Abstract
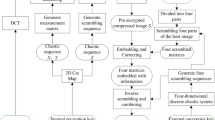
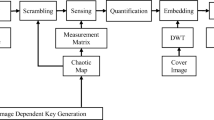
This paper introduces a novel Fast Visually Meaningful Image Encryption based on Compressive Sensing and Joint Diffusion and Scrambling (FVMIECJ). Our approach leverages several innovative aspects: First, we employ a novel seven-dimensional (7D) hyper-chaotic system to generate the measurement matrix for Compressive Sensing (CS) and the random sequences essential for subsequent encryption operations. Utilizing this 7D hyper-chaotic system enhances the randomness and security of the image encryption process. Second, we propose a novel joint diffusion and scrambling encryption scheme to improve the security performance of the algorithm further. This algorithm combines different cryptographic techniques to provide robust protection against attacks. Finally, we present an efficient visual image encryption framework for high-speed encryption applications. This framework ensures robust security and delivers exceptional encryption speed, making it suitable for scenarios where fast encryption is required. Through simulations and comparative analysis, FVMIECJ demonstrated outstanding performance in terms of security and speed, making it a promising solution for image encryption applications.










Similar content being viewed by others
Data Availibility Statement
The USC-SIPI dataset analysed in this paper are available in the USC-SIPI repository, URL: https://sipi.usc.edu/database/database.php?volume=misc. The BossBase 1.01 dataset analysed in this paper are available in the BossBase 1.01 repository, URL: http://dde.binghamton.edu/download/. The source codes of FVMIECJ algorithm are available in the GitHub repository, URL: https://github.com/wushuang42/FVMIECJ.
Abbreviations
- CS::
-
Compressive sensing
- FVMIECJ::
-
Fast Visually Meaningful Image Encryption algorithm based on Compressive sensing and Joint diffusion and scrambling
- LSB::
-
Least Significant Bit
- 7D::
-
Seven-dimensional
- DNA::
-
Deoxyribonucleic Acid
- VMIE::
-
Visually Meaningful Image Encryption algorithm
- IWT::
-
Discrete Integer Wavelet Transform
- SVD::
-
Singular Value Decomposition
- DCT::
-
Discrete Cosine Transform
- LE::
-
Lyapunov Exponents
- FFT::
-
Fast Fourier Transform
- DWT::
-
Discrete Wavelet Transform
- LL::
-
Low-Low Component
- LH::
-
Low-High Component
- HL::
-
High-Low Component
- HH::
-
High-High Component
- RIP::
-
Restricted Isometry Property
- MP::
-
Matching pursuit
- OMP::
-
Orthogonal Matching Pursuit
- \(\varvec{\textrm{SL}}\) \({_0}\)::
-
Smoothed \(l_0\) norm
- SHA-256::
-
Secure Hash Algorithm 256-bit
- CR::
-
Compression Ratio
- PSNR::
-
Peak Signal-to-Noise Ratio
- MSSIM::
-
Mean Structural Similarity
- MSE::
-
Mean Square Error
- TS::
-
Threshold
- CC::
-
Correlation Coefficient
References
Li X-W (2015) I-K Lee Modified computational integral imaging-based double image encryption using fractional fourier transform. Opt Lasers Eng 66:112–121
Wang Y, Quan C, Tay CJ (2016) Asymmetric optical image encryption based on an improved amplitude-phase retrieval algorithm. Opt Lasers Eng 78:8–16
Chai X, Gan Z, Yuan K, Chen Y, Liu X (2019) A novel image encryption scheme based on dna sequence operations and chaotic systems. Neural Comput Appl 31(1):219–237
Chen J, Chen L, Zhou Y (2020) Cryptanalysis of a dna-based image encryption scheme. Inf Sci 520:130–141
Wang X, Li Y (2021) Chaotic image encryption algorithm based on hybrid multi-objective particle swarm optimization and dna sequence. Opt Lasers Eng 137:106393
Abbasi AA, Mazinani M, Hosseini R (2020) Chaotic evolutionary-based image encryption using rna codons and amino acid truth table. Opt Laser Technol 132:106465
Liu L, Lei Y, Wang D (2020) A fast chaotic image encryption scheme with simultaneous permutation-diffusion operation. IEEE Access 8:27361–27374
Sahasrabuddhe A, Laiphrakpam DS (2021) Multiple images encryption based on 3d scrambling and hyper-chaotic system. Inf Sci 550:252–267
Wang X, Guan N (2020) A novel chaotic image encryption algorithm based on extended zigzag confusion and rna operation. Opt Laser Technol 131:106366
Wang X, Liu L (2021) Application of chaotic josephus scrambling and rna computing in image encryption. Multimed Tools Appl 80:23337–23358
