Abstract
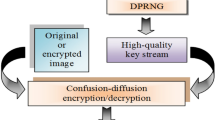
Currently, chaos-based cryptosystems are widely used for the reason of protecting sensitive data. Various different chaos-based cryptography systems with software implementation have been studied and documented in the literature. Nevertheless, with the fast growth of the internet and connected objects, the development of hardware secure and low-resource cryptographic systems is required. This article presents an FPGA implementation of a block-cipher image encryption scheme based on different three-dimensional chaotic systems and genetic operations. Our approach is to define a novel approach to block-cipher hardware systems while basing it on the biological characteristics of DNA and chaos. Firstly, a robust chaos-based PRNG based on four 3D chaotic maps is proposed to create high-quality keys. The generated key sequences validate with no fail the NIST SP 800–22 test suite. Furthermore, some biological operations are added in the encryption process such as DNA biological algebraic operations to strengthen the confusion process and improve the complexity of the generated keys. Verily, a very secure block-cipher method is created to perform encryption and decryption of different images. The cryptosystem is implemented and evaluated on a Xilinx ZedBoard Zynq Evaluation and Development Kit platform. The proposed hardware architecture is capable of securing different sizes of gray-scale, medical and RGB color images. As a result, a new hardware architecture is implemented that accomplishes numerical image confusion and diffusion with a good frequency of 194.906 MHz and high throughput of 49,895,936 Mbps. Furthermore, the simulation results show that the encryption system is capable of higher security against cryptographic attacks. The entropy has reached a new high of 7.9998. A comparative study of the suggested algorithm with various new encryption methods shows that our system produces good results and provides better solutions than the state-of-the-art designs.
Access this article
Rent this article via DeepDyve


















Similar content being viewed by others
Data availability
Data are not shared.
References
Ajili S et al (2014) Joint Watermarking\Encryption image for safe transmission: Application on medical imaging, Global summit on Computer & Information Technology (GSCIT). IEEE 2014. https://doi.org/10.1109/GSCIT.2014.6970110
Ajili S, Hajjaji MA, Mtibaa A (2016) Combining watermarking and encryption algorithm for medical image safe transfer: method based on DCT. International Journal of Signal and Imaging Systems Engineering 9.4–5. https://doi.org/10.1504/IJSISE.2016.078269
Al-Maadeed TA et al (2021) A image encryption algorithm based on chaotic Lorenz system and novel primitive polynomial S-boxes. Multimedia Tools and Applications 80.16. https://doi.org/10.1007/s11042-021-10695-5
Al-Musawi WA, Wali WA, Al-Ibadi MAA (2022) Field-programmable gate array design of image encryption and decryption using Chua’s chaotic masking. International Journal of Electrical and Computer Engineering 12.3. https://doi.org/10.11591/ijece.v12i3.pp2414-2424
Bansal, Monika, et al (2021) Transfer learning for image classification using VGG19: Caltech-101 image data set. Journal of Ambient Intelligence and Humanized Computing. https://doi.org/10.1007/s12652-021-03488-z
Bansal M, Kumar M, Kumar M (2021) 2D object recognition: a comparative analysis of SIFT, SURF and ORB feature descriptors. Multimedia Tools and Applications 80.12. https://doi.org/10.1007/s11042-021-10646-0
Belazi A et al (2019) Novel medical image encryption scheme based on chaos and DNA encoding. IEEE access 7. https://doi.org/10.1109/ACCESS.2019.2906292
Dagadu JC, J-P Li, Aboagye EO (2019) Medical image encryption based on hybrid chaotic DNA diffusion. Wireless Personal Communications 108.1. https://doi.org/10.1007/s11277-019-06420-z
Dridi M, Hajjaji MA, Mtibaa A (2016) Hardware implementation of encryption image using xilinx system generator. 2016 17th international conference on sciences and techniques of automatic control and computer engineering (STA). IEEE. https://doi.org/10.1109/STA.2016.7952064
ElBeltagy M et al (2022) Image Encryption Through Rössler System, PRNG S-Box and Recamán's Sequence. 2022 IEEE 12th annual computing and communication workshop and conference (CCWC). IEEE. https://doi.org/10.1109/CCWC54503.2022.9720905
Gafsi M et al (2018) High securing cryptography system for digital image transmission. International conference on the Sciences of Electronics, Technologies of Information and Telecommunications. Springer, Cham. https://doi.org/10.1007/978-3-030-21005-2_30
Gafsi M et al (2021) FPGA hardware acceleration of an improved chaos-based cryptosystem for real-time image encryption and decryption. Journal of Ambient Intelligence and Humanized Computing. https://doi.org/10.1007/s12652-021-03555-5
Gafsi M et al (2021) FPGA hardware acceleration of an improved chaos-based cryptosystem for real-time image encryption and decryption. Journal of Ambient Intelligence and Humanized Computing. https://doi.org/10.1007/s12652-021-03555-5
Gafsi M et al (2022) Hardware implementation of the Haar 2D discrete wavelet transform with an application to image watermarking. 2022 5th International Conference on Advanced Systems and Emergent Technologies (IC_ASET). IEEE. https://doi.org/10.1109/IC_ASET53395.2022.9765864
