Abstract
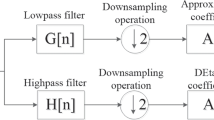
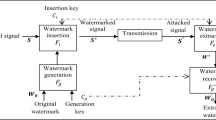
Accurate tamper localization is one of the most challenging problems in semi-fragile watermarking authentication schemes. The existing semi-fragile watermarking methods have some problems, such as blurred localization shape and high false alarm rate, which stem from the rough analysis of tampering information. To address these problems, this paper proposes a semi-fragile watermarking tamper localization method based on quaternion discrete Fourier transform (QDFT) and multi-view fusion, which embeds two watermarks in the QDFT domain for robust resistance to the geometric attack and integrity protection of host image, respectively. On the receiver side, considering that the difference map in binary mode is difficult to identify tampering, the global information and local smoothing cues are used in the method, to obtain the multi-scale candidate maps with real values instead of binary. Then, local adaptive fusion is accomplished by minimizing the energy function, to obtain a more consistent single tampering map. The design of the energy function integrates the image content and multi-scale feature views. Finally, a tamper seed-based propagation strategy is designed to generate a binary map of the tampered regions. Experimental results show that the proposed method provides better resistant to signal processing attacks, and the Fmeasure value of tamper localization is improved by 11.17% on average compared to the state-of-the-art methods.











Similar content being viewed by others
Data availability
The datasets that support the conclusions of this paper are cited in the article. These datasets were derived from the following public domain resources: http://forensics.idealtest.org/; http://pkorus.pl/downloads/dataset-realistic-tampering; http://sipi.usc.edu/database/.
References
Ahmadi M, Norouzi A, Karimi N, Samavi S, Emami A (2020) ReDMark: Framework for residual diffusion watermarking based on deep networks. Expert Syst Appl 146:113157
Al-Mualla ME (2007) Content-Adaptive Semi-Fragile Watermarking for Image Authentication," In: 2007 14th IEEE international conference on electronics, Circuits and Systems, pp. 1256–1259
Al-Otum HM (2014) Semi-fragile watermarking for grayscale image authentication and tamper detection based on an adjusted expanded-bit multiscale quantization-based technique. J Vis Commun Image Represent 25(5):1064–1081
Balasamy K, Ramakrishnan S (2018) An intelligent reversible watermarking system for authenticating medical images using wavelet and PSO. Clust Comput 22(S2):4431–4442
Bappy JH, Simons C, Nataraj L, Manjunath BS, Roy-Chowdhury AK (Jul, 2019) Hybrid LSTM and encoder-decoder architecture for detection of image forgeries. IEEE Trans Image Process 28(7):3286–3300
Benrhouma O, Hermassi H, Belghith S (2014) Tamper detection and self-recovery scheme by DWT watermarking. Nonlinear Dynamics 79(3):1817–1833
Bhatti UA, Yuan L, Yu Z, Li J, Nawaz SA, Mehmood A, Zhang K (2021) New watermarking algorithm utilizing quaternion Fourier transform with advanced scrambling and secure encryption. Multimed Tools Appl 80(9):13367–13387
Biswas S, Das SR, Petriu EM (2005) An adaptive compressed MPEG-2 video watermarking scheme. IEEE Trans Instrum Meas 54(5):1853–1861
Bolourian Haghighi B, Taherinia AH, Monsefi R (2020) An effective semi-fragile watermarking method for image authentication based on lifting wavelet transform and feed-forward neural network. Cogn Comput 12(4):863–890
Bolourian Haghighi B, Taherinia AH, Harati A, Rouhani M (2021) WSMN: An optimized multipurpose blind watermarking in Shearlet domain using MLP and NSGA-II. Appl Soft Comput 101:107029
CASIA (2017) Available: http://forensics.idealtest.org/. Accessed 28 Dec 2017
Chakravarthy S, Jagannathan MA, Ranjani JJ, Baluswamy B, Kadry S (2019) An optimized hierarchical encryption technique for tamper recognition. Multimed Tools Appl 78(13):18693–18712
Chen F, He H, Huo Y (2016) Self-embedding watermarking scheme against JPEG compression with superior imperceptibility. Multimed Tools Appl 76(7):9681–9712
Chen BJ, Gao Y, Xu LZ, Hong XP, Zheng YH, Shi YQ (Jul 29, 2019) Color image splicing localization algorithm by quaternion fully convolutional networks and superpixel-enhanced pairwise conditional random field. Math Biosci Eng 16(6):6907–6922
