Abstract
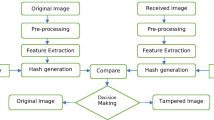
Perceptual image hashing has mainly been used in the literature to authenticate images or to identify similar contents for image copy detection. In this work, we investigate the introduction of perceptual image hashing to protect biometric systems against digital replay attacks, and we propose a novel Replay Attack Detection (RAD) scheme that guarantees the authenticity of the received biometric image on the one hand, and identifies if it has been resubmitted on the other hand. The proposed scheme has the advantages of operating in an uncontrolled environment and does not need the cooperation of end users. It relies on the Challenge/Response principle and combines perceptual image hashing and data hiding techniques. Additionally, a new perceptual image hashing system that performs both content authentication and identification is proposed for fingerprint images. It is based on a shift-invariant calibration signal technique that uses the Discrete Cosine Transform (DCT) and Discrete Sine Transform (DST) of the Differential Block Luminance Mean (DBLM) features to compute the hash sequence. The performance of the proposed system has been evaluated through intensive experiments with real fingerprint images, and the obtained results have shown that the proposed system can provide high performance in terms of authentication and identification. Furthermore, the proposed system outperformed related state-of-the-art image hashing techniques.















Similar content being viewed by others
Availability of data and material
The datasets generated during and/or analyzed during the current study are available from the corresponding author on reasonable request.
References
Abbas SQ, Ahmed F, Chen Y-PP (2021) Perceptual image hashing using transform domain noise resistant local binary pattern. Multimed Tools Appl 80:9849–9875. https://doi.org/10.1007/s11042-020-10135-w
Abbas SQ, Ahmed F, živić N, Ur-Rehman O (2016) Perceptual image hashing using SVD based noise resistant local binary pattern. In: 2016 8th International Congress on Ultra Modern Telecommunications and Control Systems and Workshops (ICUMT). IEEE, pp 401–407
Abdullahi SM, Wang H, Malik A (2018) Fingerprint Image Hashing Based on Minutiae Points and Shape Context. Int J Digit Crime Forensics 10 (4):1–20. https://doi.org/10.4018/ijdcf.2018100101
Adler A (2003) Sample images can be independently restored from face recognition templates. In: Canadian Conference on Electrical and Computer Engineering. Toward a Caring and Humane Technology (CCECE 2003), pp 1163–1166. https://doi.org/10.1109/CCECE.2003.1226104
Ahmaderaghi B, Kurugollu F, Rincon JMD, Bouridane A (2018) Blind image watermark detection algorithm based on discrete shearlet transform using statistical decision theory. IEEE Trans Comput Imaging 4(1):46–59. https://doi.org/10.1109/TCI.2018.2794065
Anjos A, Komulainen J, Marcel S, Hadid A, Pietikainen M (2014) Face anti-spoofing: Visual approach. In: Marcel S, Nixon M, Li S (eds) Handbook of biometric anti-spoofing. Advances in computer vision and pattern recognition. Springer, pp 65–82. https://doi.org/10.1007/978-1-4471-6524-8_4
Avila AR, Alam J, O’Shaughnessy D, Falk TH (2019) Blind channel response estimation for replay attack detection. In: Proc. Interspeech 2019, pp 2893–2897. https://doi.org/10.21437/Interspeech.2019-2956
Benseddik ML, Zebbiche K, Azzaz MS, Sadoudi S (2022) Interpolation-based reversible data hiding in the transform domain for fingerprint images. Multimed Tools Appl 81:20329–20356. https://doi.org/10.1007/s11042-022-12288-2
Bharath KP, Kumar MR (2022) New replay attack detection using iterative adaptive inverse filtering and high frequency band. Expert Syst Appl 195:116597. https://doi.org/10.1016/j.eswa.2022.116597
Birouk W, Lahoulou A, Melit A, Bouridane A (2023) Robust perceptual fingerprint image hashing: A comparative study. Int J Biometrics 15(1):59. https://doi.org/10.1504/IJBM.2023.127724
Bolle RM, Connell JH, Ratha NK (2002) Biometric perils and patches. Pattern Recognit 35(12):2727–2738. https://doi.org/10.1016/S0031-3203(01)00247-3
Boutellaa E, Boulkenafet Z, Komulainen J, Hadid A (2015) Audiovisual synchrony assessment for replay attack detection in talking face biometrics. Multimed Tools Appl 75(9):5329–5343. https://doi.org/10.1007/s11042-015-2848-2
