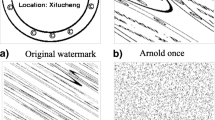
Abstract
In order to make the image copyright protection system can resist network attacks, and to solve the problems of unknown copyright owner, difficulty in data integrity verification and unauthorized redistribution, a digital image copyright protection method based on blockchain and zero trust mechanism was proposed. Firstly, after the copyright owner signs with the elliptic curve digital signature algorithm (ECDSA), the signature and copyright information are encrypted with the elliptic curve cryptography (ECC) algorithm, and the ciphertext and the generated image hashing are uploaded to the blockchain; Then, the smart contract is called to authenticate the copyright owner, the similarity of the hash value is used to detect the infringement of the verified image, the MD5 key generated by the image hashing value is used to encrypt the detected image, the ciphertext and encrypted image are uploaded to the interplanetary file system (IPFS), and the corresponding storage address is returned to the blockchain. Consumers can download ciphertext and encrypted images in IPFS as needed after completing asset evaluation and paying when calling the dual-smart contract to initiate copyright transaction. Experimental results show that the proposed method can not only authenticate the identity, but also realize double encryption of the image and copyright information. It can prevent the unauthorized use and redistribution of digital content, and improve the overall security of the image copyright protection system.

















Similar content being viewed by others
Data availability
Data sharing not applicable to this article as no datasets were generated or analyzed during the current study.
References
Zhao M, Wang B, Wang W, Kong Y, Zheng T, Ren K (2022) Guided Erasable Adversarial Attack (GEAA) toward shared data protection. IEEE Trans Inf Forensics Secur 17:2468–2482. https://doi.org/10.1109/TIFS.2022.3186791
Zhang D, Wu XJ, Xu T, Kittler J (2022) WATCH: two-stage discrete cross-media hashing. IEEE Trans Knowl Data Eng. https://doi.org/10.1109/TKDE.2022.3159131
Yan Z (2021) The color and artistic features of murals in Dunhuang cave 465 in Mogao Grottoes. The 6th International Conference on Arts, Design and Contemporary Education (ICADCE2020). Atlantis Press, 56–62. https://doi.org/10.2991/assehr.k.210106.012
Lin CW, Wu TY, Fournier-Viger P, Lin G, Zhan J (2016) Fast algorithms for hiding sensitive high-utility itemsets in privacy-preserving utility mining. Eng Appl Artif Intell 55:269–284. https://doi.org/10.1016/j.engappai.2016.07.003
Cheng P, Roddick JF, Chu SC, Lin CW (2016) Privacy preservation through a greedy, distortion-based rule-hiding method. Appl Intell 44(2):295–306. https://doi.org/10.1007/s10489-015-0671-0
Sultana M, Hossain A, Laila F, Taher K, Lslam M (2020) Towards developing a secure medical image sharing system based on zero trust principles and blockchain technology. BMC Med Inform Decis Mak 20(1):256. https://doi.org/10.1186/s12911-020-01275-y. (1-10)
Wylde A (2021) Zero trust: never trust, always verify. 2021 international conference on cyber situational awareness, data analytics and assessment (cybersa). IEEE, 1–4. https://doi.org/10.1109/CyberSA52016.2021.9478244
Zheng J, Teng S, Li P, Ou W, Zhou D, Ye J (2021) A novel video copyright protection scheme based on blockchain and double watermarking. Secur Commun Netw 6493306:1–16. https://doi.org/10.1155/2021/6493306
Wang C, Ma B, Xia Z, Li J, Li Q, Liu X, Sang S (2022) Geometric resistant polar quaternion discrete fourier transform and its application in color image zero-hiding. ISA Trans 125:665–680. https://doi.org/10.1016/j.isatra.2021.06.019
