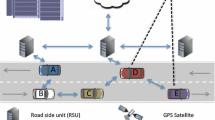
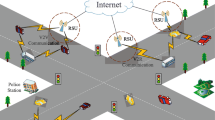
Abstract
The Intelligent transport systems (ITS) have evolved with the Internet of Vehicles (IoV) and the growth of advanced wireless technology associated with billions of smart devices connected to Internet. The rapidly evolving use of the Internet of Things (IoT) has led to significant growth in VANETs have transformed the traditional VANET topology into an Internet of vehicles (IoV),an improving road safety and automatic traffic monitoring to reduce issues related to traffic congestion. However, the security risk is expanding due to VANET communications’ dependence on resources such as computing as well as a lack of standards due to rapidly evolving technologies. Existing methods have proposed very limited protections in using a single pseudonym or invalidating the trust scheme that anonymous attackers can easily compromise. During vehicular communication, messages in VANET might be associated with reliability since the transaction of messages in vehicular communication needs to be comprehensive enough and secure enough to withstand the security threats by achieving trustworthiness transmission of the dynamic pseudonyms trust model (DPTM). Conversely, the severe challenge is to protect information exchange between vehicles because some malicious nodes might perform as Man-in-the-Middle (MiTM) network attackers due to dishonest vehicles in VANET. The increasing trustworthiness between nodes can thus lead to an increase in VANET’s trustworthy sharing of knowledge, privacy, security, accuracy, and authenticity. In this paper, we proposed a dynamic trust-based model in the term of dynamic pseudonyms changing scheme that first identify the honest vehicles as nodes to broadcast messages to normal vehicles on the road and secondly change their pseudonyms in only some specific zone to identify the dishonest nodes for protection assurance in the State of MiTM and Sybil attacks. Furthermore, it has addressed the use of pseudonym schemes for privacy and security requirements. All VANET nodes have built the trust given initially by the various RSUs and servers, trusted communication in the network. The experiment was performed based on various network scenarios to assess the accuracy and efficacy of the dynamic trust-based model. We have extensively evaluated performance measures of the F-Score, Recall, and Precision indices to demonstrate that the proposed model has outperformed the MARINE and PPARTM models already reported. The experimental results have verified the proposed lightweight model for certifying the recognized trust level of 40% of MiTM attackers with an F-Score of 95% compared to the MARINE model’s highest recognized detection of 90%.














Similar content being viewed by others
Data availability
All data used is available in the Manuscript.
References
Agrawal A, Garg A, Chaudhiri N, Gupta S, Pandey D, Roy T (2013) Security on vehicular ad hoc networks (vanet): a review paper. Int J Emerg Technol Adv Eng 3(1):231–235
Ahmad F, Adnane A, Kurugollu F, Hussain R (2019) A comparative analysis of trust models for safety applications in IoT-enabled vehicular networks. In: 2019 Wireless Days (WD), pp 1–8
Ahmad F, Kurugollu F, Adnane A, Hussain R, Hussain F (2020) MARINE: Man-in-the-middle attack resistant trust model inconnected vehicles. IEEE Internet of Things Journal 7(4):3310–3322
Ahmed S, Rehman MU, AtifIshtiaq SK, Ali A, Begum S (2018) VANSec: attack-resistant VANET security algorithm in terms of trust computation error and normalized routing overhead. J Sens 2018:1–17. https://doi.org/10.1155/2018/6576841
