Abstract
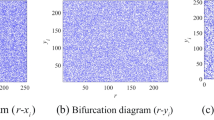
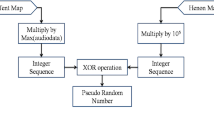
Today, Internet users who share personal and professional data are concerned about the safety of the data. Encryption is one way to safeguard sensitive and private data on internet sites. Encrypting audio data is more challenging than other types of data owing to the correlation between neighbouring samples. Encryption algorithms based on chaos theory are now widely used to protect digital audio and image data. Chaos theory is the idea that tiny changes in initial conditions will escalate into much more significant difference in the future. This paper proposes a robust and effective method for audio encryption based on chaos theory and user-biometric images. In addition, the SHA-256 hash technique and zigzag traversal are employed to bolster the system. First, the algorithm reads the sample values from the input audio and then separates them into byte blocks. In addition, each byte block is blended with chaotic sequences generated by the Henon map first, then by the Lorenz system. The chaotic sequences generated by the logistic map are used to create different initial values for the Henon map and Lorenz Systems. The initial values of the logistic map are constructed using the hash values of the plain audio signals and biometric images produced by the SHA-256 hash algorithm. The proposed method has a variety of desirable characteristics, such as good chaotic behaviour, low computational complexity, a huge key space, and substantial parameter space. The results of the various security and performance assessments show that the proposed algorithm is more robust and efficient than existing approaches against all forms of crypto-graphic threats.











Similar content being viewed by others
Data availability
Not applicable.
References
Adhikari S, Karforma S (2021) A novel audio encryption method using Henon-Tent chaotic pseudo random number sequence. Int J Inf Technol 13(4):1463–1471. https://doi.org/10.1007/s41870-021-00714-x
Al-kateeb ZN, Mohammed SJ (2020) A novel approach for audio file encryption using hand geometry. Multimed Tools Appl 79(27):19615–19628. https://doi.org/10.1007/s11042-020-08869-8
Babu NR, Kalpana M, Balasubramaniam P (2021) A novel audio encryption approach via finite-time synchronization of fractional order hyperchaotic system. Multimed Tools Appl 80(12):18043–18067. https://doi.org/10.1007/s11042-020-10288-8
Batool SI, Waseem HM (2019) A novel image encryption scheme based on Arnold scrambling and Lucas series. Multimed Tools Appl 78(19):27611–27637. https://doi.org/10.1007/s11042-019-07881-x
Dai W, Xu X, Song X, Li G (2022) Audio encryption algorithm based on chen memristor chaotic system. Symmetry (Basel) 14(1):1–19. https://doi.org/10.3390/sym14010017
El Fadili H (2021) Security analysis of an audio data encryption scheme based on key chaining and DNA encoding. Multimed Tools Appl 80(8):12077–12099. https://doi.org/10.1007/s11042-020-10153-8
George SN, Augustine N, Pattathil DP (2015) Audio security through compressive sampling and cellular automata. Multimed Tools Appl 74(23):10393–10417. https://doi.org/10.1007/s11042-014-2172-2
Guleria V, Mishra DC (2020) A new multi-layer RGB image encryption algorithm based on Diffie-Hellman cryptography associated with FrDCT and Arnold transform. Multimed Tools Appl 79(43–44):33119–33160. https://doi.org/10.1007/s11042-020-09615-w
Höfer CN, Karagiannis G (2011) Cloud computing services: taxonomy and comparison. J Internet Serv Appl 2(2):81–94. https://doi.org/10.1007/s13174-011-0027-x
Kakaei H, Jafar K, Ayaz R (2018) A novel fast and secure approach for voice encryption based on DNA computing. 3D Res 9(2):1–11. https://doi.org/10.1007/s13319-018-0167-x
Kaur G, Singh K, Gill HS (2021) Chaos-based joint speech encryption scheme using SHA-1. Multimed Tools Appl 80(7):10927–10947. https://doi.org/10.1007/s11042-020-10223-x
Kumar P, Rana SB (2016) Development of modified AES algorithm for data security. Optik (Stuttg) 127(4):2341–2345. https://doi.org/10.1016/j.ijleo.2015.11.188
