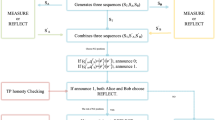
Abstract
Semi-quantum private comparison (SQPC) aims to compare the equality of the classical participants’ secrets with the help of a semi-honest TP, in which TP has full quantum capability while the classical participants’ quantum capability is limited. In the existing SQPC protocols, the entanglement resource (e.g., entangled state preparation and entangled state measurement) and pre-shared key are usually required. Besides, the qubit efficiency is relatively low. In this paper, we propose an efficient SQPC protocol based on single-particle states, in which the entanglement resource and pre-shared key are unnecessary. The qubit efficiency of our protocol is far greater than that of all existing SQPC protocols due to the use of single-particle states and circular transmission mode. Moreover, our protocol can be extended to the multi-party case, which can accomplish arbitrary pair’s comparison of equality among \(n(n\ge 2)\) classical participants. Finally, various kinds of attacks have been analyzed, which show that the proposed protocol is secure against the outside and inside attacks.

Similar content being viewed by others
References
Bennett, C,H., Brassard, G.: Quantum cryptography: public-key distribution and coin tossing. In: Proceedings of the IEEE International Conference on Computers, Systems and Signal Processing. Bangalore: IEEE Press, (1984), 175-179
Ekert, A.K.: Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett 67(6), 661–663 (1991)
Bennett, C.H., Brassard, G., Mermin, N.D.: Quantum cryptography without Bell theorem. Phys. Rev. Lett 68, 557–559 (1992)
Cabello, A.: Quantum key distribution in the Holevo limit. Phys. Rev. Lett 85, 5635 (2000)
Shor, P.W., Preskill, J.: Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett 85(2), 441 (2000)
Hillery, M., Bužek, V., Berthiaume, A.: Quantum secret sharing. Phys. Rev. A 59(3), 1829 (1999)
Xiao, L., Long, G.L., Deng, F.G., Pan, J.W.: Efficient multiparty quantum-secret-sharing schemes. Phys. Rev. A 69, 052307 (2004)
Deng, F.G., Zhou, H.Y., Long, G.L.: Circular quantum secret sharing. J. Phys. A: Math. Theor 39(45), 14089–14099 (2006)
Wang, T.Y., Wen, Q.Y., Chen, X.B., et al.: An efficient and secure multiparty quantum secret sharing scheme based on single photons. Optics. Communications 281(24), 6130–6134 (2008)
Yang, C.W., Tsai, C.W.: Efficient and secure dynamic quantum secret sharing protocol based on bell states. Quantum Inf. Process, 19(5) (2020)
Deng, F.G., Long, G.L., Liu, X,S.: Two-step quantum direct communication protocol using the Einstein-Podolsky-Rosen pair block. Phys. Rev. A, 68:042317 (2003)
Deng, F.G., Long, G.L.: Secure direct communication with a quantum one-time pad. Phys. Rev. A 69, 052319 (2004)
Chen, X.B., Wen, Q.Y., Guo, F.Z., Sun, Y., Xu, G., Zhu, F.C.: Controlled quantum secure direct communication with W state. Int. J. Quant. Inform 6(4), 899–906 (2008)
Chang, Y., Xu, C.X., Zhang, S.B., et al.: Controlled quantum secure direct communication and authentication protocol based on five-particle cluster state and quantum one-time pad. Chin. Sci. Bull 59(21), 2541–2546 (2014)
Giovannetti, V., Lloyd, S., Maccone, L.: Quantum private queries. Phys. Rev. Lett 100(23), 230502 (2008)
Jakobi, M., Simon, C., Gisin, N., et al.: Practical private database queries based on a quantum-key- distribution protocol. Phys. Rev. A 83, 022301 (2011)
Gao, F., Liu, B., Huang, W., Wen, Q.Y.: Postprocessing of the oblivious key in quantum private query. IEEE. J. Sel. Top. Quant 21, 6600111 (2015)
Wei, C.Y., Wang, T.Y., Gao, F.: Practical quantum private query with better performance in resisting joint- measurement attack. Phys. Rev. A 93, 042318 (2016)
Yao, A.C.: Protocols for secure computations. In: Proceedings of 23rd IEEE Symposium on Foundations of Computer Science (FOCS’82), Washington, DC, (1982), p.160
Yang, Y.G., Wen, Q.Y.: An efficient two-party quantum private comparison protocol with decoy photons and two-photon entanglement. J. Phys. A: Math and Theor 42(5), 055305 (2009)
