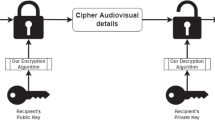
Abstract
Security and confidentiality are one of the main concerns when transmitting multimedia data over the Internet. To deal with the arising security issues, many advanced cryptographic algorithms have been proposed in the literature. The efficiency of these encryption algorithms varies according to the application area in which they are deployed. Although there are many objective evaluation metrics available in the literature to measure the performance of the cryptographic algorithms, however, to the best of our knowledge, no survey or review addresses the quality of the metrics for cryptography algorithms. In this paper, we have presented and analyzed the cryptography algorithms and performance evaluation metrics such as resource utilization measure, quality measure, and security measures to evaluate the security performance of different encryption algorithms for multimedia data. Extensive experiments have been carried out to evaluate the performance of the cryptography algorithms for multimedia data such as images and videos. We have also discussed and analyzed in detail the performance of evaluation measures used to validate the cryptography algorithms. Our findings highlight the strength of different cryptography algorithms and performance evaluation metrics. The analysis is expected to contribute to the design of a new and efficient model for multimedia applications. A detailed analysis of major attacks was also presented for each encryption scheme in tabular form.


















Similar content being viewed by others
References
Abbas NA (2016) Image encryption based on independent component analysis and arnold’s cat map. Egyptian informatics journal 17(1):139–146
Adams (1997) Rfc2144: The cast-128 encryption algorithm
Adams C (1999) The cast-256 encryption algorithm
Adams C, Heys HM, Tavares SE, Wiener M (1999) An analysis of the cast-256 cipher. In Engineering Solutions for the Next Millennium. 1999 IEEE Canadian Conference on Electrical and Computer Engineering (Cat. No. 99TH8411), volume 1, pages 361–366. IEEE
Ahmad J, Ahmed F (2010) Efficiency analysis and security evaluation of image encryption schemes. Computing 23:25
Ahmad S, Hayat MF, Qureshi MA, Asef S, Saleem Y (2021) Enhanced halftone-based secure and improved visual cryptography scheme for colour/binary images. Multimedia Tools and Applications 80(21):32071–32090
Ahmed HEldH, Kalash HM, Allah OSF (2007) Encryption efficiency analysis and security evaluation of rc6 block cipher for digital images. In 2007 International Conference on Electrical Engineering, pages 1–7. IEEE
Ahmed N, Asif HMS, Saleem G (2016) A benchmark for performance evaluation and security assessment of image encryption schemes. International Journal of Computer Network & Information Security, 8(12)
Bagherzandi A, Salmasizadeh M, Mohajeri J (2009) A related key attack on the feistel type block ciphers. IJ Network Security 8(3):221–226
Bala T, Kumar Y (2015) Asymmetric algorithms and symmetric algorithms: A review. International Journal of Computer Applications (ICAET), pages 1–4
Bhanot R, Hans R (2015) A review and comparative analysis of various encryption algorithms. International Journal of Security and Its Applications 9(4):289–306
Biham E, Dunkelman O, Keller N (2008) A unified approach to related-key attacks. In International Workshop on Fast Software Encryption, pages 73–96. Springer
Bin CW, Xin Z (2009) Image encryption algorithm based on henon chaotic system. In 2009 International Conference on Image Analysis and Signal Processing, pages 94–97. IEEE
Bleichenbacher D (1998) Chosen ciphertext attacks against protocols based on the rsa encryption standard pkcs# 1. In Annual International Cryptology Conference, pages 1–12. Springer
Burnwick C, Coppersmith D (1999) The mars encryption algorithm. IBM, http://csrc.nist.gov/encryption/aes/round2/AESAIgs/MARS
Charbathia S, Sharma S (2014) A comparative study of rivest cipher algorithms. International Journal of Information and Computation Technology 4(17):1831–1838
Data Encryption Standard et al (1977) Federal information processing standards publication 46. National Bureau of Standards, US Department of Commerce, 23
Davida GI (1982) Chosen signature cryptanalysis of the RSA (MIT) public keycryptosystem. Department of Electrical and Computer Science, College of Engineering and’..
