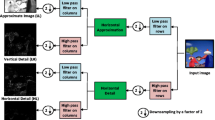
Abstract
For image steganography, it is necessary to improve the quality of the reconstructed image and stego image as high as possible while maintaining the security of the system. To achieve this goal, we propose a novelty image steganography via deep-based compressive sensing (CS) for the reconstructed image and directional lifting wavelet transform (DLWT) for the stego image. The plain image is first randomly under-sampled and diffused by the measurement matrix and simulated noise to generate the secret image. And the above two matrices were created using a logistic map with two initial values. Then, we embed the secret image into the DLWT domain of the carrier image by singular value decomposition (SVD), resulting in the meaningful stego image. Finally, for enhancing the quality of the reconstructed image from the extracted secret image, we present the deep-based CS reconstruction algorithm. Experimental results verify the effectiveness that the proposed scheme can achieve visual quality, robustness, and security.















Similar content being viewed by others
Data Availability
The data that support the findings of this study are available in [CVG-UGR] at [https://ccia.ugr.es/cvg/dbimagenes/index.php].
References
Cui J, Zhang P, Li S, Zheng L, Bao C, Xia J, Li X (2021) Multitask identity-aware image steganography via minimax optimization. IEEE Trans Image Process 30:8567–8579. https://doi.org/10.1109/TIP.2021.3107999
Kadhim IJ, Premaratne P, Vial PJ (2020) Improved image steganography based on super-pixel and coefficient-plane-selection. Signal Process 171:107481. https://doi.org/10.1016/j.sigpro.2020.107481
Kadhim IJ, Premaratne P, Vial PJ, Halloran B (2019) Comprehensive survey of image steganography: Techniques, evaluations, and trends in future research. Neurocomputing 335:299–326. https://doi.org/10.1016/j.neucom.2018.06.075
Yang H, Kot AC (2007) Pattern-based data hiding for binary image authentication by connectivity-preserving. IEEE Trans Multimed 9(3):475–486. https://doi.org/10.1109/TMM.2006.887990
Liao X, Wen Q, Zhang J (2012) A novel steganographic method with four-pixel differencing and exploiting modification direction. IEICE Trans Fund Electron Commun Comput Sci E95.A(7):1189–1192. https://doi.org/10.1587/transfun.E95.A.1189
Liao X, Wen Q, Zhang J (2013) Improving the adaptive steganographic methods based on modulus function. IEICE Trans Fund Electron Commun Comput Sci E96.A(12):2731–2734. https://doi.org/10.1587/transfun.E96.A.2731
Parah SA, Sheikh JA, Akhoon JA, Loan NA, Bhat GM (2018) Information hiding in edges: A high capacity information hiding technique using hybrid edge detection. Multimed Tools Appl 77(1):185–207. https://doi.org/10.1007/s11042-016-4253-x
Yin Z, Xiang Y, Zhang X (2020) Reversible data hiding in encrypted images based on multi-msb prediction and huffman coding. IEEE Trans Multimed 22(4):874–884. https://doi.org/10.1109/TMM.2019.2936314
Mukherjee (Ganguly) N., Paul G, Saha SK (2021) Two-point fft-based high capacity image steganography using calendar based message encoding. Inf Sci 552:278–290. https://doi.org/10.1016/j.ins.2020.11.044
Liao X, Yu Y, Li B, Li Z, Qin Z (2020) A new payload partition strategy in color image steganography. IEEE Trans Circ Syst Vid Technol 30(3):685–696. https://doi.org/10.1109/TCSVT.2019.2896270
Liao X, Yin J, Chen M, Qin Z (2022) Adaptive payload distribution in multiple images steganography based on image texture features. IEEE Trans Depend Secur Comput 19(2):897–911. https://doi.org/10.1109/TDSC.2020.3004708
Xiong L, Zhong X, Yang C.-N. (2020) Dwt-sisa: a secure and effective discrete wavelet transform-based secret image sharing with authentication. Signal Process 173:107571. https://doi.org/10.1016/j.sigpro.2020.107571
Evsutin O, Melman A, Meshcheryakov R (2021) Algorithm of error-free information embedding into the dct domain of digital images based on the qim method using adaptive masking of distortions. Signal Process 179:107811. https://doi.org/10.1016/j.sigpro.2020.107811
Yang J, Ruan D, Huang J, Kang X, Shi Y.-Q. (2020) An embedding cost learning framework using gan. IEEE Trans Inf Forens Secur 15:839–851. https://doi.org/10.1109/TIFS.2019.2922229
Ray B, Mukhopadhyay S, Hossain S, Ghosal SK, Sarkar R (2021) Image steganography using deep learning based edge detection. Multimed Tools Appl 80(24):33475–33503. https://doi.org/10.1007/s11042-021-11177-4
Srinivasu LN, Veeramani V (2022) Cnn based ”text in image” steganography using slice encryption algorithm and lwt. Optik 265:169398. https://doi.org/10.1016/j.ijleo.2022.169398
Hsu L-Y, Hu H-T (2017) Robust blind image watermarking using crisscross inter-block prediction in the dct domain. J Vis Commun Image Represent 46:33–47. https://doi.org/10.1016/j.jvcir.2017.03.009
Zhang H, Hu L (2019) A data hiding scheme based on multidirectional line encoding and integer wavelet transform. Signal Process Image Commun 78:331–344. https://doi.org/10.1016/j.image.2019.07.019
Chai X, Wu H, Gan Z, Zhang Y, Chen Y, Nixon KW (2020) An efficient visually meaningful image compression and encryption scheme based on compressive sensing and dynamic lsb embedding. Opt Lasers Eng 124:105837. https://doi.org/10.1016/j.optlaseng.2019.105837
