Abstract
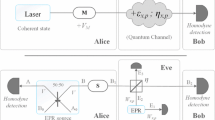
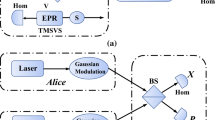
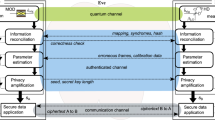
Numerous continuous-variable quantum key distribution (CV-QKD) schemes are based on the Gaussian modulation, which is carried out in conjugate quadratures. In order to simplify the traditional protocols, as well as improving the security of the system, we propose the plug-and-play unidimensional CV-QKD protocol, which waives the necessity of propagating a local oscillator (LO) between legitimate users and generates a real local LO for quantum measurement. The new protocol utilizes only one phase modulator rather than two, which is different from the dual-phase-modulated coherent-states protocol that we proposed earlier. The prepare-and-measure and entanglement-based schemes are described. The security of the new protocol against collective attacks in a Gaussian channel is analyzed, and the security boundary is derived, which is achieved by establishing the relationship between the uncertain parameters of the unmodulated quadrature. The performance of it is analyzed in both asymptotic and finite-size cases. Such an efficient scheme not only provides a way of removing the security loopholes associated with the transmitting LO, but also eliminates the need for one of the phase modulators, and thus will facilitate commercialization of continuous-variable quantum key distribution.










Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.References
Scarani, V., Bechmann-Pasquinucci, H., Cerf, N.J., Dušek, M., Lütkenhaus, N., Peev, M.: The security of practical quantum key distribution. Rev. Mod. Phys. 81(3), 1301 (2009)
Weedbrook, C., Pirandola, S., García-Patrón, R., Cerf, N.J., Ralph, T.C., Shapiro, J.H., Lloyd, S.: Gaussian quantum information. Rev. Mod. Phys. 84(2), 621 (2012)
Takeda, S., Fuwa, M., van Loock, P., Furusawa, A.: Entanglement swapping between discrete and continuous variables. Phys. Rev. Lett. 114(10), 100501 (2014)
Gessner, M., Pezzė, L., Smerzi, A.: Efficient entanglement criteria for discrete, continuous, and hybrid variables. Phys. Rev. A 94(2), 020101 (2016)
Grosshans, F., Grangier, P.: Continuous variable quantum cryptography using coherent states. Phys. Rev. Lett. 88(5), 057902 (2002)
Jouguet, P., Elkouss, D., Kunz-Jacques, S.: High-bit-rate continuous-variable quantum key distribution. Phys. Rev. A 90(4), 042329 (2014)
Guo, Y., Liao, Q., Huang, D., Zeng, G.H.: Quantum relay schemes for continuous-variable quantum key distribution. Phys. Rev. A 95(4), 042326 (2017)
Grosshans, F., Assche, G.V., Wenger, J., Brouri, R., Cerf, N.J., Grangier, P.: Quantum key distribution using Gaussian-modulated coherent states. Nature 421(6920), 238 (2003)
Weedbrook, C., Lance, A.M., Bowen, W.P., Symul, T., Ralph, T.C., Lam, P.K.: Coherent-state quantum key distribution without random basis switching. Phys. Rev. A 73(2), 022316 (2006)
Guo, Y., Liao, Q., Wang, Y.J., Huang, D., Huang, P., Zeng, G.H.: Performance improvement of continuous-variable quantum key distribution with an entangled source in the middle via photon subtraction. Phys. Rev. A 95(3), 032304 (2017)
Wu, X.D., Chen, F., Wu, X.H., Guo, Y.: Controlling continuous-variable quantum key distribution with entanglement in the middle using tunable linear optics cloning machines. Int. J. Theor. Phys. 56(2), 415 (2016)
