Abstract
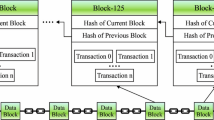
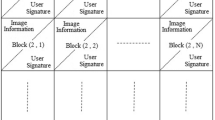
In the recent years, there has been tremendous growth in the use of IoT based applications. It is making its footprint strong with day to day life uses as well as industrial uses. IoT has vast applications ranging from medical, automobile industry, daily task automation, security surveillance and a lot more. Surveillance based IoT system shares images over internet for information exchange between filed experts and technical members for faster analysis about the locations and if it has any unauthorized activity. So these image information exchange should be secured. Thus this paper proposes a new technique for achieving this task in two phases. In first phase the secret/informative image is encrypted using a novel encryption technique. In second phase this encrypted image is shared to receiver team using a highly secured Tangle(latest secured transmission model advanced from Blockchain).Tangle eliminates the drawback of the traditional blockchain while providing its security features like decentralization, high reliability, and low cost to transfer and store users image information data. Tangle can be combined with IoT to make it more stronger. The proposed method has been tested on various images and its performance has been compared using standard metrics such as Correlation, number of pixels change rate (NPCR), the unified average changed intensity(UACI), information entropy analysis, key space analysis, etc. The proposed technique was found to be better than literature methods like the entropy value is near to an ideal value 8, which is considered safe from brute force attack.









Similar content being viewed by others
Data Availability
Data sharing is not applicable to this article as no new datasets were generated or analyzed during the current study.
References
Alvarez G, Li S (2006) Some basic cryptographic requirements for chaos-based cryptosystems. Int J Bifur Chaos 16.08:2129–2151
Arroyo D, Rhouma R, Alvarez G, Li S, Fernandez V (2008) On the security of a new image encryption scheme based on chaotic map lattices. CHAOS: Interdiscip J Nonlinear Sci 18(3):033112
Bauer DP (2022) InterPlanetary file system. In: Getting started with ethereum. Apress, Berkeley, pp 83–96
Belazi A, El-Latif AAA, Belghith S (2016) A novel image encryption scheme based on substitution-permutation network and chaos. Signal Process 128:155–170
Chai X, Bi J, Gan Z, Liu X, Zhang Y, Chen Y (2020) Color image compression and encryption scheme based on compressive sensing and double random encryption strategy. Signal Process 176:107684
Chai X, Chen Y, Broyde L (2017) A novel chaos-based image encryption algorithm using DNA sequence operations. Opt Lasers Eng 88:197–213
Chen G, Mao Y, Chui CK (2004) A symmetric image encryption scheme based on 3D chaotic cat maps. Chaos, Solitons Fractals 21.3:749–761
Dai HN, Zheng Z, Zhang Y (2019) Blockchain for internet of things: a survey. IEEE Internet Things J 6(5):8076–8094
Elkandoz MT, Alexan W (2022) Image encryption based on a combination of multiple chaotic maps. Multimed Tools Appl, 1–22
Farwa S, Shah T, Muhammad N, Bibi N, Jahangir A, Arshad S (2017) An image encryption technique based on chaotic S-box and Arnold transform. Int J Adv Comput Sci Appl 8(6):360–364
Fu C, Zhang G-y, Zhu M, Chen Z, Lei Wei-min (2018) A new chaos-based color image encryption scheme with an efficient substitution keystream generation strategy. Security and Communication Networks, 2018
Geetha S, Punithavathi P, Infanteena AM, Sindhu SS (2018) A literature review on image encryption techniques. Int J Inform Secur Privacy (IJISP) 12(3):42–83
Hu X, Wei L, Chen W, Chen Q, Guo Y (2020) Color image encryption algorithm based on dynamic chaos and matrix convolution. IEEE Access 8:12452–12466
Hua Z, Zhou B, Zhou Y (2017) Sine-transform-based chaotic system with FPGA implementation. IEEE Trans Industr Electron 65(3):2557–66
Hua Z, Zhou B, Zhou Y (2018) Sine chaotification model for enhancing chaos and its hardware implementation. IEEE Trans Industr Electron 66 (2):1273–84
Javan K, Akbar A, Shoeibi A, Zare A, Izadi NH, Jafari M, Alizadehsani R, Moridian P, Mosavi A, Rajendra Acharya U, Nahavandi S (2021) Design of adaptive-robust controller for multi-state synchronization of chaotic systems with unknown and time-varying delays and its application in secure communication. Sensors 21(1):254
Javan AAK, Jafari M, Shoeibi A, Zare A, Khodatars M, Ghassemi N, Alizadehsani R, Gorriz JM (2021) Medical images encryption based on adaptive-robust multi-mode synchronization of chen hyper-chaotic systems. Sensors 21 (11):3925
Khan PW, Byun Y (2020) A blockchain-based secure image encryption scheme for the industrial. Intern Things Entropy 22(2):175
Khan M, Masood F (2019) A novel chaotic image encryption technique based on multiple discrete dynamical maps. Multimed Tools Appl 78 (18):26203–26222
