Abstract
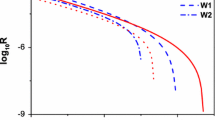
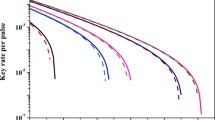
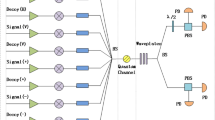
In this manuscript, we propose an improved scheme on the decoy-state quantum key distribution (QKD) under practical experimental conditions with biased basis. Compared with the standard decoy-state method with biased basis (prepare signal pulses in both X and Z basis with certain probabilities, and weak decoy pulses as well), the difference here is, we prepare signal pulses in both X and Z basis, but the weak decoy state in only X basis. In the follow-up, we adopt this scheme to conducting numerical simulations on the QKD with the mostly often used source, i.e., weak coherent source by taking statistical fluctuations into account. Furthermore, we carry out full parameter optimization on it. Numerical simulation results demonstrate that our new scheme can present a higher key generation rate and a longer transmission distance compared with standard three-intensity decoy-state method with biased basis. Moreover, it shows drastically improved performance by conducting full parameter optimization in our new scheme compared with partial optimization.



Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.References
Ekert, A.: Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 67, 661 (1991)
Lo, H.-K., Chau, H.F.: Unconditional security of quantum key distribution over arbitrarily long distances. Science 283, 2050 (1999)
Mayers, D.: Unconditional security in quantum cryptography. J. ACM 48, 351 (2001)
Bennett, C.H., Brassard, G.: Quantum cryptography: public key distribution and coin tossing. In: Proceedings of the IEEE International Conference on Computers, Systems and Signal Processing, pp. 175–179. IEEE, New York (1984)
Shor, P.W., Preskill, J.: Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 85, 441 (2000)
Peev, M., Pacher, C., Alleaume, R., et al.: The SECOQC quantum key distribution network in Vienna. New J. Phys. 11, 075001 (2009)
Sasaki, M., Fujiwara, M., Ishizuka, H., et al.: Field test of quantum key distribution in the Tokyo QKD network. Opt. Express 19, 10387 (2011)
Lo, H.-K., Chau, H.F., Ardehali, M.: Efficient quantum key distribution scheme and a proof of its unconditional security. J. Cryptol. 18, 133 (2005)
Brassard, G., Ltkenhaus, N., Mor, T., Sanders, B.C.: Limitations on practical quantum cryptography. Phys. Rev. Lett. 85, 1330 (2000)
Ltkenhaus, N., Jahma, M.: Quantum key distribution with realistic states: photon-number statistics in the photon-number splitting attack. New J. Phys. 4, 44.1 (2002)
Hwang, W.Y.: Quantum key distribution with high loss: toward global secure communication. Phys. Rev. Lett. 91, 057901 (2003)
Wang, X.-B.: Beating the photon-number-splitting attack in practical quantum crytography. Phys. Rev. Lett. 94, 230503 (2005)
Wang, Q., Wang, X.-B., Guo, G.-C.: Practical decoy-state method in quantum key distribution with a heralded single-photon source. Phys. Rev. A 75, 012312 (2007)
Wang, Q., Chen, W., Xavier, G., et al.: Experimental decoy-state quantum key distribution with a sub-Poissionian heralded single-photon source. Phys. Rev. Lett. 100, 090501 (2008)
Wang, Q., Wang, X.-B.: Improved practical decoy state method in quantum key distribution with parametric down-conversion source. Europhys. Lett. 79, 40001 (2007)
Lo, H.-K., Ma, X.-F., Chen, K.: Decoy state quantum key distribution. Phys. Rev. Lett. 94, 230504 (2005)
Ma, X.-F., Qi, B., Zhao, Y., Lo, H.-K.: Practical decoy state for quantum key distribution. Phys. Rev. A 75, 012312 (2007)
Peng, C.-Z., Zhang, J., Yang, D., et al.: Experimental long-distance decoy-state quantum key distribution based on polarization encoding. Phys. Rev. Lett. 98, 010505 (2007)
Wei, Z.-C., Wang, W.-L., Zhang, Z., Guo, M., Ma, X.-F.: Decoy-state quantum key distribution with biased basis choice. Sci. Rep. 3, 2454 (2013)
Lucamarini, M., Patel, K., Dynes, J., et al.: Efficient decoy-state quantum key distribution with quantified security. Opt. Express 21, 24550 (2013)
Lim, C.C.W., Curty, M., Walenta, N., et al.: Concise security bounds for practical decoy-state quantum key distribution. Phys. Rev. A 89, 022307 (2014)
Gottesman, D., Lo, H.-K., Ltkenhaus, N., Preskill, J.: Security of quantum key distribution with imperfect devices. Quantum Inf. Comput. 4, 325 (2004)
Fung, C.-H.F., Ma, X.-F., Chau, H.F.: Practical issues in quantum-key-distribution postprocessing. Phys. Rev. A 81, 012318 (2010)
Zhou, Y.-H., Yu, Z.-W., Wang, X.-B.: Tightened estimation can improve the key rate of measurement-device-indepengdent quantum key distribution by more than 100%. Phys. Rev. A 89, 052325 (2014)
Ma, X.-F., Fung, C.-H.F., Boileau, J.-C., Chau, H.F.: Universally composable and customizable post-processing for practical quantum key distribution. Comput. Secur. 30, 172 (2011)
Wang, X.-B., Yang, L., Peng, C.-Z., Pan, J.-W.: Decoy-state quantum key distribution with both source errors and statistical fluctuations. New J. Phys. 11, 075006 (2009)
Yu, Z.-W., Zhou, Y.-H., Wang, X.-B.: Statistical fluctuation analysis for measurement-device-independent quantum key distribution three-intensity decoy-state method. Phys. Rev. A 91, 032318 (2015)
Xu, F.-H., Xu, H., Lo, H.-K.: Protocol choice and parameter optimization in decoy-state measurement-device-independent quantum key distribution. Phys. Rev. A 89, 052333 (2014)
Wang, Q., Zhang, C.-H., Wang, X.-B.: Scheme for realizing passive quantum key distribution with heralded single-photon sources. Phys. Rew. A 93, 032312 (2016)
Acknowledgements
We gratefully acknowledge the financial support from the National Key Research and Development Program of China through Grant No. 2017YFA0304100, the National Natural Science Foundation of China through Grants Nos. 61475197, 61590932, 11774180, 61705110, the Natural Science Foundation of the Jiangsu Higher Education Institutions through Grant No. 15KJA120002, the Outstanding Youth Project of Jiangsu Province through Grant No. BK20150039, the Natural Science Foundation of Jiangsu Province through Grant No. BK20170902, and the NUPTSF through Grant No. NY217006.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Mao, CC., Li, J., Zhu, JR. et al. An improved proposal on the practical quantum key distribution with biased basis. Quantum Inf Process 16, 256 (2017). https://doi.org/10.1007/s11128-017-1707-7
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-017-1707-7