Ahmed, N, Deng Z, Memon I, Hassan F, Mohammadani KH, Iqbal R (2022) "A survey on location privacy attacks and prevention deployed with IoT in vehicular networks." Wirel Commun Mob Comput
Al Junaid MAH, Syed AA, Warip MNM, Azir KNFK, Romli NH (2018) Classification of security attacks in VANET: A review of requirements and perspectives. MATEC Web Conf 150:6038
Al-Kahtani MS (2012) Survey on security attacks in Vehicular Ad hoc Networks (VANETs). In: Signal Processing and Communication Systems (ICSPCS), 2012 6th International Conference, pp 1–9
Al-Turjman F, Lemayian JP (2020) Intelligence, security, and vehicular sensor networks in internet of things (IoT)-enabled smart-cities: an overview. Comput Electr Eng 87:106776
Arain QA et al (2017) Privacy protection with dynamic pseudonym-based multiple mix-zones over road networks. China Commun 14(4):89–100
Asghar M, Doss RRM, Pan L (2018) A scalable and efficient PKI based authentication protocol for VANETs. In: 2018 28th International Telecommunication Networks and Applications Conference (ITNAC), pp 1–3
Buttyán L, Holczer T, Weimerskirch A, Whyte W (2009) Slow: A practical pseudonym changing scheme for location privacy in vanets. In: 2009 IEEE Vehicular Network Conf (VNC), pp 1–8
Cavalcanti ER, de Souza JAR, Spohn MA, Gomes RC d M, da Costa AFBF (2018) VANETs’ research over the past decade: overview, credibility, and trends. ACM SIGCOMM Comput Commun Rev 48(2):31–39
Chen C, Zhang J, Cohen R, Ho PH (2010) A trust-based message propagation and evaluation framework in vanets. In Proceedings of the Int. Conf. on Information Technology Convergence and Services. 2010. https://personal.ntu.edu.sg/zhangj/paper/ifiptm10-chen.pdf
Chen C, Zhang J, Cohen R, Ho PH (2010) A trust modeling framework for message propagation and evaluation in VANETs. 2010 2nd International Conference on Information Technology Convergence and Services. IEEE, pp 1–8. https://doi.org/10.1109/ITCS.2010.5581298
Chen J-M, Li T-T, Panneerselvam J (2018) DPTMEC: a trust management based on evidence combination on attack-resistant and collaborative internet of vehicles. IEEE Access 7:148913–148922
Chukwuocha C, Thulasiraman P, Thulasiram RK (2021) Trust and scalable blockchain-based message exchanging scheme on VANET. Peer-to-Peer Network Appl:1–18
De Fuentes JM, González-Tablas AI, Ribagorda A (2011) Overview of security issues in vehicular ad-hoc networks. In: Handbook of research on mobility and computing: Evolving technologies and ubiquitous impacts. IGI Global:894–911
Deshpande A (2021) Review of Effective Trust Management Systems in VANET Environments. International Journal of Grid and Distributed Computing 14(1):1771–1780
Dotzer F, Fischer L, Magiera P (2005) Vars: A vehicle ad-hoc network reputation system. In: Sixth IEEE International Symposium on a World of Wireless Mobile and Multimedia Networks, pp 454–456
Eltahir Amal A, Saeed Rashid A, Mukherjee Amitava, Hasan Mohammad Kamrul (2016) Evaluation and analysis of an enhanced hybrid wireless mesh protocol for vehicular ad hoc network. EURASIP Journal on Wireless Communications and Networking 2016(1):1–11. https://doi.org/10.1186/s13638-016-0666-5
Emara K, Woerndl W, Schlichter J (2016) Context-based pseudonym changing scheme for vehicular adhoc networks. arXiv Prepr. arXiv1607.07656
Fabian P, Rachedi A, Guéguen C (2020) Programmable objective function for data transportation in the internet of vehicles. Trans Emerg Telecommun Technol 31(5):e3882
Fan N, Wu CQ (2018) On trust models for communication security in vehicular ad-hoc networks. Ad Hoc Netw
Förster D, Kargl F, Löhr H (2016) PUCA: a pseudonym scheme with strong privacy guarantees for vehicular ad-hoc networks. Ad Hoc Netw 37:122–132
