Abstract
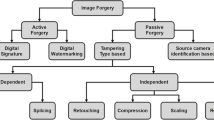
Digital image forgeries become one of the most challenges faced by technology users today. A copy-move forgery is one of the most common types of these forgeries. This type is not only common, but it is also very simple to execute to create deceptive images. Many algorithms use various technologies to create a high-performance Copy Move Forgery Detection (CMFD) system. There are currently two major CMFD trends: traditional CMFD algorithms and deep-learning-based CMFD algorithms. The main concept behind CMFD algorithms is to extract image features using various techniques and then search for matching features. This main idea can be carried out by using different feature extraction techniques with various matching techniques. For traditional algorithms, there are many types of features extractors used such as invariant image moments, texture and intensity descriptors, Scale-Invariant Feature Transform (SIFT), Speed Up Roust Features (SURF), Discrete Cosine Transform (DCT), Singular Value Decomposition (SVD), Principal Component Analysis (PCA), and other extractors. The strength of these extractors varies according to the image properties and the forgery’s performance perfection. Deep learning-based CMFD algorithms operate as a black box, by extracting image features using layers with complex training and validation processes to achieve the best scenario, such as Convolutional Neural Network (CNN), Convolutional Long Short-Term Memory (CovLSTM), Multi-domain CNN, and Buster-Net. This paper discusses different types of digital image forgery with focusing on copy-move forgery. A detailed survey of various types of CMFD algorithms, on the other hand, has been displayed. The paper provides a comprehensive comparison of various algorithms and evaluates them using various types of evaluation parameters. Finally, the paper focuses on the different datasets used by various algorithms to evaluate their performance accuracy and testing time. These datasets are detailed in terms of image numbers, the number of original images, the number of forged images, the resolution variety in each dataset, the size of the tampered region in each dataset, and the strength of each dataset compared with each other.




















Similar content being viewed by others
References
Amerini I, Ballan L, Caldelli R, Del Bimbo A, Serra G (2011) A sift-based forensic method for copy–move attack detection and transformation recovery. IEEE Trans. Inf. Forensics Secur. 6:1099–1110
Amerini I, Ballan L, Caldelli R, Del Bimbo A, Del Tongo L, Serra G (2013) Copy-move forgery detection and localization by means of robust clustering with J-linkage. Signal Process Image Commun 28:659–669
Amerini I, Uricchio T, Ballan L, Caldelli R (2017) Localization of JPEG double compression through multi-domain convolutional neural networks. In: 2017 IEEE Conf. Comput. Vis. Pattern Recognit. Work., IEEE, pp. 1865–1871
Bay H, Ess A, Tuytelaars T, Van Gool L (2008) Speeded-up robust features (SURF). Comput Vis Image Underst 110:346–359
Bayar B, Stamm MC (2016) A deep learning approach to universal image manipulation detection using a new convolutional layer. In: Proc. 4th ACM Work. Inf. Hiding Multimed. Secur., pp. 5–10
Bi X, Wei Y, Xiao B, Li W (2019) Rru-net: The ringed residual u-net for image splicing forgery detection. In: Proc. IEEE Conf. Comput. Vis. Pattern Recognit. Work., p. 0
Bo X, Junwen W, Guangjie L, Yuewei D (2010) Image copy-move forgery detection based on SURF. In: 2010 Int. Conf. Multimed. Inf. Netw. Secur., IEEE, pp. 889–892
Bondi L, Lameri S, Güera D, Bestagini P, Delp EJ, Tubaro S (2017) Tampering detection and localization through clustering of camera-based CNN features. In: 2017 IEEE Conf. Comput. Vis. Pattern Recognit. Work., IEEE, pp. 1855–1864
Chauhan D, Kasat D, Jain S, Thakare V (2016) Survey on keypoint based copy-move forgery detection methods on image. Procedia Comput Sci 85:206–212
Chen J, Kang X, Liu Y, Wang ZJ (2015) Median filtering forensics based on convolutional neural networks. IEEE Signal Process Lett 22:1849–1853
Christlein V, Riess C, Jordan J, Riess C, Angelopoulou E (2012) An evaluation of popular copy-move forgery detection approaches. IEEE Trans. Inf. Forensics Secur. 7:1841–1854
