Abstract
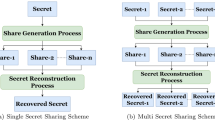
The existing state of the art schemes deals with the same dimension secret images but less work is available in the literature for different dimension secret images. In this paper, we have proposed an efficient multi secret image sharing scheme for different dimension secret images. In the proposed scheme, Chinese Remainder Theorem (CRT), shift and XOR operations are used for shares generation and secrets reconstruction to provide more randomized shares without revealing any secret information. The proposed scheme is attack resistive as if there is an attack on any of the share(s) then the reconstructed secrets doesn’t reveal the attacked portion whereas the remaining portion of the secrets gets reconstructed correctly. This confirms that an attack has been performed on the share(s) during transmission. The quantitative analysis of the proposed scheme is performed using Jaccard coefficient, correlation, RMSE, PSNR, MAE, NPCR, UACI, Information Entropy, and EQ parameters whereas the qualitative analysis has been performed using histogram analysis. The experimental results shows that the proposed scheme performs better on different dimension secret images.


























Similar content being viewed by others
References
Abdulla AA, Sellahewa H, Jassim SA (2019) Improving embedding efficiency for digital steganography by exploiting similarities between secret and cover images. Multimed Tools Appl 78(13):17799–17823
Agarwal A, Deshmukh M (2021) 3-D plane based extended Shamir’s secret sharing. Int J Inf Technol 13(2):609–612
Agarwal A, Deshmukh M, Singh M (2020) Object detection framework to generate secret shares. Multimed Tools Appl 79(33):24685–24706
Bhattacharjee T, Maity SP, Islam SR (2018) Hierarchical secret image sharing scheme in compressed sensing. Signal Process Image Commun 61:21–32
Binu VP, Sreekumar A (2017) Secure and efficient secret sharing scheme with general access structures based on elliptic curve and pairing. Wirel Pers Commun 92(4):1531–1543
Bisht K, Deshmukh M (2021) A novel approach for multilevel multi-secret image sharing scheme. J Supercomput 77(10):12157–12191
Chen T-H, Wu C-S (2011) Efficient multi-secret image sharing based on boolean operations. Signal Process 91(1):90–97
Chen C-C, Chen J-L (2017) A new Boolean-based multiple secret image sharing scheme to share different sized secret images. J Inf Sec Appl 33:45–54
Chen Chien-Chang, Wei-Jie W u (2014) A secure boolean-based multi-secret image sharing scheme. J Syst Softw 92:107–114
Chen Chien-Chang, Wei-Jie W u, Chen Jun-Long (2016) Highly efficient and secure multi-secret image sharing scheme. Multimed Tools Appl 75 (12):7113–7128
Deshmukh M, Nain N, Ahmed M (2017) A novel approach for sharing multiple color images by employing chinese remainder theorem. J Vis Commun Image Represent 49:291–302
Deshmukh M, Nain N, Ahmed M (2017) A novel approach of an (n, n) multi-secret image sharing scheme using additive modulo, Int Conf Comput Vision Image Process. Springer:149-158
Deshmukh M, Nain N, Ahmed M (2018) Efficient and secure multi secret sharing schemes based on boolean XOR and arithmetic modulo. Multimed Tools Appl 77(1):89–107
Deshmukh M, Nain N, Ahmed M (2019) Secret sharing scheme based on binary trees and boolean operation. Knowl Inf Syst 60(3):1377–1396
Deshmukh M, Nain N, Mushtaq A (2016) Enhanced modulo based multi secret image sharing. In: International conference on information systems security. Springer, pp 212-224
Dharani P, Berlin MA (2015) Survey on secret sharing scheme with deduplication in cloud computing. In: International Conference on Intelligent Systems and Control. IEEE, pp 1-5
Eslami Z, Razzaghi SH, Zarepour Ahmadabadi J (2010) Secret image sharing based on cellular automata and steganography. Pattern Recogn 43(1):397–404
Eslami Z, Zarepour Ahmadabadi J (2010) A verifiable multi-secret sharing scheme based on cellular automata. Inf Sci 180(15):2889–2894
Feng J-B et al (2005) A new multi-secret images sharing scheme using Largrange’s interpolation. J Syst Softw 76(3):327–339
Forouzan BA (2015) And Debdeep Mukhopadhyay. Cryptography and network security, Mc Graw Hill Education (India) Private Limited
Gayathri J, Subashini S (2018) A spatiotemporal chaotic image encryption scheme based on self adaptive model and dynamic keystream fetching technique. Multimed Tools Appl 77.19:24751–24787
Gupta M, Gupta M, Deshmukh M (2020) Single secret image sharing scheme using neural cryptography. Multimed Tools Appl 79(17):12183–12204
He Q i et al (2019) A weighted threshold secret sharing scheme for remote sensing images based on Chinese remainder theorem. Comput Mater Continua 58 (2):349–361
Jia X et al (2019) A new threshold changeable secret sharing scheme based on the Chinese Remainder Theorem. Inf Sci 473:13–30
Kabirirad S, Eslami Z (2019) Improvement of (n, n)-multi-secret image sharing schemes based on boolean operations. J Inf Sec Appl 47:16–27
Khorasgani HA et al (2014) A lattice-based threshold secret sharing scheme. In: International conference on information security and cryptology. IEEE, pp 173-179
