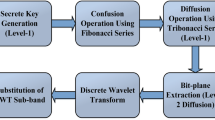
Abstract
In recent years, encryption algorithms have undergone rapid development, finding extensive applications across diverse industries. In the pursuit of enhancing the security of image encryption methodologies, this paper introduces a novel computational holographic encryption approach grounded in DNA coding and bit-plane decomposition. The encryption framework employs a Logistic-Sine chaotic mapping system characterized by a substantial key space to control encryption particulars. The plaintext image undergoes encryption through the input–output algorithm of computational holography. This algorithm shifts information from the spatial domain, represented by the greyscale map, to the frequency domain, concealing the distribution of pixel values. The incorporation of DNA coding and bit-plane transformations serves to intensify the chaos within the ciphertext image, thereby maximizing the efficacy of the encryption process. By integrating principles from biology and physical optics into encryption methodologies, this approach amalgamates diverse scientific domains. Simulation results and data analyses substantiate that the proposed encryption algorithm adeptly withstands various attacks, attesting to its security and reliability.









Similar content being viewed by others
Explore related subjects
Discover the latest articles and news from researchers in related subjects, suggested using machine learning.Data availability
Lena is available at http://www.lenna.org/. Baboon, peppers and goldhill are available at https://sipi.usc.edu/database/. The encryption and decryption algorithms proposed in the paper can be accessed in https://github.com/legend-liang/Holographic-encryption-algorithm-based-on-DNA-coding-and-bit-plane-decomposition.git.
Abbreviations
- Ambut:
-
Full Name
- DNA:
-
DeoxyriboNucleic Acid
- DES:
-
Data Encryption Standard
- RSA:
-
Rivest-Shamir-Adleman
- FFT:
-
Fast Fourier transform
- IFFT:
-
Inverse Fast Fourier transform
- GS:
-
Gerchberg-Saxton
- XOR:
-
Exclusive OR
- CPU:
-
Central Processing Unit
- NPCR:
-
Number of Pixels Changed Rate
- UACI:
-
Unified Average Change Intensity
- PSNR:
-
Peak Signal-to-Noise Ratios
- RGB:
-
Red-Green–Blue
References
Zhang X et al (2014) Compressing encrypted images with auxiliary information. IEEE Trans Multimed 16(5):1327–1336
Ke Y et al (2020) Fully homomorphic encryption encapsulated difference expansion for reversible data hiding in encrypted domain. IEEE Trans Circuits Syst Video Technol 30(8):2353–2365
Yu C et al (2021) Reversible data hiding with hierarchical embedding for encrypted images. IEEE Transact Circuits Syst Video Technol 32(2):451–466
Du Y, Yin Z, Zhang X (2020) High capacity lossless data hiding in JPEG bitstream based on general VLC mapping. IEEE Trans Dependable Secure Comput 19(2):1420–1433
Li S, Ma R, Zhang H (2019) Enhancing security for JPEG Image against mosaic attack using Inter-block shuffle encryption. IEEE Access 7:72696–72702
Wu Y, Dai X (2020) Encryption of accounting data using DES algorithm in computing environment. J Intell Fuzzy Syst 39(4):5085–5095
Shao Z, Gao Y (2015) Certificate-based verifiably encrypted RSA signatures. Trans Emerg Telecommun Technol 26(2):276–289
Li S et al (2006) Chaos-based encryption for digital image and video. In: Furht B, Kirovski D (eds) Multimedia encryption and authentication techniques and applications. Auerbach Publications, pp 129–163. https://doi.org/10.1201/9781420013450-4
Mazloom S, Eftekhari-Moghadam AM (2009) Color image encryption based on coupled nonlinear chaotic map. Chaos Solitons Fractals 42(3):1745–1754
Nithya R, Dhanasekaran D (2022) Novel dominant color subband image encryption in visual sensor network for smart military surveillance system. Traitement Du Signal 39(3):951–960. https://doi.org/10.18280/ts.390322
Alslman Y et al (2022) Hybrid encryption scheme for medical imaging using autoencoder and advanced encryption standard. Electronics 11(23):3967
Deb S, Biswas B, Bhuyan B (2019) Secure image encryption scheme using high efficiency word-oriented feedback shift register over finite field. Multimed Tools Appl 78:34901–34925
Zope-Chaudhari S, Venkatachalam P, Buddhiraju KM (2015) Secure dissemination and protection of multispectral images using crypto-watermarking. IEEE J Select Top Appl Earth Obs Remote Sensing 8(11):5388–5394
Song C, Qiao Y (2015) A novel image encryption algorithm based on DNA encoding and spatiotemporal chaos. Entropy 17(10):6954–6968
Matthews R (1989) On the derivation of a “chaotic” encryption algorithm. Cryptologia 13(1):29–42
Chai X et al (2020) Color image compression and encryption scheme based on compressive sensing and double random encryption strategy. Signal Process 176:107684
Chen C, Sun K, He S (2020) An improved image encryption algorithm with finite computing precision. Signal Process 168:107340
Hou W et al (2020) A novel image-encryption scheme based on a non-linear cross-coupled hyperchaotic system with the dynamic correlation of plaintext pixels. Entropy 22(7):779