Columbia Image Splicing Detection Evaluation Dataset, (n.d.) DVMM Laboratory of Columbia University, CalPhotos Digital Library, http://www.ee.columbia.edu/ln/dvmm/downloads/AuthSplicedDataSet/AuthSplicedDataSet.htm. Accessed May 2020
Cozzolino D, Verdoliva L (2016) Single-image splicing localization through autoencoder-based anomaly detection. In: 2016 IEEE Int. Work. Inf. Forensics Secur., IEEE, pp. 1–6
Dalal N, Triggs B (2005) Histograms of oriented gradients for human detection. In: 2005 IEEE Comput. Soc. Conf. Comput. Vis. Pattern Recognit., IEEE, pp. 886–893
Dander A, Mueller LA, Gallasch R, Pabinger S, Emmert-Streib F, Graber A, Dehmer M (2013) [COMMODE] a large-scale database of molecular descriptors using compounds from PubChem. Source Code Biol Med 8:22. https://doi.org/10.1186/1751-0473-8-22
Davarzani R, Yaghmaie K, Mozaffari S, Tapak M (2013) Copy-move forgery detection using multiresolution local binary patterns. Forensic Sci Int 231:61–72
Diane WNN, Xingming S, Moise FK (2014) A survey of partition-based techniques for copy-move forgery detection. The Scientific World Journal 2014. https://doi.org/10.1155/2014/975456
Dong J, Wang W, Tan T (2013) Casia image tampering detection evaluation database. In: 2013 IEEE China summit Int. Conf. Signal Inf. Process., IEEE, pp. 422–426
Elaskily MA, Aslan HK, Abd El-Samie FE, Elshakankiry OA, Faragallah OS, Dessouky MM (2017) Comparative study of copy-move forgery detection techniques, Intl Conf on advanced control circuits systems (ACCS) systems & Intl Conf on new paradigms in Electronics & Information Technology (PEIT), Alexandria, Egypt
Elaskily MA, Elnemr HA, Dessouky MM, Faragallah OS (2018) Two stages object recognition based copy-move forgery detection algorithm. Multimedia Tools and Applications 78:15353–15373. https://doi.org/10.1007/s11042-018-6891-7
Elaskily MA, Aslan HK, Dessouky MM, Abd El-Samie FE, Faragallah OS, Elshakankiry OA (Jan. 2019) Enhanced Filter-based SIFT Approach for Copy-Move Forgery Detection. Menoufia Journal of Electronic Engineering Research (MJEER) 28(1):159–182
Elaskily MA, Elnemr HA, Sedik A, Dessouky MM, El Banby GM, Elshakankiry OA, Khalaf AM, Aslan HK, Faragallah OS, Abd El-Samie FE (2020) A novel deep learning framework for copy-move forgery detection in images. Multimedia Tools and Applications 79:19167–19192. https://doi.org/10.1007/s11042-020-08751-7
Elaskily MA, Alkinani MH, Sedik A, Dessouky MM (2021) Deep learning based algorithm (ConvLSTM) for copy move forgery detection. Journal of Intelligent & Fuzzy Systems 40(3):4385–4405. https://doi.org/10.3233/JIFS-201192
Fadl SM, Semary NA (2014) A proposed accelerated image copy-move forgery detection, In: 2014 IEEE vis. Commun. Image Process. Conf., IEEE, pp. 253–257
Hashmi MF, Anand V, Keskar AG (2014) A copy-move image forgery detection based on speeded up robust feature transform and wavelet transforms. In: 2014 Int. Conf. Comput. Commun. Technol., IEEE, pp. 147–152
Hassaballah M, Abdelmgeid AA, Alshazly HA (2016) Image features detection, description and matching, In: Image Featur. Detect. Descriptors, Springer, pp. 11–45
Huang Y, Lu W, Sun W, Long D (2011) Improved DCT-based detection of copy-move forgery in images. Forensic Sci Int 206:178–184
Jwaid MF, Baraskar TN (2017) Study and analysis of copy-move & splicing image forgery detection techniques, In: 2017 Int. Conf. I-SMAC (IoT Soc. Mobile, Anal. Cloud)(I-SMAC), IEEE, pp. 697–702
Kumar S, Desai J, Mukherjee S (2013) A fast DCT based method for copy move forgery detection, In: 2013 IEEE second Int. Conf. Image Inf. Process., IEEE, pp. 649–654
Liu B, Pun C-M (2013) A SIFT and local features based integrated method for copy-move attack detection in digital image, In: 2013 IEEE Int. Conf. Inf. Autom., IEEE, pp. 865–869
Liu G, Wang J, Lian S, Wang Z (2011) A passive image authentication scheme for detecting region-duplication forgery with rotation. J Netw Comput Appl 34:1557–1565
Lowe DG (2004) Distinctive image features from scale-invariant keypoints. Int J Comput Vis 60:91–110
Luo W, Huang J, Qiu G (2006) Robust detection of region-duplication forgery in digital image, In: 18th Int. Conf. Pattern Recognit., IEEE, pp. 746–749