Li Q et al (2021) Image steganography based on style transfer and quaternion exponent moments. Appl Soft Comput 110:107618
Lin S-J, Ja-Chen L (2007) VCPSS: a two-in-one two-decoding-options image sharing method combining visual cryptography (VC) and polynomial-style sharing (PSS) approaches. Pattern Recogn 40(12):3652–3666
Liu Z, Ahmad MA, Liu S (2008) Image sharing scheme based on combination theory. Optics Commun 281(21):5322–5325
Maroti D, Nain N, Ahmed M (2016) An (n, n)-multi secret image sharing scheme using boolean XOR and modular arithmetic. IEEE, Int Conf Adv Inf Netw Appl (AINA):690-697
Pang L et al (2008) A verifiable (t, n) multiple secret sharing scheme and its analyses. In: International symposium on electronic commerce and security. IEEE, pp 22-26
Pilaram H, Eghlidos T (2015) An efficient lattice based multi-stage secret sharing scheme. IEEE Trans Dependable Secure Comput 14(1):2–8
Pilaram H, Eghlidos T (2017) A lattice-based changeable threshold multi-secret sharing scheme and its application to threshold cryptography. Scientia Iranica 24(3):1448–1457
Rajput M, Deshmukh M (2016) Secure (n, n + 1)-multi secret image sharing scheme using additive modulo. Procedia Comput Sci 89:677–683
Rey D, Martin A, Pereira Mateus J, Rodríguez Sánchez G (2005) A secret sharing scheme based on cellular automata. App Math Comput 170 (2):1356–1364
Shamir A (1979) How to share a secret. Commun ACM 22(11):612–613
Shankar K, Devika G, Ilayaraja M (2017) Secure and efficient multi-secret image sharing scheme based on boolean operations and elliptic curve cryptography. Int J Pure Appl Math 116(10):293–300
Sheikhi-Garjan M, Bahramian M, Doche C (2019) Threshold verifiable multi-secret sharing based on elliptic curves and Chinese remainder theorem. IET Inf Secur 13(3):278–284
Teodoro AAM et al (2021) An FPGA-based performance evaluation of artificial neural network architecture algorithm for IoT. Wirel Pers Commun:1–32
Thien Chih-Ching, Lin Ja-Chen (2002) Secret image sharing. Comput Graph 26(5):765–770
Ulutas M, Ulutas G, Nabiyev VV (2011) Medical image security and EPR hiding using Shamir’s secret sharing scheme. J Syst Softw 84(3):341–353
Wang X, Gao S (2020) Image encryption algorithm based on the matrix semi-tensor product with a compound secret key produced by a Boolean network. Inf Sci 539:195–214
Wang X, Gao S (2020) Image encryption algorithm for synchronously updating boolean networks based on matrix semi-tensor product theory. Inf Sci 507:16–36
Wang X, Le F, Zhao H (2019) Fast image encryption algorithm based on parallel computing system. Inf Sci 486:340–358
Wang X, Liu C, Jiang D (2021) A novel triple-image encryption and hiding algorithm based on chaos, compressive sensing and 3D DCT. Inf Sci 574:505–527
Wang X, Yang J (2021) A privacy image encryption algorithm based on piecewise coupled map lattice with multi dynamic coupling coefficient. Inf Sci 569:217–240
Wang X, Zhang M (2021) An image encryption algorithm based on new chaos and diffusion values of a truth table. Inf Sci 579:128–149
Wang D et al (2007) Two secret sharing schemes based on Boolean operations. Pattern Recogn 40(10):2776–2785
Wang C et al (2019) Ternary radial harmonic fourier moments based robust stereo image zero-watermarking algorithm. Inf Sci 470:109–120
Wang C et al (2019) Image description with polar harmonic Fourier moments. IEEE Trans Circ Syst Video Technol 30.12:4440–4452
Wang X et al (2021) High precision error prediction algorithm based on ridge regression predictor for reversible data hiding. IEEE Signal Process Lett 28:1125–1129
Xian Y, Wang X (2021) Fractal sorting matrix and its application on chaotic image encryption. Inf Sci 547:1154–1169
Xian Y, Wang X, Teng L (2021) Double parameters fractal sorting matrix and its application in image encryption. IEEE Trans Circuits Syst Video Technol:1–10
Yan X et al (2018) Chinese remainder theorem-based two-in-one image secret sharing with three decoding options. Digital Signal Processing 82:80–90
Yang C-C, Chang T-Y, Min-Shiang HA (2004) (T, n) multi-secret sharing scheme. Appl Math Comput 151(2):483–490
Yang C-N, Chen C-H, Cai S-R (2016) Enhanced Boolean-based multi secret image sharing scheme. J Syst Software 116:22–34
Author information
Authors and Affiliations
Contributions
All authors have participated in (a) conception and design, or analysis and interpretation of the data; (b) drafting the article or revising it critically for important intellectual content; and (c) approval of the final version. This manuscript has not been submitted to, nor is under review at, another journal or other publishing venue.
Corresponding author
Ethics declarations
Conflict of Interests
The authors declare that they have no conflict of interest.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Rawat, A.S., Deshmukh, M. & Singh, M. A novel multi secret image sharing scheme for different dimension secrets. Multimed Tools Appl 82, 35183–35219 (2023). https://doi.org/10.1007/s11042-023-14609-5
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-14609-5