Abstract
Identity document (ID) verification is crucial in fostering trust in the digital realm, especially with the increasing shift of transactions to online platforms. Our research, building upon our previous work (Al-Ghadi et al. 2023), delves deeper into ID verification by focusing on guilloche patterns. We present two innovative ID verification models leveraging contrastive and adversarial learning. These models enhance guilloche pattern detection, offering new insights into identifying counterfeit IDs. Each approach comprises two main components: (i) guilloche pattern recognition and feature generation using a convolutional neural network (CNN), and (ii) precise classification of input data as authentic or forged. We evaluate our models extensively on the MIDV and FMIDV datasets, achieving accuracy and F1-score results ranging from 68-92% and 75-100%, respectively. Our study, incorporating contrastive and adversarial learning, contributes significantly to the ongoing discourse on ID verification, specifically in analyzing guilloche patterns.













Similar content being viewed by others
Data Availability
Both the data and forgery detection code are made available at https://github.com/malghadi/CheckID.
Notes
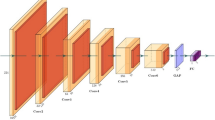
The dimensions of each latent vector are \(1664 \times 7 \times 7\).
Here we have used the “Adaptive Average Pooling” algorithm from the PyTorch library. For more details, see: https://pytorch.org/cppdocs/api/classtorch_1_1nn_1_1_adaptive_avg_pool1d.html .
The concatenated vector is of dimension \(3328 \times 7 \times 7\)
References
Al-Ghadi M, Ming Z, Gomez-Krämer P, Burie JC, Coustaty M, and Sidere N (2023) Guilloche detection for ID authentication: a dataset and baselines. In: Proceedings of the international workshop on multimedia signal processing (MMSP). IEEE, pp 1–6
Jung C, Kim G, Jeong M, Jang J, Dong Z, Badloe T, Yang JK, Rho J (2021) Metasurface-driven optically variable devices. Chem Rev 121:13 013–13 050
Stepien PJ, Gajda R., Marszalek A (1998) Guilloche in diffractive optically variable image devices. In: Optical security and counterfeit deterrence techniques II, SPIE conference series, vol 3314. SPIE, 4, pp 231–236
Li CL, Sohn K, Yoon J, Pfister T (2021) Cutpaste: self-supervised learning for anomaly detection and localization. Proceedings of the IEEE computer society conference on computer vision and pattern recognition, pp 9659–9669
Ghanmi N, Nabli C, Awal AM (2021) Checksim: a reference-based identity document verification by image similarity measure. In: Document analysis and recognition - ICDAR 2021 workshops, vol 12916 LNCS. Springer Science and Business Media Deutschland GmbH, pp 422–436
Kada O, Kurtz C, van Kieu C, Vincent N (2022) Hologram detection for identity document authentication. In: El Yacoubi M, Granger E, Yuen PC, Pal U, Vincent N (eds) Pattern recognition and artificial intelligence. Springer International Publishing, Cham, pp 346–357
Chapel MN, Al-Ghadi M, Burie JC (2023) Authentication of holograms with mixed patterns by direct LBP comparison. In: Proceedings of the international workshop on multimedia signal processing (MMSP). IEEE, pp 7–12
Chen C, Xie Y, Lin S, Qiao R, Zhou J, Tan X, Zhang Y, Ma L (2021) Novelty detection via contrastive learning with negative data augmentation. In: IJCAI international joint conference on artificial intelligence. International Joint Conferences on Artificial Intelligence, pp 606–614
Chen T, Kornblith S, Norouzi M, Hinton G (2020) A simple framework for contrastive learning of visual representations. In: International conference on machine learning
Ng T, Kim HJ, Lee VT, DeTone D, Yang TY, Shen T, Ilg E, Balntas V, Mikolajczyk K, Sweeney C (2022) Ninjadesc: content-concealing visual descriptors via adversarial learning. In: Proceedings of the IEEE/CVF conference on computer vision and pattern recognition (CVPR), pp 12 797–12 807
Zhu J, Kaplan R, Johnson J, Fei-Fei L (2018) Hidden: hiding data with deep networks. Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), vol 11219 LNCS, pp 682–697
Chernov TS, Nikolaev DP, Kliatskine VM, Chernov TS, Nikolaev DP, Kliatskine VM (2015) A method of periodic pattern localization on document images. In: Society of photo-optical instrumentation engineers (SPIE) Conference Series, vol 9875. SPIE, p 987508
Ghanmi N, Awal AM (2018) A new descriptor for pattern matching: application to identity document verification. In: Proceedings - 13th IAPR international workshop on document analysis systems, DAS 2018. Institute of Electrical and Electronics Engineers Inc., pp 375–380
Castelblanco A, Solano J, Lopez C, Rivera E, Tengana L, Ochoa M (2020) Machine learning techniques for identity document verification in uncontrolled environments: A case study. In: Mexican conference on pattern recognition, vol 12088 LNCS. Springer, pp 271–281
Sirajudeen M, Anitha R (2020) Forgery document detection in information management system using cognitive techniques. J Intell Fuzzy Syst 39:8057–8068
Centeno AB, Terrades OR, Canet JL, Morales CC (2019) Recurrent comparator with attention models to detect counterfeit documents. In: Proceedings of the international conference on document analysis and recognition, ICDAR. IEEE Computer Society, pp 1332–1337
