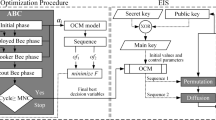
Abstract
Chaotic-based image encryption approaches have attracted great attention in the field of information security. The properties of chaotic maps such as randomness and sensitivity have given new ways to develop efficient encryption approaches. But chaotic maps require initial parameters to develop random sequences. The selection of these parameters is a tedious task. To obtain the optimal initial parameters, evolutionary optimization approaches have been utilized in image encryption. Therefore, in this paper, a hyper-chaotic map is optimized using a multiobjective evolutionary optimization approach. A dual local search based multiobjective optimization (DLS-MO) is used to obtain the optimal parameters of a hyper-chaotic map and encryption factors. Then, using optimal parameters, a hyper-chaotic map develops the secret keys. These secret keys are then used to perform permutation and diffusion on a plain image to develop the encrypted image. To perform encryption, permutation–permutation–diffusion–diffusion architecture is adopted for better confusion and diffusion. Experimental results show that the proposed approach provides better performance in comparison to existing competitive approaches.









Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.References
Abbasi, A. A., Mazinani, M., & Hosseini, R. (2020). Evolutionary-based image encryption using biomolecules operators and non-coupled map lattice. Optik, 219, 164949.
Akhavan, A., Samsudin, A., & Akhshani, A. (2017). Cryptanalysis of an image encryption algorithm based on DNA encoding. Optics and Laser Technology, 95, 94–99.
Basavegowda, H. S., & Dagnew, G. (2020). Deep learning approach for microarray cancer data classification. CAAI Transactions on Intelligence Technology, 5(1), 22–33.
Beume, N., Naujoks, B., & Emmerich, M. (2007). SMS-EMOA: Multiobjective selection based on dominated hypervolume. European Journal of Operational Research, 181(3), 1653–1669.
Çavuşoğlu, Ü., Kaçar, S., Pehlivan, I., & Zengin, A. (2017). Secure image encryption algorithm design using a novel chaos based S-Box. Chaos, Solitons and Fractals, 95, 92–101.
Chen, L., Ma, B., Zhao, X., & Wang, S. (2017). Differential cryptanalysis of a novel image encryption algorithm based on chaos and line map. Nonlinear Dynamics, 87(3), 1797–1807.
Chen, E., Min, L., & Chen, G. (2017). Discrete chaotic systems with one-line equilibria and their application to image encryption. International Journal of Bifurcation and Chaos, 27(03), 1750046.
Enayatifar, R., Abdullah, A. H., & Isnin, I. F. (2014). Chaos-based image encryption using a hybrid genetic algorithm and a DNA sequence. Optics and Lasers in Engineering, 56, 83–93.
Ghosh, S., Shivakumara, P., Roy, P., Pal, U., & Lu, T. (2020). Graphology based handwritten character analysis for human behaviour identification. CAAI Transactions on Intelligence Technology, 5(1), 55–65.
Gupta, A., Singh, D., & Kaur, M. (2020). An efficient image encryption using non-dominated sorting genetic algorithm-III based 4-D chaotic maps. Journal of Ambient Intelligence and Humanized Computing, 11(3), 1309–1324.
Gupta, B., Tiwari, M., & Lamba, S. S. (2019). Visibility improvement and mass segmentation of mammogram images using quantile separated histogram equalisation with local contrast enhancement. CAAI Transactions on Intelligence Technology, 4(2), 73–79.
Hansen, N., Arnold, D. V., & Auger, A. (2015). Evolution strategies. In Springer handbook of computational intelligence (pp. 871–898). Springer.
Hong, W., Tang, K., Zhou, A., Ishibuchi, H., & Yao, X. (2018). A scalable indicator-based evolutionary algorithm for large-scale multiobjective optimization. IEEE Transactions on Evolutionary Computation, 23(3), 525–537.
