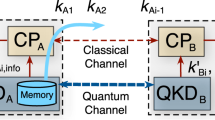
Abstract
Covert communication methods are used in the communication with high security level. When it turns to quantum communication, covertness is also an important concern which is firstly discussed by Arrazola and Scarani (Phys Rev Lett, 117:250503, 2016). To make quantum key distribution (QKD) protocol more suitable in the scenarios need high security, we propose a covert QKD protocol with decoy-state method in this paper. The secure key rate and covertness of the covert decoy-state QKD are proved. We compare the performance of the covert decoy-state QKD with those of the original decoy-state QKD and covert QKD without decoy states in numerical simulations. It shows that (1) the covert decoy-state QKD can have a performance comparable to the original decoy-state QKD protocol besides its covertness; (2) the covert decoy-state QKD can have a considerable improvement of transmission distance over covert QKD without decoy states at the cost of a small change of covertness parameter. Furthermore, the statistical fluctuation due to the finite length of data is also taken into account based on the Gaussian analysis method.




Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.References
Bennett, C.H., Brassard, G.: Quantum cryptography: public-key distribution and coin tossing. In: In Proceedings of IEEE International Conference on Computers, Systems and Signal Processing, Bangalore, India, pp. 175–179 (1984)
Simon, M.K., Omura, J.K., Scholtz, R.A., Levitt, B.K.: Spread Spectrum Communications Handbook. McGraw-Hill, New York City (2002)
Fridrich, J.: Steganography in Digital Media: Principles, Algorithms, and Applications. Cambridge University Press, Cambridge (2009)
Bash, B.A., Guha, S., Goeckel, D., Towsley, D.: Quantum noise limited optical communication with low probability of detection. In: 2013 IEEE International Symposium on Information Theory Proceedings (ISIT), pp. 1715–1719 (2013)
Che, P.H., Bakshi, M., Jaggi, S.: Reliable deniable communication: hiding messages in noise. In: 2013 IEEE International Symposium on Information Theory Proceedings (ISIT), pp. 2945–2949 (2013)
Bash, B.A., Goeckel, D., Towsley, D.: Limits of reliable communication with low probability of detection on awgn channels. IEEE J. Sel. Areas Commun. 31, 1921 (2013)
Bash, B.A., Gheorghe, A.H., Patel, M., Habif, J.L., Goeckel, D., Towsley, D., Guha, S.: Quantum-secure covert communication on bosonic channels. Nat. Commun. 6, 8626 (2015)
Arrazola, J.M., Scarani, V.: Covert quantum communication. Phys. Rev. Lett. 117, 250503 (2016)
Shor, P.W., Preskill, J.: Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 85, 441 (2000)
Gisin, N., Ribordy, G., Tittel, W., Zbinden, H.: Quantum cryptography. Rev. Mod. Phys. 74, 145–195 (2002)
Lo, H.K., Chau, H.F.: Unconditional security of quantum key distribution over arbitrarily long distances. Science 283, 2050 (1999)
Scarani, V., Acin, A., Ribordy, G., Gisin, N.: Quantum cryptography protocols robust against photon number splitting attacks for weak laser pulse implementations. Phys. Rev. Lett. 92, 057901 (2004)
Wang, X.B.: Beating the photon-number-splitting attack in practical quantum cryptography. Phys. Rev. Lett. 94, 230503 (2005)
Lo, H.K., Ma, X.F., Chen, K.: Decoy state quantum key distribution. Phys. Rev. Lett. 94, 230504 (2005)
Hwang, W.Y.: Quantum key distribution with high loss: toward global secure communication. Phys. Rev. Lett. 91, 057901 (2003)
Lin, S., Wen, Q.Y., Gao, F., Zhu, F.C.: Eavesdropping on secure deterministic communication with qubits through photon-number-splitting attacks. Phys. Rev. A 79, 054303 (2009)
Brassard, G., Lutkenhaus, N., Mor, T., Sanders, B.C.: Limitations on practical quantum cryptography. Phys. Rev. Lett. 85, 1330 (2000)
Song, T.T., Zhang, J., Qin, S.J., Gao, F., Wen, Q.Y.: Finite-key analysis for quantum key distribution with decoy states. Quantum Inf. Comput. 11, 374–389 (2011)
Ma, X., Razavi, M.: Alternative schemes for measurement-device-independent quantum key distribution. Phys. Rev. A 86, 062319 (2012)
Song, T.T., Wen, Q.Y., Guo, F.Z., Tan, X.Q.: Finite-key analysis for measurement-device-independent quantum key distribution. Phys. Rev. A 86, 022332 (2012)
Rubenok, A., Slater, J.A., Chan, P., Lucio-Martinez, I., Tittel, W.: Real-world two-photon interference and proof-of-principle quantum key distribution immune to detector attacks. Phys. Rev. Lett. 111, 130501 (2013)
Wang, X.B.: Three-intensity decoy-state method for device-independent quantum key distribution with basis-dependent errors. Phys. Rev. A 87, 012320 (2013)
Yu, Z.W., Zhou, Y.H., Wang, X.B.: Three-intensity decoy-state method for measurement device independent quantum key distribution. Phys. Rev. A 88, 062339 (2013)
