Abstract
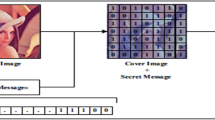
This review paper explores the use of optimization techniques in steganography, the art of hiding secret information within other data. Steganography is a field that has gained significant attention in recent years due to the increasing need for secure communication and data protection. Optimization techniques have been shown to be effective in improving the performance of steganography systems, particularly in terms of maximizing the amount of secret data that can be hidden while minimizing the impact on the cover data. This paper provides a comprehensive overview of the state-of-the-art optimization techniques in steganography, including genetic algorithms, particle swarm optimization, ant colony optimization and fruit fly optimization algorithm. This paper also discusses the advantages and limitations of these techniques and their potential for further development in the future. Also the state-of-the-art methods were compared in terms of PSNR (Peak Signal to Noise Ratio), payload capacity, SSIM (Structured Similarity Index) etc. The review concludes by highlighting the importance of optimization techniques in steganography and their potential impact on the development of more efficient and secure steganography systems.



Similar content being viewed by others
Data availability
Data sharing is not applicable to this article.
References
Al-Shatanawi OM, Nameer N Emam E (2015) “A new image steganography algorithm based on MLSB method with random pixels selection” , Int J Netw Secur Appl (IJNSA) Vol.7, No.2
Ambika, Biradar RL (2019) Secure medical image steganography through optimal pixel selection by EH-MB pipelined optimization technique. Heal Technol 10:2019. https://doi.org/10.1007/s12553-018-00289-x
Aref M, Faez K (2017) Adaptive image steganography based on transform domain via genetic algorithm. Opt Int J Light Electron Opt 145:158–168
Arivazhagan S, Jebarani WSL, Roy SA, Amrutha E (2019) “Improving quality of Stego images through dithering techniques for pixel pair matching Steganographic schemes”, Int J Eng Adv Technology (IJEAT), Volume-8 Issue-6
Banharnsakun A (2018) Artificial bee colony approach for enhancing LSB based image steganography. Multimed Tools Appl 77:27491–27504
Bedi P, Bansal R, Sehgal P (2013) Using PSO in a spatial domain based image hiding scheme with distortion tolerance. Comput Electr Eng 39(2):640–654
Bhandari M, Panday S, Bhatta CP, Panday SP (2022) Image steganography approach based ant colony optimization with triangular chaotic map, 2nd International Conference on Innovative Practices in Technology and Management (ICIPTM) 2:429–34
Carvalho D, Lima R, Silva WGD, Morais AHO (2017) Optimizing image steganography using particle swarm optimization algorithm. Int J Comput Appl 164(7):1–5
Hemanth DJ, Umamaheswari S, Popescu DE, Naaji A (2016) Application of genetic algorithm and particle swarm optimization techniques for improved image steganography systems. Open Phys 14(1):452–62
Jaradat Aya , Eyad Taqieddin , Moad Mowafi (2021), “A high-capacity image steganography method using chaotic particle swarm optimization, Secur Commun Netw, https://doi.org/10.1155/2021/6679284, Volume 2021, June 2021.
Kamdar NP, Kamdar DG, Khandhar DN (2013) Performance evaluation of LSB based steganography for optimization of PSNR and MSE. J Inf, Knowl Res Electron Commun Eng 2:505–508
Kaur A, Kaur R, Kumar N (2015) “Image steganography using discrete wavelet transformation and artificial bee colony optimization” ,1st International conference on next generation computing technologies (NGCT), Dehradun: IEEE, pp. 990–94
Kaur G, Singh N, Kumar M (2023) Image forgery techniques: a review. Artif Intell Rev 56:1577–1625. https://doi.org/10.1007/s10462-022-10211-7
Li X, Wang J (2007) A steganographic method based upon JPEG and particles swarm optimization algorithm. Inf Sci 177:3099–3109
Mohsin AH, Zaidan AA, Zaidan BB, Albahri OS, Albahri AS, Alsalem MA, Mohammed KI, Nidhal S, Jalood NS, Jasim AN, Shareef AH (2019) New method of image steganography based on particle swarm optimization algorithm in spatial domain for high embedding capacity. IEEE Access 7:2019. https://doi.org/10.1109/ACCESS.2019.2949622
Muhuri PK, Ashraf Z, Goel S (2020) A novel image Steganographic method based on integer wavelet transformation and particle swarm optimization. Appl Soft Comput J 92:2020. https://doi.org/10.1016/j.asoc.2020.106257
Rabevohitra FH, Sang J (2011) Using PSO algorithm for simple LBS substitution based steganography scheme in DCT transformation domain. International Conference in Swarm Intelligence (ICSI 2011) 6728:212–220
Rani V, Kumar M, Mittal A, Kumar K (2022) Artificial intelligence for cybersecurity: recent advancements, challenges and opportunities. In: Nedjah N, Abd El-Latif AA, Gupta BB, Mourelle LM (eds) Robotics and AI for cybersecurity and critical infrastructure in smart cities. Studies in computational intelligence, vol 1030. Springer, Cham. https://doi.org/10.1007/978-3-030-96737-6_4
Roselin Kiruba R, Sree Sharmila T (2020) Secure data hiding by fruit fly optimization improved hybridized seeker algorithm. Multidimensional Systems and Signal Processing 32:1. https://doi.org/10.1007/s11045-019-00697-w
Sabeti V, Sobhani M, Hasheminejad SMH (2022) An adaptive image steganography method based on integer wavelet transform using genetic algorithm. Comput Electr Eng 99:107809
Sajedi H, Jamzad M (2009) Secure steganography based on embedding capacity. Int J Inf Secur 8:433–45
Sajedi H, Jamzad M (2010) Using contourlet transform and cover selection for secure steganography. Int J Inf Secur 9:337–352
Selvaraj A, Ezhilarasan A, Lilly S, Ananthi JW, Sam R (2021) Digital image steganalysis: a survey on paradigm shift from machine learning to deep learning based techniques. IET Image Process 15:504–522
Soleimanpour M, Talebi S, Azadi-Motlagh H (2013) “A novel technique for steganography method based on improved genetic algorithm optimization in spatial domain” , Iran J Electric Electron Eng ,Vol. 9, No. 2
Wang RZ, Lin CF, Lin JC (2001) Image hiding by optimal LSB substitution and genetic algorithm. Pattern Recogn 34:671–683
Wazirali R, Alasmary W,Mahmoud MMEA, Alhindi A (2019) “An Optimized Steganography Hiding Capacity and Imperceptibly Using Genetic Algorithms”,IEEE Access, volume 7
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors have no conflicts of interest to declare.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
V, G., G, I. A review on image steganographic techniques based on optimization algorithms for secret communication. Multimed Tools Appl 82, 44245–44258 (2023). https://doi.org/10.1007/s11042-023-15568-7
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-15568-7