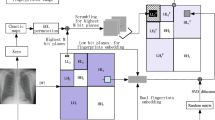
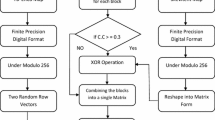
Abstract
The rapid development of mobile social networks and wireless communication technology has made image/video sharing easier and more efficient. However, the convenience of social multimedia sharing can also cause serious problems such as privacy disclosure because of illegal use of shared contents, and the existing content sharing scheme cannot meet the privacy protection requirements of users in social networks. Therefore, secure multimedia sharing and privacy protection have become critical and urgent in multimedia social networks. For protecting multimedia sharing in multimedia social networks, a novel joint fingerprinting and encryption (JFE) scheme is proposed. Both fingerprint embedding and encryption are performed in the tree structure haar wavelet transform and singular value decomposition (TSHWT_SVD) domain based on chaotic neural network. First, the social image is decomposed based on the fingerprint code structure by the TSHWT. Then, perform SVD computing for selective subbands for parallel piecewise fingerprint segments embedding. In the end, the fingerprinted coefficient stream is encrypted via block permutation and SVD diffusion. It is worth mentioning that most of the existing image security algorithms encrypt and embed a watermark in the spatial domain, which cannot meet the requirements of the era of multimedia social networks due to lack of scalability. The proposed method, to the best of our knowledge, is the first scalable JFE method for fingerprinting and encryption in the TSHWT_SVD domain. The use of fingerprinting along with encryption in the TSHWT_SVD domain can provide scalable double-layer protection for secure social multimedia sharing. When compared with existing image security algorithms, the scalable selective encryption method greatly improves encryption efficiency. Moreover, experimental results and contrastive analyses show that the proposed JFE scheme has high security, fast speed and can resist various attacks.






Similar content being viewed by others
Explore related subjects
Discover the latest articles and news from researchers in related subjects, suggested using machine learning.References
Al-Haj A, Abdel-Nabi H (2021) An efficient watermarking algorithm for medical images. Multimed Tools Appl 80(17):26021–26047. https://doi.org/10.1007/s11042-021-10801-7
Anand A, Singh AK (2022) Dual watermarking for security of covid-19 patient record. IEEE Transactions on Dependable and Secure Computing, 1–1. https://doi.org/10.1109/TDSC.2022.3144657
Cancellaro M, Battisti F, Carli M, Boato G, De Natale F, Neri A (2011) A commutative digital image watermarking and encryption method in the tree structured haar transform domain. Signal Process Image Commun 26(1):1–12
Czaplewski B (2016) Joint fingerprinting and decryption method for color images based on quaternion rotation with cipher quaternion chaining. J Vis Commun Image Represent 40:1–13
Diaconu A-V (2016) Circular inter-intra pixels bit-level permutation and chaos-based image encryption. Inf Sci 355:314–327. https://doi.org/10.1016/j.ins.2015.10.027
Ding Y, Wu G, Chen D, Zhang N, Gong L, Cao M, Qin Z (2021) Deepedn: A deep-learning-based image encryption and decryption network for internet of medical things. IEEE Internet Things J 8(3):1504–1518. https://doi.org/10.1109/JIOT.2020.3012452
Divya CD, Gururaj HL, Rohan R, Bhagyalakshmi V, Flammini F (2021) An efficient machine learning approach to nephrology through iris recognition. Discov Artif Intell 1(1):10–25. https://doi.org/10.1007/s44163-021-00010-4
Egiazarian K, Astola J (2002) Tree-structured haar transforms. Journal of Mathematical Imaging and Vision 16(3):269–279
Egorova E, Fernandez M, Kabatiansky G, Lee MH (2019) Signature codes for weighted noisy adder channel, multimedia fingerprinting and compressed sensing. Des Codes Crypt 87(SI 2-3):455–462
Elhoseny M, Shankar K, Lakshmanaprabu SK, Maseleno A, Arunkumar N (2020) Hybrid optimization with cryptography encryption for medical image security in Internet of Things. Neural Comput Appl 32(15):10979–10993
