Abstract
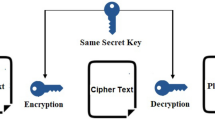
This article propounds a Piecewise Symmetric Magic Cube (PSMC), the properties of which have reinvigorated its application to text encryption. A method has been introduced for the construction of magic cubes of order m × 2l, for all \(l,m (m {\text {even}})\in N\cup \left \lbrace 0 \right \rbrace , m\geq 4\) by using the concept of compounding. The behavior of elements in PSMC is controlled by the starting variables (Sstart and Lstart). The formula for evaluation of the magic sum of these magic cubes have been derived, which ensures magic nature of PSMC. Additionally, PSMC are applied to the field of text cryptography. The proposed text encryption model is applicable for the encryption and decryption of any language that may include numeric digits, and special characters along with their different combinations. Also, the validation of this model has been checked by focusing on the analysis of bilingual data (English-German, English-Hindi, German-Hindi, French-Arabic, and Italian-Spanish). The performance evaluation metrices (brute-force analysis, avalanche effect, CPU time analysis, Shannon entropy, and known plain text analysis) have been carried to analyze the resisting efficiency of the proposed model against different types of attacks. An analysis of encryption/ decryption time shows that decryption is more time-efficient which protects the data from getting being corrupted by the intruders. The distinct entries of PSMC remove the problem of repetition in cipher text which raises the level of security to a higher extent.










Similar content being viewed by others
References
Alspach B, Heinrich K (1981) Perfect magic cubes of order 4m. Fibonacci Quarterly 19:97–106
Alvarez G, Li S (2006) Some basic cryptographic requirements for chaos-based cryptosystems. Int J Bifurcation Chaos 16(08):2129–2151
Andrew W (1960) Magic Square and Cubes-Second edition. Dover Publications, New York
Arroyo J C T, Dumdumaya C E, Delima A J P (2020) Polybius square in cryptography: a brief review of literature. Int J Adv Trends Comput Sci Eng 9(3):3798–3808
Bajaj N (2022) Caesar cipher. The MathWorks, USA
Bharathi B, Manivasagam G, Kumar M A (2017) Metrics for performance evaluation of encryption algorithms. Int J Adv Res Sci Eng 6(3):62–72
Bouffard F (2022) Rot13. The MathWorks, USA
Chen X. -s. (2002) Ways of constructing optimal magic cube of order n when (n, 2· 3· 5· 7)= 1. J Central South University of Technology 9(1):70–72
Chiron L, Oger G, De Leffe M, Le Touzé D (2018) Analysis and improvements of adaptive particle refinement (apr) through cpu time, accuracy and robustness considerations. J Comput Phys 354:552–575
Dawood O (2015) Development of symmetric cryptographic models and asymmetric models based on magic cube. University of Technology, Iraq, Ph.D. thesis
Galar D, Kumar U (2017) Chapter 3 - preprocessing and features. In: eMaintenance. Academic Press, pp 129–177
George D, Geetha J S, Mani K (2014) Add-on security level for public key cryptosystem using magic rectangle with column/row shifting. Int J Comput Appl 975(8887):38–43
Gustafson H, Dawson E, Nielsen L, Caelli W (1994) A computer package for measuring the strength of encryption algorithms. Comput Security 13 (8):687–697
Hankerson D, Menezes AJ, Vanstone S (2006) Guide to elliptic curve cryptography. Springer Science & Business Media
Hill D (2022) Advanced encryption standard (aes)-128,192, 256. The MathWorks Natick, USA
Jamel S, Herawan T, Deris MM (2010) A cryptographic algorithm based on hybrid cubes. In: International conference on computational science and its applications. Springer, vol 6019, pp 175–187
Jiang Y, Susilo W, Mu Y, Guo F (2018a) Ciphertext-policy attribute-based encryption supporting access policy update and its extension with preserved attributes. Int J Inf Secur 17(5):533–548
Jiang Y, Susilo W, Mu Y, Guo F (2018b) Flexible ciphertext-policy attribute-based encryption supporting and-gate and threshold with short ciphertexts. Int J Inf Secur 17(4):463–475
Khanas Y, Borecki M (2020) Research on the use of algorithms for matrix transformations for encrypting text information. Security and Privacy 3 (6):e108
Krishna G J, Ravi V, Bhattu S N (2018) Key generation for plain text in stream cipher via bi-objective evolutionary computing. Appl Soft Comput 70:301–317
Kumar A, Tiwari N (2012) Effective implementation and avalanche effect of aes. International Journal of Security. Privacy Trust Management (IJSPTM) 1(3/4):31–35
Lee S, Kim S, Jung K (2013) A symmetric key cryptography algorithm by using 3-dimensional matrix of magic squares. In: Proceedings of the Korea information processing society conference. Korea Information Processing Society, vol 20, pp 768–770
Lin K Y (1986) Magic cubes and hypercubes of order 3. Discrete mathematics 58(2):159–166
Mani K, Viswambari M (2017) Enhancing the security in cryptosystems based on magic rectangle. Int J Comput Netw Inform Sec, vol 9(4)
Michel R, Taubenfeld G, Berman A (1995) A connection between random variables and latin k-cubes. Discret Math 146(1-3):313–320
Mushtaq M F, Jamel S, Radhiah S, Akram U, Mat M (2019) Key schedule algorithm using 3-dimensional hybrid cubes for block cipher. Int J Adv Comput Sci Appl 10(8):427–442
National Academies of Sciences, Medicine E et al (2018) Decrypting the Encryption Debate: A Framework for Decision Makers. National Academies Press, Washington
Nordgren R P (2012) On properties of special magic square matrices. Linear Algebra Appl 437(8):2009–2025
Pavithran P, Mathew S, Namasudra S, Srivastava G (2022) A novel cryptosystem based on dna cryptography, hyperchaotic systems and a randomly generated moore machine for cyber physical systems. Comput Commun 188:1–12
Rajavel D, Shantharajah S (2012) Cubical key generation and encryption algorithm based on hybrid cube’s rotation. In: International conference on pattern recognition, informatics and medical engineering (PRIME-2012). IEEE, pp 183–187
Rani N, Mishra V (2022) Behavior of powers of odd ordered special circulant magic squares. Int J Math Educ Sci Technol 53(4):1044–1062
Rasmi P, Paul V (2014) An efficient mixed mode and paired cipher text cryptographic algorithm for effective key distribution. Int J Commun Syst 11(27):2593–2603
Richards D (1980) Generalized magic cubes. Math Mag 53(2):101–105
Sef Y (2022) Feistel text encryption. The MathWorks Natick, USA
Shibiraj N, Tomba I (2018) Modified hill cipher: secure technique using latin square and magic square. Int J Comput Sci Eng 6(12):315–320
Trenkler M (2000) A construction of magic cubes. Math Gaz 84 (499):36–41
Uko L U, Barron T L (2018) A generalization of trenkler’s magic cubes formula. Recreat Math Mag 4(8):39–45
Xu J, Zhou J (2021) Strong leakage-resilient encryption: enhancing data confidentiality by hiding partial ciphertext. Int J Inf Secur 20(2):141–159
Yuan Y, Mo Y (2020) Security for cyber-physical systems: Secure control against known-plaintext attack. Sci China Technol Sci 63(9):1637–1646
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of Interests
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Rani, N., Mishra, V. & Singh, B. Piecewise symmetric magic cube: application to text cryptography. Multimed Tools Appl 82, 19369–19391 (2023). https://doi.org/10.1007/s11042-022-14153-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-14153-8