Lance, A.M., Symul, T., Sharma, V., Weedbrook, C., Ralph, T.C., Lam, P.K.: No-switching quantum key distribution using broadband modulated coherent light. Phys. Rev. Lett. 95(18), 180503 (2005)
Lodewyck, J., Bloch, M., García-Patrón, R., Fossier, S., Karpov, E., Diamanti, E., Debuisschert, T., Cerf, N.J., Tualle-Brouri, R., McLaughlin, S.W., Grangier, P.: Quantum key distribution over 25 km with an all-fiber continuous-variable system. Phys. Rev. A 76(4), 042305 (2007)
Qi, B., Huang, L.L., Qian, L., Lo, H.K.: Experimental study on the Gaussian-modulated coherent-state quantum key distribution over standard telecommunication fibers. Phys. Rev. A 76(5), 052323 (2007)
Grosshans, F.: Collective attacks and unconditional security in continuous variable quantum key distribution. Phys. Rev. Lett. 94(2), 020504 (2005)
Navascués, M., Acín, A.: Security bounds for continuous variables quantum key distribution. Phys. Rev. Lett. 94(2), 020505 (2005)
Lodewyck, J., Debuisschert, T., Tualle-Brouri, R., Grangier, P.: Controlling excess noise in fiber-optics continuous-variable quantum key distribution. Phys. Rev. A 72(5), 050303 (2005)
García-Patrón, R., Cerf, N.J.: Unconditional optimality of Gaussian attacks against continuous-variable quantum key distribution. Phys. Rev. Lett. 97(19), 190503 (2006)
Navascués, M., Grosshans, F., Acín, A.: Optimality of Gaussian attacks in continuous-variable quantum cryptography. Phys. Rev. Lett. 97(19), 190502 (2006)
Pirandola, S., Braunstein, S.L., Lloyd, S.: Characterization of collective Gaussian attacks and security of coherent-state quantum cryptography. Phys. Rev. Lett. 101(20), 200504 (2008)
Leverrier, A., Grangier, P.: Unconditional security proof of long-distance continuous-variable quantum key distribution with discrete modulation. Phys. Rev. Lett. 102(18), 180504 (2009)
Huang, D., Huang, P., Lin, D.K., Zeng, G.H.: Long-distance continuous-variable quantum key distribution by controlling excess noise. Sci. Rep. 6(1), 19201 (2016)
Huang, D., Lin, D.K., Huang, P., Wang, C., Liu, W.Q., Fang, S.H., Zeng, G.H.: Continuous-variable quantum key distribution with 1 Mbps secure key rate. Opt. Express 23(13), 17511 (2015)
Jouguet, P., Kunz-Jacques, S., Leverrier, A., Grangier, P., Diamanti, E.: Experimental demonstration of long-distance continuous-variable quantum key distribution. Nat. Photon. 7(5), 378 (2013)
Huang, J.Z., Weedbrook, C., Yin, Z.Q., Wang, S., Li, H.W., Chen, W., Guo, G.C., Han, Z.F.: Quantum hacking on continuous-variable quantum key distribution system using a wavelength attack. Phys. Rev. A 87(6), 062329 (2013)
Ma, X.C., Sun, S.H., Jiang, M.S., Liang, L.M.: Wavelength attack on practical continuous-variable quantum-key-distribution system with a heterodyne protocol. Phys. Rev. A 87(5), 052309 (2014)
Qin, H., Kumar, R., Alléaume, R.: Saturation attack on continuous-variable quantum key distribution system. Proc. SPIE (2013). https://doi.org/10.1117/12.2028543
Jouguet, P., Kunz-Jacques, S., Diamanti, E.: Preventing calibration attacks on the local oscillator in continuous-variable quantum key distribution. Phys. Rev. A 87(6), 062313 (2013)
Ma, X.C., Sun, S.H., Jiang, M.S., Liang, L.M.: Local oscillator fluctuation opens a loophole for Eve in practical continuous-variable quantum-key-distribution systems. Phys. Rev. A 88(2), 022339 (2013)
Usenko, V.C., Grosshans, F.: Unidimensional continuous-variable quantum key distribution. Phys. Rev. A 92(6), 062337 (2015)