Huang, Z.-J., Cheng, S., Gong, L.-H., & Zhou, N.-R. (2020). Nonlinear optical multi-image encryption scheme with two-dimensional linear canonical transform. Optics and Lasers in Engineering, 124, 105821.
Jaiswal, A., Gianchandani, N., Singh, D., Kumar, V., & Kaur, M. (2020). Classification of the COVID-19 infected patients using DenseNet201 based deep transfer learning. Journal of Biomolecular Structure and Dynamics. https://doi.org/10.1080/07391102.2020.1788642.
Kaur, M., Gianey, H. K., Singh, D., & Sabharwal, M. (2019). Multi-objective differential evolution based random forest for e-health applications. Modern Physics Letters B, 33(05), 1950022.
Kaur, M., & Kumar, V. (2018). Beta chaotic map based image encryption using genetic algorithm. International Journal of Bifurcation and Chaos, 28(11), 1850132.
Kaur, M., & Kumar, V. (2018). Colour image encryption technique using differential evolution in non-subsampled contourlet transform domain. IET Image Processing, 12(7), 1273–1283.
Kaur, M., & Kumar, V. (2018). Adaptive differential evolution-based lorenz chaotic system for image encryption. Arabian Journal for Science and Engineering, 43(12), 8127–8144.
Kaur, M., & Kumar, V. (2018). Fourier-mellin moment-based intertwining map for image encryption. Modern Physics Letters B, 32(09), 1850115.
Kaur, M., & Kumar, V. (2018). Parallel non-dominated sorting genetic algorithm-II-based image encryption technique. The Imaging Science Journal, 66(8), 453–462.
Kaur, M., Kumar, V., & Li, L. (2019). Color image encryption approach based on memetic differential evolution. Neural Computing and Applications, 31(11), 7975–7987.
Kaur, M., & Singh, D. (2019). Fusion of medical images using deep belief networks. Cluster Computing,. https://doi.org/10.1007/s10586-019-02999-x.
Kaur, M., Singh, D., Kumar, V., & Sun, K. (2020). Color image dehazing using gradient channel prior and guided L0 filter. Information Sciences, 521, 326–342. https://doi.org/10.1016/j.ins.2020.02.048. http://www.sciencedirect.com/science/article/pii/S0020025520301316.
Kaur, M., Singh, D., & Singh Uppal, R. (2020). Parallel strength pareto evolutionary algorithm-II based image encryption. IET Image Processing, 14(6), 1015–1026.
Kaur, M., Singh, D., Sun, K., & Rawat, U. (2020). Color image encryption using non-dominated sorting genetic algorithm with local chaotic search based 5D chaotic map. Future Generation Computer Systems, 107, 333–350.
Kaur, M., Singh, D., & Uppal, R. S. (2019). Parallel strength pareto evolutionary algorithm-II based image encryption. IET Image Processing, 14(6), 1015–1026.
Khan, M., & Asghar, Z. (2018). A novel construction of substitution box for image encryption applications with gingerbreadman chaotic map and \(S_{8}\) permutation. Neural Computing and Applications, 29(4), 993–999.
Krishna, G. J., Ravi, V., & Bhattu, S. N. (2018). Key generation for plain text in stream cipher via bi-objective evolutionary computing. Applied Soft Computing, 70, 301–317.
Kumar, M., Iqbal, A., & Kumar, P. (2016). A new RGB image encryption algorithm based on DNA encoding and elliptic curve Diffie–Hellman cryptography. Signal Processing, 125, 187–202.
Li, C. (2016). Cracking a hierarchical chaotic image encryption algorithm based on permutation. Signal Processing, 118, 203–210.
Li, C., Luo, G., Qin, K., & Li, C. (2017). An image encryption scheme based on chaotic tent map. Nonlinear Dynamics, 87(1), 127–133.
Liao, X., Hahsmi, M. A., Haider, R., et al. (2018). An efficient mixed inter-intra pixels substitution at 2bits-level for image encryption technique using DNA and chaos. Optik-International Journal for Light and Electron Optics, 153, 117–134.