Zhou, C., Bao, W.S., Zhang, H.L., Li, H.W., Wang, Y., Li, Y., Wang, X.: Biased decoy-state measurement-device-independent quantum key distribution with finite resources. Phys. Rev. A 91, 022313 (2015)
Zhou, Y.H., Yu, Z.W., Wang, X.B.: Making the decoy-state measurement-device-independent quantum key distribution practically useful. Phys. Rev. A 93, 042324 (2016)
Liu, L., Guo, F.Z., Qin, S.J., Wen, Q.Y.: Round-robin differential-phase-shift quantum key distribution with a passive decoy state method. Sci. Rep. 7, 42261 (2017)
Liu, L., Guo, F.Z., Wen, Q.Y.: Practical passive decoy state measurement-device-independent quantum key distribution with unstable sources. Sci. Rep. 7, 11370 (2017)
Wang, Y., Bao, W.S., Zhou, C., Jiang, M.S., Li, H.W.: Tight finite-key analysis of a practical decoy-state quantum key distribution with unstable sources. Phys. Rev. A 94, 032335 (2016)
Sun, S.H., Gao, M., Li, C.Y., Liang, L.M.: Practical decoy-state measurement-device-independent quantum key distribution. Phys. Rev. A 87, 052329 (2013)
Xu, F., Xu, H., Lo, H.K.: Protocol choice and parameter optimization in decoy-state measurement-device-independent quantum key distribution. Phys. Rev. A 89, 052333 (2014)
Lim, C.C.W., Curty, M., Walenta, N., Xu, F., Zbinden, H.: Concise security bounds for practical decoy-state quantum key distribution. Phys. Rev. A 89, 022307 (2014)
Zhang, Z., Zhao, Q., Razavi, M., Ma, X.: Improved key-rate bounds for practical decoy-state quantum-key-distribution systems. Phys. Rev. A 95, 012333 (2017)
Gottesman, D., Lo, H.K., Lutkenhaus, N., Preskill, J.: Security of quantum key distribution with imperfect devices. Quantum Inf. Comput. 4, 325 (2004)
Ma, X., Qi, B., Zhao, Y., Lo, H.K.: Practical decoy state for quantum key distribution. Phys. Rev. A 72, 012326 (2005)
Tomamichel, M., Lim, C.C.W., Gisin, N., Renner, R.: Tight finite-key analysis for quantum cryptography. Nat. Commun. 3, 634 (2012)
Ma, X., Fung, C.H.F., Razavi, M.: Statistical fluctuation analysis for measurement-device-independent quantum key distribution. Phys. Rev. A 86, 052305 (2012)
Cody, W.J.: Algorithm 715: SPECFUNCA portable fortran package of special function routines and test drivers. ACM Trans. Math. Softw. 19, 22 (1993)
Boyd, S., Vandenberghe, L.: Convex Optimization. Cambridge University Press, Cambridge (2004)
Gobby, C., Yuan, Z.L., Shields, A.J.: Quantum key distribution over 122 km of standard telecom fiber. Appl. Phys. Lett. 84, 3762 (2004)
Acknowledgements
This work was supported by the National Natural Science Foundation of China, Grant Nos. 61572081, 61672110 and 61671082.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix
Appendix
In this section, we derive Eve’s state \(\sigma _\mathrm{E}\) when Alice and Bob communicate and give the details on how to obtain the bound of detection bias \(\delta \).
We have
and \(\rho _\mathrm{E}\) is shown in Eq. (14). The state \(\rho _s\) and \(\rho _d\) can be given
where \(p(k,l)=\frac{{{\bar{n}}}^k}{(1+{\bar{n}})^{k+1}}\frac{\hbox {e}^{-\mu }\mu ^l}{l!}\), \(p(k',l')=\frac{{{\bar{n}}}^{k'}}{(1+{\bar{n}})^{k'+1}}\frac{\hbox {e}^{-\upsilon }\upsilon ^{l'}}{l'!}\) and \(\sigma _{k,l}\) is Eve’s state when there are k photons coming from the signal states and l photons from the noise, \(\sigma _{k',l'}\) is Eve’s state when there are k photons coming from the decoy states and l photons from the noise.
We can obtain
In the same way, we can get the state \(\rho _d\). Then Eve’s state \(\sigma _\mathrm{E}\) when Alice and Bob communicate can be obtained.
The state \(\rho _\mathrm{E}\) and the state \(\sigma _\mathrm{E}\) that Eve gets when Alice and Bob communicate are diagonal in the Fock basis. Thus, we can treat both states as classical probability distributions and write [8]
where \(\rho _\mathrm{E}(n)\) and \(\sigma _\mathrm{E}(n)\) are the probability of observing n photons in each cases. However, higher-order terms actually decrease the value of the relative entropy. Therefore, to obtain an upper bound on the relative entropy, it suffices to consider only terms to first order in \({\bar{n}}\) and to second order in \(\mu ,\upsilon \).
We can get
We obtain a bound through a Taylor series expansion, keeping terms to second order in \(\mu \).
and
According to these two bounds, and in the same way, keeping terms to second order in \(\upsilon \), we can obtain an upper bound on the relative entropy,
Thus, using
the detection bias \(\delta \) finally can be bounded as
where \(N^s\) and \(N^d\), respectively, denote the signal states and decoy states sent by Alice.
Rights and permissions
About this article
Cite this article
Guo, FZ., Liu, L., Wang, AK. et al. Practical covert quantum key distribution with decoy-state method. Quantum Inf Process 18, 95 (2019). https://doi.org/10.1007/s11128-019-2181-1
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-019-2181-1