Gerlach M (2007) Trust for vehicular applications. In: Eighth International Symposium on Autonomous Decentralized Systems (ISADS’07), pp 295–304
Guerrero-Ibáñez JA, Flores-Cortés C, Zeadally S (2013) Vehicular ad hoc networks (VANETs): Architecture, protocols and applications. In: Chilamkurti N, Zeadally S, Chaouchi H (eds) Next-generation Wireless Technologies. Springer, London, pp 49–70. https://doi.org/10.1007/978-1-4471-5164-7_5
Gurung S, Lin D, Squicciarini AC, Bertino A (2013) Information-oriented trustworthiness evaluation in vehicular ad-hoc networks. Proc. 7th Int. Conf.Network Syst. Secur. (NSS), pp 94–108. https://doi.org/10.1007/978-3-642-38631-2_8
Halabi T, Zulkernine M (2019) Trust-based cooperative game model for secure collaboration in the internet of vehicles. In: ICC 2019–2019 IEEE International Conference on Communications (ICC), pp 1–6
Hartenstein Hannes, Laberteaux LP (2008) A tutorial survey on vehicular ad hoc networks. IEEE Communications Magazine 46(6):164–171. https://doi.org/10.1109/MCOM.2008.4539481
Hasan MK, Ahmed MM, Musa SS, Islam S, Abdullah SN, Hossain E, Nafi NS, Vo N (2021) An improved dynamic thermal current rating model for PMU-based wide area measurement framework for reliability analysis utilizing sensor cloud system. IEEE Access 18(9):14446–14458
Hasrouny H, Samhat AE, Bassil C, Laouiti A (2019) Trust model for secure group leader-based communications in VANET. Wireless Networks 25:4639–4661. https://doi.org/10.1007/s11276-018-1756-6
Ahmed H, Abdel-Hamid A, El-Nasr MA (2011) A dynamic key distribution protocol for PKI-based VANETs. In 2011 IFIP Wireless Days (WD). IEEE, pp 1–3. https://doi.org/10.1109/WD.2011.6098221
Iqbal R, Butt TA, Afzaal M, Salah K (2019) Trust management in social internet of vehicles: factors, challenges, blockchain, and fog solutions. Int J Distrib Sens Netw 15(1):1550147719825820
Islam S, Hashim AH, Habaebi MH, Hasan MK (2017) Design and implementation of a multihoming-based scheme to support mobility management in NEMO. Wirel Pers Commun 95(2):457–473. https://doi.org/10.1007/s11277-016-3903-7
Islam S, Khalifa OO, Hashim AH, Hasan MK, Razzaque MA, Pandey B (2020) Design and evaluation of a multihoming-based mobility management scheme to support inter technology handoff in PNEMO. Wirel Pers Commun 114(2):1133–1153. https://doi.org/10.1007/s11277-020-07412-0
Javed AR, Rehman SU, Khan MU, Alazab M, Reddy T (2021) CANintelliIDS: detecting in-vehicle intrusion attacks on a controller area network using CNN and attention-based GRU. IEEE Trans Netw Sci Eng 8(2):1456–1466. https://doi.org/10.1109/TNSE.2021.3059881
Jayasinghe, U, Otebolaku A, Um T-W, Lee GM (2017) Data centric trust evaluation and prediction framework for IoT. In: 2017 ITU kaleidoscope: challenges for a data-driven society (ITU K), IEEE, pp 1–7
Junejo, MH, et al (2020) A privacy-preserving attack-resistant trust model for internet of vehicles ad hoc networks. Sci Program 2020
Junejo MH, Ab Rahman AAH, Shaikh RA, Yusof KM, Kumar D, Memon I (2021) Lightweight trust model with machine learning scheme for secure privacy in VANET. Procedia Comput Sci 194:45–59. https://doi.org/10.1016/j.procs.2021.10.058
Kerrache CA, Calafate CT, Cano J-C, Lagraa N, Manzoni P (2016) Trust management for vehicular networks: an adversary-oriented overview. IEEE Access 4:9293–9307
Khan U, Agrawal S, Silakari S (2015) Detection of malicious nodes (dmn) in vehicular ad-hoc networks. Procedia Comput Sci 46:965–972. https://doi.org/10.1016/j.procs.2015.01.006
Krajzewicz D, Hertkorn G, Rössel C, Wagner P (2002) SUMO (Simulation of Urban MObility)-an open-source traffic simulation. In Proceedings of the 4th middle East Symposium on Simulation and Modelling (MESM20002). pp 183–187. https://elib.dlr.de/6661/
