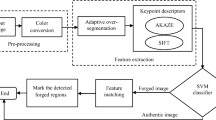
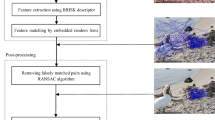
Abstract
The copy-move forgery involves copying a semantically part from an image and pasting it into a different location within the same image to change the context of the image and deceive people. The copy-move forensic detectors authenticate the image and localize similar regions without identifying which region is original or forged. Because the forged region is replicated from another region of the same image, its characteristics have been inherited, making it difficult to distinguish between the original and forged regions. This paper proposes two approaches as a second stage, after localizing duplicated regions, to distinguish between source and destination regions. The adjacent pixels in images are non-independent and have some correlations that would be destroyed due to modifying the image. The deviation of these correlations would expose traces left due to the image forgery and is evaluated by the Joint Probability Matrix (JPM) in the first approach and by the Local Binary Pattern (LBP) in the second approach. Both approaches employ Jensen Shannon Divergence (JSD) to measure the correlation between feature vectors and generate similarity scores to distinguish between the source and the destination regions. The proposed approaches were demonstrated by employing the GRIP dataset with six post-processing operations to conceal forgery. The experiments exhibit a high accuracy rate of 96.25%.
















Similar content being viewed by others
Data availability
The datasets generated during and/or analysed during the current study are available in the figshare repository, https://doi.org/10.6084/m9.figshare.c.6221192.v1
References
Beli ILK, Guo C (2017) Enhancing face identification using local binary patterns and K-nearest neighbors. J Imaging 3:. https://doi.org/10.3390/jimaging3030037
Chen J, Liao X, Qin Z (2021) Identifying tampering operations in image operator chains based on decision fusion. Signal Process Image Commun 95:116287. https://doi.org/10.1016/j.image.2021.116287
Cozzolino D, Gragnaniello D, Verdoliva L (2013) A novel framework for image forgery localization
Cozzolino D, Poggi G, Verdoliva L (2014) Copy-move forgery detection based on Patchmatch. Int Conf image process 5312–5316
Dekking FM, Kraaikamp C, Lopuhaä HP, Meester LE (2005) A modern introduction to probability and statistics. Springer London, London. https://doi.org/10.1007/1-84628-168-7
Dong J, Wang W, Tan T, Shi YQ (2009) Run-length and edge statistics based approach for image splicing detection. In: lecture notes in computer science (including subseries lecture notes in artificial intelligence and lecture notes in bioinformatics). Pp 76–87
Ferreira WD, Ferreira CBR, da Cruz JG, Soares F (2020) A review of digital image forensics. Comput Electr Eng 85:. https://doi.org/10.1016/j.compeleceng.2020.106685
Fridrich J (2004) Feature-based Steganalysis for JPEG images and its implications for future Design of Steganographic Schemes. In: lecture notes in computer science (including subseries lecture notes in artificial intelligence and lecture notes in bioinformatics). Pp 67–81
Han JG, Park TH, Moon YH, Eom IK (2016) Efficient Markov feature extraction method for image splicing detection using maximization and threshold expansion. J Electron Imaging 25:023031. https://doi.org/10.1117/1.jei.25.2.023031
He Z, Lu W, Sun W, Huang J (2012) Digital image splicing detection based on Markov features in DCT and DWT domain. Pattern Recogn 45:4292–4299. https://doi.org/10.1016/j.patcog.2012.05.014
Hu N, Ma H, Zhan T (2020) Finger vein biometric verification using block multi-scale uniform local binary pattern features and block two-directional two-dimension principal component analysis. Optik (Stuttg) 208:163664. https://doi.org/10.1016/j.ijleo.2019.163664
Image Processing Research Group of University Federico II of Naples GRIP Dataset (n.d.) https://www.grip.unina.it/download/prog/CMFD/CMFDdb_grip.zip. Accessed 14 Sep 2022
Ingemar JC, Miller ML, Jeffrey AB, Fridrich J, Kalker T (2008) Digital watermarking and steganography, 2nd ed. Elsevier, https://doi.org/10.1016/B978-0-12-372585-1.X5001-3
Jaiswal AK, Srivastava R (2019) Image splicing detection using deep residual network. SSRN Electronic Journal. https://doi.org/10.2139/ssrn.3351072
Jin X, Wu L, Li X, Chen S, Peng S, Chi J, Ge S, Song C, Zhao G (2018) Predicting aesthetic score distribution through cumulative Jensen-Shannon divergence. 32nd AAAI Conf Artif Intell AAAI 2018 77–84