Kadian P, Arora SM, Arora N (2021) Robust digital watermarking techniques for copyright protection of digital data: a survey. Wireless Pers Commun 118(4):3225–3249. https://doi.org/10.1007/s11277-021-08177-w
Janani T, Darak Y, Brindha M (2021) Secure similar image search and copyright protection over encrypted medical image databases. IRBM 42(2):83–93. https://doi.org/10.1016/j.irbm.2020.02.005
Li Y, Chen C, Liu N, Huang H, Zheng Z, Yan Q (2020) A blockchain-based decentralized federated learning framework with committee consensus. IEEE Network 35(1):234–241. https://doi.org/10.1109/MNET.011.2000263
Yang X, Li T, Pei X, Wen L, Wang C (2020) Medical data sharing scheme based on attribute cryptosystem and blockchain technology. IEEE Access 8:45468–45476. https://doi.org/10.1109/ACCESS.2020.2976894
Hassan HER, Tahoun M, ElTaweel GS (2020) A robust computational DRM framework for protecting multimedia contents using AES and ECC. Alex Eng J 59(3):1275–1286. https://doi.org/10.1016/j.aej.2020.02.020
Mehraj S, Banday MT (2020) Establishing a zero trust strategy in cloud computing environment. 2020 International Conference on Computer Communication and Informatics (ICCCI). IEEE, 1–6. https://doi.org/10.1109/ICCCI48352.2020.9104214
Samaniego M, Deters R (2018) Zero-trust hierarchical management in IoT. 2018 IEEE international congress on Internet of Things (ICIOT). IEEE, 88–95. https://doi.org/10.1109/ICIOT.2018.00019
Shen J (2021) Blockchain technology and its applications in digital content copyright protection. Proceedings of the 4th International Conference on Economic Management and Green Development. Springer, 18–25. https://doi.org/10.1007/978-981-16-5359-9_3
Li T, Wang H, He D, Yu J (2022) Blockchain-based privacy-preserving and rewarding private data sharing for IoT. IEEE Internet Things J 9(16):15138–15149. https://doi.org/10.1109/JIOT.2022.3147925
Hei Y, Liu J, Feng H, Li D, Liu Y, Wu Q (2021) Making MA-ABE fully accountable: a blockchain-based approach for secure digital right management. Comput Netw 191:108029. https://doi.org/10.1016/j.comnet.2021.108029
Gao J, Yu H, Zhu X, Li X (2021) Blockchain-based digital rights management scheme via multiauthority ciphertext-policy attribute-based encryption and proxy re-encryption. IEEE Syst J 15(4):5233–5244. https://doi.org/10.1109/JSYST.2021.3064356
Rana S, Mishra D (2021) Provably secure authenticated content key distribution framework for IoT-enabled enterprise digital rights management systems. Int J Ad Hoc Ubiquitous Comput 36(3):131–140. https://doi.org/10.1504/IJAHUC.2021.113863
Mishra D, Kasi A, Obaidat M S, Rewal P, Mishra A (2021) Construction of Lightweight Content key Distribution Framework for DRM systems. 2021 IEEE 6th International Conference on Computing, Communication and Automation (ICCCA). IEEE, 863–868. https://doi.org/10.1109/ICCCA52192.2021.9666245
Li X, Darwich M, Salehi MA, Bayoumi M (2021) A survey on cloud-based video streaming services. Adv Comput 123:193–244. https://doi.org/10.1016/bs.adcom.2021.01.003
Liu L, Shang W, Lin W, Huang W (2021) A decentralized copyright protection, transaction and content distribution system based on blockchain 3.0. 2021 21st ACIS International Winter Conference on Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing (SNPD-Winter). IEEE, 45–50. https://doi.org/10.1109/SNPDWinter52325.2021.00018
Mehta R, Kapoor N, Sourav S, Shorey R (2019) Decentralised image sharing and copyright protection using blockchain and perceptual hashes. 2019 11th International Conference on Communication Systems & Networks (COMSNETS). IEEE, 1–6. https://doi.org/10.1109/COMSNETS.2019.8711440
Guo J, Li C, Zhang G, Sun Y, Bie R (2020) Blockchain-enabled digital rights management for multimedia resources of online education. Multimed Tools Appl 79(15):9735–9755. https://doi.org/10.1007/s11042-019-08059-1