Feixiang Z, Mingzhe L, Kun W, Hong Z (2021) Color image encryption via hénon-zigzag map and chaotic restricted boltzmann machine over blockchain. Opt Laser Technol 135:1–13. https://doi.org/10.1016/j.optlastec.2020.106610
Haddad S, Coatrieux G, Moreau-Gaudry A, Cozic M (2020) Joint watermarking-encryption-jpeg-ls for medical image reliability control in encrypted and compressed domains. IEEE Trans Inform Forensics and Secur 15:2556–2569
Hua Z, Zhou Y, Huang H (2019) Cosine-transform-based chaotic system for image encryption. Inform Sci 480:403–419
Jiang J, Gu Y, Cheng M (2020) Multimedia IPP codes with efficient tracing. Des Codes Crypt 88(5):851–866
Kundur D, Karthik K (2004) Video fingerprinting and encryption principles for digital rights management. Proc IEEE 92(6):918–932
Li M, Chang H, Xiang Y, An D (2020) A Novel Anti-Collusion Audio Fingerprinting Scheme Based on Fourier Coefficients Reversing. IEEE Signal Process Lett 27:1794–1798
Li M, Xiao D, Zhu Y, Zhang Y, Sun L (2019) Commutative fragile zero-watermarking and encryption for image integrity protection. Multimed Tools Appl 78(16):22727–22742
Lian SG, Wang ZQ (2008) Collusion-traceable secure multimedia distribution based on controllable modulation. IEEE Trans Circuits Syst Video Technol 18(10):1462–1467
Lin C-Y, Muchtar K, Yeh C-H, Lu C-S (2016) Secure multicasting of images via joint privacy-preserving fingerprinting, decryption, and authentication. J Vis Commun Image Represent 38:858–871
Liu H, Wang X (2010) Color image encryption based on one-time keys and robust chaotic maps. Comput Math Appl 59(10):3320–3327
Megias D, Qureshi A (2017) Collusion-resistant and privacy-preserving P2P multimedia distribution based on recombined fingerprinting. Expert Syst Appl 71:147–172
Mohamed KS, Nouh S, Naguib AM (2019) Adaptive power transmission and efficient energy scheme of dsr protocol (apee-dsr). Int J Comput Netw Appl 6(1):13–24
Peng H, Yang B, Li L, Yang Y (2020) Secure and traceable image transmission scheme based on semitensor product compressed sensing in telemedicine system. IEEE Internet Things J 7(3):2432–2451
Ren H, Niu S Joint encryption and authentication in hybrid domains with hidden double random-phase encoding. Multimed Tools Appl . https://doi.org/10.1007/s11042-022-12013-z
Rostami MJ, Shahba A, Saryazdi S, Nezamabadi-pour H (2017) A novel parallel image encryption with chaotic windows based on logistic map. Comput Electr Eng 62:384–400. https://doi.org/10.1016/j.compeleceng.2017.04.004
Sahoo SR, Gupta BB (2019) Hybrid approach for detection of malicious profiles in twitter. Comput Electr Eng 76:65–81. https://doi.org/10.1016/j.compeleceng.2019.03.003
Sahoo SR, Gupta BB (2019) Classification of various attacks and their defence mechanism in online social networks: a survey. Enterprise Information Systems 13(6):832–864. https://doi.org/10.1080/17517575.2019.1605542
Sahoo SR, Gupta BB (2020) Classification of spammer and nonspammer content in online social network using genetic algorithm-based feature selection. Enterprise Information Systems 14(5):710–736. https://doi.org/10.1080/17517575.2020.1712742
Sahoo SR, Gupta BB (2021) Multiple features based approach for automatic fake news detection on social networks using deep learning. Appl Soft Comput 100:106983. https://doi.org/10.1016/j.asoc.2020.106983
Shanmugam L, Mani P, Rajan R, Joo YH (2020) Adaptive synchronization of reaction-diffusion neural networks and its application to secure communication. IEEE Trans Cybern 50(3):911–922
Singh SK, Sachan MK (2021) Classification of code-mixed bilingual phonetic text using sentiment analysis. Int J Semant Web Inf Syst 17(2):59–78. https://doi.org/10.4018/IJSWIS.2021040104
Skoric B, Katzenbeisser S, Celik M, Schaathun H (2011) Tardos fingerprinting codes in the combined digit model. IEEE Trans Inform Forensics and Secur 6(3):906–919
Subhash S, Gururaj HL, Ramesh B (2016) Entropy correlation coefficient technique for visual data in multimedia sensor network. Indian J Comput Sci Eng 148(2):1–6