Lugon Moulin S, Weyermann C, Baechler S (2022) An efficient method to detect series of fraudulent identity documents based on digitised forensic data. Sci Justice 62(5):610–620 [Online]. Available: https://www.sciencedirect.com/science/article/pii/S1355030622001113
Talbot-Wright B, Baechler S, Morelato M, Ribaux O, Roux C (2016) Image processing of false identity documents for forensic intelligence. Forensic Sci Int 263:67–73 [Online]. Available: https://www.sciencedirect.com/science/article/pii/S0379073816301414
Martínez Tornés B, Boros E, Doucet A, Gomez-Krämer P, Ogier JM (2023) Detecting forged receipts with domain-specific ontology-based entities & relations. In: Fink GA, Jain R, Kise K, Zanibbi R (eds) Document analysis and recognition - ICDAR 2023. Cham, Springer Nature Switzerland, pp 184–199
Martínez Tornés B, Boros E, Doucet A, Gomez-Krämer P, Ogier JM (2023) Detecting forged receipts with domain-specific ontology-based entities & relations. In: Document analysis and recognition - ICDAR 2023: 17th international conference, San José, CA, USA, August 21-26, 2023, Proceedings, Part III. Berlin, Heidelberg: Springer-Verlag, pp 184–199. [Online]. Available: https://doi.org/10.1007/978-3-031-41682-8_12
Bertojo L, Néraud C, Puech W (2022) A very fast copy-move forgery detection method for 4k ultra hd images. Front Signal Process, vol 2. [Online]. Available: https://www.frontiersin.org/articles/10.3389/frsip.2022.906304
Al-Ghadi M, Gomez-Krämer P, Burie JC (2022) CheckScan: a reference hashing for identity document quality detection. In: Osten W, Nikolaev D, and Zhou J (Eds) \(14^{th}\) international conference on machine vision (ICMV 2021), vol 12084, International Society for Optics and Photonics. SPIE, pp 120840J. [Online]. Available: https://doi.org/10.1117/12.2623887
Bertrand R, Gomez-Krämer P, Terrades OR, Franco P, Ogier JM (2013) A system based on intrinsic features for fraudulent document detection. In: \(12^{th}\) international conference on document analysis and recognition, pp 106–110
Gomez-Krämer P, Rouis K, Diallo AO, Coustaty M (2023) Printed and scanned document authentication using robust layout descriptor matching. Multimed Tools Appl. [Online]. Available: https://doi.org/10.1007/s11042-023-17021-1
Li Z, Tang H, Peng Z, Qi GJ, Tang J (2023) Knowledge-guided semantic transfer network for few-shot image recognition. IEEE Transactions on Neural Networks and Learning Systems, pp 1–15
Tang H, Yuan C, Li Z, Tang J (2022) Learning attention-guided pyramidal features for few-shot fine-grained recognition. Pattern Recognit 130:108792. [Online]. Available: https://www.sciencedirect.com/science/article/pii/S0031320322002734
Tang H, Li Z, Peng Z, Tang J (2020) Blockmix: Meta regularization and self-calibrated inference for metric-based meta-learning. In: Proceedings of the \(28^{th}\) ACM international conference on multimedia, ser. MM ’20. New York, USA: Association for Computing Machinery, pp 610–618. [Online]. Available: https://doi.org/10.1145/3394171.3413884
Tang H, Liu J, Yan S, Yan R, Li, Tang J (2023) M3net: multi-view encoding, matching, and fusion for few-shot fine-grained action recognition. In: Proceedings of the \(31^{st}\) ACM international conference on multimedia, ser. MM ’23. New York, USA: Association for Computing Machinery, pp 1719–1728. [Online]. Available: https://doi.org/10.1145/3581783.3612221
Zha Z, Tang H, Sun Y, Tang J (2023) Boosting few-shot fine-grained recognition with background suppression and foreground alignment. IEEE Trans Circuits Syst Video Technol 33(8):3947–3961 [Online]. Available: https://doi.org/10.1109/TCSVT.2023.3236636
Akcay S, Atapour-Abarghouei A, Breckon TP (2018) Ganomaly: semi-supervised anomaly detection via adversarial training. Lect Notes Comput Sci (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics) LNCS, 11363:622–637
Wang Z, Bovik AC, Sheikh HR, Simoncelli EP (2004) Image quality assessment: from error visibility to structural similarity. IEEE Trans Image Process 13:600–612
Godard C, Aodha OM, Brostow GJ (2016) Unsupervised monocular depth estimation with left-right consistency. In: Proceedings - 30th IEEE conference on computer vision and pattern recognition, CVPR 2017, vol 2017-January. Institute of Electrical and Electronics Engineers Inc., pp 6602–6611
Bulatov K, Emelianova E, Tropin D, Skoryukina N, Chernyshova Y, Sheshkus A, Usilin S, Ming Z, Burie JC, Luqman MM, Arlazarov VV (2021) Midv-2020: a comprehensive benchmark dataset for identity document analysis. Comput Opt 46:252–270
Ouyang J, Coatrieux G, Shu H (2015) Robust hashing for image authentication using quaternion discrete fourier transform and log-polar transform. Digit Signal Process 41:98–109
Funding
This work has been financed by (le fonds unique interministériel) FUI IDECYS+ project (No.:DOS0098984/00)
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
The ID samples and the photos of individuals throughout this manuscript are sourced exclusively from the publicly available MIDV dataset.
Conflict of Interest
We have no conflict of interest to declare.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Al-Ghadi, M., Mondal, T., Ming, Z. et al. Identifying fraudulent identity documents by analyzing imprinted guilloche patterns. Multimed Tools Appl 83, 79145–79192 (2024). https://doi.org/10.1007/s11042-024-18611-3
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-024-18611-3