Kumar R, Tripathi R, Marchang N, Srivastava G, Gadekallu TR, Xiong NN (2021) A secured distributed detection system based on IPFS and blockchain for industrial image and video data security. J Parallel Distrib Comput 152:128–143. https://doi.org/10.1016/j.jpdc.2021.02.022
Liu Y, Zhang J, Wu S, Pathan MS (2021) Research on digital copyright protection based on the hyperledger fabric blockchain network technology. PeerJ Comput Sci 7:e709. https://doi.org/10.7717/peerj-cs.709
Wang Z, Li T (2021) Research on Image copyright confirmation and protection model based on blockchain. 2021 2nd International Conference on Control, Robotics and Intelligent System. ACM, 230–234. https://doi.org/10.1145/3483845.3483886
Wang BW, Shi JW, Wang WS, Zhao P (2022) Image copyright protection based on blockchain and zero-watermark. IEEE Trans Netw Sci Eng 9(4):2188–2199. https://doi.org/10.1109/TNSE.2022.3157867
Brabin D, Ananth C, Bojjagani S (2022) Blockchain based security framework for sharing digital images using reversible data hiding and encryption. Multimed Tools Appl 81(17):24721–24738. https://doi.org/10.1007/s11042-022-12617-5
Lin CW, Srivastava G, Zhang YY, Djenouri Y, Aloqaily M (2021) Privacy-preserving multiobjective sanitization model in 6G IoT environments. IEEE Internet Things J 8(7):5340–5349. https://doi.org/10.1109/JIOT.2020.3032896
Prokop K, Połap D, Srivastava G, Lin CW (2023) Blockchain-based federated learning with checksums to increase security in internet of things solutions. J Ambient Intell Humaniz Comput 14(5):4685–4694. https://doi.org/10.1007/s12652-022-04372-0
Gai K, She Y, Zhu L, Choo K R, Wan Z (2022) A blockchain-based access control scheme for zero trust cross-organizational data sharing. ACM Trans Internet Technol (TOIT): 1–24. https://doi.org/10.1145/3511899
Wang J, Chen JH, Xiong N, Alfarraj O, Tolba A, Ren YJ (2022) S-BDS: an effective blockchain-based data storage scheme in zero-trust IoT. ACM Trans Internet Technol 23(3):1–23. https://doi.org/10.1145/3511902
Jin X, Jing PG, Wu JS, Xu J, Su YT (2021) Visual sentiment classification via low-rank regularization and label relaxation. IEEE Trans Cognit Dev Syst 14(4):1678–1690
Jin X, Guo CL, He Z, Xu J, Wang YW, Su YT (2021) FCMNet: frequency-aware cross-modality attention networks for RGB-D salient object detection. Neurocomputing 491:417–425. https://doi.org/10.1016/j.neucom.2022.04.015
Jin X, Yi K, Xu J (2022) MoADNet: mobile asymmetric dual-stream networks for real-time and lightweight RGB-D salient object detection. IEEE Trans Circuits Syst Video Technol 32(11):7632–7645. https://doi.org/10.1109/TCSVT.2022.3180274
Jin X, He Z, Wang YW, Yu JW, Xu J (2021) Towards general object-based video forgery detection via dual-stream networks and depth information embedding. Multimed Tools Appl 81:35733–35749. https://doi.org/10.1007/s11042-021-11126-1
Jin X, He Z, Xu J, Wang YW, Su YT (2022) Video splicing detection and localization based on multi-level deep feature fusion and reinforcement learning. Multimed Tools Appl 81:40993–41011. https://doi.org/10.1007/s11042-022-13001-z
Acknowledgements
This work is supported by the National Natural Science Foundation of China (No. 61862041). The authors also gratefully acknowledge the helpful comments and suggestions of the reviewers, which have improved the presentation.
Author information
Authors and Affiliations
Corresponding authors
Ethics declarations
Conflict of interests
The authors declare that they have no conflict of interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Zhang, Qy., Wu, Gr., Yang, R. et al. Digital image copyright protection method based on blockchain and zero trust mechanism. Multimed Tools Appl 83, 77267–77302 (2024). https://doi.org/10.1007/s11042-024-18514-3
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-024-18514-3