Abstract
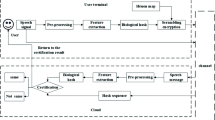
Most of the existing Biohashing authentication algorithms extract perception feature from the original domain and store the generated hashing sequence in the cloud, which can easily cause the hashing sequence to be leaked. At the same time, the algorithm’s robustness and matching accuracy under background noise are too low, leading to serious deviation in the authentication process. Therefore, this paper proposed an encrypted speech Biohashing authentication algorithm based on 4D hyperchaotic Bao system and feature fusion. Firstly, the algorithm encrypts the original speech by setting the key to the 4D hyperchaotic Bao system and transforms it into encrypted speech. Secondly, the preprocessed encrypted speech is processed by discrete wavelet transform (DWT) and spectral entropy to obtain the feature fusion matrix of the speech, and the pseudo-random matrix is generated by using two-dimensional Logistic ICMIC cascade mapping (2D-LICM). Then the feature fusion matrix and pseudo-random matrix are projected and mapped to construct the biometric template. Finally, the threshold is selected for binarization, and the Biohashing sequence is generated and uploaded to the cloud. In this way, a one-to-one correspondence is established between the encrypted speech and the hashing sequence. The experimental results show that the algorithm can directly extract the authentication digest from the encrypted speech. During the authentication process, the download and decryption of the speech data is not required, which improves the security of the hashing sequence storage. The encrypted speech can reduce the amplitude of signal change, has strong discrimination and robustness, and can resist complex background noise and has good real-time performance.
















Similar content being viewed by others
References
Bochen B, Liu Z, Xu JP (2009) New chaotic system and its hyperchaos generation. J Syst Eng Electron 20(6):1179–1187
Cao C, Sun KH, Liu W (2017) A novel bit-level image encryption algorithm based on 2d-licm hyperchaotic map. Signal Process 143:122–133
Chen N, Wan WG (2010) Robust speech hash function. ETRI J 32(2):345–347
Chen YZ, Wo Y, Xie R, Wu CD (2019) Deep secure quantization: On secure biometric hashing against similarity-based attacks - sciencedirect. Signal Process 154:314–323
Cornelius G, Gerard C, Nazim D, Nigel C (2017) Privacy preserving encrypted phonetic search of speech data. In: IEEE international conference on acoustics, pp 6414–6418
Gaurav D, Amandeep K (2019) Stoa: A bio-inspired based optimization algorithm for industrial engineering problems. Appl Artif Intell 82:148–174
Gaurav D, Vijay K (2018) Emperor penguin optimizer: A bio-inspired algorithm for engineering problems. Knowl-Based Syst 159:20–50
Ge S, Zhao S, li C, Li J (2018) Low-resolution face recognition in the wild via selective knowledge distillation. IEEE Trans Image Process 28 (4):2051–2062
He SF, Zhao H (2017) A retrieval algorithm of encrypted speech based on syllable-level perceptual hashing. Comput Sci Inform Syst 14(3):703–718
Huang YB, Hou HX, Wang Y, Zhang Y (2020) A long sequence speech perceptual hashing authentication algorithm based on constant q transform and tensor decomposition. IEEE Access 8:34140–34152
Huang YB, Wang Y, Zhang Q, Zhang WZ (2020) Multi-format speech biohashing based on spectrogram. Multimed Tools Appl 79 (33-34):24889–24909
Kang Q, Liu X, Yao Y, Wang Z, Li Y (2016) Efficient authentication and access control of message dissemination over vehicular ad hoc network. Neurocomputing 181:132–138
Kim HG, Cho HS, Kim JY (2016) Robust audio fingerprinting using peak-pair-based hash of non-repeating foreground audio in a real environment. Clust Comput 19(1):315–323
Kumar R, Gaurav D (2021) A comparative study of fuzzy optimization through fuzzy number. Int J Mod Res 1(1):1–14
Kumar P, Mukherjee S, Saini R, Kaushik P (2019) Multimodal gait recognition with inertial sensor data and video using evolutionary algorithm. IEEE Trans Fuzzy Syst 27(5):956–965
Kumar N, Rawat M (2020) Rp-lpp: A random permutation based locality preserving projection for cancelable biometric recognition. Multimed Tools Appl 79(12):2363–2381
Kumar SM, Sharma BB (2018) Control and synchronization of a class of uncertain fractional order chaotic systems via adaptive backstepping control. Asian Journal of Control 20(2):707–720
Leonov GA (2018) Lyapunov functions in the global analysis of chaotic systems. Ukr Math J 70:42–66
Li JF, Wang HX, Jing Y (2015) Audio perceptual hashing based on nmf and mdct coefficients. Chin J Electron 24(3):579–588
Li JF, Wu T, Wang H (2015) Perceptual hashing based on correlation coefficient of mfcc for speech authentication. J Beijing Univ Posts Telecommun 38 (2):89–93