Johnson MK, Farid H (2005) Exposing digital forgeries by detecting inconsistencies in lighting. In: Proceedings of the 7th workshop on multimedia and security - MM&sec ‘05. ACM Press, New York, New York, USA, pp. 1–10
Kaur C, Kanwal N (2019) An analysis of image forgery detection techniques. Stat Optim Inf Comput 7:486–500. https://doi.org/10.19139/soic.v7i2.542
Kee E, Farid H (2011) A perceptual metric for photo retouching. Proc Natl Acad Sci 108:19907–19912. https://doi.org/10.1073/pnas.1110747108
Khaleefah SH, Mostafa SA, Mustapha A, Nasrudin MF (2019) The ideal effect of Gabor filters and uniform local binary pattern combinations on deformed scanned paper images. J King Saud Univ - Comput Inf Sci https://doi.org/10.1016/j.jksuci.2019.07.012
Koshy L, Praylashyry S (2020) Copy-move forgery detection and performance analysis of feature detectors. In: 2020 International Conference on Communication and Signal Processing (ICCSP), Chennai, India, pp 41–45. https://doi.org/10.1109/ICCSP48568.2020.9182066
Li Y, Liu M (2018) Aerial image classification using color coherence vectors and rotation uniform invariant LBP descriptors. In: 2018 IEEE 3rd Advanced Information Technology, Electronic and Automation Control Conference (IAEAC), Chongqing, China, pp 653–656. https://doi.org/10.1109/IAEAC.2018.8577881
Li Y, Xie Y (2020) Is a picture worth a thousand words? An empirical study of image content and social media engagement. J Mark Res 57:1–19. https://doi.org/10.1177/0022243719881113
Li Y, Zhou J (2019) Fast and effective image copy-move forgery detection via hierarchical feature point matching. IEEE Trans Inf Forensic Secur 14:1307–1322. https://doi.org/10.1109/TIFS.2018.2876837
Li Z, Liu G, Yang Y, You J (2012) Scale- and rotation-invariant local binary pattern using scale-adaptive Texton and subuniform-based circular shift. IEEE Trans Image Process 21:2130–2140. https://doi.org/10.1109/TIP.2011.2173697
Liang Z, Yang G, Ding X, Li L (2015) An efficient forgery detection algorithm for object removal by exemplar-based image Inpainting. J Vis Commun Image Represent 30:75–85. https://doi.org/10.1016/j.jvcir.2015.03.004
Liao X, Li K, Zhu X, Liu KJR (2020) Robust detection of image operator chain with two-stream convolutional neural network. IEEE J Sel Top Signal Process 14:955–968. https://doi.org/10.1109/JSTSP.2020.3002391
Liao X, Chen J, Chen J (2021) Image source identification with known post-processed based on convolutional neural network. Signal Process Image Commun 99:116438. https://doi.org/10.1016/j.image.2021.116438
Liu Q, Chen Z (2015) Improved Approaches with Calibrated Neighboring Joint Density to Steganalysis and Seam-Carved Forgery Detection in JPEG Images ACM Trans Intell Syst Technol 5:. https://doi.org/10.1145/2560365
Liu L, Fieguth P, Guo Y, Wang X, Pietikäinen M (2017) Local binary features for texture classification: taxonomy and experimental study. Pattern Recogn 62:135–160. https://doi.org/10.1016/j.patcog.2016.08.032
Lu J, Henchion M, Namee B, Mac (2020) Diverging Divergences: Examining Variants of Jensen Shannon Divergence for Corpus Comparison Tasks. Lr 2020 - 12th Int Conf Lang Resour Eval Conf Proc 2:6740–6744
Mahmood T, Mehmood Z, Shah M, Saba T (2018) A robust technique for copy-move forgery detection and localization in digital images via stationary wavelet and discrete cosine transform. J Vis Commun Image Represent 53:202–214. https://doi.org/10.1016/j.jvcir.2018.03.015
Malik MSA, Zahra Q, Khan IU, Awais M, Qiao G (2020) An efficient retinal vessels biometric recognition system by using multi-scale local binary pattern descriptor. J Med Imaging Heal Inf 10:2481–2489. https://doi.org/10.1166/jmihi.2020.3180
Matern F, Riess C, Stamminger M (2020) Gradient-based illumination description for image forgery detection. IEEE Trans Inf Forensics Secur 15:1303–1317. https://doi.org/10.1109/TIFS.2019.2935913
Moghaddasi Z, Jalab HA, Noor RM (2019) Image splicing forgery detection based on low-dimensional singular value decomposition of discrete cosine transform coefficients. Neural Comput & Applic 31:7867–7877. https://doi.org/10.1007/s00521-018-3586-y
Nguyen HV, Vreeken J (2015) Non-parametric Jensen-Shannon divergence. Lect Notes Comput Sci (including Subser Lect Notes Artif Intell Lect Notes Bioinf) 9285:173–189. https://doi.org/10.1007/978-3-319-23525-7_11
Ojala T, Pietikainen M, Maenpaa T (2002) Multiresolution gray-scale and rotation invariant texture classification with local binary patterns. IEEE Trans Pattern Anal Mach Intell 24:971–987. https://doi.org/10.1109/TPAMI.2002.1017623