Yang, Y.G., Gao, W.F., Wen, Q.Y.: Secure quantum private comparison. Phys. Scr 80(6), 065002 (2009)
Chen, X.B., Su, Y., Niu, X.X., Yang, Y.X.: Efficient and feasible quantum private comparison of equality against the collective amplitude damping noise. Quantum Inf. Process 13(1), 101–112 (2014)
Liu, B., Gao, F., Jia, H.Y., Huang, W., Zhang, W.W., Wen, Q.Y.: Efficient quantum private comparison employing single photons and collective detection. Quantum Inf. Process 12(2), 887–897 (2013)
Tseng, H.Y., Lin, J., Hwang, T.: New quantum private comparison protocol using EPR pairs. Quantum Inf. Process 11(2), 373–384 (2012)
Lin, J., Yang, C.W., Hwang, T.: Quantum private comparison of equality protocol without a third party. Quantum Inf. Process 13(2), 239–247 (2014)
Chen, X.B., Xu, G., Niu, X.X., Wen, Q.Y., Yang, Y.X.: An efficient protocol for the private comparison of equal information based on the triplet entangled state and single-particle measurement. Opt. Commun 283(7), 1561–1565 (2010)
Chang, Y.J., Tsai, C.W., Hwang, T.: Multi-user private comparison protocol using GHZ class states. Quantum Inf. Process 12(2), 1077–1088 (2013)
Liu, W., Wang, Y.B., Jiang, Z.T.: An efficient protocol for the quantum private comparison of equality with W state. Opt. Commun 284(12), 3160–3163 (2011)
Li, J., Zhou, H.F., Jia, L., Zhang, T.T.: An efficient protocol for the private comparison of equal information based on four-particle entangled W state and Bell entangled states swapping. Int. J. Theor. Phys 53(7), 2167–2176 (2014)
Zhang, W.W., Li, D., Li, Y.B.: Quantum private comparison protocol with W states. Int. J. Theor. Phys 53(5), 1723–1729 (2014)
Xu, G.A., Chen, X.B., Wei, Z.H., Li, M.J., Yang, Y.X.: An efficient protocol for the quantum private comparison of equality with a four-qubit cluster state. Int. J. Quant. Inform 10(4), 1250045 (2012)
Li, C.Y., Chen, X.B., et al.: Efficient quantum private comparison protocol based on the entanglement swapping between four-qubit cluster state and extended Bell state. Quantum Inf. Process, 18(5) (2019)
Ye, T.Y., Ji, Z.X.: Multi-user quantum private comparison with scattered preparation and one-way convergent transmission of quantum states. Sci. China Phys. Mech. Astron. 60(9), 090312 (2017)
Hung, S.M., Hwang, S.L., Hwang, T., Kao, S.H.: Multiparty quantum private comparison with almost dishonest third parties for strangers. Quantum Inf. Process 16(2), 36 (2017)
Wang, Q.L., Sun, H.X., Huang, W.: Multi-party quantum private comparison protocol with n-level entangled states. Quantum Inf. Process 13(11), 2375–2389 (2014)
Ye, C.Q., Ye, T.Y.: Circular Multi-party quantum private comparison with-level single-particle states. Int. J. Theor. Phys 58(4), 1282–1294 (2019)
Lo, H.K.: Insecurity of quantum secure computations. Phys. Rev. A 56(2), 1154–1162 (1997)
Boyer, M., Kenigsberg, D., Mor, T.: Quantum key distribution with classical Bob. Phys. Rev. Lett 99(14), 140501 (2007)
Boyer, M., Gelles, R., Kenigsberg, D., Mor, T.: Semiquantum key distribution. Phys. Rev. A 79(3), 032341 (2009)
Lu, H., Cai, Q.Y.: Quantum key distribution with classical Alice. Int. J. Quant. Inform 6(6), 1195–1202 (2008)
Zou, X.F., Qiu, D.W., Li, L.Z., Wu, L.H., Li, L.J.: Semiquantum-key distribution using less than four quantum states. Phys. Rev. A 79(5), 052312 (2009)
Sun, Z.W., Du, R.G., Long, D.Y.: Quantum key distribution with limited classical Bob. Int. J. Quant. Inform 11(1), 1350005 (2003)
Zou, X.F., Qiu, D.W., Zhang, S.Y., Mateus, P.: Semiquantum key distribution without invoking the classical party’s measurement capability. Quantum Inf. Process 14(8), 2981–2996 (2015)
Krawec, W.O.: Restricted attacks on semi-quantum key distribution protocols. Quantum Inf. Process 13(11), 2417–2436 (2014)
Krawec, W.O.: Security of a semi-quantum protocol where reflections contribute to the secret key. Quantum Inf. Process 15(5), 2067–2090 (2016)
