Abstract
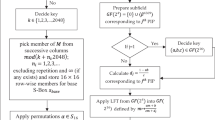
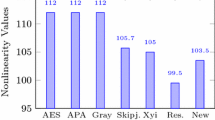
A substitution box (S-box) in data encryption is a non-linear tool that conducts substitution to assure the overall security of the system. S-box is the most important part of the block cipher. The non-linearity trait is critical for the construction of more reliable substitution boxes in data encryption. As a result, new approaches for generating high no n-linear S-boxes are required. Using the Mellin transformation and the McLaurin series, this work suggests an approach for creating Substitution boxes with a high non-linearity value of 112.5. S-box construction consists of three phases. In step 1, we build a sequence from a function's McLaurin series and then apply Mellin transformation to the sequence's terms without substituting limits. In the second phase, we solved all of the coefficients under mod 257, and in the third step, we improved the unpredictability of the initial S-box by using a particular permutation of Symmetric group \({S}_{256}\). Furthermore, the algebraic characteristics of S-box are evaluated using various tests, including non-linearity (NL), Bit Independent Criterion (BIC), Strict Avalanche Criterion (SAC), Linear Approximation Probability (LAP), and Differential Uniformity (DU), all of which certify the algebraic properties of the S-box.






Similar content being viewed by others
Data availability
The data used to support the findings of this study are available from the corresponding author upon request.
References
Abramowitz, Milton, Stegun, Irene A (1970) “Handbook of Mathematical Functions with Formulas, Graphs, and Mathematical Tables” New York: Dover’s Publications, Ninth printing
Ahmad M, Khaja IA, Baz A, Alhakami H, and Alhakami W (2020) Particle swarm optimization based highly nonlinear substitution- boxes generation for security applications. IEEE Access, 8, 116132_116147
Alanazi AS, Munir N, Khan M, Asif M, Hussain I (2021) Cryptanalysis of Novel Image Encryption Scheme Based on Multiple Chaotic Substitution Boxes. IEEE Access 9:93795–93802
Alhadawi HS, Majid MA, Lambić D, Ahmad M (2021) A novel method of S-box design based on discrete chaotic maps and cuckoo search algorithm. Multimedia Tools Appl 80(20):7333–7350
Alshammari BM, Guesmi R, Guesmi T, Alsaif H, Alzamil A (2021) Implementing a Symmetric Lightweight Cryptosystem in Highly Constrained IoT Devices by Using a Chaotic S-Box. Symmetry 13(129):1–20
Asif M, Shah T (2019) BCH Codes with computational approach and its applications in image encryption. Journal of Intelligent & Fuzzy Systems 37(3):3925–3939
Bhanot R, Hans R (2015) A review and comparative analysis of various encryption algorithms. International Journal of Security and Its Applications 9(4):289–306
Bhatti S, Safdar R, Shehzad K, Jawad M, Ahmed H (2020) New Cryptographic Scheme with Mellin Transformation. Pakistan Journal of Multidisciplinary Research 1(2):259–272
Daemen, Joan, and Vincent Rijmen (1999) "Aes proposal: Rijndael, aes algorithm submission, september 3, 1999." URL http://www.nist.gov/CryptoToolKit:37–38
Daemen J, Rijmen V (2002) AES the advanced encryption standard. The design of Rijndael 1(1):1–238
El-Latif AAA, Abd-El-Atty B, Amin M, Iliyasu AM (Dec.2020) Quantum inspired cascaded discrete-time quantum walks with induced chaotic dynamics and cryptographic applications. Sci Rep 10(1):116
Faheem ZB, Ali A, Khan MA, Ul-Haq ME, and Ahmad W (2020) Highly dispersive substitution box (S-box) design using chaos. ETRI Journal, pp. 1–14
Farah MAB, Farah A, Farah T (2020) An image encryption scheme based on a new hybrid chaotic map and optimized substitution box. Nonlinear Dyn 99(4):3041–3064
Farah MAB, Guesmi R, Kachouri A, Samet M (Mar.2020) A new design of cryptosystem based on S-box and chaotic permutation. Multimedia Tools Appl 79(6):19129–19150
Feng D, Wu W (2000). Design and analysis of block ciphers
Firdousi F, Batool SI, Amin M (2019) A novel construction scheme for nonlinear component based on quantum map. J Theor Phys 58(11):3871–3898
Gao W, Idrees B, Zafar S, and Rashid T (2020) Construction of nonlinear component of block cipher by action of modular group PSL(2, Z) on projective line PL(GF(28)). IEEE Access, 8 136736_136749
Hussain S, Jamal SS, Shah T, and Hussain I (2020) A power associative loop structure for the construction of non-linear components of block cipher, IEEE Access, 8 123492_123506