Li G, Pu Y, Yang B, Zhao J (2019) Synchronization between different hyper chaotic systems and dimensions of cellular neural network and its design in audio encryption. Cluster Comput 22(3):7423–7434. https://doi.org/10.1007/s10586-018-1700-7
Lima JB, Eronides F, Neto S (2016) Audio encryption based on the cosine number transform. Multimed Tools Appl 75(14):8403–8418. https://doi.org/10.1007/s11042-015-2755-6
Lin CH, Hu GH, Chen JS, Yan JJ, Tang KH (2022) Novel design of cryptosystems for video/audio streaming via dynamic synchronized chaos-based random keys. Multimed Syst 28(5):1793–1808. https://doi.org/10.1007/s00530-022-00950-6
Lin C-M, Pham D-H, Huynh T-T (2022) Encryption and decryption of audio signal and image secure communications using chaotic system synchronization control by TSK fuzzy brain emotional learning controllers. IEEE Trans Cybern 52(12):13684–13698. https://doi.org/10.1109/TCYB.2021.3134245
Liu H, Kadir A, Sun X (2017) Chaos-based fast colour image encryption scheme with true random number keys from environmental noise. IET Image Process 11(5):324–332. https://doi.org/10.1049/iet-ipr.2016.0040
Liu H, Zhang Y, Kadir A, Xu Y (2019) Image encryption using complex hyper chaotic system by injecting impulse into parameters. Appl Math Comput 360:83–93. https://doi.org/10.1016/j.amc.2019.04.078
Lone PN, Singh D, Mir UH (2021) A novel image encryption using random matrix affine cipher and the chaotic maps. J Mod Opt 68(10):507–521. https://doi.org/10.1080/09500340.2021.1924885
Nagaraju S, Parthiban L (2015) Trusted framework for online banking in public cloud using multi-factor authentication and privacy protection gateway. J Cloud Comput 4(1):1–23. https://doi.org/10.1186/s13677-015-0046-4
Naskar PK, Paul S, Nandy D, Chaudhuri A (2019) DNA encoding and channel shuffling for secured encryption of audio data. Multimed Tools Appl 78(17):25019–25042. https://doi.org/10.1007/s11042-019-7696-z
Naskar PK, Bhattacharyya S, Chaudhuri A (2021) An audio encryption based on distinct key blocks along with PWLCM and ECA. Nonlinear Dyn 103(2):2019–2042. https://doi.org/10.1007/s11071-020-06164-7
Nicole A, Telem K, Fotsin HB, Kengne J (2021) Image encryption algorithm based on dynamic DNA coding operations and 3D chaotic systems. Multimed Tools Appl 80(12):19011–19041. https://doi.org/10.1007/s11042-021-10549-0
Nugraha Y, Martin A (2021) Towards a framework for trustworthy data security level agreement in cloud procurement. Comput Secur 106:102266. https://doi.org/10.1016/j.cose.2021.102266
Pareek NK, Patidar V, Sud KK (2006) Image encryption using chaotic logistic map. Image Vis Comput 24(9):926–934. https://doi.org/10.1016/j.imavis.2006.02.021
Riad K, Huang T, Ke L (2019) A dynamic and hierarchical access control for IoT in multi-authority cloud storage. J Netw Comput Appl 160(December):2020. https://doi.org/10.1016/j.jnca.2020.102633
Roy S, Shrivastava M, Vinodkumar C, Kumar S, Umashankar N (2021) IEVCA: an efficient image encryption technique for IoT applications using 2-D Von-Neumann cellular automata. Multimed Tools Appl 80(21):31529–31567. https://doi.org/10.1007/s11042-020-09880-9
Sabir S, Guleria V (2021) Multi-layer color image encryption using random matrix affine cipher, RP2DFrHT and 2D Arnold map. Multimed Tools Appl 80(18):27829–27853. https://doi.org/10.1007/s11042-021-11003-x
Salam MI et al (2015) Implementation of searchable symmetric encryption for privacy-preserving keyword search on cloud storage. Hum-Centric Comput Inf Sci 5(1):19. https://doi.org/10.1186/s13673-015-0039-9
Salau AO, Oluwafemi I, Faleye KF, Jain S (2019) Audio compression using a modified discrete cosine transform with temporal auditory masking. 2019 Int. Conf. Signal Process. Commun. ICSC 2019, pp 135–142.https://doi.org/10.1109/ICSC45622.2019.8938213
Sam IS, Devaraj P, Bhuvaneswaran RS (2012) A novel image cipher based on mixed transformed logistic maps. Multimed Tools Appl 56(2):315–330. https://doi.org/10.1007/s11042-010-0652-6