Gehring, T., Jacobsen, C.S., Andersen, U.L.: Single-quadrature continuous-variable quantum key distribution. arXiv:1507.01003v2 (2015)
Usenko, V.C.: Unidimensional continuous-variable quantum key distribution using squeezed states. Phys. Rev. A 98(3), 032321 (2018)
Huang, D., Huang, P., Wang, T., Li, H.S., Zhou, Y.M., Zeng, G.H.: Continuous-variable quantum key distribution based on a plug-and-play dual-phase-modulated coherent-states protocol. Phys. Rev. A 94(3), 032305 (2016)
Mao, Q.P., Wang, L., Zhao, S.M.: Plug-and-play round-robin differential phase-shift quantum key distribution. Sci. Rep. 7(1), 15435 (2017)
Laudenbach, F., Pacher, C., Fung, C.H.F., Poppe, A., Peev, M., Schrenk, B., Hentschel, M., Walther, P., Hübel, H.: Continuous-variable quantum key distribution with Gaussian modulation: the theory of practical implementations. arXiv:1703.09278v3 (2018)
Shen, S.Y., Dai, M.W., Zheng, X.T., Sun, Q.Y., Zhu, B., Guo, G.C., Han, Z.F.: Free-space continuous-variable quantum key distribution of unidimensional Gaussian modulation using polarized coherent-states in urban environment. arXiv:1810.00408v1 (2018)
Qi, B., Lougovski, P., Pooser, R., Grice, W., Bobrek, M.: Generating the local oscillator locally in continuous-variable quantum key distribution based on coherent detection. Phys. Rev. X 5(4), 041009 (2015)
Mo, X.F., Zhu, B., Han, Z.F., Gui, Y.Z., Guo, G.C.: Faraday–Michelson system for quantum cryptography. Opt. Lett. 30(19), 2632 (2005)
Legre, M., Zbinden, H., Gisin, N.: Implementation of continuous variable quantum cryptography in optical fibres using a go-and-return configuration. Quantum Inf. Comput. 6(4), 326 (2012)
Liao, Q., Guo, Y., Xie, C.L., Huang, D., Huang, P., Zeng, G.H.: Composable security of unidimensional continuous-variable quantum key distribution. Quantum Inf. Process 17(5), 113 (2018)
Hillery, M.: Quantum cryptography with squeezed states. Phys. Rev. A 61(2), 022309 (2000)
Fossier, S., Diamanti, E., Debuisschert, T., Villing, A., Tualle-Brouri, R., Grangier, P.: Field test of a continuous-variable quantum key distribution prototype. New J. Phys. 11(4), 045023 (2009)
Li, Z.Y., Zhang, Y.C., Xu, F.H., Peng, X., Guo, H.: Continuous-variable measurement-device-independent quantum key distribution. Phys. Rev. A 89(5), 052301 (2014)
Wang, X.Q., Huang, C.H.: Noise-enhanced CVQKD with untrusted source. Mod. Phys. Lett. B 31(16), 1750143 (2017)
Grosshans, F., Cerf, N.J., Wenger, J., Tualle-Brouri, R., Grangier, P.: Virtual entanglement and reconciliation protocols for quantum cryptography with continuous variables. Quantum Inf. Comput. 3(7), 535 (2003)
Huang, P., He, G.Q., Zeng, G.H.: Bound on noise of coherent source for secure continuous-variable quantum key distribution. Int. Theor. Phys. 52(5), 1572 (2013)
Hirano, T., Yamanaka, H., Ashikaga, M., Konishi, T., Namiki, R.: Quantum cryptography using pulsed homodyne detection. Phys. Rev. A 68(4), 042331 (2003)
Wang, P., Wang, X.Y., Li, Y.M.: Security analysis of unidimensional continuous-variable quantum key distribution using uncertainty relations. Entropy 20, 157 (2018)
Wang, X.Y., Cao, Y.X., Wang, P., Li, Y.M.: Advantages of the coherent state compared with squeezed state in unidimensional continuous variable quantum key distribution. Quantum Inf. Process 17, 344 (2018)
Leverrier, A., Grosshans, F., Grangier, P.: Finite-size analysis of continuous-variable quantum key distribution. Phys. Rev. A 81(6), 062343 (2010)