Hussain I, Shah T, Gondal MA, Khan WA, Mahmood H (2013) A group theoretic approach to construct cryptographically strong substitution boxes. Neural Comput Appl 23(1):97–104
Hussain T, Shah MA, Gondal and Khan WA (2011) Construction of Cryptographically Strong 8x8 S-boxes. World App. Sc. J., 13, 11, 2389-2395
Kazlauskas K, Kazlauskas J (2009) Key-dependent S-box generation in AES block cipher system. Informatica 20(1):23–34
Lambic D (2020) A new discrete-space chaotic map based on the multiplication of integer numbers and its application in S-box design. Nonlinear Dyn 100
Lambić D (2020) A new discrete-space chaotic map based on the multiplication of integer numbers and its application in S-box design. Nonlinear Dyn 100(1):699–711
Liu H, Kadir A, Xu C (2020) Cryptanalysis and constructing S-box based on chaotic map and backtracking. App Math Comp 376:1–11
Lokenath debnath, Dambaru Bhatta, (2016) “Integral Transforms and their Applications”. CRC press. ISBN 978–1–4200–1091–6, 19
Lu Q, Zhu C, Deng X (2020) An efficient image encryption scheme based on the LSS chaotic map and single S-box. IEEE Access 8:25664–25678
Mar PP, Latt KM (2008) New analysis methods on strict avalanche criterion of S-boxes. World Academy of Science, Engineering and Technology 48(150–154):25
Matsui M (1994) ‘“Linear cryptanalysis method for DES cipher”,’ in Proc. Adv. Cryptol, Lofthus, Norway, pp 386–397
Muhammad Asif et al (2021) "A Novel Image Encryption Technique Based on Mobius Transformation. " Computational Intelligence and Neuroscience 2021
Patro KAK, Soni A, Netam PK, Acharya B (2020) Multiple grayscale image encryption using cross-coupled chaotic maps. Journal of Information Security and Applications 52:102470
Pieprzyk J, Finkelstein G (1988) Towards effective nonlinear cryptosystem design. IEE Proceedings Part E Computers and Digital Techniques 135(6):325–335
Pub, F. I. P. S. (1999). Data encryption standard (des). FIPS PUB, 46–3
Saha M (2017) Application of Laplace-Mellin transform for cryptography. Rai Journal of Technology Research & Innovation 5(1):12–17
Santana YC (2014) “A Cryptographic Scheme OfMellin Transform,” arXiv preprint arXiv: 1401.1232
Shafique A (2020) A new algorithm for the construction of substitution box by using chaotic map. Eur Phys J Plus 135(2):1–13
Shannon CE (1949) Communication theory of secrecy systems. TBell Syst. Tech. J 28(4):656–715
Siddiqui N, Khalid H, Murtaza F, Ehatisham-Ul-Haq M, Azam MA (2020) A novel algebraic tech- nique for design of computational substitution-boxes using action of matrices on galois field. IEEE Access 8:197630–197643
Siddiqui N, Naseer A, Ehatisham-ul-Haq MA (2021) Novel Scheme of Substitution-Box Design Based on Modified Pascal’s Triangle and Elliptic Curve. Wireless Pers Commun 116(20):3015–3030
Tian Y, Lu Z (Nov.2017) Chaotic S-box: Intertwining logistic map and bacterial foraging optimization. Math Problems Eng 2017:1–11
Tsafack N, Kengne J, Abd-El-Atty B, Iliyasu AM, Hirota K, El-Latif A (2020) Design and implementation of a simple dynamical 4-D chaotic circuit with applications in image encryption. Inf Sci 515:191–217
Webster A, and Tavares S (1986) “On the design of S-boxes,” in Advances in Cryptology: Proc. of Crypto’85 Lecture Notes in Computer Science, 523–534
Zahid AH, Al-Solami E, Ahmad M (2020) A novel modular approach based substitution-box design for image encryption. IEEE Access 8:150326–150340
Zhang T, Chen CP, Chen L, Xu X, Hu B (2018) Design of highly nonlinear substitution boxes based on I-Ching operators. IEEE Trans Cybern 48(12):3349–3358
Zhu D, Tong X, Zhang M, Wang Z (2020) A new S-box generation method and advanced design based on combined chaotic system. Symmetry 12(12):2087
Zhang YQ, Hao J-L, and Wang X-Y (2020) “An efficient image encryption scheme based on S-boxes and fractional-order differential logistic map,” IEEE Access, 8 54175_54188
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Competing interests
The writers affirm that they have no established financial or interpersonal conflicts that would have seemed to have an impact on the research presented in this study.
Conflict of Interest
There is no conflict of interest.
Additional information
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Mahboob, A., Siddique, I., Asif, M. et al. Construction of highly non linear component of block cipher based on mclaurin series and mellin transformation with application in image encryption. Multimed Tools Appl 83, 7159–7177 (2024). https://doi.org/10.1007/s11042-023-15965-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-15965-y