Pavlichin DS, Weissman T (2016) Chained Kullback-Leibler Divergences. IEEE Int Symp Inf Theory - Proc 2016-Augus:580–584. https://doi.org/10.1109/ISIT.2016.7541365
Peyret R, Bouridane A, Khelifi F, Tahir MA, Al-Maadeed S (2018) Automatic classification of colorectal and prostatic histologic tumor images using multiscale multispectral local binary pattern texture features and stacked generalization. Neurocomputing 275:83–93. https://doi.org/10.1016/j.neucom.2017.05.010
Pham NT, Lee JW, Kwon GR, Park CS (2019) Efficient image splicing detection algorithm based on Markov features. Multimed Tools Appl 78:12405–12419. https://doi.org/10.1007/s11042-018-6792-9
Pishro-Nik H (2015) Introduction to probability, statistics, and random processes. In: Wikipedia. https://www.probabilitycourse.com/chapter3/3_1_3_pmf.php. Accessed 25 Apr 2021
Priya TSV, Sanchez GV, Raajan NR (2018) Facial recognition system using local binary patterns (LBP). Int J Pure Appl Math 119:1895–1899
Rahman T, Rohan R, Pal D, Kanthamanon P (2021) Human factors in cybersecurity: a scoping review. ACM Int Conf Proceed Ser https://doi.org/10.1145/3468784.3468789
Rathgeb C, Botaljov A, Stockhardt F, Isadskiy S, Debiasi L, Uhl A, Busch C (2020) PRNU-based detection of facial retouching. IET Biomet 9:154–164. https://doi.org/10.1049/iet-bmt.2019.0196
Rouder JN, Morey RD (2019) Teaching Bayes’ theorem: strength of evidence as predictive accuracy. Am Stat 73:186–190. https://doi.org/10.1080/00031305.2017.1341334
Sadeghi S, Dadkhah S, Jalab HA, Mazzola G, Uliyan D (2018) State of the art in passive digital image forgery detection: copy-move image forgery. Pattern Anal Applic 21:291–306. https://doi.org/10.1007/s10044-017-0678-8
Shah A, El-Alfy ES (2018) Image splicing forgery detection using DCT coefficients with multi-scale LBP. 2018 Int Conf Comput Sci Eng ICCSE 2018 - proc 1–6. https://doi.org/10.1109/ICCSE1.2018.8374214
Shah H, Shinde P, Kukreja J (2013) Retouching detection and Steganalysis. Int J Eng Innov Res 2:487–490
Shi YQ, Chen C, Chen W (2007) A natural image model approach to splicing detection. In: proceedings of the 9th workshop on multimedia & security - MM&sec ‘07. ACM Press, New York, New York, USA, p 51
Shi YQ, Chen C, Chen W (2007) A Markov process based approach to effective attacking JPEG steganography. In: Information hiding. Springer Berlin Heidelberg, Berlin, Heidelberg, pp 249–264
Srivastava P, Khare A (2018) Utilizing multiscale local binary pattern for content-based image retrieval. Multimed Tools Appl 77:12377–12403. https://doi.org/10.1007/s11042-017-4894-4
Tralic D, Zupancic I, Grgic S, Grgic M (2013) CoMoFoD - new database for copy-move forgery detection. In: Proceedings Elmar - International Symposium Electronics in Marine
Wang R, Lu W, Li J, Xiang S, Zhao X, Wang J (2018) Digital image splicing detection based on Markov features in QDCT and QWT domain. Int J Digit Crime Forensic 10:90–107. https://doi.org/10.4018/IJDCF.2018100107
Yohannan RP, Manuel M (2016) Detection of copy-move forgery based on Gabor filter. Proc 2nd IEEE Int Conf Eng Technol ICETECH 2016 629–634. https://doi.org/10.1109/ICETECH.2016.7569326
Zeebaree DQ, Abdulazeez AM, Zebari DA, Haron H, Hamed HNA (2020) Multi-level fusion in ultrasound for Cancer detection based on uniform LBP features. Comput Mater Contin 66:3363–3382. https://doi.org/10.32604/cmc.2021.013314
Zhang J, Zhao Y, Su Y (2009) A new approach merging markov and DCT features for image splicing detection. In: 2009 IEEE International Conference on Intelligent Computing and Intelligent Systems, Shanghai, China, pp 390–394. https://doi.org/10.1109/ICICISYS.2009.5357642
Zhang D, Liang Z, Yang G, Li Q, Li L, Sun X (2018) A robust forgery detection algorithm for object removal by exemplar-based image Inpainting. Multimed Tools Appl 77:11823–11842. https://doi.org/10.1007/s11042-017-4829-0
Zhe S, Peng S (2020) Authentication of splicing manipulation by exposing inconsistency in color shift. Multimed Tools Appl 79:8235–8248. https://doi.org/10.1007/s11042-019-08565-2
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
All authors certify that they have no affiliations with or involvement in any organization or entity with any financial or non-financial interest in the subject matter or materials discussed in this manuscript.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Iseed, S.Y., Mahmoud, K.W. Forensic approach for distinguishing between source and destination regions in copy-move forgery. Multimed Tools Appl 82, 31181–31210 (2023). https://doi.org/10.1007/s11042-023-14824-0
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-14824-0