Çelik H, Doğan N (2023) A hybrid color image encryption method based on extended logistic map. Multimed Tools Appl 83(5):12627–12650. https://doi.org/10.1007/s11042-023-16215-x
Iqbal N et al (2023) An efficient image cipher based on the 1D scrambled image and 2D logistic chaotic map. Multimed Tools Appl 82(26):40345–40373. https://doi.org/10.1007/s11042-023-15037-1
Hazer A, Yıldırım R (2021) A review of single and multiple optical image encryption techniques. J Opt 23(11):113501
Liu S, Guo C, Sheridan JT (2014) A review of optical image encryption techniques. Opt Laser Technol 57:327–342
Chen W, Javidi B, Chen X (2014) Advances in optical security systems. Adv Opt Photon 6(2):120–155
Refregier P, Javidi B (1995) Optical image encryption based on input plane and Fourier plane random encoding. Opt Lett 20(7):767–769
Qin W, Peng X (2010) Asymmetric cryptosystem based on phase-truncated Fourier transforms. Opt Lett 35(2):118–120
Clemente P et al (2010) Optical encryption based on computational ghost imaging. Opt Lett 35(14):2391–2393
Tsang PWM (2017) Single-random-phase holographic encryption of images. Opt Lasers Eng 89:22–28
Piao M-L et al (2019) Robust multidepth object encryption based on a computer-generated hologram with a cascaded structure. Appl Opt 58(36):9921–9930
Kong D et al (2017) Image encryption based on interleaved computer-generated holograms. IEEE Trans Indust Inform 14(2):673–678
Wang X, Zhao D (2012) Fully phase multiple-image encryption based on superposition principle and the digital holographic technique. Opt Commun 285(21–22):4280–4284
Abookasis D, Rosen J (2006) Three types of computer-generated hologram synthesized from multiple angular viewpoints of a three-dimensional scene. Appl Opt 45(25):6533–6538
Tricoles G (1987) Computer generated holograms: an historical review. Appl Opt 26(20):4351–4360
Zhou P et al (2019) Dynamic compensatory Gerchberg-Saxton algorithm for multiple-plane reconstruction in holographic displays. Opt Express 27(6):8958–8967
Yifat Y et al (2014) Highly efficient and broadband wide-angle holography using patch-dipole nanoantenna reflectarrays. Nano Lett 14(5):2485–2490
Sun S et al (2012) Gradient-index meta-surfaces as a bridge linking propagating waves and surface waves. Nat Mater 11(5):426–431
Liu L et al (2014) Broadband metasurfaces with simultaneous control of phase and amplitude. Adv Mater 26(29):5031–5036
Chong KE et al (2016) Efficient polarization-insensitive complex wavefront control using Huygens’ metasurfaces based on dielectric resonant meta-atoms. Acs Photon 3(4):514–519
Zhao W et al (2016) Dielectric Huygens’ metasurface for high-efficiency hologram operating in transmission mode. Sci Reports 6(1):30613
Chen WT et al (2014) High-efficiency broadband meta-hologram with polarization-controlled dual images. Nano Lett 14(1):225–230
Montelongo Y et al (2014) Polarization switchable diffraction based on subwavelength plasmonic nanoantennas. Nano Lett 14(1):294–298
Zhu M, Wang C (2020) A novel parallel chaotic system with greatly improved Lyapunov exponent and chaotic range. Int J Mod Phys B 34(07):2050048
Qi G, Chen G (2015) A spherical chaotic system. Nonlinear Dyn 81:1381–1392
Li Q, Chen L (2023) An image encryption algorithm based on 6-dimensional hyper chaotic system and DNA encoding. Multimed Tools Appl 83(2):5351–5368. https://doi.org/10.1007/s11042-023-15550-3
Wang Y et al (2015) Security analysis on a color image encryption based on DNA encoding and chaos map. Comput Electr Eng 46:433–446
Zhou Y et al (2012) Image encryption using P-Fibonacci transform and decomposition. Opt Commun 285(5):594–608
Alvarez G, Li S (2006) Some basic cryptographic requirements for chaos-based cryptosystems. Int J Bifurcation Chaos 16(08):2129–2151
Li J et al (2022) Holographic encryption algorithm based on bit-plane decomposition and hyperchaotic Lorenz system. Opt Laser Technol 152:108127
Wan Y, Wang S, Baoxiang Du (2023) A bit plane image encryption algorithm based on compound chaos. Multimed Tools Appl 82(14):22103–22121
Musanna F, Kumar S (2020) Image encryption using quantum 3-D Baker map and generalized gray code coupled with fractional Chen’s chaotic system. Quantum Inf Process 19:1–31
Tian J et al (2021) A novel image encryption algorithm using PWLCM map-based CML chaotic system and dynamic DNA encryption. Multimed Tools Appl 80(21–23):32841–32861
Acknowledgements
This research is supported by the National Natural Science Foundation of China under Grants No. 62175039.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Competing interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix
Appendix
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Liang, Z., Chen, L., Chen, K. et al. Holographic encryption algorithm based on DNA coding and bit-plane decomposition. Multimed Tools Appl 83, 87385–87413 (2024). https://doi.org/10.1007/s11042-024-18838-0
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-024-18838-0