Czajka A, Refaey A, Pacut A (2008) Replay attack prevention for iris biometrics. In: 42nd Annual IEEE International Carnahan Conference on Security Technology, pp 247–253. https://doi.org/10.1109/CCST.2008.4751309
Davarzani R, Mozaffari S, Yaghmaie K (2016) Perceptual image hashing using center-symmetric local binary patterns. Multimed Tools Appl 75:4639–4667. https://doi.org/10.1007/s11042-015-2496-6
De Marsico M, Nappi M, Riccio D, Dugelay J-L (2012) Moving face spoofing detection via 3D projective invariants. In: 5th IAPR International Conference on Biometrics (ICB), pp 73–78. https://doi.org/10.1109/ICB.2012.6199761
Dua M, Sadhu A, Jindal A, Mehta R (2022) A hybrid noise robust model for multireplay attack detection in Automatic speaker verification systems. Biomed Signal Process Control 74:103517. https://doi.org/10.1016/j.bspc.2022.103517
Frischholz RW, Werner A (2003) Avoiding replay-attacks in a face recognition system using head-pose estimation. In: IEEE International SOI Conference. proceedings (Cat. No.03CH37443), pp 234–235. https://doi.org/10.1109/AMFG.2003.1240849
Ghouti E (2018) A new perceptual video fingerprinting system. Multimed Tools Appl 77:6713–6751. https://doi.org/10.1007/s11042-017-4595-z
Gui Q, Yang W, Jin Z, Ruiz-Blondet MV, Laszlo S (2016) A residual feature-based replay attack detection approach for brainprint biometric systems. In: 2016 IEEE International Workshop on Information Forensics and Security (WIFS), pp 1–6. https://doi.org/10.1109/WIFS.2016.7823907
Gupta R, Sehgal P (2020) Optimized Singular Value Decomposition(SVD) Based watermarking of iris biometric data to mitigate replay attack. In: ICT for Competitive Strategies, 1st edn. CRC Press, p 12. https://doi.org/10.1201/9781003052098-18
Hosseinzadeh M, Sinopoli B, Garone E (2019) Feasibility and detection of replay attack in networked constrained cyber-physical systems. In: 57th Annual Allerton Conference on Communication, Control, and Computing (Allerton). https://doi.org/10.1109/allerton.2019.8919762
Joshi VB, Raval MS, Gupta D, Rege PP, Parulkar SK (2016) A multiple reversible watermarking technique for fingerprint authentication. Multimed Syst 22:367–378. https://doi.org/10.1007/s00530-015-0465-6
Karmakar D, Sarkar R, Datta M (2021) Spoofed replay attack detection by Multidimensional Fourier transform on facial micro-expression regions. Signal Process: Image Commun 93:116164. https://doi.org/10.1016/j.image.2021.116164
Khelifi F, Bouridane A, Wang A (2019) Perceptual Video Hashing for Content Identification and Authentication. IEEE Trans Circuits Syst Video Technol 29(1):50–67. https://doi.org/10.1109/TCSVT.2017.2776159
Lebcir M, Awang S, Benziane A (2020) Reversible watermarking technique for fingerprint authentication based on DCT. IOP Conf Ser: Mater Sci Eng 769:012070. https://doi.org/10.1088/1757-899x/769/1/012070
Lin C-Y, Chang SF (1997) Robust image authentication method surviving JPEG lossy compression. In: SPIE Storage and retrieval of image/video database. https://doi.org/10.1117/12.298462
Loukhaoukha K, Refaey A, Zebbiche K, Shami A (2018) Efficient and secure cryptosystem for fingerprint images in wavelet domain, vol 77, pp 9325–9339. https://doi.org/10.1007/s11042-017-4938-9
Maio D, Maltoni D, Cappelli R, Wayman JL, Jain AK (2002) FVC2000: fingerprint verification competition. In: IEEE Transactions on pattern analysis and machine intelligence, 24.3, pp 402–412. https://ieeexplore.ieee.org/document/990140
Maltoni D, Maio D, Jain AK, Prabhakar S (2009) Securing fingerprint systems. In: Handbook of fingerprint recognition, Springer, London, pp 371–416. https://doi.org/10.1007/978-1-84882-254-2
Mitre (2021) Common Weakness Enumeration. Retrieved May 03, 2021, from. https://cwe.mitre.org/data/definitions/294.html
Monga V, Evans BL (2006) Perceptual Image Hashing Via Feature Points: Performance Evaluation and Tradeoffs. IEEE Trans Image Process 15 (11):3452–3465. https://doi.org/10.1109/tip.2006.881948
Muthu R, Bouridane A, Khelifi F (2014) Minutiae based fingerprint image hashing. In: International Conference on Control, Decision and Information Technologies (CoDIT). https://doi.org/10.1109/codit.2014.6996981
Muthu R, Rani C (2017) Perceptual hashing for efficient fingerprint based identification. In: 4th International Conference on Advanced Computing and Communication Systems (ICACCS). https://doi.org/10.1109/icaccs.2017.8014713