Kumari S, Karuppiah M, Li X, Wu F, Das AK, Odelu V (2016) An enhanced and secure trust-extended authentication mechanism for vehicular ad-hoc networks. Secur Commun Netw 9(17):4255–4271
Li W, Song H (2016) ART: an attack-resistant trust management scheme for securing vehicular ad hoc networks. IEEE Trans Intell Transp Syst 17(4):960–969. https://doi.org/10.1109/TITS.2015.2494017
Li H, Pei L, Liao D, Sun G, Du X (2019) Blockchain meets VANET: an architecture for identity and location privacy protection in VANET. Peer-to-Peer Network Appl 12(5):1178–1193. https://doi.org/10.1007/s12083-019-00786-4
Li H, Pei L, Liao D, Sun G, Xu D (2019) Blockchain meets VANET: an architecture for identity and location privacy protection in VANET. Peer-to-Peer Netw Appl 12(5):1178–1193
Li W, Song W, Lu Q, Yue C (2020) Reliable congestion control mechanism for safety applications in urban VANETs. Ad Hoc Netw 98:102033
Liao D, Sun G, Zhang M, Chang V, Li H (2017) Towards location and trajectory privacy preservation in 5G vehicular social network. In 2017 IEEE International Conference on Computational Science and Engineering (CSE) and IEEE International Conference on Embedded and Ubiquitous Computing (EUC), pp 63–69. https://doi.org/10.1109/CSE-EUC.2017.197
Liao D, Li H, Sun G, Zhang M, Chang V (2018) Location and trajectory privacy preservation in 5G-Enabled vehicle social network services. J Netw Comput Appl 110:108–118. https://doi.org/10.1016/j.jnca.2018.02.002
Liu Z, Ma J, Jiang Z, Zhu H, Miao Y (2016) LSOT: a lightweight self-organized trust model in VANETs. Mob Inf Syst: 2016
Liu Y, Liu F, Gao Y, Zhao L (2018) Implementation and analysis of tightly coupled global navigation satellite system precise point positioning/inertial navigation system (GNSS PPP/INS) with insufficient satellites for land vehicle navigation. Sens 18(12):4305
Lo N-W, Tsai H-C (2009) A reputation system for traffic safety event on vehicular ad hoc networks. EURASIP J Wirel Commun Netw 2009(1):125348. https://doi.org/10.1155/2009/125348
Lu R, Lin X, Luan TH, Liang X, Shen X (2011) Pseudonym changing at social spots: an effective strategy for location privacy in vanets. IEEE Trans Veh Technol 61(1):86–96
Lu Z, Liu W, Wang Q, Qu G, Liu Z (2018) A privacy-preserving trust model based on blockchain for vanets. IEEE Access 6:45655–45664
Mansour MB, Salama C, Mohamed HK, Hammad SA (2018) VANET security and privacy-an overview. Int J Netw Secur Its Appl:10
Mármol FG, Pérez GM (2012) TRIP, a trust and reputation infrastructure-based proposal for vehicular ad hoc networks. J Netw Comput Appl 35(3):934–941. https://doi.org/10.1016/j.jnca.2011.03.028
Memon I (2015) A secure and efficient communication scheme with authenticated key establishment protocol for road networks. Wirel Pers Commun 85(3):1167–1191
Memon I (2018) Distance and clustering-based energy-efficient pseudonyms changing strategy over road network. Int J Commun Syst 31(11):e3704
Memon I, Arain QA (2017) Dynamic path privacy protection framework for continuous query service over road networks. World Wide Web 20(4):639–672. https://doi.org/10.1007/s11280-016-0403-3
Memon I, Mirza HT (2018) MADPTM: mix zones and dynamic pseudonym trust management system for location privacy. Int J Commun Syst 31(17):e3795. https://doi.org/10.1002/dac.3795
Memon I et al (2018) Pseudonym changing strategy with multiple mix zones for trajectory privacy protection in road networks. Int J Commun Syst 31(1):e3437. https://doi.org/10.1002/dac.3437
Memon I, Memon H, Arain QA (2021) Pseudonym changing strategy with mix zones based authentication protocol for location privacy in road networks. Wirel Pers Commun 116(4):3309–3329