Krawec, W.O.: Mediated semi-quantum key distribution. Phys. Rev. A 91(3), 032323 (2015)
Zou, X.F., Qiu, D.W.: Three-step semiquantum secure direct communication protocol. Sci. China-Phys Mech. Astron 57(9), 1696–1702 (2014)
Luo, Y.P., Hwang, T.: Authenticated semi-quantum direct communication protocols using Bell states. Quantum Inf. Process 15(2), 947–958 (2016)
Zhang, M.H., Li, H.F., Xia, Z.Q., et al.: Semiquantum secure direct communication using EPR pairs. Quantum Inf. Process 16(5), 117 (2017)
Li, Q., Chan, W.H., Long, D.Y.: Semiquantum secret sharing using entangled states. Phys. Rev. A 82(2), 022303 (2010)
Wang, J., Zhang, S., Zhang, Q., et al.: Semiquantum secret sharing using two-particle entangled state. Int. J. Quantum Inf 10(5), 1250050 (2012)
Li, L.Z., Qiu, D.W., Mateus, P.: Quantum secret sharing with classical Bobs. J. Phys. A Math. Theor 46(4), 045304 (2013)
Lin, J., Yang, C.W., Tsai, C.W., et al.: Intercept-resend attacks on semi-quantum secret sharing and the improvements. Int. J. Theor. Phys 52(1), 156–162 (2013)
Yang, C.W., Hwang, T.: Efficient key construction on semi-quantum secret sharing protocols. Int. J. Quant. Inform 11(5), 1350052 (2013)
Gao, G., Wang, Y., Wang, D.: Multiparty semiquantum secret sharing based on rearranging orders of qubits. Mod. Phys. Lett. B 30(10), 1650130 (2016)
Li, Z., Li, Q., Liu, C., et al.: Limited resource semiquantum secret sharing. Quantum Inf. Process 17(10), 1–11 (2018)
Chou, W.H., Hwang, T., Gu, J.: Semi-quantum private comparison protocol under an almost-dishonest third party. http://arxiv.org/pdf/quant-ph/160707961.pdf
Thapliyala, K., Sharmab, R.D., Pathak, A.: Orthogonal-state-based and semi-quantum protocols for quantum private comparison in noisy environment. Int. J. Quant. Inform, (2016)
Jiang, L.-Z.: Semi-Quantum Private Comparison Based on Bell States. Quantum Inf. Process 19(6), 180 (2020)
Ye, T.Y., Ye, C.Q.: Measure-Resend Semi-Quantum Private Comparison Without Entanglement. Int. J. Theor. Phys 57(12), 3819–3834 (2018)
Lin, P.H., Hwang, T., Tsai, C.W.: Efficient semi-quantum private comparison using single photons. Quantum Inf. Process. 18, 207 (2019)
Yan, L.L., Zhang, S.B., Chang,Y., et al.: Semi-quantum private comparison protocol with three-particle G-like states. Quantum Inf. Process, 20(1), (2021)
Beveratos, A., Brouri, R., Gacoin, T., Villing, A., Poizat, J.-P., Grangier, P.: Single photon quantum cryptography. Phys. Rev. Lett 89(18), 187901 (2002)
Diamanti, E., Lo, H.-K., Qi, B., Yuan, Z.: Practical challenges in quantum key distribution. Npj. Quantum. Inf 2, 16025 (2016)
Hwang, W.Y.: Quantum key distribution with high loss: toward global secure communication. Phys. Rev. Lett 91(5), 057901 (2003)
Lo, H.K., Ma, X., Chen, K.: Decoy state quantum key distribution. Phys. Rev. Lett 94(23), 230504 (2005)
Wang, X.B.: Beating the photon-number-splitting attack in practical quantum cryptography. Phys. Rev. Lett 94(23), 230503 (2005)
Rosenberg, D., Harrington, J.W., Rice, P.R., Hiskett, P.A., Peterson, C.G., Hughes, R.J., Lita, A.E., Nam, S.W., Nordholt, J.E.: Long-distance decoy-state quantum key distribution in optical fiber. Phys. Rev. Lett 98(1), 010503 (2007)
Song, X.L., Liu, Y.B., Deng, H.Y., Xiao, Y.G.: (t, n) threshold d-level quantum secret sharing. Sci. Rep. 7(1), 6366 (2017)
Acknowledgements
This work was supported by the National Natural Science Foundation of China (Grant Nos. U1636106, 61671087 and 61962009), the Natural Science Foundation of Beijing Municipality (Grant No. 4182006), the BUPT Excellent Ph.D Students Foundation (Grant No. CX2021117) and the Fund of the Fundamental Research Funds for the Central Universities (Grant No. 2019XD-A02).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Chongqiang, Y., Jian, L., Xiubo, C. et al. Efficient semi-quantum private comparison without using entanglement resource and pre-shared key. Quantum Inf Process 20, 262 (2021). https://doi.org/10.1007/s11128-021-03194-x
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-021-03194-x