Cong R, Lei J, Zhang C, Huang Q, Cao X, Hou C (2016) Saliency detection for stereoscopic images based on depth confidence analysis and multiple cues fusion. IEEE Signal Process Lett 23(6):819–823
Cong R, Lei J, Fu H, Hou J, Huang Q, Kwong S (Aug, 2020) Going from RGB to RGBD saliency: a depth-guided transformation model. IEEE Trans Cybern 50(8):3627–3639
Ding W, Xie Y, Wang Y (2018) Image authentication and tamper localization based on relative difference between DCT coefficient and its estimated value. Multimed Tools Appl 78(5):5305–5328
Duan S, Wang H, Liu Y, Huang L, Zhou X, Zhou N (2020) A novel comprehensive watermarking scheme for color images. Secur Commun Netw 2020:1–12
Feng B, Li X, Jie Y, Guo C, Fu H (2019) A novel semi-fragile digital watermarking scheme for scrambled image authentication and restoration. Mob Netw Appl 25(1):82–94
Fletcher P, Sangwine SJ (2017) The development of the quaternion wavelet transform. Signal Process 136:2–15
Fu J, Mao J, Xue D, Chen D (2019) A watermarking scheme based on rotating vector for image content authentication. Soft Comput 24(8):5755–5772
Huo Y, He H, Chen F (2013) A semi-fragile image watermarking algorithm with two-stage detection. Multimed Tools Appl 72(1):123–149
Korus P, Huang J (2017) Multi-scale analysis strategies in PRNU-based tampering localization. IEEE Trans Inf Forensics Secur 12(4):809–824
Kumar K (2021) Text query based summarized event searching interface system using deep learning over cloud. Multimed Tools Appl 80(7):11079–11094
Kumar K, Shrimankar DD (2018) F-DES: fast and deep event summarization. IEEE Trans Multimedia 20(2):323–334
Kumar S, Singh BK (2021) DWT based color image watermarking using maximum entropy. Multimed Tools Appl 80(10):15487–15510
Li J, Levine MD, An X, Xu X, He H (Apr, 2013) Visual saliency based on scale-space analysis in the frequency domain. IEEE Trans Pattern Anal Mach Intell 35(4):996–1010
Li C, Zhang A, Liu Z, Liao L, Huang D (2014) Semi-fragile self-recoverable watermarking algorithm based on wavelet group quantization and double authentication. Multimed Tools Appl 74(23):10581–10604
Li H, Wu W, Wu E (2015) Robust interactive image segmentation via graph-based manifold ranking. Comput Vis Media 1(3):183–195
Li J, Lin Q, Yu C, Ren X, Li P (2016) A QDCT- and SVD-based color image watermarking scheme using an optimized encrypted binary computer-generated hologram. Soft Comput 22(1):47–65
Lin CY, Chang SF (Jan. 2000) Semi-fragile watermarking for authenticating JPEG visual content,“ In: Proc. SPIE, Security and Watermarking of Multimedia Contents, San Jose, CA, pp. 140–151
Liu X, Wu Y, Zhang H, Wu J, Zhang L (2021) Quaternion discrete fractional Krawtchouk transform and its application in color image encryption and watermarking. Signal Process 189:108275
Lu ZM, Xu DG, Sun SH (Jun, 2005) Multipurpose image watermarking algorithm based on multistage vector quantization. IEEE Trans Image Process 14(6):822–831
Maeno K, Qibin S, Shih-Fu C, Suto M (2006) New semi-fragile image authentication watermarking techniques using random bias and nonuniform quantization. IEEE Trans Multimedia 8(1):32–45
Miller ML, Doerr GJ, Cox IJ (Jun, 2004) Applying informed coding and embedding to design a robust high-capacity watermark. IEEE Trans Image Process 13(6):792–807
Ouyang J, Coatrieux G, Chen B, Shu H (2015) Color image watermarking based on quaternion Fourier transform and improved uniform log-polar mapping. Comput Electr Eng 46:419–432
Preda RO (2013) Semi-fragile watermarking for image authentication with sensitive tamper localization in the wavelet domain. Measurement 46(1):367–373
Qi X, Xin X (2011) A quantization-based semi-fragile watermarking scheme for image content authentication. J Vis Commun Image Represent 22(2):187–200
Qi X, Xin X (2015) A singular-value-based semi-fragile watermarking scheme for image content authentication with tamper localization. J Vis Commun Image Represent 30:312–327
Rhayma H, Makhloufi A, Hamam H, Hamida AB (2019) Semi-fragile self-recovery watermarking scheme based on data representation through combination. Multimed Tools Appl 78(10):14067–14089
Salloum R, Ren Y, Jay Kuo CC (2018) Image splicing localization using a multi-task fully convolutional network (MFCN). J Vis Commun Image Represent 51:201–209
Schmalz MS, Schlauweg M, Proefrock D, Palfner T, Mueller E (2005) Quantization-based semi-fragile public-key watermarking for secure image authentication. In: Mathematics of Data/Image Coding, Compression, and Encryption VIII, with Applications, pp. 591506–591506-11