Tanuja U, Gururaj VHL (2020) Janhavi: A machine learning algorithm for classification, analyzation and prediction of multimedia messages in social networks. In: Singh PK, Pawłowski W, Tanwar S, Kumar N, Rodrigues JJPC, Obaidat MS (eds) Proceedings of first international conference on computing, communications, and cyber-security (IC4S 2019), vol 121. Springer, Singapore, pp 485–499
Tembhurne JV, Almin MM, Diwan T (2022) Mc-dnn: Fake news detection using multi-channel deep neural networks. Int J Semantic Web Inform Syst 18(1):1–20. https://doi.org/10.4018/IJSWIS.295553
Thakur S, Singh AK, Ghrera SP, Elhoseny M (2019) Multi-layer security of medical data through watermarking and chaotic encryption for tele-health applications. Multimed Tools Appl 78(3):3457–3470. https://doi.org/10.1007/s11042-018-6263-3
Thanki R, Kothari A (2021) Multi-level security of medical images based on encryption and watermarking for telemedicine applications. Multimed Tools Appl 80(3):4307–4325. https://doi.org/10.1007/s11042-020-09941-z
Wang X-Y, Li Z-M (2019) A color image encryption algorithm based on hopfield chaotic neural network. Opt Lasers Eng 115:107–118
Wu J, Liao X, Yang B (2018) Image encryption using 2d hénon-sine map and dna approach. Signal Process 153:11–23
Xiong Z, Wu Y, Ye C, Zhang X, Xu F (2019) Color image chaos encryption algorithm combining CRC and nine palace map. Multimed Tools Appl 78 (22):31035–31055
Xiong L, Xia Z, Chen X, Shim HJ (2019) Secure multimedia distribution in cloud computing using re-encryption and fingerprinting. Multimed Tools Appl 78(21):30297–30313
Yan L, Fu J, Wang C, Ye Z, Chen H, Ling H (2021) Enhanced network optimized generative adversarial network for image enhancement. Multimed Tools Appl 80(9):14363–14381. https://doi.org/10.1007/s11042-020-10310-z
Yan L, Lu H, Wang C, Ye Z, Chen H, Ling H (2019) Deep linear discriminant analysis hashing for image retrieval. Multimed Tools Appl 78 (11):15101–15119. https://doi.org/10.1007/s11042-018-6855-y
Yan L, Sheng M, Wang C, Gao R, Yu H (2022) Hybrid neural networks based facial expression recognition for smart city. Multimed Tools Appl 81(1):319–342. https://doi.org/10.1007/s11042-021-11530-7
Yang Y, Liu X, Deng RH, Li Y (2020) Lightweight sharable and traceable secure mobile health system. IEEE Trans Dependable Secure Comput 17 (1):78–91
Yasui T, Kuribayashi M, Funabiki N, Echizen I (2020) Near-optimal detection for binary tardos code by estimating collusion strategy. IEEE Trans Inf Forensics Secur 15:2069–2080
Ye C, Ling H, Zou F, Lu Z (2013) A new fingerprinting scheme using social network analysis for majority attack. Telecommun Syst 54(3):315–331. https://doi.org/10.1007/s11235-013-9736-8
Zhang LY, Zheng Y, Weng J, Wang C, Shan Z, Ren K (2020) You can access but you cannot leak: Defending against illegal content redistribution in encrypted cloud media center. IEEE Trans Dependable Secure Comput 17(6):1218–1231
Acknowledgments
This paper is supported by Natural Science Foundation of China (No.61502154, No.61972136, No.61370092), NSF of Chinese Hubei Provinc (No.2015CFB236), Natural Science Fundation of Hubei Provincial Department of Education (No.D20142703), Philosophy and Social Science Research Project of Hubei Provincial Department of Education (No.21Q213).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
All data generated or analysed during this study are included in this published article.
Conflict of Interests
The authors declare that they have no conflict of interest.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Shenglong Tan, Zheng Wang, Li Shi and Jun Wang are contributed equally to this work.
Rights and permissions
Springer Nature or its licensor holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Ye, C., Tan, S., Wang, Z. et al. A secure social multimedia sharing scheme in the TSHWT_SVD domain based on neural network. Multimed Tools Appl 82, 15395–15414 (2023). https://doi.org/10.1007/s11042-022-13953-2
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-13953-2