Gupta BB et al (2021) Blockchain-assisted secure fine-grained searchable encryption for a cloud-based healthcare cyber-physical system. IEEE/CAA J Automatica Sinica 8(12):10.1109/JAS.2021.1004003
Hao J et al (2021) A New Fractional Chaotic System and its application in image encryption with DNA mutation. IEEE Access 9. https://doi.org/10.1109/ACCESS.2021.3069977
Hore A, Ziou D (2010) Image quality metrics: PSNR vs. SSIM. 2010 20th international conference on pattern recognition. IEEE. https://doi.org/10.1109/ICPR.2010.579
Kaur M et al (2021) Secure and energy efficient-based E-health care framework for green internet of things. IEEE Transactions on Green Communications and Networking 5.3. https://doi.org/10.1109/TGCN.2021.3081616
Masood F et al (2020) A novel privacy approach of digital aerial images based on mersenne twister method with DNA genetic encoding and chaos. Remote Sensing 12.11. https://doi.org/10.3390/rs12111893
Mirsadeghi F, Rafsanjani MK, Gupta BB (2021) A trust infrastructure based authentication method for clustered vehicular ad hoc networks. Peer-to-Peer Networking and Applications 14.4. https://doi.org/10.1007/s12083-020-01010-4
Nguyen GN et al (2021) Secure blockchain enabled Cyber–physical systems in healthcare using deep belief network with ResNet model. Journal of parallel and distributed computing 153. https://doi.org/10.1016/j.jpdc.2021.03.011
Niu Y, Zheng Z, Zhang X (2020) An image encryption approach based on chaotic maps and genetic operations." Multimedia Tools and Applications 79.35. https://doi.org/10.1007/s11042-020-09237-2
Pitman EJG (1939) A note on normal correlation. Biometrika 31.1/2. 9–12. http://www.jstor.com/stable/2334971
Rehman AU et al (2019) A selective cross-substitution technique for encrypting color images using chaos, DNA rules and SHA-512. IEEE Access 7. https://doi.org/10.1109/ACCESS.2019.2951749
Rezk AA et al (2019) Reconfigurable chaotic pseudo random number generator based on FPGA. AEU-international Journal of Electronics and Communications 98. https://doi.org/10.1016/j.aeue.2018.10.024
Rukhin A et al (2001) A statistical test suite for random and pseudorandom number generators for cryptographic applications. Booz-allen and hamilton inc mclean va, 2001. https://csrc.nist.gov/publications/detail/sp/800-22/rev-1a/final
Shaheed K et al (2022) DS-CNN: A pre-trained Xception model based on depth-wise separable convolutional neural network for finger vein recognition. Expert Syst Appl 191. https://doi.org/10.1016/j.eswa.2021.116288
Shaheed K et al (2022) Finger-vein presentation attack detection using depthwise separable convolution neural network. Expert Systems with Applications 198. https://doi.org/10.1016/j.eswa.2022.116786
Shaheed K et al (2022) Recent advancements in finger vein recognition technology: methodology, challenges and opportunities. Information Fusion 79. https://doi.org/10.1016/j.inffus.2021.10.004
Stalin S et al (2019) Fast and secure medical image encryption based on non linear 4D logistic map and DNA sequences (NL4DLM_DNA). Journal of medical systems 43.8. https://doi.org/10.1007/s10916-019-1389-z
Syafalni I et al (2022) Efficient Homomorphic Encryption Accelerator With Integrated PRNG Using Low-Cost FPGA. IEEE Access 10. https://doi.org/10.1109/ACCESS.2022.3143804
Telem K, Nicole A, Fotsin HB, Kengne J (2021) Image encryption algorithm based on dynamic DNA coding operations and 3D chaotic systems. Multimedia Tools and Applications 80.12. https://doi.org/10.1007/s11042-021-10549-0
Tewari A, Gupta BB (2017) Cryptanalysis of a novel ultra-lightweight mutual authentication protocol for IoT devices using RFID tags. The Journal of Supercomputing 73.3. https://doi.org/10.1007/s11227-016-1849-x
Walia S et al (2021) Fusion of handcrafted and deep features for forgery detection in digital images. IEEE Access 9. https://doi.org/10.1109/ACCESS.2021.3096240
Wang X-Y et al (2010) A chaotic image encryption algorithm based on perceptron model. Nonlinear Dynamics 62.3. https://doi.org/10.1007/s11071-010-9749-8
Wang X, Xue W, An J (2021) Image encryption algorithm based on LDCML and DNA coding sequence. Multimedia Tools and Applications 80.1. https://doi.org/10.1007/s11042-020-09688-7
Xu J, Zhao B, Zeming W (2022) Research on color image encryption algorithm based on bit-plane and Chen Chaotic System. Entropy 24. 2. https://doi.org/10.3390/e24020186
Yu C et al (2018) Four-image encryption scheme based on quaternion Fresnel transform, chaos and computer generated hologram. Multimedia Tools and Applications 77.4. https://doi.org/10.1007/s11042-017-4637-6
Yu F et al (2021) Design and FPGA implementation of a pseudo-random number generator based on a Hopfield neural network under electromagnetic radiation. Frontiers in Physics. https://doi.org/10.3389/fphy.2021.690651
Zhang Q, Han J (2021) A novel color image encryption algorithm based on image hashing, 6D hyperchaotic and DNA coding. Multimedia Tools and Applications 80.9. https://doi.org/10.1007/s11042-020-10437-z
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no conflict of interest.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Amdouni, R., Gafsi, M., Abbassi, N. et al. Robust hardware implementation of a block-cipher scheme based on chaos and biological algebraic operations. Multimed Tools Appl 82, 37097–37130 (2023). https://doi.org/10.1007/s11042-023-15027-3
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-15027-3