Zhang D, Chen L, Li T (2021) Hyper-chaotic color image encryption based on transformed zigzag diffusion and rna operation. Entropy 23(3):361
Zhou N, Yan X, Liang H, Tao X, Li G (2018) Multi-image encryption scheme based on quantum 3d arnold transform and scaled zhongtang chaotic system. Quantum Inf Process 17(12):1–36
Chai X, Gan Z, Yang K, Chen Y, Liu X (2017) An image encryption algorithm based on the memristive hyperchaotic system, cellular automata and dna sequence operations. Signal Process Image Commun 52:6–19
Chai X, Bi J, Gan Z, Liu X, Zhang Y, Chen Y (2020) Color image compression and encryption scheme based on compressive sensing and double random encryption strategy. Signal Process 176:107684
Yang Y-G, Guan B-W, Li J, Li D, Zhou Y-H, Shi W-M (2019) Image compression-encryption scheme based on fractional order hyper-chaotic systems combined with 2d compressed sensing and dna encoding. Opt Laser Technol 119:105661
Diab H (2018) An efficient chaotic image cryptosystem based on simultaneous permutation and diffusion operations. IEEE Access 6:42227–42244
Hu T, Liu Y, Gong L-H, Guo S-F, Yuan H-M (2017) Chaotic image cryptosystem using dna deletion and dna insertion. Signal Process 134:234–243
Hu T, Liu Y, Gong L-H, Ouyang C-J (2017) An image encryption scheme combining chaos with cycle operation for dna sequences. Nonlinear Dyn 87(1):51–66
Li T, Shi J, Zhang D (2021) Color image encryption based on joint permutation and diffusion. J Electron Imaging 30(01):013008
Fang H, Vorobyov SA, Jiang H, Taheri O (2014) Permutation meets parallel compressed sensing: How to relax restricted isometry property for 2d sparse signals. IEEE Trans Signal Process 62(1):196–210
Zhou N, Jiang H, Gong L, Xie X (2018) Double-image compression and encryption algorithm based on co-sparse representation and random pixel exchanging. Opt Lasers Eng 110:72–79
Bao L, Zhou Y (2015) Image encryption: Generating visually meaningful encrypted images. Inf Sci 324:197–207
Kanso A, Ghebleh M (2017) An algorithm for encryption of secret images into meaningful images. Opt Lasers Eng 90:196–208
Wen W, Zhang Y, Fang Y, Fang Z (2018) Image salient regions encryption for generating visually meaningful ciphertext image. Neural Comput Appl 29(3):653–663
Chai X, Wu H, Gan Z, Zhang Y, Chen Y, Nixon KW (2020) An efficient visually meaningful image compression and encryption scheme based on compressive sensing and dynamic lsb embedding. Opt Lasers Eng 124:105837
Huo D, Zhu Z, Wei L, Han C, Zhou X (2021) A visually secure image encryption scheme based on 2d compressive sensing and integer wavelet transform embedding. Opt Commun 492:126976
Zhu L, Song H, Zhang X, Yan M, Zhang T, Wang X, Xu J (2020) A robust meaningful image encryption scheme based on block compressive sensing and svd embedding. Signal Process 175:107629
Jiang D, Liu L, Zhu L, Wang X, Rong X, Chai H (2021) Adaptive embedding: a novel meaningful image encryption scheme based on parallel compressive sensing and slant transform. Signal Process 188:108220
Wang X, Liu C, Jiang D (2021) A novel triple-image encryption and hiding algorithm based on chaos, compressive sensing and 3d dct. Inf Sci 574:505–527
Wang X, Ren Q, Jiang D (2021) An adjustable visual image cryptosystem based on 6d hyperchaotic system and compressive sensing. Nonlinear Dyn 104(4):4543–4567
Yang Y-G, Wang B-P, Yang Y-L, Zhou Y-H, Shi W-M, Liao X (2023) A visually meaningful image encryption algorithm based on adaptive 2d compressive sensing and chaotic system. Multimed Tools Appl 82:22033–22062
Ye G, Pan C, Dong Y, Shi Y, Huang X (2020) Image encryption and hiding algorithm based on compressive sensing and random numbers insertion. Signal Process 172:107563
Chai X, Wu H, Gan Z, Zhang Y, Chen Y (2020) Hiding cipher-images generated by 2-d compressive sensing with a multi-embedding strategy. Signal Process 171:107525
Ponuma R, Amutha R, Aparna S, Gopal G (2019) Visually meaningful image encryption using data hiding and chaotic compressive sensing. Multimed Tools Appl 78(18):25707–25729
Zhang D, Shafiq M, Wang L, Srivastava G, Yin S (2023) Privacy-preserving remote sensing images recognition based on limited visual cryptography. CAAI Trans Intell Technol 8:1166–1177
