Abstract
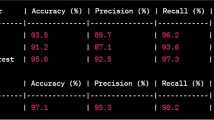
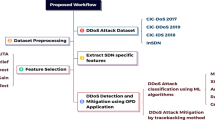
DDOS attack is malicious attack that causes disturbance in service corresponding to target server. Malicious user in this case try to flood the server with large volume of packets. Resources thus will not be available to consumers and network is said to be jammed. The research towards distributed denial of service is carried out. Research indicates that network layer is most prone to this type of attack. The proposed work prevents the DDOS attack by reducing the surface area of the attack. This is accomplished by reducing the exposure of resources to ports and applications. The entire work of prevention is categorized into pre-processing that is accomplished through normalization. This operation is used to bring the features from the dataset into specific range. Feature extraction and selection is with optimal procedure of KMLP. K value indicates the exposure value that will act as threshold for exposing server to different ports and applications. Multi-layer perceptron will be used to select optimal features from extracted features. Classification is the last phase that is accomplished with voting classifier including adaptive boost, random forest and KNN. The result of the classification indicates reduced packet drop and increased lifetime of the network. Packet drop ratio is improved by 10% and lifetime by 7%.




Similar content being viewed by others
Data availability
All the data is collected from the simulation reports of the software and tools used by the authors. Authors are working on implementing the same using real world data with appropriate permissions.
References
Aamir M, Ali Zaidi SM (2021) Clustering based semi-supervised machine learning for DDoS attack classification. J. King Saud Univ. – Comput. Inf. Sci 33(4):436–446. https://doi.org/10.1016/J.JKSUCI.2019.02.003
Behal S, Kumar K (2016) Trends in Validation of DDoS Research. Procedia Comput. Sci 85:7–15. https://doi.org/10.1016/J.PROCS.2016.05.170
Behal S, Kumar K, Sachdeva M D-FACE: An anomaly based distributed approach for early detection of DDoS attacks and flash events. J. Netw. Comput. App 111:49–63. https://doi.org/10.1016/J.JNCA.2018.03.024
Bhuyan MH, Bhattacharyya DK, Kalita JK (2014) Network anomaly detection: Methods, systems and tools. IEEE Commun. Surv. Tutorials 16(1):303–336. https://doi.org/10.1109/SURV.2013.052213.00046
Cao Y, Gao Y, Tan R, Han Q, Liu Z (2018) Understanding internet DDoS Mitigation from academic and industrial perspectives. IEEE Access 6:66641–66648. https://doi.org/10.1109/ACCESS.2018.2877710
Chang RKC (2002) Defending against flooding-based distributed denial-of-service attacks: A tutorial. IEEE Commun. Mag 40(10):42–51. https://doi.org/10.1109/MCOM.2002.1039856
Cheng J, Li M, Tang X, Sheng VS, Liu Y, Guo W (2018) Flow Correlation Degree Optimization Driven Random Forest for Detecting DDoS Attacks in Cloud Computing. Secur. Commun. Networks 2018. https://doi.org/10.1155/2018/6459326
Ganapathy S, Kulothungan K, Muthurajkumar S, Vijayalakshmi M, Yogesh L, Kannan A (2013) Intelligent feature selection and classification techniques for intrusion detection in networks: A survey. Eurasip J. Wirel. Commun. Netw 2013(1). https://doi.org/10.1186/1687-1499-2013-271
Gu Y, Li K, Guo Z, Wang Y (2019) Semi-supervised k-means ddos detection method using hybrid feature selection algorithm. IEEE Access 7:64351–64365. https://doi.org/10.1109/ACCESS.2019.2917532
Jazi HH, Gonzalez H, Stakhanova N, Ghorbani AA (2017) Detecting HTTP-based application layer DoS attacks on web servers in the presence of sampling. Comput. Networks 121:25–36. https://doi.org/10.1016/J.COMNET.2017.03.018
Liu Z, Cao Y, Zhu M, Ge W (2018) Umbrella: Enabling ISPs to offer readily deployable and privacy-preserving DDoS prevention services. IEEE Trans. Inf. Forensics Secur 14(4):1098–1108. https://doi.org/10.1109/TIFS.2018.2870828
Meng W, Li W, Su C, Zhou J, Lu R (2017) Enhancing Trust Management for Wireless Intrusion Detection via Traffic Sampling in the Era of Big Data. IEEE Access 6:7234–7243. https://doi.org/10.1109/ACCESS.2017.2772294
Newman S (2019) Under the radar: the danger of stealthy DDoS attacks. Netw. Secur. 2019(2):18–19. https://doi.org/10.1016/S1353-4858(19)30025-X
Phan TV, Park M (2019) Efficient distributed denial-of-service attack defense in sdn-based cloud. IEEE Access 7:18701–18714. https://doi.org/10.1109/ACCESS.2019.2896783
Praseed A, Santhi Thilagam P (2019) DDoS attacks at the application layer: Challenges and research perspectives for safeguarding web applications. IEEE Commun. Surv. Tutorials 21(1):661–685. https://doi.org/10.1109/COMST.2018.2870658
Roman R, Zhou J, Lopez J (2013) On the features and challenges of security and privacy in distributed internet of things. Comput. Netwo 57(10):2266–2279. https://doi.org/10.1016/J.COMNET.2012.12.018
Shiravi A, Shiravi H, Tavallaee M, Ghorbani AA (2012) Toward developing a systematic approach to generate benchmark datasets for intrusion detection. Comput. Secur 31(3):357–374. https://doi.org/10.1016/J.COSE.2011.12.012
Simpson S, Shirazi SN, Marnerides A, Jouet S, Pezaros D, Hutchison D (2018) An Inter-Domain Collaboration Scheme to Remedy DDoS Attacks in Computer Networks. IEEE Trans. Netw. Serv. Manag 15(3):879–893. https://doi.org/10.1109/TNSM.2018.2828938
Singh K, Singh P, Kumar K (2017) Application layer HTTP-GET flood DDoS attacks: Research landscape and challenges. Comput. Secur 65:344–372. https://doi.org/10.1016/J.COSE.2016.10.005
Zargar ST, Joshi J, Tipper D (2013) A survey of defense mechanisms against distributed denial of service (DDOS) flooding attacks. IEEE Commun. Surv. Tutorials 15(4):2046–2069. https://doi.org/10.1109/SURV.2013.031413.00127
Funding
No fund received for this project
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Conflict of interest
The authors declare that we have no conflict of interest.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Dogra, A., Taqdir DDOS attack prevention and validation with metric based ensemble approach. Multimed Tools Appl 82, 44147–44154 (2023). https://doi.org/10.1007/s11042-023-15523-6
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-15523-6