NIST/SEMATECH (2012) e-Handbook of Statistical Methods. https://doi.org/10.18434/M32189
Ojala T, Pietikainen M, Maenpaa T (2002) Multiresolution gray-scale and rotation invariant texture classification with local binary patterns. Pattern Anal Mach Intell IEEE Trans 24(7):971–987
Oostveen J, Kalker T, Haitsma J (2002) Feature extraction and a database strategy for video fingerprinting. In: Proc. of the 5th International Conference on Recent Advances in Visual Information Systems, Taiwan, March 2002. https://doi.org/10.1007/3-540-45925-1_11
Patil HA, Kamble MR (2018) A survey on replay attack detection for Automatic Speaker Verification (ASV) system. In: Asia-Pacific Signal and Information Processing Association Annual Summit and Conference (APSIPA ASC). https://doi.org/10.23919/apsipa.2018.8659666
Ratha NK, Connell JH, Bolle RM (2001) Enhancing security and privacy in biometrics-based authentication systems. IBM Syst J 40(3):614–634. https://doi.org/10.1147/sj.403.0614
Ratha NK, Connell JH, Bolle RM (2001) An analysis of minutiae matching strength. In: 3rd International Conference on Audio- and Video-Based Biometric Person Authentication (AVBPA), Lecture Notes in Computer Science, Springer, vol 2091, pp 223–228. https://doi.org/10.1007/3-540-45344-X_32
Ren Y, Fang Z, Liu D, Chen C (2019) Replay attack detection based on distortion by loudspeaker for voice authentication. Multimed Tools Appl 78:8383–8396. https://doi.org/10.1007/s11042-018-6834-3
Ren J, Jiang X, Yuan J (2016) Face and facial expressions recognition and analysis. In: Magnenat-Thalmann N, Yuan J, Thalmann D, You BJ (eds) Context aware human-robot and human-agent interaction. Human–computer interaction series. Springer, Cham. https://doi.org/10.1007/978-3-319-19947-4_1
Rui Z, Yan Z (2019) A survey on biometric authentication: Toward secure and privacy-preserving identification. IEEE Access 7:5994–6009. https://doi.org/10.1109/ACCESS.2018.2889996
Rusia MK, Singh DK (2022) A comprehensive survey on techniques to handle face identity threats: challenges and opportunities, vol 82. https://doi.org/10.1007/s11042-022-13248-6
Saranya MS, Murthy HA (2018) Decision-level feature switching as a paradigm for replay attack detection. In: Proc. Interspeech 2018, pp 686–690. https://doi.org/10.21437/Interspeech.2018-1494
Schneider M, Chang SF (1996) A robust content based digital signature for image authentication. In: The 3rd IEEE International conference on image processing. https://doi.org/10.1109/ICIP.1996.560425
Sluganovic I, Roeschlin M, Rasmussen KB, Martinovic I (2019) Analysis of Reflexive Eye Movements for Fast Replay-Resistant Biometric Authentication. ACM Trans Privacy Secur 22(1):1–30. https://doi.org/10.1145/3281745
Smith DF (2016) Countering digital replay attacks for face verification on consumer smart devices using structured illumination. PhD thesis. School of Information Technology and Electrical Engineering, The University of Queensland. https://doi.org/10.14264/uql.2016.227
Tan CB, Hijazi MHA, Khamis N, Puteri NEBN, Zuraini Z, Frans C, Abdullah G (2021) A survey on presentation attack detection for automatic speaker verification systems: State-of-the-art, taxonomy, issues and future direction. Multimed Tools Appl 80:32725–32762. https://doi.org/10.1007/s11042-021-11235-x
Wang Y, Liu Y, Gao P, Wang Y (2021) ICDSP 2021: 5th International Conference on Digital Signal Processing, pp 266–271. https://doi.org/10.1145/3458380.3458426
Yip P, Rao KR (1987) On the shift property of DCTs and DSTs. IEEE Trans Acoustics, Speech, and Signal Process 35(3):404–406. https://doi.org/10.1109/TASSP.1987.1165127
Yuan X, Zhao Y (2021) Perceptual image hashing based on three-dimensional global features and image energy. IEEE Access 9:49325–49337. https://doi.org/10.1109/ACCESS.2021.3069045
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of Interests
The authors declare that they have no conflict of interest.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Hamadouche, M., Khalil, Z., TEBBI, H. et al. A replay attack detection scheme based on perceptual image hashing. Multimed Tools Appl 83, 8999–9031 (2024). https://doi.org/10.1007/s11042-023-15300-5
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-15300-5