Zhang D, Ren L, Shafiq M, Gu Z (2022) A lightweight privacy-preserving system for the security of remote sensing images on iot. Remote Sensing 14(24):6371
Ren L, Zhang D (2022) A privacy-preserving biometric recognition system with visual cryptography. Adv Multimed 1–7:2022
Mukherjee I, Ganguly R (2018) Multiple video clips preservation using folded back audio-visual cryptography scheme. Multimed Tools Appl 77(5):5281–5301
Tripathi J, Saini A, Kishan Nikhil, Shazad (2020) An augmented model for image security: enhanced visual cryptography. Procedia Comput Sci 167:323–333
Al-Obeidi AS, Fawzi Al-Azzawi S, Abdullah Hamad A, Lellis Thivagar M, Meraf Z, Ahmad S (2021) A novel of new 7d hyperchaotic system with self-excited attractors and its hybrid synchronization. Comput Intell Neurosci 2021:3081345
Donoho DL (2006) Compressed sensing. IEEE Trans Inf Theory 52(4):1289–1306
Candes EJ, Tao T (2005) Decoding by linear programming. IEEE Trans Inf Theory 51(12):4203–4215
Mallat SG, Zhang Z (1993) Matching pursuits with time-frequency dictionaries. IEEE Trans Signal Process 41(12):3397–3415
Needell D, Tropp JA (2009) Cosamp: iterative signal recovery from incomplete and inaccurate samples. Appl Comput Harmon Anal 26(3):301–321
Mohimani H, Babaie-Zadeh M, Jutten C (2009) A fast approach for overcomplete sparse decomposition based on smoothed \(\ell ^{0}\) norm. IEEE Trans Signal Process 57(1):289–301
Alvarez G, Li S (2006) Some basic cryptographic requirements for chaos-based cryptosystems. Int J Bifurcat Chaos 16(08):2129–2151
Wen W, Hong Y, Fang Y, Li M, Li M (2020) A visually secure image encryption scheme based on semi-tensor product compressed sensing. Signal Process 173:107580
Li C, Zhang Y, Xie EY (2019) When an attacker meets a cipher-image in 2018: a year in review. J Inf Secur Appl 48:102361
Li C, Lin D, Feng B, Lu J, Hao F (2018) Cryptanalysis of a chaotic image encryption algorithm based on information entropy. IEEE Access 6:75834–75842
Li C, Lin D, Lu J, Hao F (2018) Cryptanalyzing an image encryption algorithm based on autoblocking and electrocardiography. IEEE Multimedia 25(4):46–56
Zhu L, Jiang D, Ni J, Wang X, Rong X, Ahmad M, Chen Y (2022) A stable meaningful image encryption scheme using the newly-designed 2d discrete fractional-order chaotic map and bayesian compressive sensing. Signal Process 195:108489
Wang X, Liu C, Jiang D (2022) A novel visually meaningful image encryption algorithm based on parallel compressive sensing and adaptive embedding. Expert Syst Appl 209:118426
Wang X, Liu C, Jiang D (2022) Visually meaningful image encryption scheme based on new-designed chaotic map and random scrambling diffusion strategy. Chaos Solitons Fractal 164:112625
Chai X, Gan Z, Chen Y, Zhang Y (2017) A visually secure image encryption scheme based on compressive sensing. Signal Process 134:35–51
Wang H, Xiao D, Li M, Xiang Y, Li X (2019) A visually secure image encryption scheme based on parallel compressive sensing. Signal Process 155:218–232
Gan Z, Sun M, Song Y, Chai X, Jiang D, Long G, He X (2023) Visually meaningful image encryption scheme using multi-parameter fractal theory and block synchronous sorting diffusion. Phys Scr 98(8):085216
Acknowledgements
This work was supported by the Guanghua Youth Project of Southwestern University of Finance and Economics (Grant no. 220810001002020113).
Author information
Authors and Affiliations
Contributions
Duzhong Zhang: Conceptualization, Methodology, Software, Writing - original draft. Chao Yan: Software, Validation. Yun Duan: Validation, Writing - review & editing. Sijian Liang: Validation, Writing - review & editing. Jiang Wu: Methodology, Writing - review & editing. Taiyong Li: Conceptualization, Methodology, Writing - review & editing.
Corresponding author
Ethics declarations
Competing Interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Zhang, D., Yan, C., Duan, Y. et al. A fast visually meaningful image encryption algorithm based on compressive sensing and joint diffusion and scrambling. Multimed Tools Appl 83, 70693–70725 (2024). https://doi.org/10.1007/s11042-024-18343-4
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-024-18343-4