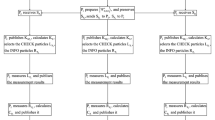
Abstract
This article proposes the first multi-party quantum private comparison protocol with an almost-dishonest third party, where many participants can compare their secrets in either ascending or descending order without revealing any secret information to anyone. In order to do that, the participants need not to pre-share any secret key between them. As a consequence, the proposed scheme can be enforced in several environments such as multi-party ranking and multi-data ranking protocol.

Similar content being viewed by others
References
Bennett, C.H., Brassard, G.: Quantum cryptography: public key distribution and coin tossing. In: Proceedings of the IEEE International Conference on Computers, Systems and Signal Processing, Bangalore, pp. 175–179 (1984)
Deng, F.G., Long, G.L., Liu, X.S.: Two-step quantum direct communication protocol using the Einstein-Podolsky-Rosen pair block. Phys. Rev. A 68, 042317 (2003)
Yang, C.-W., Kao, S.-H., Hwang, T.: Comment on “Efficient and feasible quantum private comparison of equality against the collective amplitude damping noise”. Quantum Inf. Process. 12, 2871–2875 (2013)
Yang, Y.-G., Xia, J., Jia, X., Zhang, H.: Comment on quantum private comparison protocols with a semi-honest third party. Quantum Inf. Process. 12, 877–885 (2013)
Zhang, W.-W., Zhang, K.-J.: Cryptanalysis and improvement of the quantum private comparison protocol with semi-honest third party. Quantum Inf. Process. 12, 1981–1990 (2013)
Wang, C., Xu, G., Yang, Y.-X.: Cryptanalysis and improvements for the quantum private comparison protocol using EPR pairs. Int. J. Quantum Inf. 11, 1350039 (2013)
Liu, X.-T., Zhao, J.-J., Wang, J., Tang, C.-J.: Cryptanalysis of the secure quantum private comparison protocol. Phys. Scr. 87, 065004 (2013)
Chen, X.-B., Su, Y., Niu, X.-X., Yang, Y.-X.: Efficient and feasible quantum private comparison of equality against the collective amplitude damping noise. Quantum Inf. Process. 13, 101–112 (2012)
Chen, X.-B., Xu, G., Niu, X.-X., Wen, Q.-Y., Yang, Y.-X.: An efficient protocol for the private comparison of equal information based on the triplet entangled state and single-particle measurement. Opt. Commun. 283, 1561–1565 (2010)
Liu, W., Wang, Y.-B., Jiang, Z.-T.: An efficient protocol for the quantum private comparison of equality with W state. Opt. Commun. 284, 3160–3163 (2011)
Liu, B., Gao, F., Jia, H.-Y., Huang, W., Zhang, W.-W., Wen, Q.-Y.: Efficient quantum private comparison employing single photons and collective detection. Quantum Inf. Process. 12, 887–897 (2012)
Yang, Y.-G., Wen, Q.-Y.: An efficient two-party quantum private comparison protocol with decoy photons and two-photon entanglement. J. Phys. A Math. Theor. 42, 055305 (2009)
Li, Y.-B., Wang, T.-Y., Chen, H.-Y., Li, M.-D., Yang, Y.-T.: Fault-tolerate quantum private comparison based on GHZ states and ECC. Int. J. Theor. Phys. 52, 2818–2825 (2013)
Li, Y.B., Wen, Q.Y., Gao, F., Jia, H.Y., Sun, Y.: Information leak in Liu et al’.s quantum private comparison and a new protocol. Eur. Phys. J. D 66, 110 (2012)
Tseng, H.-Y., Lin, J., Hwang, T.: New quantum private comparison protocol using EPR pairs. Quantum Inf. Process. 11, 373–384 (2011)
Yang, Y.-G., Xia, J., Jia, X.I.N., Shi, L.E.I., Zhang, H.U.A.: New quantum private comparison protocol without entanglement. Int. J. Quantum Inf. 10, 1250065 (2012)
Liu, W., Wang, Y.-B., Jiang, Z.-T., Cao, Y.-Z.: A protocol for the quantum private comparison of equality with \(\upchi \)-type state. Int. J. Theor. Phys. 51, 69–77 (2011)
Li, Y.-B., Qin, S.-J., Yuan, Z., Huang, W., Sun, Y.: Quantum private comparison against decoherence noise. Quantum Inf. Process. 12, 2191–2205 (2012)
Liu, W., Wang, Y.-B.: Quantum private comparison based on GHZ entangled states. Int. J. Theor. Phys. 51, 3596–3604 (2012)
Zi, W., Guo, F., Luo, Y., Cao, S., Wen, Q.: Quantum private comparison protocol with the random rotation. Int. J. Theor. Phys. 52, 3212–3219 (2013)