Maind RA, Khade A, Chitre DK (2014) Image copy move forgery detection using block representing method. Int J Soft Comput Eng 4:49–53
Muhammad G, Hussain M (2013) Passive detection of copy-move image forgery using undecimated wavelets and zernike moments. Inf J 16:2957–2964
Mushtaq S, Mir AH (2014) Digital Image Forgeries and Passive Image Authentication Techniques: A Survey. International Journal of Advanced Science and Technology 73:15–32. https://doi.org/10.14257/ijast.2014.73.02
Pandey RC, Singh SK, Shukla KK, Agrawal R (2014) Fast and robust passive copy-move forgery detection using SURF and SIFT image features. In: 2014 9th Int. Conf. Ind. Inf. Syst., pp. 1–6. https://doi.org/10.1109/ICIINFS.2014.7036519
Prasad S, Ramkumar B (2016) Passive copy-move forgery detection using SIFT, HOG and SURF features. In: 2016 IEEE Int. Conf. Recent Trends Electron. Inf. Commun. Technol., IEEE, pp. 706–710
Qureshi AM, Deriche M (2014) A review on copy-move image forgery detection techniques, multi-conference on systems. Signals & Devices (SSD):11–14
Rao Y, Ni J (2016) A deep learning approach to detection of splicing and copy-move forgeries in images. In: 2016 IEEE Int. Work. Inf. Forensics Secur., IEEE, pp. 1–6
Redi JA, Taktak W, Dugelay JL (2011) Digital image forensics: a booklet for beginners. Multimed Tools Appl 51:133–162
Ryu S-J, Kirchner M, Lee M-J, Lee H-K (2013) Rotation invariant localization of duplicated image regions based on Zernike moments. IEEE Trans Inf Forensics Secur 8:1355–1370
Salloum R, Ren Y, Kuo C-CJ (2018) Image splicing localization using a multi-task fully convolutional network (MFCN). J Vis Commun Image Represent 51:201–209
Shivakumar BL, Baboo SS (2011) Detection of region duplication forgery in digital images using SURF. Int J Comput Sci Issues 8:199
Tralic D, Zupancic I, Grgic S, M. Grgic (2013) CoMoFoD — new database for copy-move forgery detection. Proceedings ELMAR-2013, pp. 49–54
Wang X, Wang H, Niu S, Zhang J (2019) Detection and localization of image forgeries using improved mask regional convolutional neural network. Math Biosci Eng MBE 16:4581–4593
Wu Y, Abd-Almageed W, Natarajan P (2018) Busternet: Detecting copy-move image forgery with source/target localization. In: Proc. Eur. Conf. Comput. Vis., pp. 168–184
Yang J, Ran P, Xiao D, Tan J (2013) Digital image forgery forensics by using undecimated dyadic wavelet transform and Zernike moments. J Comput Inf Syst 9:6399–6408
Zhang J, Ruan Q, Jin Y (2014) Combined SIFT and bi-coherence features to detect image forgery. In: 2014 12th Int. Conf. Signal Process., IEEE, pp. 1859–1863
Zhang W, Yang Z, Niu S, Wang J (2016) Detection of copy-move forgery in flat region based on feature enhancement. In: Int. Work. Digit. Watermarking, Springer, pp. 159–171
Zhang Y, Goh J, Win LL, Thing VLL (2016) Image Region Forgery Detection: A Deep Learning Approach., SG-CRC. 2016, 1–11
Zhao J, Guo J (2013) Passive forensics for copy-move image forgery using a method based on DCT and SVD. Forensic Sci Int 233:158–166
Zheng Y, Cao Y, Chang C-H (2019) A PUF-based data-device hash for tampered image detection and source camera identification. IEEE Trans. Inf. Forensics Secur. 15:620–634
Funding
This study was funded by the Deanship of Scientific Research, Taif University Researchers Supporting Project number (TURSP-2020/08), Taif University, Taif, Saudi Arabia.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
-
All authors have participated in (a) conception and design, or analysis and interpretation of the data; (b) drafting the article or revising it critically for important intellectual content; and (c) approval of the final version.
-
This manuscript has not been submitted to, nor is under review at, another journal or other publishing venue.
-
The authors have no affiliation with any organization with a direct or indirect financial interest in the subject matter discussed in the manuscript.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Elaskily, M.A., Dessouky, M.M., Faragallah, O.S. et al. A survey on traditional and deep learning copy move forgery detection (CMFD) techniques. Multimed Tools Appl 82, 34409–34435 (2023). https://doi.org/10.1007/s11042-023-14424-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-14424-y