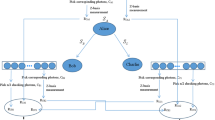
Abstract
To ensure communication security, it is necessary to verify the identities of the communicators. Two semi-quantum identification protocols with single photons involving two parties, i.e., quantum Alice and classical Bob, are presented. In the first semi-quantum identification protocol, classical Bob can authenticate quantum Alice’s identity without the help of an authenticated classical channel. As for the second one, quantum Alice can verify the identity of classical Bob without the classical measurement ability. Semi-quantum identification is significant to ensure the security of semi-quantum key distribution, semi-quantum secret sharing and so on. The proposed two identification protocols against common attacks can be employed in several existing semi-quantum key distribution protocols based on single photons to resist the man-in-the-middle attack.





Similar content being viewed by others
References
Bennett, C.H., Brassard, G.: Quantum cryptography: public key distribution and coin tossing. In: Proceedings of IEEE International Conference on Computers, Systems and Signal Processing, Bangalore, India, pp. 175–179 (1984)
Ekert, A.K.: Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 67(6), 661–663 (1991)
Bennett, C.H.: Quantum cryptography using any two nonorthogonal states. Phys. Rev. Lett. 68(21), 3121–3124 (1992)
Deng, F., Long, G.: Bidirectional quantum key distribution protocol with practical faint laser pulses. Phys. Rev. A 70(1), 235–238 (2004)
Mayers, D.: Unconditional security in quantum cryptography. J. ACM 48(3), 351–406 (1998)
Lo, H.K., Chau, H.F.: Unconditional security of quantum key distribution over arbitrarily long distances. Science 283(5410), 2050–2056 (1999)
Shor, P.W., Preskill, J.: Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 85(2), 441–444 (2000)
Biham, E., Boyer, M., Boykin, P.O., Mor, T., Roychowdhury, V.: A proof of the security of quantum key distribution. J. Cryptol. 19(4), 381–439 (2006)
Dusek, M., Haderka, O., Hendrych, M., Mayska, R.: Quantum identification system. Phys. Rev. A 60(1), 149–155 (1999)
Zeng, G., Zhang, W.: Identity verification in quantum key distribution. Phys. Rev. A 61(2), 022303 (2000)
Mihara, T.: Quantum identification schemes with entanglements. Phys. Rev. A 65, 052326 (2002)
Zeng, G.: Quantum identity authentication without trusted-party. Acta Electron. Sin. 32(7), 1148–1151 (2004)
Zhou, N., Zeng, G., Zeng, W., Zhu, F.: Cross-center quantum identification scheme based on teleportation and entanglement swapping. Opt. Commun. 254(4–6), 380–388 (2005)
Zhang, Z., Zeng, G., Zhou, N., Xiong, J.: Quantum identity authentication based on ping–pong technique for photons. Phys. Lett. A 356(3), 199–205 (2006)
Yuan, H., Liu, Y., Pan, G., Zhang, G., Zhou, J., Zhang, Z.: Quantum identity authentication based on ping–pong technique without entanglements. Quantum Inf. Process. 13, 2535–2549 (2014)
Chang, Y., Changchun, X., Zhang, S., Yan, L.: Quantum secure direct communication and authentication protocol with single photons. Chin. Sci. Bull. 58, 4571–4576 (2013)
Shi, W., Zhou, Y., Yang, Y.: Quantum deniable authentication. Quantum Inf. Process. 13, 1501–1510 (2014)
Huang, P., Zhu, J., Yuan, L., Zeng, G.: Quantum identity authentication using Gaussian-modulated squeezed states. Int. J. Quantum Inf. 9(2), 701–721 (2011)
Hong, C.H., Heo, J., Jang, J.G., Kwon, D.: Quantum identity authentication with single photon. Quantum Inf. Process. 16, 236 (2017)
Boyer, M., Kenigsberg, D., Mor, T.: Quantum key distribution with classical Bob. Phys. Rev. Lett. 99(14), 140501 (2007)
Hua, L., Cai, Q.: Quantum key distribution with classical Alice. Int. J. Quantum Inf. 6(6), 1195–1202 (2008)
Tan, Y., Hua, L., Cai, Q.: Comment on “Quantum key distribution with classical Bob”. Phys. Rev. Lett. 102(9), 1767–1787 (2009)
Boyer, M., Kenigsberg, D., Mor, T.: Comment on “Quantum key distribution with classical Bob’’ reply. Phys. Rev. Lett. 102(9), 098902 (2009)
Boyer, M., Gelles, R., Kenigsberg, D., Mor, T.: Semiquantum key distribution. Phys. Rev. A 79(3), 295 (2008)