Liu, H., Kadir, A., & Sun, X. (2017). Chaos-based fast colour image encryption scheme with true random number keys from environmental noise. IET Image Processing, 11(5), 324–332.
Liu, H., Wen, F., & Kadir, A. (2019). Construction of a new 2D Chebyshev-Sine map and its application to color image encryption. Multimedia Tools and Applications, 78(12), 15997–16010.
Mahmud, M., Lee, M., Choi, J.-Y., et al. (2020). Evolutionary-based image encryption using RNA codons truth table. Optics and Laser Technology, 121, 105818.
Matthews, R. (1989). On the derivation of a “chaotic” encryption algorithm. Cryptologia, 13(1), 29–42.
Nematzadeh, H., Enayatifar, R., Motameni, H., Guimarães, F. G., & Coelho, V. N. (2018). Medical image encryption using a hybrid model of modified genetic algorithm and coupled map lattices. Optics and Lasers in Engineering, 110, 24–32.
Noshadian, S., Ebrahimzade, A., & Kazemitabar, S. J. (2018). Optimizing chaos based image encryption. Multimedia Tools and Applications, 77(19), 25569–25590.
Osterland, S., & Weber, J. (2019). Analytical analysis of single-stage pressure relief valves. International Journal of Hydromechatronics, 2(1), 32–53.
Pannu, H. S., Singh, D., & Malhi, A. K. (2018). Improved particle swarm optimization based adaptive neuro-fuzzy inference system for benzene detection. CLEAN-Soil, Air, Water, 46(5), 1700162.
Pannu, H. S., Singh, D., & Malhi, A. K. (2019). Multi-objective particle swarm optimization-based adaptive neuro-fuzzy inference system for benzene monitoring. Neural Computing and Applications, 31, 2195–2205.
Pathak, Y., Shukla, P. K., Tiwari, A., Stalin, S., Singh, S., & Shukla, P. K. (2020). Deep transfer learning based classification model for COVID-19 disease. IRBM,. https://doi.org/10.1016/j.irbm.2020.05.003.
Shankar, K., & Eswaran, P. (2016). An efficient image encryption technique based on optimized key generation in ECC using genetic algorithm. In Artificial intelligence and evolutionary computations in engineering systems (pp. 705–714). Springer.
Shukla, P. K., Shukla, P. K., Sharma, P., Rawat, P., Samar, J., Moriwal, R., et al. (2020). Efficient prediction of drug–drug interaction using deep learning models. IET Systems Biology,. https://doi.org/10.1049/iet-syb.2019.0116.
Singh, D., Kaur, M., & Singh, H. (2018). Remote sensing image fusion using fuzzy logic and gyrator transform. Remote Sensing Letters, 9(10), 942–951.
Singh, D., & Kumar, V. (2018). Dehazing of outdoor images using notch based integral guided filter. Multimedia Tools and Applications, 77(20), 27363–27386.
Singh, D., & Kumar, V. (2019). A comprehensive review of computational dehazing techniques. Archives of Computational Methods in Engineering, 26(5), 1395–1413.
Singh, D., & Kumar, V. (2019). Single image defogging by gain gradient image filter. Science China Information Sciences, 62(7), 79101.
Singh, D., Kumar, V., & Kaur, M. (2019). Single image dehazing using gradient channel prior. Applied Intelligence, 49(12), 4276–4293.
Singh, D., Kumar, V., & Kaur, M. (2019). Image dehazing using window-based integrated means filter. Multimedia Tools and Applications,. https://doi.org/10.1007/s11042-019-08286-6.
Singh, D., Kumar, V., & Vaishali, M. K. (2020). Classification of COVID-19 patients from chest CT images using multi-objective differential evolution-based convolutional neural networks. European Journal of Clinical Microbiology and Infectious Diseases, 39, 1–11. https://doi.org/10.1007/s10096-020-03901-z.