Chen Z, Hou X, Shao L, Wang S (2019) Revising regularisation with linear approximation term for compressive sensing improvement. Electron Lett 55(7):384–386. https://doi.org/10.1049/el.2018.8019
Chen Z, Hou X, Gong C, Qian X (2016) Compressive sensing reconstruction for compressible signal based on projection replacement. Multimed Tools Appl 75(5):2565–2578. https://doi.org/10.1007/s11042-015-2578-5
Zhang B, Xiao D, Xiang Y (2020) Robust coding of encrypted images via 2d compressed sensing. IEEE Trans Multimed:1–1. https://doi.org/10.1109/TMM.2020.3014489
Zhu L, Song H, Zhang X, Yan M, Zhang T, Wang X et al (2020) A robust meaningful image encryption scheme based on block compressive sensing and svd embedding. Signal Process 175:107629. https://doi.org/10.1016/j.sigpro.2020.107629
Jiang D, Liu L, Zhu L, Wang X, Rong X, Chai H (2021) Adaptive embedding: A novel meaningful image encryption scheme based on parallel compressive sensing and slant transform. Signal Process 188:108220. https://doi.org/10.1016/j.sigpro.2021.108220
Chen Z, Hou X, Qian X, Gong C (2017) Efficient and robust image coding and transmission based on scrambled block compressive sensing. IEEE Trans Multimed 20(7):1610–1621. https://doi.org/10.1109/TMM.2017.2774004
Wang X, Liu C, Jiang D (2021) A novel triple-image encryption and hiding algorithm based on chaos, compressive sensing and 3d dct. Inf Sci 574:505–527. https://doi.org/10.1016/j.ins.2021.06.032
Mun S, Fowler JE (2009) Block compressed sensing of images using directional transforms. In: 16th IEEE International conference on image processing. https://doi.org/10.1109/ICIP.2009.5414429, pp 3021–3024
Dong W, Shi G, Li X, Ma Y, Huang F (2014) Compressive sensing via nonlocal low-rank regularization. IEEE Trans Image Process 23(8):3618–3632. https://doi.org/10.1109/TIP.2014.2329449
Chen Z, Guo W, Feng Y, Li Y, Zhao C, Ren Y et al (2021) Deep-learned regularization and proximal operator for image compressive sensing. IEEE Trans Image Process:1–1. https://doi.org/10.1109/TIP.2021.3088611
Metzler C, Mousavi A, Baraniuk R (2017) Learned d-amp: Principled neural network based compressive image recovery. In: Advances in neural information processing systems, pp 1772–1783
Chen Z, Hou X, Shao L, Gong C, Qian X, Huang Y et al (2020) Compressive sensing multi-layer residual coefficients for image coding. IEEE Trans Circ Syst Vid Technol 30(4):1109–1120. https://doi.org/10.1109/TCSVT.2019.2898908
Metzler CA, Maleki A, Baraniuk RG (2016) From denoising to compressed sensing. IEEE Trans Inf Theory 62(9):5117–5144. https://doi.org/10.1109/TIT.2016.2556683
Zhang J, Ghanem B (2018) Ista-net: Interpretable optimization-inspired deep network for image compressive sensing. In: 2018 IEEE/CVF conference on computer vision and pattern recognition. https://doi.org/10.1109/CVPR.2018.00196, pp 1828–1837
Zhang Z, Liu Y, Liu J, Wen F, Zhu C (2021) Amp-net: Denoising-based deep unfolding for compressive image sensing. IEEE Trans Image Process 30:1487–1500. https://doi.org/10.1109/TIP.2020.3044472
Zhang J, Zhao C, Gao W (2020) Optimization-inspired compact deep compressive sensing. IEEE J Select Topics Signal Process 14(4):765–774. https://doi.org/10.1109/JSTSP.2020.2977507
Rajendran S, Doraipandian M (2017) Chaotic map based random image steganography using lsb technique. Int J Netw Secur 19(4):593–598. https://doi.org/10.6633/IJNS.201707.19(4).12
Swain G (2016) A steganographic method combining lsb substitution and pvd in a block. Procedia Comput Sci 85:39–44. https://doi.org/10.1016/j.procs.2016.05.174
Kumar V, Kumar D (2018) A modified dwt-based image steganography technique. Multimed Tools Appl 77(11):13279–13308. https://doi.org/10.1007/s11042-017-4947-8
Saidi M, Hermassi H, Rhouma R, Belghith S (2017) A new adaptive image steganography scheme based on dct and chaotic map. Multimed Tools Appl 76(11):13493–13510. https://doi.org/10.1007/s11042-016-3722-6
Wang H, Xiao D, Li M, Xiang Y, Li X (2019) A visually secure image encryption scheme based on parallel compressive sensing. Signal Process 155:218–232. https://doi.org/10.1016/j.sigpro.2018.10.001
Bassham LE III, Rukhin AL, Soto J, Nechvatal JR, Smid ME, Barker EB et al (2010) Sp 800-22 rev. 1a. a statistical test suite for random and pseudorandom number generators for cryptographic applications. National Institute of Standards & Technology
Acknowledgements
This research was sponsored in part by the National Natural Science Foundation of China (Grant Nos. 62002327, 61976190, 62073294, 61872286), Natural Science Foundation of Zhejiang Province (Grant No. LQ21F020017, LZ21F030003), and agricultural and social development foundation of Hangzhou (Grant No. 202004A07).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of Interests
The authors have no relevant financial or non-financial interests to disclose.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Chen, Z., Ma, C., Feng, Y. et al. Directional lifting wavelet transform domain image steganography with deep-based compressive sensing. Multimed Tools Appl 82, 40891–40912 (2023). https://doi.org/10.1007/s11042-023-14939-4
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-14939-4