Sharma S, Kumar K (2021) ASL-3DCNN: American sign language recognition technique using 3-D convolutional neural networks. Multimed Tools Appl 80(17):26319–26331
Shojanazeri H, Wan Adnan WA, Syed Ahmad SM, Rahimipour S (2015) Authentication of images using Zernike moment watermarking. Multimed Tools Appl 76(1):577–606
Sivasubramanian N, Konganathan G (2020) A novel semi fragile watermarking technique for tamper detection and recovery using IWT and DCT. Computing 102(6):1365–1384
Soualmi A, Alti A, Laouamer L (2020) A novel blind watermarking approach for medical image authentication using MinEigen value features. Multimed Tools Appl 80(2):2279–2293
Sreenivas K, Kamkshi Prasad V (2017) Fragile watermarking schemes for image authentication: a survey. Int J Mach Learn Cybern 9(7):1193–1218
Stamm MC, Min W, Liu KJR (2013) Information forensics: An overview of the first decade. IEEE Access 1:167–200
Thabit R (2021) Review of medical image authentication techniques and their recent trends. Multimed Tools Appl 80(9):13439–13473
Tiwari A, Sharma M, Tamrakar RK (2017) Watermarking based image authentication and tamper detection algorithm using vector quantization approach. AEU Int J Electron Commun 78:114–123
Tsai C, Qian X, Lin Y (2017) Image co-saliency detection via locally adaptive saliency map fusion. In: 2017 IEEE international conference on acoustics, speech and signal processing (ICASSP), pp. 1897-1901
USC-SIPI (1997) Available: http://sipi.usc.edu/database/. Accessed 20 Dec 2020
Xiangui K, Jiwu H, Wenjun Z (2010) Efficient general print-scanning resilient data hiding based on uniform log-polar mapping. IEEE Trans Inf Forensics Secur 5(1):1–12
Xiao J, Wang Y (2008) A Semi-fragile Watermarking Tolerant of Laplacian Sharpening. In: 2008 International Conference on Computer Science and Software Engineering, pp. 579–582
Yan C-P, Pun C-M (2017) Multi-scale difference map fusion for tamper localization using binary ranking hashing. IEEE Trans Inf Forensics Secur 12(9):2144–2158
Yang C, Zhang L, Lu H, Ruan X, Yang M-H (2013) Saliency Detection via Graph-Based Manifold Ranking. In: 2013 IEEE Conference on Computer Vision and Pattern Recognition, pp. 3166–3173
Yu X, Wang C, Zhou X (2017) Review on Semi-Fragile Watermarking Algorithms for Content Authentication of Digital Images. Future Internet 9(4):56
Yuchen Y, Changyang L, Jinman K, Weidong C, Feng DD (Mar, 2018) Reversion correction and regularized random walk ranking for saliency detection. IEEE Trans Image Process 27(3):1311–1322
Zhang L, Wu H (2021) Cosaliency detection and region-of-interest extraction via manifold ranking and MRF in remote sensing images. IEEE Trans Geosci Remote Sens 60:1–17
Zhao H, Ren J (2015) Cognitive computation of compressed sensing for watermark signal measurement. Cogn Comput 8(2):246–260
Zhou K, Zhang Y, Li J, Zhan Y, Wan W (2020) Spatial-Perceptual Embedding with Robust Just Noticeable Difference Model for Color Image Watermarking. Mathematics 8(9):1506–1522
Zhuang P, Li H, Tan S, Li B, Huang J (2021) Image tampering localization using a dense fully convolutional network. IEEE Trans Inf Forensics Secur 16(8):2986–2999
Acknowledgments
The authors would like to thank the anonymous reviewers for their valued comments and suggestions. This work was supported by the natural science foundation of Hunan province under Grants 2021JJ30277, 2019JJ50168, by the project of Hunan province education department under Grants 19 K035, 19B202, by the Ministry of Education humanities social sciences the youth fund project under Grants 20YJCZH179, and by the projects of national social science foundation of China under Grant 21BXW077. The code related to this paper is available at https://github.com/jingtaohuang/A-Novel-Semi-Fragile-Watermarking.git.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Competing interests
The authors declare that they have no known competing interests or personal relationships that could have appeared to influence the work reported in this paper.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Ouyang, J., Huang, J., Wen, X. et al. A semi-fragile watermarking tamper localization method based on QDFT and multi-view fusion. Multimed Tools Appl 82, 15113–15141 (2023). https://doi.org/10.1007/s11042-022-13938-1
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-13938-1