Furrer, F., Franz, T., Berta, M., Leverrier, A., Scholz, V.B., Tomamichel, M., Werner, R.F.: Continuous variable quantum key distribution: finite-key analysis of composable security against coherent attacks. Phys. Rev. Lett. 109(10), 100502 (2012)
Fossier, S., Diamanti, E., Debuisschert, T., Tualle-Brouri, R., Grangier, P.: Improvement of continuous-variable quantum key distribution systems by using optical preamplifiers. J. Phys. B 42(11), 114014 (2009)
Serafini, A., Paris, M.G.A., Illuminati, F., De Siena, S.: Quantifying decoherence in continuous variable systems. J. Opt. B: Quantum Semiclass. Opt. 7(4), R19 (2005)
Zhang, X.Y., Zhang, Y.C., Zhao, Y.J., Wang, X.Y., Yu, S., Guo, H.: Finite-size analysis of continuous-variable measurement-device-independent quantum key distribution. arXiv:1707.05931v2 (2017)
Wang, P., Wang, X.Y., Li, J.Q., Li, Y.M.: Finite-size analysis of unidimensional continuous-variable quantum key distribution under realistic conditions. Opt. Express 25(23), 27995 (2017)
Acknowledgements
This work is supported by the National Natural Science Foundation of China (Grant Nos. 61801522, 61871407) and the Fundamental Research Funds for the Central Universities of Central South University.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix A: The derivation of the symplectic eigenvalues
To calculate the second part of (17), we need to calculate the symplectic eigenvalues of the covariance matrix \(\gamma _{BHG}^{p_A}\), which can be characterized by the following equation:
where \(\gamma _{BHG}\), \(\gamma _A\), and \(\sigma _{BHGA}\) are the submatrix of \(\gamma _{BHGA}\), and
which can be derived by rearranging the lines and columns of matrix \(\gamma _{BAHG}\) describing the state \(\rho _{BAHG}\). Specifically, \(\gamma _{BAHG}\) can be derived by applying a beam splitter transformation \(Y^{AS}\) that models the inefficiency of the detector and acts on modes \(A_2\) and \(H_0\) [52], and it is given as follows:
where \(Y^{AS}=\varPi _B \oplus Y_{A_2 H_0}^{AS} \oplus \varPi _G \), with
\(\gamma _{H_0 G}\) is the matrix that describes the EPR state of variance \(V_d\) used to model the detector’s electronic noise, and it is written as
Therefore, we can calculate the symplectic eigenvalues of the covariance matrix \(\gamma _{BHG}^{p_A}\):
where
Appendix B: Physical constraint
This Eq. (25) imposes physical constraints on the possible values of \(C_x^{A_2}\) and \(V_x^{A_2}\). Such constraint can be further described by the following parabolic inequality:
where \(V_0 = \frac{1}{1+T_p (\xi _p^2+2V\xi _p+\varepsilon _p)}\).
Considering that \(C_x^{A_2}=\sqrt{\frac{T_x (V^2-1)}{V}}, V_x^{A_2}=1+T_x \varepsilon _x\), the above parabolic inequality transforms into the following inverse function inequality:
From the mathematical relationship, we can know that the inverse function inequality is satisfied if \(\varepsilon _x \ge 0\) and \(T_x \in [0, 1]\). Therefore, Eq. (25) is true in the same condition. It means that the plug-and-play UD protocol always satisfies the requirement of the physicality of the state.
Rights and permissions
About this article
Cite this article
Zhang, H., Ruan, X., Wu, X. et al. Plug-and-play unidimensional continuous-variable quantum key distribution. Quantum Inf Process 18, 128 (2019). https://doi.org/10.1007/s11128-019-2241-6
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-019-2241-6