Dehkordi MH, Taghizadeh R (2018) Biclique cryptanalysis of full round present with reduced data complexity. Electric Electron Tech Open Acc J 2(2):251–255
Dener M (2014) Security analysis in wireless sensor networks. International Journal of Distributed Sensor Networks 10(10):303501
Elkamchouchi HM, Makar MA (2005) Measuring encryption quality for bitmap images encrypted with rijndael and kamkar block ciphers. In: Proceedings of the Twenty-Second National Radio Science Conference, 2005. NRSC 2005., pages 277–284. IEEE
Fan J, Verbauwhede I (2012) An updated survey on secure ecc implementations: Attacks, countermeasures and cost. In Cryptography and Security: From Theory to Applications, pages 265–282. Springer
Fishawy NFE, Zaid OMA (2007) Quality of encryption measurement of bitmap images with rc6, mrc6, and rijndael block cipher algorithms. IJ Network Security 5(3):241–251
Fouque PA, Valette F (2003) The doubling attack–why upwards is better than downwards. In: International Workshop on Cryptographic Hardware and Embedded Systems, pages 269–280. Springer
Girault M, Cohen R, Campana M (1988) A generalized birthday attack. In: Workshop on the Theory and Application of of Cryptographic Techniques, pages 129–156. Springer
Gray RM (2011) Entropy and information theory. Springer Science & Business Media
Gunasundari T, Elangovan K (2014) A comparative survey on symmetric key encryption algorithms. International Journal of Computer Science and Mobile Applications 2(2):78–83
Hong D, Sung J, Hong S, Lim J, Lee S, Koo BS, Lee C, Chang D, Lee J, Jeong K, et al (2006) Hight: A new block cipher suitable for low-resource device. In International Workshop on Cryptographic Hardware and Embedded Systems, pages 46–59. Springer
Hunn SAY, Idris Nb, et al (2012) The development of tiny encryption algorithm (tea) crypto-core for mobile systems. In 2012 IEEE International Conference on Electronics Design, Systems and Applications (ICEDSA), pages 45–49. IEEE
Jang S (2017) Comparative analysis of aes blowfish twofish and threefish encryption algorithms. Anal. Appl. Math. 10:5
Kader HM, Hadhoud MM (2009) Performance evaluation of symmetric encryption algorithms. Performance Evaluation, pages 58–64
Kaur M, Kumar V (2020) A comprehensive review on image encryption techniques. Archives of Computational Methods in Engineering 27(1):15–43
Kitsos P, Galanis MD, Koufopavlou O (2004) High-speed hardware implementations of the kasumi block cipher. In: 2004 IEEE International Symposium on Circuits and Systems (IEEE Cat. No. 04CH37512), volume 2, pages II–549. IEEE
Knudsen LR (1993) Practically secure feistel ciphers. In: International Workshop on Fast Software Encryption, pages 211–221. Springer
Kumari, Manju, Gupta, Shailender, Sardana, Pranshul (2017) A survey of image encryption algorithms. 3D Research 8(4):37
Li J, Liu H (2013) Colour image encryption based on advanced encryption standard algorithm with two-dimensional chaotic map. IET information security 7(4):265–270
Lian S (2008) Multimedia content encryption: techniques and applications. CRC Press
Liehuang Z, Wenzhuo Lejian L, Hong L (2006) A novel image scrambling algorithm for digital watermarking based on chaotic sequences. International Journal of Computer Science and Network Security 6(8B):125–130
Liu Y, Gu D, Liu Z, Li W (2012) Impossible differential attacks on reduced-round lblock. In International Conference on Information Security Practice and Experience, pages 97–108. Springer
Luo Y, Ouyang X, Liu J, Cao L (2019) An image encryption method based on elliptic curve elgamal encryption and chaotic systems. IEEE Access 7:38507–38522
Luo Y, Lin J, Liu J, Wei D, Cao L, Zhou R, Cao Y, Ding X (2019) A robust image encryption algorithm based on chua’s circuit and compressive sensing. Signal Processing 161:227–247
Mahajan P, Sachdeva A (2013) A study of encryption algorithms aes, des and rsa for security. Global Journal of Computer Science and Technology
Mandal AK, Tiwari A (2012) Analysis of avalanche effect in plaintext of des using binary codes. International Journal of Emerging Trends and Technology in Computer Science (IJETTCS) 1(3):166–177
Massoudi A, Lefebvre F, De Vleeschouwer C, Macq B (2008) Quisquater JJ (2008) Overview on selective encryption of image and video: challenges and perspectives. Eurasip Journal on information security 1:179290
Milad AA, Muda Z, Noh ZABM, Algaet MA (2012) Comparative study of performance in cryptography algorithms (blowfish and skipjack). Journal of Computer Science 8(7):91
Mohammad Farook O, Rahim Mohd MS, Zeebaree Mohammed SR, Ahmed FY (2017) A survey and analysis of the image encryption methods. International Journal of Applied Engineering Research 12(23):13265–13280
Mohan HS, Reddy AR (2011) Performance analysis of aes and mars encryption algorithms. International Journal of Computer Science Issues (IJCSI) 8(4):363
Moriai S, Yin YS (2000) Cryptanalysis of twofish (ii)
Mushtaque MdA, Dhiman H, Hussain S, Maheshwari S (2014) Evaluation of des, tdes, aes, blowfish and two fish encryption algorithm: based on space complexity. International Journal of Engineering Research & Technology (IJERT), 3(4)
Naeemabadi M, Ordoubadi BS, Dehnavi AM, Bahaadinbeigy K (2015) Comparison of serpent, twofish and rijndael encryption algorithms in tele-ophthalmology system. Advances in Natural and Applied Sciences 9(4):137–150