Lerner S (2015) Dagcoin draft. Online manuscript
Li Y, Cao B, Peng M, Zhang L, Zhang L, Feng D, Yu J (2019) Direct acyclic graph based blockchain for internet of things: Performance and security analysis. arXiv:1905.10925
Li C, Li S, Asim M, Nunez J, Alvarez G, Chen G (2009) On the security defects of an image encryption scheme. Image Vis Comput 27 (9):1371–81
Li C, Liu Y, Xie T, Chen MZQ (2013) Breaking a novel image encryption scheme based on improved hyperchaotic sequences. Nonlin Dynam 73 (3):2083–2089
Liu L, Miao S (2017) An image encryption algorithm based on Baker map with varying parameter. Multimed Tools Appl 76(15):16511–16527
Lu Q, Zhu C, Deng X (2020) An efficient image encryption scheme based on the LSS chaotic map and single S-box. IEEE Access 8:25664–25678
Mohanty SN, Ramya KC, Sheeba Rani S, Gupta D, Shankar K, Lakshmanaprabu SK, Khanna A (2020) An efficient lightweight integrated Blockchain (ELIB) model for IoT security and privacy. Futur Gener Comput Syst 102:1027–1037
Nkandeu YPK, Tiedeu A (2019) An image encryption algorithm based on substitution technique and chaos mixing. Multimed Tools Appl 78 (8):10013–10034
Orhan K, Bayrakdar IS, Celik O, Ayan B, Polat E (2021) Can the blockchain-enabled interplanetary file system (Block-IPFS) be a solution for securely transferring imaging data for artificial intelligence research in oral and maxillofacial radiology? Imaging Sci Dent 51(3):337–339
Parvaz R, Zarebnia M (2018) A combination chaotic system and application in color image encryption. Opt Laser Technol 101:30–41
Popov S (2018) The tangle. White paper, 1(3)
Qian X, Qi Y, Li Q, Liu Q, Wu Y, Wang W (2021) A novel color image encryption algorithm based on three-dimensional chaotic maps and reconstruction techniques. IEEE Access 9:61334–61345
Sadeghi D, Shoeibi A, Ghassemi N, Moridian P, Khadem A, Alizadehsani R, Teshnehlab M et al (2022) An overview of artificial intelligence techniques for diagnosis of Schizophrenia based on magnetic resonance imaging modalities: methods, challenges, and future works. Computers in Biology and Medicine, 105554
Shen M, Deng Y, Zhu L, Du X, Guizani N (2019) Privacy-preserving image retrieval for medical IoT systems: a blockchain-based approach. IEEE Netw 33(5):27–33
Shoeibi A, Ghassemi N, Heras J, Rezaei M, Gorriz JM (2022) Automatic diagnosis of myocarditis in cardiac magnetic images using CycleGAN and deep PreTrained models. In: International work-conference on the interplay between natural and artificial computation. Springer, Cham, pp 145–155
Shoeibi A, Ghassemi N, Khodatars M, Moridian P, Khosravi A, Zare A, Gorriz JM, Chale-Chale AH, Khadem A, Acharya UR (2022) Automatic diagnosis of schizophrenia and attention deficit hyperactivity disorder in rs-fMRI modality using convolutional autoencoder model and interval type-2 fuzzy regression. arXiv:2205.15858
Silvano WF, Marcelino R (2020) Iota tangle: a cryptocurrency to communicate internet-of-things data. Futur Gener Comput Syst 112:307–319
Singh P, Yadav AK, Singh K (2017) Phase image encryption in the fractional Hartley domain using Arnold transform and singular value decomposition. Opt Lasers Eng 91:187–195
Szydlo M (2004) Merkle tree traversal in log space and time. Eurocrypt 3027:541–554
Wang X, Zhao H, Wang M (2019) A new image encryption algorithm with nonlinear-diffusion based on multiple coupled map lattices. Opt Laser Technol 115:42–57
Wang X, Zhu X, Wu X, Zhang Y (2018) Image encryption algorithm based on multiple mixed hash functions and cyclic shift. Opt Lasers Eng 107:370–379
Wang X, Zhu X, Zhang Y (2018) An image encryption algorithm based on Josephus traversing and mixed chaotic map. IEEE Access 6:23733–23746
Wu X, Zhu B, Hu Y, Ran Y (2017) A novel color image encryption scheme using rectangular transform-enhanced chaotic tent maps. IEEE Access 5:6429–6436
Xie EY, Li C, Yu S, Jinhu L (2017) On the cryptanalysis of Fridrich’s chaotic image encryption scheme. Signal Process 132:150–154
Yi L, Tong X, Wang Z, Zhang M, Zhu H, Liu J (2019) A novel block encryption algorithm based on chaotic S-box for wireless sensor network. IEEE Access 7:53079–90
Zhou N, Hu Y, Gong L, Li G (2017) Quantum image encryption scheme with iterative generalized Arnold transforms and quantum image cycle shift operations. Quantum Inf Process 16(6):164
Zhu C, Sun K (2018) Cryptanalyzing and improving a novel color image encryption algorithm using RT-enhanced chaotic tent maps. IEEE Access 6:18759–18770
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of Interests
The authors declare that they have no conflict of interest.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
B, R., Makhija, N. Secured image storage and transmission technique suitable for IoT using Tangle and a novel image encryption technique. Multimed Tools Appl 82, 36793–36814 (2023). https://doi.org/10.1007/s11042-023-14794-3
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-14794-3