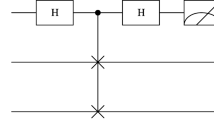
Abstract
Recently, Sun et al. (Quantum Inf Process:14:2125-2133, 2015) proposed a quantum private comparison protocol allowing two participants to compare the equality of their secrets via a malicious third party (TP). They designed an interesting trap comparison method to prevent the TP from knowing the final comparison result. However, this study shows that the malicious TP can use the statistics attack to reveal the comparison result. A simple modification is hence proposed to solve this problem.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.References
Bennett, C.H., Brassard, G.: Quantum cryptography: public key distribution and coin tossing. In: International Conference on Computers, Systems and Signal Processing, pp. 175–179. Bangalore, India (1984)
Chang, Y.-J., Tsai, C.-W., Hwang, T.: Multi-user private comparison protocol using GHZ class states. Quantum Inf. Process. 12, 1077–1088 (2013)
Guo, F.Z., Gao, F., Qin, S.J., Zhang, J., Wen, Q.Y.: Quantum private comparison protocol based on entanglement swapping of d-level Bell states. Quantum Inf. Process. 12, 2793–2802 (2013)
Huang, S.-L., Hwang, T., Gope, P.: Multi-party quantum private comparison with an almost-dishonest third party. Quantum Inf. Process. 14, 4225–4235 (2015)
Liu, W.-J., Liu, C., Chen, H.-W., Liu, Z.-H., Yuan, M.-X., Lu, J.-S.: Improvement on an efficient protocol for the quantum private comparison of equality with W state. Int. J. Quantum Inf. 12, 1450001 (2014)
Liu, W.-J., Liu, C., Liu, Z.-H., Liu, J.-F., Geng, H.-T.: Same initial states attack in Yang et al’.s quantum private comparison protocol and the improvement. Int. J. Theor. Phys. 53, 271–276 (2014)
Liu, W.-J., Liu, C., Wang, H-b, Liu, J.-F., Wang, F., Yuan, X.-M.: Secure quantum private comparison of equality based on asymmetric W state. Int. J. Theor. Phys. 53, 1804–1813 (2014)
Liu, W., Wang, Y.-B.: Quantum private comparison based on GHZ entangled states. Int. J. Theor. Phys. 51, 3596–3604 (2012)
Liu, W., Wang, Y.-B., Wang, X.-M.: Multi-party quantum private comparison protocol using d-dimensional basis states without entanglement swapping. Int. J. Theor. Phys. 53, 1085–1091 (2014)
Liu, X.-T., Zhao, J.-J., Wang, J., Tang, C.-J.: Cryptanalysis of the secure quantum private comparison protocol. Phys. Scripta 87, 065004 (2013)
Luo, Q-b, Yang, G-w, She, K., Niu, W.-N., Wang, Y.-Q.: Multi-party quantum private comparison protocol based on d-dimensional entangled states. Quantum Inf. Process. 13, 2343–2352 (2014)
Sun, Z., Jianping, Y., Wang, P., Xu, L., Wu, C.: Quantum private comparison with a malicious third party. Quantum Inf. Process. 14, 2125–2133 (2015)
Tseng, H.-Y., Lin, J., Hwang, T.: New quantum private comparison protocol using EPR pairs. Quantum Inf. Process. 11, 373–384 (2012)
Xu, G.A., Chen, X.-B., Wei, Z.-H., Li, M.-J., Yang, Y.-X.: An efficient protocol for the quantum private comparison of equality with a four-qubit cluster state. Int. J. Quantum Inf. 10, 1250045 (2012)
Yang, Y.-G., Wen, Q.-Y.: An efficient two-party quantum private comparison protocol with decoy photons and two-photon entanglement. J. Phys. A Math. Theor. 42, 055305 (2009)
Zhang, W.-W., Li, D., Song, T.-T., Li, Y.-B.: Quantum private comparison based on quantum search algorithm. Int. J. Theor. Phys. 52, 1466–1473 (2013)
Acknowledgements
We would like to thank the Ministry of Science and Technology of the Republic of China, Taiwan, for partially supporting this research in finance under the Contract No. MOST 105-2221-E-006-162 -MY2.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Gu, J., Ho, CY. & Hwang, T. Statistics attack on ‘quantum private comparison with a malicious third party’ and its improvement. Quantum Inf Process 17, 23 (2018). https://doi.org/10.1007/s11128-017-1788-3
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-017-1788-3