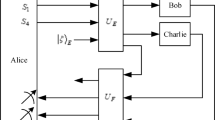
Abstract
The general theory of three-party QSS protocols with the noisy quantum channels is discussed. When the particles are transmitted through the noisy quantum channels, the initial pure three-qubit tripartite entangled states would be changed into mixed states. We analyze the security of QSS protocols with the different kinds of three-qubit tripartite entangled states under phase-damping channels and figure out, for different kinds of initial states, the successful probabilities that Alice’s secret can be recovered by legal agents are different. Comparing with one recent QSS protocol based on GHZ states, our scheme is secure, and has a little smaller key rate than that of the recent protocol.


Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.References
Bennett, C.H., Brassard, G.: Quantum Cryptography: Public Key Distribution and Coin Tossing, vol. 175, p. 175. Bangalore, India (1984)
Ekert, A.K.: Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 67, 661 (1991)
Bennett, C.H., Brassard, G., Mermin, N.D.: Quantum cryptography without Bell’s theorem. Phys. Rev. Lett. 68, 557 (1992)
Braunstein, S.L., Pirandola, S.: Side-channel-free quantum key distribution. Phys. Rev. Lett. 108, 130502 (2012)
Lo, H.-K., Curty, M., Qi, B.: Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 108, 130503 (2012)
Lance, A.M., Symul, T., Bowen, W.P., Sanders, B.C., Koy, Lam, P.K.: Tripartite quantum state sharing. Phys. Rev. Lett. 92, 177903 (2004)
Gordon, G., Rigolin, G.: Generalized quantum-state sharing. Phys. Rev. A 73, 062316 (2006)
Zhang, Z.-J.: Robust multiparty quantum secret key sharing over two collective-noise channels. Phys. A: Stat. Mech. Its Appl. 361, 233 (2006)
Dür, W., Vidal, G., Cirac, J.I.: Three qubits can be entangled in two inequivalent ways. Phys. Rev. A 62, 062314 (2000)
Hillery, M., Buzek, V., Berthiaume, A.: Quantum secret sharing. Phys. Rev. A 59, 1829 (1999)
Adhikari, S., Chakrabarty, I., Agrawal, P.: Probabilistic secret sharing through noisy quantum channel. Quant. Inf. Comp. 12, 253 (2012)
Liu, L.-L., Tsai, C.-W., Hwang, T.: Quantum secret sharing using symmetric W state. Int. J. Theor. Phys. 51, 2291 (2012)
Demkowicz-Dobrzański, R., De Sen, A., Sen, U., Lewenstein, M.: Phys. Rev. A 80, 012311 (2009)
Maitra, S., Nandi, K.: Cryptanalysis of a secret sharing scheme that uses quantum resources. Quant. Inf. Comp. 13, 178 (2013)
Gisin, N., Ribordy, G., Tittel, W., Zbinden, H.: Quantum cryptography. Rev. Mod. Phys. 74, 145 (2002)
Wójcik, A.: Eavesdropping on the “ping-pong” quantum communication protocol. Phys. Rev. Lett. 90, 157901 (2003)
Qi, B., Fung, C.-H.F., Lo, H.-K., Ma, X.: Time-shift attack in practical quantum cryptosystems. Quant. Inf. Comp. 7, 073 (2007)
Acknowledgments
This work is supported by NSFC (Grant Nos. 61272057, 61202434, 61170270, 61100203, 61003286, 61121061, 61103210), NCET (Grant No. NCET-10-0260), Beijing Natural Science Foundation (Grant Nos. 4112040, 4122054), the Fundamental Research Funds for the Central Universities (Grant No. 2012RC0612, 2011YB01).
Author information
Authors and Affiliations
Corresponding author
Appendix
Appendix
By the coincidence between the state of second particle and that of the third particle, the states shown in Eq. (2) can be easily divided into four groups, \(\{\rho ^{\prime }_{II}(\rho ^{\prime }_{ZZ}), \rho ^{\prime }_{IZ}(\rho ^{\prime }_{ZI})\}, \{\rho ^{\prime }_{IX}(\rho ^{\prime }_{ZY}), \rho ^{\prime }_{IY}(\rho ^{\prime }_{ZX})\}, \{\rho ^{\prime }_{XI}(\rho ^{\prime }_{YZ}), \rho ^{\prime }_{XZ}(\rho ^{\prime }_{YI})\}\), and \(\{\rho ^{\prime }_{XX}(\rho ^{\prime }_{YY}), \rho ^{\prime }_{XY}(\rho ^{\prime }_{YX})\}\). The two states in each group can be discriminated in same way. Now we give the discrimination between
and
which are appeared with the prior probabilities \(1/2\) and \(1/2\), respectively. From the forms of \(\rho ^{\prime }_{II}\) and \(\rho ^{\prime }_{IZ}\), we know that the support set of \(\rho ^{\prime }_{II}\) and that of \(\rho ^{\prime }_{IZ}\) are same, so there is no unambiguous discrimination between these two mixed states. Thus the maximum confidence discrimination is considered.
