK (Oct 2001) High-speed implementation of an ECC based wireless authentication protocol on an ARM microprocessor. IEEE Proc Commun 148(5):273–279
Chen G, Bai G, Chen H (2007) A High-Performance Elliptic Curve Cryptographic Processor for General Curves Over GF(p) Based on a Systolic Arithmetic Unit. Trans Circuits Syst II: Express Briefs 54(5):412–416, May.
Chen J-X, Zhu Z-L, Fu C (2015) An efficient image encryption scheme using lookup table-based confusion and diffusion. Nonlinear Dynam 81(3):1151–1166
Cheng RCC, Telle NJ, Luk W, Cheung PYK (Sep 2005) Customizable Elliptic Curve Cryptosystems. IEEE Trans Very Large Scale Integr (VLSI) Syst 13(9):1048–1059
Cilardo A, Coppolino L (Feb. 2006) Nicola Mazzocca, and Luigi Romano," elliptic curve cryptography engineering". Proc IEEE 94(2):395–406
Elminaam DSA, Kader HMA, Hadhoud MM (2010) Evaluating the performance of symmetric encryption algorithms. Int J Netw Secur 10(3):213–219
Finnigin KM, Mullins BE, Raines RA, Potoczny HB (2006) Cryptanalysis of an elliptic curve cryptosystem for wireless sensor networks. Int J Secur Netw 2(3/4):260–271
Ganapathi G, Mani K (Oct 2009) Add on security model for public key Cryptosystem based on magic square implementation. Proceedings of the World Congress on Engineering and Computer Science (WCECS), Vol 1. San Francisco, USA
Guan ZH, Huang F, Guan W (Oct. 2005) Chaos-based image encryption algorithm. Physics Letter A 346:153–157
He P, Sun K, Zhu C (2021) A novel image encryption algorithm based on the delayed maps and permutation-confusion-diffusion architecture. Secur Commun Netw:Article ID 6679288
IEEE Standard Specifications for Public-Key Cryptography, Sponsor by Microprocessor and Microcomputer Standards Committee of the IEEE Computer Society, IEEE Std 1363–2000.
Jiao K, Pan C, Huang X (2018) An effective framework for chaotic image encryption based on 3D logistic map. Secur Commun Netw:Article ID 8402578
Khalane V, Suralkar S, Bhadade U (2020) Image encryption based on matrix factorization. Int J Safety Secur Eng 10(05):655–661
Lee J, Kim H, Lee Y, Hong S-M, Yoon H (Jan. 2007) Parallelized scalar multiplication on elliptic curves defined over optimal extension field. Int J Netw Secur 4(1):99–106
Loukhaoukha K, Chouinard J-Y, Berdai A (2012) A Secure Image Encryption Algorithm Based on Rubik's Cube Principle. J Electr Comput Eng:Article ID 173931
Lu CC, Tseng SY (2002) Integrated design of AES (Advanced Encryption Standard) encrypter and decrypter”, IEEE International Conference on Application-Specific Systems, Architectures, and Processors (ASAP’02), p 277–285
Manjula Y, Shiva Kumar KB (2020) Image security implementation and cryptanalysis using ECC cryptography, LSB-watermarking steganography. J Interdiscip Res 1(01):67–79
McIvor C, McLoone M, McCanny JV (2006) Hardware elliptic curve cryptographic processor over GF(p). IEEE Trans Circuits Syst I 53(9):1946–1957
Nadeem A, Javed M (2005) A performance comparison of data encryption algorithms. IEEE International Conference on Information and Communication Technologies, p 84–89
Shaktawat R, Shaktawat RS, Lakshmi N, Panwar A, Vaishnav A (2020) A hybrid technique of combining AES algorithm with block permutation for image encryption. Reliab: Theory Appl 15(1):51–56
Sharma P (2020) A new image encryption using modified AES algorithm and it’s comparison with AES. Int J Eng Res Technol 9(08):194–197
Stallings W (2006) Cryptography and network security, Prentice Hall, 4th edn
Tong XJ (2013) Design of an image encryption scheme based on a multiple chaotic map. Commun Nonlinear Sci Numer Simul 18(7):1725–1733
Wang X, Luan D (2013) A novel image encryption algorithm using chaos and reversible cellular automata. Commun Nonlinear Sci Numer Simul 18:3075–3085
Wu Y, Noonan JP, Agaian S (2011) NPCR and UACI Randomness Tests for Image Encryption. Multidiscip J Sci Technol, J Sel Areas Telecommun (JSAT), p 31–38
Zhang R, Xiao D (2020) A secure image permutation–substitution framework based on chaos and compressive sensing. Int J Distrib Sens Netw 16(3):1–11
Zhang Y, Xu P, Xiang L (2012) Research of image encryption algorithm based on chaotic magic square. Advances in Electronic Commerce, Web Application and Communication, Advances in Intelligent and Soft Computing, Vol 149. Springer, Berlin, p 103–109
Zhu C, Wang Z (2014) An Improved Piecewise Linear Chaotic Map Based Image Encryption Algorithm. Spec Issue Recent Adv Inf Technol, Sci World J 2014:Article ID 275818
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Authors declare that they have no financial or non-financial interests that are directly or indirectly related to the work submitted for publication.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Raju, D., Eleswarapu, L., Pranav, M.S. et al. Multi-level image security using elliptic curve and magic matrix with advanced encryption standard. Multimed Tools Appl 81, 37783–37803 (2022). https://doi.org/10.1007/s11042-022-12993-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-12993-y