Sathiyamurthi P, Ramakrishnan S (2022) Speech encryption using hybrid-hyper chaotic system and binary masking technique. Multimed Tools Appl 81(5):6331–6349. https://doi.org/10.1007/s11042-021-11757-4
Shah D, Shah T, Jamal SS (2020) Digital audio signals encryption by Mobius transformation and Hénon map. Multimed Syst 26(2):235–245. https://doi.org/10.1007/s00530-019-00640-w
Shah D, Shah T, Ahamad I, Haider MI, Khalid I (2021) A three-dimensional chaotic map and their applications to digital audio security. Multimed Tools Appl 80(14):22251–22273. https://doi.org/10.1007/s11042-021-10697-3
Sheela SJ, Suresh KV, Tandur D (2018) Image encryption based on modified Henon map using hybrid chaotic shift transform. Multimed Tools Appl 77(19):25223–25251. https://doi.org/10.1007/s11042-018-5782-2
Suman RR, Mondal B, Mandal T (2022) A secure encryption scheme using a Composite Logistic Sine Map (CLSM) and SHA-256. Multimed Tools Appl 81(19):27089–27110. https://doi.org/10.1007/s11042-021-11460-4
Sun Y-j, Zhang H, Wang X-y, Wang X-q, Yan P-f (2020) 2D non-adjacent coupled map lattice with q and its applications in image encryption. Appl Math Comput 373:125039. https://doi.org/10.1016/j.amc.2020.125039
Thoms GRW, Muresan R, Al-dweik A (2019) Chaotic encryption algorithm with key controlled neural networks for intelligent transportation systems. IEEE Access 7:158697–158709. https://doi.org/10.1109/ACCESS.2019.2950007
Wang X, Su Y (2020) An audio encryption algorithm based on DNA coding and chaotic system. IEEE Access 8(8):9260–9270. https://doi.org/10.1109/ACCESS.2019.2963329
Wang X, Wang S, Zhang Y, Guo K (2017) A novel image encryption algorithm based on chaotic shuffling method. Inf Secur J A Glob Perspect 00(00):1–10. https://doi.org/10.1080/19393555.2016.1272725
Wu R et al (2022) AEA-NCS: an audio encryption algorithm based on a nested chaotic system. Chaos Solitons Fractals 165(September):112770. https://doi.org/10.1016/j.chaos.2022.112770
Yaser A, Alsahlani F, Popa A (2021) Journal of network and computer applications LMAAS-IoT : lightweight multi-factor authentication and authorization scheme for real-time data access in IoT cloud-based environment ✩. J Netw Comput Appl 192(November 2020):103177. https://doi.org/10.1016/j.jnca.2021.103177
Zia U et al (2022) Survey on image encryption techniques using chaotic maps in spatial, transform and spatiotemporal domains. Int J Inf Secur 21(4):917–935. https://doi.org/10.1007/s10207-022-00588-5
Acknowledgements
This research work has been written with the support of Rashtriya Uchchatar Siksha Abhiyan (RUSA- Phase 2.0), Policy(TNMulti-Gen), Dept. Of Edn. Govt. Of India
Author information
Authors and Affiliations
Contributions
All authors have made substantial contributions to the following: the conception and design of the study, acquisition of data, analysis, and interpretation of data, drafting of the article or revising it critically for important intellectual content, and final approval of the submitted version.
Corresponding author
Ethics declarations
Ethics approval and consent to participate
This article does not contain any studies with human participants or animals performed by any of the authors.
Consent for publication
The Author warrants that the Work has not been published before in any form that the Work is not being concurrently submitted to and is not under consideration by another publisher, that the persons listed above are listed in the proper order. The Author also warrants that the Work does not libel anyone, infringe anyone’s copyright, or otherwise violate anyone’s statutory or common law rights.
Competing interests
The authors declare that they have no conflict of interest.
Additional information
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Rahul, B., Kuppusamy, K. & Senthilrajan, A. Chaos-based audio encryption algorithm using biometric image and SHA-256 hash algorithm. Multimed Tools Appl 82, 43729–43758 (2023). https://doi.org/10.1007/s11042-023-15289-x
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-15289-x