Memon I, Hasan MK, Shaikh RA, Nebhen J, Bakar KAA, Hossain E, Tunio MH (2021) Energy-efficient fuzzy management system for internet of things connected vehicular ad hoc networks. Electron 10(9):1068
Minhas UF, Zhang J, Tran T, Cohen R (2011) A multifaceted approach to modeling agent trust for effective communication in the application of mobile ad hoc vehicular networks. IEEE Trans Syst Man, Cybern Part C (Applications Rev) 41(3):407–420
Mishra B, Panigrahy SK, Tripathy TC, Jena D, Jena SK (2011) A secure and efficient message authentication protocol for VANETs with privacy preservation. In: 2011 World Congress Inf Commun Technol, pp 880–885
Mokhtar B, Azab M (2015) Survey on security issues in vehicular ad hoc networks. Alexandria Eng J 54(4):1115–1126
Mondal A, Mitra S (2016) TDMAC: A timestamp defined message authentication code for secure data dissemination in VANET. In: Advanced Networks and Telecommunications Systems (ANTS), 2016 IEEE Int Conf, pp 1–6
Muniyandi RC, Qamar F, Jasim AN (2020) Genetic optimized location aided routing protocol for VANET based on rectangular estimation of position. Appl Sci 10(17):5759. https://doi.org/10.3390/app10175759
Nafi NS, Hasan MK, Abdallah AH (2012) Traffic flow model for vehicular network. In: In2012 international conference on computer and communication engineering (ICCCE), vol 3. IEEE, pp 738–743
Nurelmadina N, Hasan MK, Memon I, Saeed RA, Zainol Ariffin KA, Ali ES, Mokhtar RA, Islam S, Hossain E, Hassan M (2021) A systematic review on cognitive radio in low power wide area network for industrial IoT applications. Sustain 13(1):338. https://doi.org/10.3390/su13010338
Pan Y, Li J (2013) Cooperative pseudonym change scheme based on the number of neighbors in VANETs. J Netw Comput Appl 36(6):1599–1609
Parno B, Perrig A (2005) Challenges in securing vehicular networks. In: Workshop on hot topics in networks (HotNets-IV), pp 1–6. http://conferences.sigcomm.org/hotnets/2005/papers/parno.pdf
Patwardhan A, Joshi A, Finin T, Yesha Y (2006) A data intensive reputation management scheme for vehicular ad hoc networks. In: 2006 3rd Annual International Conference on Mobile and Ubiquitous Systems-Workshops, IEEE, pp 1–8. https://doi.org/10.1109/MOBIQW.2006.361754
Petit J, Schaub F, Feiri M, Kargl F (2014) Pseudonym schemes in vehicular networks: a survey. IEEE Commun Surv Tutor 17(1):228–255
Rai IA, Shaikh RA, Hassan SR (2020) A hybrid dual-mode trust management scheme for vehicular networks. Int J Distrib Sens Netw 16(7):1550147720939372. https://doi.org/10.1177/1550147720939372
Ravi Chandrasekar, Anmol Tigga G, Reddy Thippa, Hakak Saqib, Alazab Mamoun (2022) Driver identification using optimized deep learning model in smart transportation. ACM Trans Internet Technol 22(4):1–7. https://doi.org/10.1145/3412353
Ravie CM et al (2021) An improved harmony search algorithm for proactive routing protocol in VANET. J Adv Transp (2021)
Raya M, Papadimitratos P, Gligor VD, Hubaux J-P (2008) “On data-centric trust establishment in ephemeral ad hoc networks. In: INFOCOM 2008. The 27th conference on computer communications, IEEE, pp 1238–1246
Salem AH, Abdel-Hamid A, El-Nasr MA (2016) The case for dynamic key distribution for PKI-based VANETS. arXiv Prepr. arXiv1605.04696
Samara G, Al-Raba’nah Y (2017) Security issues in vehicular ad hoc networks (VANET): a survey. arXiv Prepr. arXiv1712.04263
Sedjelmaci H, Senouci SM (2015) An accurate and efficient collaborative intrusion detection framework to secure vehicular networks. Comput Electr Eng 43:33–47
Sengar JS (2015) SURVEY: reputation and trust management in VANETs. Int J Grid Distrib Comput 8(4):301–306. https://www.earticle.net/Article/A253964