Jia, H.-Y., Wen, Q.-Y., Song, T.-T., Gao, F.: Quantum protocol for millionaire problem. Opt. Commun. 284, 545–549 (2011)
Yao, A.C.C.: Protocols for secure computations. In: 23rd Annual Symposium on Foundations of Computer Science, 1982. SFCS ’08, pp. 160–164 (1982)
Chang, Y.J., Tsai, C.W., Hwang, T.: Multi-user private comparison protocol using GHZ class states. Quantum Inf. Process. 12, 1077–1088 (2013)
Zhang, W.-W., Li, D., Zhang, K.-J., Zuo, H.-J.: A quantum protocol for millionaire problem with Bell states. Quantum Inf. Process. 12, 2241–2249 (2012)
Yu, C.-H., Guo, G.-D., Lin, S.: Quantum private comparison with \(d\)-level single-particle states. Phys. Scr. 88, 065013 (2013)
Lin, S., Sun, Y., Liu, X.-F., Yao, Z.-Q.: Quantum private comparison protocol with \(d\)-dimensional Bell states. Quantum Inf. Process. 12, 559–568 (2012)
Guo, F., Gao, F., Qin, S., Zhang, J., Wen, Q.: Quantum private comparison protocol based on entanglement swapping of \(d\)-level Bell states. Quantum Inf. Process. 12, 2793–2802 (2013)
Wang, Q.L., Sun, H.X., Huang, W.: Multi-party quantum private comparison protocol with n-level entangled states. Quantum Inf. Process. 13, 2370–2389 (2014)
Luo, Q.B., Yang, G.W., She, K., Niu, W.N., Wang, Y.Q.: Multi-party quantum private comparison protocol based on \(d\)-dimensional entangled states. Quantum Inf. Process. 13, 2343–2352 (2014)
Gao, F., Guo, F.-Z., Wen, Q.-Y., Zhu, F.-C.: Comment on “Experimental demonstration of a quantum protocol for byzantine agreement and liar detection”. Phys. Rev. Lett. 101, 208901 (2008)
Gao, F., Lin, S., Wen, Q.-Y., Zhu, F.-C.: A special eavesdropping on one-sender versus N-receiver QSDC protocol. Chin. Phys. Lett. 25, 1561 (2008)
Gao, F., Qin, S.-J., Wen, Q.-Y., Zhu, F.-C.: A simple participant attack on the Bradler–Dusek protocol. Quantum Info. Comput. 7, 329–334 (2007)
Cai, Q.-Y.: Eavesdropping on the two-way quantum communication protocols with invisible photons. Phys. Lett. A 351, 23–25 (2006)
Lin, J., Hwang, T.: New circular quantum secret sharing for remote agents. Quantum Inf. Process. 12, 685–697 (2013)
Acknowledgments
We would like to thank the Ministry of Science and Technology of the Republic of China, Taiwan, for partially supporting this research in finance under the Contract No. MOST 103-2221-E-006-177-. We also would like to thank our editor Yaakov S Weinstein and all the anonymous reviewers for all their valuable suggestions. We would like to sincerely thank Mr. Hung-Shih Min for his help during revision.
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix 1
\((k~\hbox {satisfies}~k_{1}\oplus k_{2}\oplus \cdots \oplus k_{n}\ne 0\left( {\hbox {mod}~2}\right) ~\hbox {or}~k_{1}\oplus k_{2}\oplus \cdots \oplus k_{n}=0\left( {\hbox {mod}~d}\right) )\)
Appendix 2
Theorem 1
The proposed scheme adequately performs the comparison of size relation.
Proof
In our proposed protocol, let \(s_{i}\) be the secret of participant i and \(\left| {p_{i}}\rangle \right. \), \(\left| {q_{i}} \rangle \right. \) be two initial states that the TP sends to the participant i. Now, we further consider that \(\left\{ {s_{i}} \right\} _{\max }\) be the maximum size of the secret \(s_{i}\), where \(l=\left\{ {s_{i}} \right\} _{\max } +1\), \(d=2\,*\,l,\) and \(\left| {q_{i}^{{\prime }{\prime }}} \rangle \right. \) denotes the qubit of the participant i that he/she sends to TP. Now, we demonstrate that how the proposed scheme performs the comparison of size relation.
Since the size relation of \(k+s_{i}\) is equal to the size relation of \(s_{i}\), therefore, we can constitute the size relation of \(s_{i},\) using the non-empty area. In this way, the proposed scheme can perform the comparison of size relation. \(\square \)
Rights and permissions
About this article
Cite this article
Huang, SL., Hwang, T. & Gope, P. Multi-party quantum private comparison with an almost-dishonest third party. Quantum Inf Process 14, 4225–4235 (2015). https://doi.org/10.1007/s11128-015-1104-z
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11128-015-1104-z