Suppose the positive detection operators are \(\Pi _{II}, \Pi _{IZ}\) and \(\Pi _2=I-\Pi _{II}-\Pi _{IZ}\), where they satisfy that \(\Pi _{II}, \Pi _{IZ}, \Pi _2\ge 0\). The failure probability is \(Q=1-tr(\rho \Pi _{II})-tr(\rho \Pi _{IZ})\), where the density operator \(\rho \) is equal to \(1/2\rho ^{\prime }_{II}+1/2\rho ^{\prime }_{IZ}\). The confidences are also introduced by \(C_j=\frac{tr(\rho ^{\prime }_j\Pi _j)}{2\times tr(\rho \Pi _j)}\) with \(j=II,IZ\). We define the positive operators \({\tilde{\rho }}_j=\frac{1}{2}\rho ^{-1/2}\rho ^{\prime }_j\rho ^{-1/2}\), so there exist
and the spectral decompositions are
When \(\tilde{\Pi }_j=\frac{\rho ^{1/2}\Pi _j\rho ^{1/2}}{tr(\rho \Pi _j)}\) for \(j=II, IZ\), we have \(C_j=tr({\tilde{\rho }}_j\tilde{\Pi }_j)\). In order to maximizing \(C_j\), the operators \(\tilde{\Pi }_j\) should be diagonalized under the basis \(\{|v_0\rangle \langle v_0|=(|000\rangle +|111\rangle )(\langle 000|+\langle 111|)/2, |v_1\rangle \langle v_1|=(|000\rangle +|111\rangle )(\langle 000|+\langle 111|)/2\}\). Because of \(tr(\tilde{\Pi }_j)=1\), the maximum confidences take the form \(C_{II}^{max}=C_{IZ}^{max}=[1+(1-p)^4]/2\), which are the largest eigenvalues of the operators \({\tilde{\rho }}_{II}\) and \({\tilde{\rho }}_{IZ}\). According to the values of \(\tilde{\Pi }_j\), there have \(\Pi _{II}=c_{II}\rho ^{-1/2}|v_0\rangle \langle v_0|\rho ^{-1/2}=a_{II}|w_0\rangle \langle w_0|\) and \(\Pi _{IZ}=c_{IZ}\rho ^{-1/2}|v_1\rangle \langle v_1|\rho ^{-1/2}=a_{IZ}|w_1\rangle \langle w_1|\), where the normalized states \(|w_j\rangle =\frac{\rho ^{-1/2}|v_j\rangle }{\sqrt{\langle v_j|\rho ^{-1}|v_j\rangle }}\) for \(j=0, 1\) are
Thus the minimum failure probability \(Q=tr(\rho \Pi _2)=0\) is reached, when \(a_{II}=a_{IZ}=1\). So the space spanned by the measurement operators \(\Pi _{II}\) and \(\Pi _{IZ}\) is same with the space spanned by \(\rho ^{\prime }_{II}\) and \(\rho ^{\prime }_{IZ}\). At the same time, the optimal measurement operators are \(\Pi _{II}=(\frac{1}{\sqrt{2}}|000\rangle +\frac{1}{\sqrt{2}}|111\rangle )(\frac{1}{\sqrt{2}}\langle 000|+\frac{1}{\sqrt{2}}\langle 111|)\) and \(\Pi _{IZ}=(\frac{1}{\sqrt{2}}|000\rangle -\frac{1}{\sqrt{2}}|111\rangle )(\frac{1}{\sqrt{2}}\langle 000|-\frac{1}{\sqrt{2}}\langle 111|)\). The error rate \(P=[tr(\rho ^{\prime }_{II}\Pi _{IZ})+tr(\rho ^{\prime }_{IZ}\Pi _{II})]/2=[1-(1-p)^4]/2\) is related with the parameter of channel \(p\). Until now, we give the discrimination of the \(\rho ^{\prime }_{II}\) and \(\rho ^{\prime }_{IZ}\) with maximum confidence and the minimum failure probability. The discrimination of other group states in Eq. (2) is in the same way.
Rights and permissions
About this article
Cite this article
Song, TT., Wen, QY., Qin, SJ. et al. The general theory of three-party quantum secret sharing protocols over phase-damping channels. Quantum Inf Process 12, 3291–3304 (2013). https://doi.org/10.1007/s11128-013-0600-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11128-013-0600-2