Suri, S., & Vijay, R. (2020). A Pareto-optimal evolutionary approach of image encryption using coupled map lattice and DNA. Neural Computing and Applications, 32, 11859–11873.
Usama, M., Khan, M. K., Alghathbar, K., & Lee, C. (2010). Chaos-based secure satellite imagery cryptosystem. Computers and Mathematics with Applications, 60(2), 326–337.
Wang, X., Yin, Y. L., & Yu, H. (2005). Finding collisions in the full SHA-1. In Annual international cryptology conference (pp. 17–36). Springer.
Wang, R., Yu, H., Wang, G., Zhang, G., & Wang, W. (2019). Study on the dynamic and static characteristics of gas static thrust bearing with micro-hole restrictors. International Journal of Hydromechatronics, 2(3), 189–202.
Wang, X.-Y., Zhang, Y.-Q., & Bao, X.-M. (2015). A novel chaotic image encryption scheme using DNA sequence operations. Optics and Lasers in Engineering, 73, 53–61.
Wen, W. (2016). Security analysis of a color image encryption scheme based on skew tent map and hyper chaotic system of 6th-order CNN against chosen-plaintext attack. Multimedia Tools and Applications, 75(6), 3553–3560.
While, L., Hingston, P., Barone, L., & Huband, S. (2006). A faster algorithm for calculating hypervolume. IEEE Transactions on Evolutionary Computation, 10(1), 29–38.
Wiens, T. (2019). Engine speed reduction for hydraulic machinery using predictive algorithms. International Journal of Hydromechatronics, 2(1), 16–31.
Wu, J., Liao, X., & Yang, B. (2018). Cryptanalysis and enhancements of image encryption based on three-dimensional bit matrix permutation. Signal Processing, 142, 292–300.
Wu, Y., Noonan, J. P., Agaian, S., et al. (2011). NPCR and UACI randomness tests for image encryption. Cyber Journals: Multidisciplinary Journals in Science and Technology Journal of Selected Areas in Telecommunications (JSAT), 1(2), 31–38.
Wu, Y., Zhou, Y., Saveriades, G., Agaian, S., Noonan, J. P., & Natarajan, P. (2013). Local Shannon entropy measure with statistical tests for image randomness. Information Sciences, 222, 323–342.
Yang, P., Tang, K., & Yao, X. (2017). Turning high-dimensional optimization into computationally expensive optimization. IEEE Transactions on Evolutionary Computation, 22(1), 143–156.
Zhang, X., Fan, X., Wang, J., & Zhao, Z. (2016). A chaos-based image encryption scheme using 2D rectangular transform and dependent substitution. Multimedia Tools and Applications, 75(4), 1745–1763.
Zhang, Y.-Q., & Wang, X.-Y. (2014). Analysis and improvement of a chaos-based symmetric image encryption scheme using a bit-level permutation. Nonlinear Dynamics, 77(3), 687–698.
Zhang, W., Yu, H., Zhao, Y.-L., & Zhu, Z.-L. (2016). Image encryption based on three-dimensional bit matrix permutation. Signal Processing, 118, 36–50.
Zhang, X., Zhu, G., & Ma, S. (2012). Remote-sensing image encryption in hybrid domains. Optics Communications, 285(7), 1736–1743.
Zhou, G., Zhang, D., Liu, Y., Yuan, Y., & Liu, Q. (2015). A novel image encryption algorithm based on chaos and line map. Neurocomputing, 169, 150–157.
Zhu, Z.-L., Zhang, W., Wong, K.-W., & Yu, H. (2011). A chaos-based symmetric image encryption scheme using a bit-level permutation. Information Sciences, 181(6), 1171–1186.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Kaur, M., Singh, D. Multiobjective evolutionary optimization techniques based hyperchaotic map and their applications in image encryption. Multidim Syst Sign Process 32, 281–301 (2021). https://doi.org/10.1007/s11045-020-00739-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11045-020-00739-8