Liao QH, Lüking M, Krüger DM, Deindl S (2019) Long time-scale atomistic simulations of the structure and dynamics of transcription factor-dna recognition. J Phys Chem B 123(17):3576–3590
Liu WH, Zhu CX, Sun K (2016) A fast image encryption algorithm based on chaotic map. Opt Lasers Eng 84:26–36
Mendelson A (2019) Security and privacy in the age of big data and machine learning. Computer 52(12):65–70
Mohamed H, Wang KQ (2019) Parallel score fusion of ecg and fingerprint for human authentication based on convolution neural network. Comput Secur 81:107–122
Ning-Chen HD, Zhu J, Lin J (2013) Xiao Robust audio hashing scheme based on cochleagram and cross recurrence analysis. Electron Lett 49(1):7–8
Peng L, Zhang J, Liu M, Hu A (2019) Deep learning based rf fingerprint identification using differential constellation trace figure. IEEE Trans Veh Technol 69(1):1091–1095
Prathosh AP, Ananthapadmanabha TV, Ramakrishnan AG (2013) Epoch extraction based on integrated linear prediction residual using plosion index. EEE Transactions on Audio Speech and Language Processing 21 (12):2471–2480
Qian Q, Wang HX, Sun X, Cui YH (2018) Speech authentication and content recovery scheme for security communication and storage. Telecommun Syst 67(4):635–649
Shadi A, Bani YM, Adel TW (2017) A resource-efficient encryption algorithm for multimedia big data. Multimed Tools Appl 76(21):22703–22724
Siniscalchi SM, Svendsen T, Lee CH (2014) An artificial neural network approach to automatic speech processing. Neurocomputing 140:326–338
Ullah S, Mumtaz Z, Liu S, Abubaqr M, Mahboob A, Madni HA (2019) Single-equipment with multiple-application for an automated robot-car control system. Sensors 19(3):662
Wang L, Li CR (2010) An improved speech endpoint detection method based on adaptive band-partition spectral entropy. Comput Simul 27(12):373–375
Wang Z, Guo L, Adjouadi M (2015) Wavelet decomposition and phase encoding of temporal signals using spiking neurons. Neurocomputing 173 (3):1203–1210
Zhang QY, Ge ZX, Zhou L, Zhang Y (2019) An efficient retrieval algorithm of encrypted speech based on inverse fast 2 fourier-transform and measurement matrix. Turk J Electr Eng Comput Sci 27(3):1719–1736
Zhang QY, Hu WJ, Huang Y, Qiao SB (2018) An efficient perceptual hashing based on improved spectral entropy for speech authentication. Multimed Tools Appl 77(2):1–27
Zhang YB, Mi BQ, Zhou L, Zhang T (2019) Speech perceptual hashing algorithm based on short-term auto-correlation for speech authentication. Radio Eng 49(10):899–904
Zhang QY, Qiao SB, Zhang T, Huang YB (2017) Perceptual hashing authentication algorithm for multi-format audio based on energy to zero ratio. Journal of Huazhong University of Science and Technology(Nature Science Edition) 45(9):33–38
Zhang QY, Qiao SB, Huang Y, Zhang T (2019) A high-performance speech perceptual hashing authentication algorithm based on discrete wavelet transform and measurement matrix. Multimed Tools Appl 77(16):21653–21669
Zhao S, Zhang B, Philip Chen CL (2019) Joint deep convolutional feature representation for hyperspectral palmprint recognition. Inf Sci 489:167–181
Zhang QY, Zhang T, Qiao S (2019) Spectrogram-based efficient perceptual hashing scheme for speech identification. Int J Netw Secur 21(2):259–268
Zhang QY, Zhou L, Zhang T, Zhang DH (2019) A retrieval algorithm of encrypted speech based on short-term cross-correlation and perceptual hashing. Multimed Tools Appl 78:17825–17846
Zheng Y, Cao Y, Chang CH (2018) Facial biohashing based user-device physical unclonable function for bring your own device security. In: 2018 ieee international conference on consumer electronics (ICCE).
Zhou ZY, Zhou Y, Philip-Chen CL (2013) A new series-wound framework for generating 1d chaotic maps. In: 2013 IEEE digital signal processing and signal processing education meeting (DSP/SPE)
Zhou L, Rodrigues J (2019) Honggang-wang, and Maria-G-Martini. 5g multimedia communications: theory, technology, and application. IEEE MultiMedia 26(1):8–9
Acknowledgments
This work is supported by the National Natural Science Foundation of China (No.61862041), Youth Science and Technology Fund of Gansu Province of China(No.21JR7RA120).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of Interests
The authors declare that they have no conflict of interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Chen, Tf., Huang, Yb., Pu, Xr. et al. Encrypted speech Biohashing authentication algorithm based on 4D hyperchaotic Bao system and feature fusion. Multimed Tools Appl 82, 16767–16792 (2023). https://doi.org/10.1007/s11042-022-13933-6
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-13933-6