Boyer, M., Gelles, R., Kenigsberg, D., Mor, T.: Semiquantum key distribution. In: Quantum Computation and Quantum Information Theory: Reprint Volume with Introductory Notes for ISI TMR Network School, pp. 235–274 (2010)
Zou, X., Qiu, D., Li, L., Lihua, W., Li, L.: Semiquantum-key distribution using less than four quantum states. Phys. Rev. A 79(5), 1744–1747 (2009)
Boyer, M., Mor, Tl: Comment on “Semiquantum-key distribution using less than four quantum states”. Phys. Rev. A 83(4), 1744–1747 (2010)
Zou, X., Qiu, D., Li, L., Lihua, W., Li, L.: Reply to “Comment on ‘Semiquantum-key distribution using less than four quantum states’”. Phys. Rev. A 83(4), 1744–1747 (2010)
Boyer, M., Mor, T.: On the robustness of quantum key distribution with classical Alice (photons-based protocol). In: Proceedings of the Ninth International Conference on Quantum, Nano/Bio, and Micro Technologies (ICQNM2015), Venice, Italy, pp. 29–34 (2015)
Zhang, X., Gong, W., Tan, Y., Ren, Z., Guo, X.: Quantum key distribution series network protocol with M-classical Bobs. Chin. Phys. B 18(6), 2143–2148 (2009)
Wang, J., Zhang, S., Zhang, Q., Tang, C.: Semiquantum key distribution using entangled states. Chin. Phys. Lett. 28(10), 100301–100304 (2011)
Kunfei, Y., Yang, C., Liao, C., Hwang, T.: Authenticated semi-quantum key distribution protocol using Bell states. Quantum Inf. Process. 13(6), 1457–1465 (2014)
Li, C., Kunfei, Y., Kao, S., Hwang, T.: Authenticated semi-quantum key distributions without classical channel. Quantum Inf. Process. 15(7), 2881–2893 (2016)
Meslouhi, A., Hassouni, Y.: Cryptanalysis on authenticated semi-quantum key distribution protocol using Bell states. Quantum Inf. Process. 16(1), 18 (2017)
Zou, X., Qiu, D., Zhang, S., Mateus, P.: Semiquantum key distribution without invoking the classical party’s measurement capability. Quantum Inf. Process. 14(8), 2981–2996 (2015)
Liu, Z., Hwang, T.: Mediated semi-quantum key distribution without invoking quantum measurement. Ann. Phys. 530, 1700206 (2018)
He, J., Li, Q., Wu, C., Chan, W., Zhang, S.: Measurement-device-independent semiquantum key distribution. Int. J. Quantum Inf. (2018). https://doi.org/10.1142/S0219749918500120
Zhang, M., Li, H., Peng, J., Feng, X.: Fault-tolerant semiquantum key distribution over a collective-dephasing noise channel. Int. J. Theor. Phys. 56(8), 1–12 (2017)
Boyer, M., Katz, M., Liss, R., Mor, T.: Experimentally feasible protocol for semiquantum key distribution. Phys. Rev. A 96, 62335 (2017)
Krawec, W.O.: Restricted attacks on semi-quantum key distribution protocols. Quantum Inf. Process. 13(11), 2417–2436 (2014)
Krawec, W.O.: Mediated semi-quantum key distribution. Phys. Rev. A 91(3), 032323 (2014)
Krawec, W.O.: Security proof of a semi-quantum key distribution protocol. In: Proceedings of 2015 IEEE International Symposium on Information Theory (ISIT2015), Hongkong, China, pp. 686–690 (2015)
Krawec, W.O.: Security of a semi-quantum protocol where reflections contribute to the secret key. Quantum Inf. Process. 15(5), 2067–2090 (2016)
Wang, X.: Decoy-state protocol for quantum cryptography with four different intensities of coherent light. Phys. Rev. A 72, 049908 (2005)
Lo, H.K., Ma, X., Chen, K.: Decoy state quantum key distribution. Phys. Rev. Lett. 94, 230504 (2005)
Guo, H., Li, Z., Peng, X.: Quantum Cryptography. National Defense Industry Press, Beijing (2016)
Acknowledgements
This work is supported by the National Natural Science Foundation of China (Grant Nos. 61871205, 61561033 and 61462061), the China Scholarship Council (Grant No. 201606825042), the Department of Human Resources and Social security of Jiangxi Province, the Major Discipline Academic and Technical Leader Training Plan Project of Jiangxi Province (Grant No. 20162BCB22011), and the Natural Science Foundation of Jiangxi Province (Grant No. 20171BAB202002).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Zhou, NR., Zhu, KN., Bi, W. et al. Semi-quantum identification. Quantum Inf Process 18, 197 (2019). https://doi.org/10.1007/s11128-019-2308-4
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-019-2308-4