Nie T, Zhang T (2009) A study of des and blowfish encryption algorithm. In: Tencon 2009-2009 IEEE Region 10 Conference, pages 1–4. IEEE
Padmavathi B, Kumari SR (2013) survey on performance analysis of des, aes and rsa algorithm along with lsb substitution. IJSR, India
Pandey A, Som S (2016) Applications and usage of visual cryptography: A review. In 2016 5th International Conference on Reliability, Infocom Technologies and Optimization (Trends and Future Directions) (ICRITO), pages 375–381, Sep
Patil P, Narayankar P, Narayan DG, Meena SMd (2016) A comprehensive evaluation of cryptographic algorithms: Des, 3des, aes, rsa and blowfish. Procedia Computer Science 78:617–624
Preishuber Mario, Hütter Thomas, Katzenbeisser Stefan, Uhl Andreas (2018) Depreciating motivation and empirical security analysis of chaos-based image and video encryption. IEEE Transactions on Information Forensics and Security 13(9):2137–2150
Rajesh S, Paul V, Menon VG, Khosravi MR (2019) A secure and efficient lightweight symmetric encryption scheme for transfer of text files between embedded iot devices. Symmetry 11(2):293
Rasoolzadeh S, Ahmadian Z, Salmasizadeh M, Aref MR (2016) An improved truncated differential cryptanalysis of klein. Tatra Mountains Mathematical Publications 67(1):135–147
Rawat N, Kim B, Kumar R (2016) Fast digital image encryption based on compressive sensing using structurally random matrices and arnold transform technique. Optik 127(4):2282–2286
Raza Fatima S, Satpute Vishal (2019) A novel bit permutation-based image encryption algorithm. Nonlinear Dynamics 95(2):859–873
Rijmen V, Daemen J (2001) Advanced encryption standard. Proceedings of Federal Information Processing Standards Publications, National Institute of Standards and Technologys, pages 19–22
Rinne S, Eisenbarth T, Paar C (2007) Performance analysis of contemporary light-weight block ciphers on 8-bit microcontrollers. In Ecrypt Workshop SPEED, pages 33–43. Citeseer
Saher M, Amin A, Qureshi IA, Qureshi MA, Jawaid MM (2018) Efficient advanced encryption standard for securing cognitive radio networks. Mehran University Research Journal of Engineering and Technology 37(4):645–654
Saito T (2011) A single-key attack on 6-round kasumi. IACR Cryptol. ePrint Arch. 2011:584
Saleh, Matasem, Jhanjhi, NZ and Abdullah, Azween, Saher, Raazia (2021) Proposing encryption selection model for IoT devices based on IoT device design. In: 2021 23rd International Conference on Advanced Communication Technology (ICACT), pages 210–219. IEEE
Schneier B (1996) Applied cryptography second edition
Schneier B, Kelsey J, Whiting D, Wagner D, Hall C, Ferguson N (1998) Twofish: A 128-bit block cipher. NIST AES Proposal 15(1):23–91
Shah D, Shah T (2020) A novel discrete image encryption algorithm based on finite algebraic structures. Multimedia Tools and Applications 79(37):28023–28042
Shah J, Saxena V (2011) Performance study on image encryption schemes. arXiv:1112.0836
Shannon CE (1949) Communication theory of secrecy systems. Bell system technical journal 28(4):656–715
Shetty A, Shravya K, Krithika K (2014) A review on asymmetric cryptography rsa and elgamal algorithm. Int. J. Innovative. Res. Comput. Commun. Eng. 2(5):98–105
Sindhuja K, Devi SP (2014) A symmetric key encryption technique using genetic algorithm. International journal of computer science and information technologies 5(1):414–416
Soomro S, Belgaum MR, Alansari Z, Jain R (2019) Review and open issues of cryptographic algorithms in cyber security. In: 2019 International Conference on Computing, Electronics & Communications Engineering iCCECE), pages 158–162. IEEE
Stallings W (2017) Cryptography and network security: principles and practice. Pearson Upper Saddle River
Surendran S, Nassef A, Beheshti BD (2018) A survey of cryptographic algorithms for iot devices. In 2018 IEEE Long Island Systems, Applications and Technology Conference (LISAT), pages 1–8. IEEE
Trad A, Bahattab AA, Othman SB (2014) Performance trade-offs of encryption algorithms for wireless sensor networks. In: 2014 World Congress on Computer Applications and Information Systems (WCCAIS), pages 1–6. IEEE
Wu Y, Noonan JP, Agaian S et al (2011) Npcr and uaci randomness tests for image encryption. Cyber journals: multidisciplinary journals in science and technology, Journal of Selected Areas in Telecommunications (JSAT) 1(2):31–38
Yingbing, Zhou, Yongzhen, Li (2014) The design and implementation of a symmetric encryption algorithm based on DES. In 5th International Conference on Software Engineering and Service Science, pages 517–520. IEEE
Zeghid M, Machhout M, Khriji L, Baganne A, Tourki R et al (2007) A modified aes based algorithm for image encryption. International Journal of Computer Science and Engineering 1(1):70–75
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Competing interests
All authors certify that they have no affiliations with or involvement in any organization or entity with any financial interest or non-financial interest in the subject matter or materials discussed in this manuscript.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Farooq, A., Tariq, S., Amin, A. et al. Towards the design of new cryptographic algorithm and performance evaluation measures. Multimed Tools Appl 83, 9709–9759 (2024). https://doi.org/10.1007/s11042-023-15673-7
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-15673-7