Shaikh RA, Alzahrani AS (2013) Trust management method for vehicular ad hoc networks. In: Singh K, Awasthi AK (eds) Quality, Reliability, Security and Robustness in Heterogeneous Networks. QShine 2013. Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering, vol 115. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-642-37949-9_70
Shaikh RA, Alzahrani AS (2014) Intrusion-aware trust model for vehicular ad hoc networks. Secur Commun Networks 7(11):1652–1669
Sharma S, Sparsh, Kaul A (2021) VANETs cloud: architecture, applications, challenges, and issues. Arch Computation Method Eng 28:2081–2102
Sheikh MS, Liang J (2019) A comprehensive survey on VANET security services in traffic management system. Wirel Commun Mob Comput 2019:1–23. https://doi.org/10.1155/2019/2423915
Shrivastava S (2019) V2V vehicle safety communication. In: Connected Vehicles, Springer, pp 117–155
Soleymani SA et al (2021) A security and privacy scheme based on node and message authentication and trust in fog-enabled VANET. Vehicular Commun 29:100335
Sumra IA, Akhtar AN (2020) Applications of internet of vehicle (IoV): a survey. LGURJCSIT 4(2):59–70
Sun Y, Zhang B, Zhao B, Su X, Su J (2015) Mix-zones optimal deployment for protecting location privacy in VANET. Peer-to-Peer Netw Appl 8(6):1108–1121
Sun A, Rui, YH, Zhu L (2021) Communication by credence: trust communication in vehicular ad hoc networks. Mob Netw Appl 2021:1–13
Tajeddine A, Kayssi A, Chehab A (2010) A privacy-preserving trust model for VANETs. In: 2010 10th IEEE International Conference on Computer and Information Technology. IEEE, pp 832–837. https://doi.org/10.1109/CIT.2010.157
Tangade SS, Manvi SS (2013) A survey on attacks, security and trust management solutions in VANETs. In: 2013 Fourth international conference on computing, communications and networking technologies (ICCCNT), IEEE, pp 1–6. https://doi.org/10.1109/ICCCNT.2013.6726668
Sommer, C, Eckhoff S, Brummer A, Buse DS, Hagenauer F, Joerer S, Segata M (2019) Veins: The open source vehicular network simulation framework. Recent Advances in Network Simulation: The OMNeT++ Environment and its Ecosystem 215–252. https://doi.org/10.1007/978-3-030-12842-5_6
Wang S, Yao N (2019) A RSU-aided distributed trust framework for pseudonym-enabled privacy preservation in VANETs. Wirel Netw 25(3):1099–1115
Wang J, Zhang Y, Wang Y, Gu X (2016) RPRep: a robust and privacy-preserving reputation management scheme for pseudonym-enabled VANETs. Int J Distrib Sens Netw 12(3):6138251
Wang C, Shen J, Lai J-F, Liu J (2020) B-TSCA: Blockchain assisted trustworthiness scalable computation for V2I authentication in VANETs. IEEE Transactions on Emerging Topics in Computing 9(3):1386–1396. https://doi.org/10.1109/TETC.2020.2978866
Yan X et al (2021) A kind of event trust model for VANET based on statistical method. Wirel Pers Commun 118(1):489–503. https://doi.org/10.1007/s11277-020-08027-1
Yang N (2013) A similarity based trust and reputation management framework for vanets. Int J Futur Gener Commun Netw 6(2):25–34
Zhang J (2011) A survey on trust management for vanets, in Advanced information networking and applications (AINA). IEEE Int Conf 2011:105–112
Zhao H, Sun D, Yue H, Zhao M, Cheng S (2018) Dynamic trust model for vehicular cyber-physical systems. IJ Netw Secur 20(1):157–167
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
“The authors declare no conflict of interest.”
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Memon, I., Shaikh, R.A. & Shaikh, H. Dynamic pseudonyms trust-based model to protect attack scenario for internet of vehicle ad-hoc networks. Multimed Tools Appl 83, 13395–13426 (2024). https://doi.org/10.1007/s11042-023-16110-5
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-16110-5