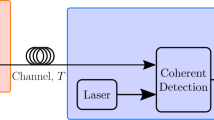
Abstract
Finite sampling bandwidth of analog-to-digital converter (ADC) has an effect on performance of continuous-variable quantum key distribution (CVQKD). The matter results in a considerable decrease in performance and leaves the practical security of the system, brought on by a safe loophole exploited by eavesdropper to launch the potential attacks. The linear relationship between secret key rate and repetition frequency is thus restrained from this challenge. To seek and deal with such a loophole in CVQKD with discrete modulation, we suggest a dual sampling detection approach that involves two ADCs in data processing. Security analysis shows that the performance of the discretely modulated (DM) CVQKD system can be improved in terms of the secret key rate and maximal transmission distance. The practical security of DM CVQKD is therefore demonstrated, thereby providing a theoretical proof for applying the DM CVQKD system to a realistic environment.





Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.References
Grosshans, F., Grangier, P.: Continuous variable quantum cryptography using coherent states. Phys. Rev. Lett. 88(5), 057902 (2002)
Grosshans, F., Van Assche, G., Wenger, J., Brouri, R., Cerf, N.J., Grangier, P.: Quantum key distribution using gaussian-modulated coherent states. Nature 421, 238–241 (2003)
Weedbrook, C., Lance, A.M., Bowen, W.P., Symul, T., Ralph, T.C., Lam, P.K.: Quantum cryptography without switching. Phys. Rev. Lett. 93, 170504 (2004)
Scarani, V., Bechmann-Pasquinucci, H., Cerf, N.J., Dušek, M., Lütkenhaus, N., Peev, M.: The security of practical quantum key distribution. Rev. Mod. Phys. 81(3), 1301 (2009)
Lance, A.M., Symul, T., Sharma, V., Weedbrook, C., Ralph, T.C., Lam, P.K.: No-switching quantum key distribution using broadband modulated coherent light. Phys. Rev. Lett. 95(18), 180503 (2005)
Lodewyck, J., Bloch, M., García-Patrón, R., Fossier, S., Karpov, E., Diamanti, E., Debuisschert, T., Cerf, N.J., Tualle-Brouri, R., McLaughlin, Steven W., McLaughlin, S.W., Grangier, P.: Quantum key distribution over 25 km with an all-fiber continuous-variable system. Phys. Rev. A 76(4), 042305 (2007)
Gisin, N., Ribordy, G., Tittel, W., Zbinden, H.: Quantum cryptography. Rev. Mod. Phys. 74(1), 145 (2002)
Braunstein, S.L., Van Loock, P.: Quantum information with continuous variables. Rev. Mod. Phys. 77, 513577 (2005)
Laudenbach, F., Pacher, C., Fung, C.H.F., Poppe, A., Peev, M., Schrenk, B., Hentschel, M., Walther, P., Hübel, H.: Continuous-variable quantum key distribution with gaussian modulation - the theory of practical implementations. Adv. Quantum Technol. 1, 1800011 (2018)
Scarani, V., Renner, R.: Quantum cryptography with finite resources: unconditional security bound for discrete-variable protocols with one-way postprocessing. Phys. Rev. Lett. 100(20), 200501 (2008)
Sano, Y., Matsumoto, R., Uyematsu, T.: Secure key rate of the BB84 protocol using finite sample bits. Phys. Math. Theor. 43(49), 495302 (2010)
Lo, H.K., Curty, M., Tamaki, K.: Secure quantum key distribution. Nat. Photon. 8(8), 595604 (2014)
Quezada, L.F., Dong, S.H.: Quantum key-distribution protocols based on a quantum version of the monty hall game. Annalen der Physik 532(6), 2000126 (2020)
Quezada, L.F., Dong, S.H.: Quantum version of a generalized Monty Hall game and its possible applications to quantum secure communications. Annalen der Physik 533(1), 2000427 (2021)
Liao, Q., Xiao, G., Xu, C.G., Xu, Y., Guo, Y.: Discretely modulated continuous-variable quantum key distribution with an untrusted entanglement source. Phys. Rev. A 102(3), 032604 (2020)
Gottesman, D., Preskill, J.: Secure quantum key distribution using squeezed states. Phys. Rev. A 63(2), 022309 (2001)
Usenko, V.C., Grosshans, F.: Unidimensional continuous-variable quantum key distribution. Phys. Rev. A 92(6), 062337 (2015)
Guo, Y., Liao, Q., Huang, D., Zeng, G.: Quantum relay schemes for continuous-variable quantum key distribution. Phys. Rev. A 95(4), 042326 (2017)
Pirandola, S., Ottaviani, C., Spedalieri, G., Weedbrook, C., Braunstein, S.L., Lloyd, S., Gehring, T., Jacobsen, C.S., Andersen, U.L.: High-rate measurement-device-independent quantum cryptography. Nat. Photon. 9(6), 397–402 (2015)
Casta\({\widetilde{n}}\)eda Valle, D., Quezada, L. F., Dong, S. H.: Bell-GHZ measurement-device-independent quantum key distribution. Annalen der Physik 533(9), 2100116 (2021)
Becir, A., El-Orany, F.A.A., Wahiddin, M.R.B.: Performance improvement of eight-state continuous-variable quantum key distribution with an optical amplifier. Int. J. Quantum Inf. 10(01), 12500041 (2010)
Leverrier, A., Grangier, P.: Unconditional security proof of long-distance continuous-variable quantum key distribution with discrete modulation. Phys. Rev. Lett. 102(18), 180504 (2008)
Ma, X.C., Sun, S.H., Jiang, M.S., Liang, L.M.: Local oscillator fluctuation opens a loophole for Eve in practical continuous-variable quantum-key-distribution systems. Phys. Rev. A 88(2), 022339 (2013)
Jouguet, P., Kunz-Jacques, S., Diamanti, E.: Preventing calibration attacks on the local oscillator in continuous-variable quantum key distribution. Phys. Rev. A 87(6), 062313 (2013)
Huang, J.Z., Weedbrook, C., Yin, Z.Q., Wang, S., Li, H.W., Chen, W., Guo, G.C., Han, Z.F.: Quantum hacking of a continuous-variable quantum-key-distribution system using a wavelength attack. Phys. Rev. A 87(6), 062329 (2013)
Ma, X.C., Sun, S.H., Jiang, M.S., Liang, L.M.: Wavelength attack on practical continuous-variable quantum-key-distribution system with a heterodyne protocol. Phys. Rev. A 87(5), 052309 (2013)
Qin, H., Kumar, R., Alléaume, R.: Quantum hacking: saturation attack on practical continuous-variable quantum key distribution. Phys. Rev. A 94(1), 012325 (2016)
Wang, C., Huang, P., Huang, D., Lin, D., Zeng, G.: Practical security of continuous-variable quantum key distribution with finite sampling bandwidth effects. Phys. Rev. A 93(2), 022315 (2016)
Qin, H., Kumar, R., Makarov, V., Alléaume, R.: Homodyne-detector-blinding attack in continuous-variable quantum key distribution. Phys. Rev. A 98(1), 012312 (2018)
Xie, C., Guo, Y., Liao, Q., Zhao, W., Huang, D., Zhang, L., Zeng, G.: Practical security analysis of continuous-variable quantum key distribution with jitter in clock synchronization. Phys. Lett. A 382(12), 811–817 (2018)
Zhao, Y., Zhang, Y., Huang, Y., Xu, B., Yu, S., Guo, H.: Polarization attack on continuous-variable quantum key distribution. J. Phys. B 52(1), 015501 (2018)
Kunz-Jacques, S., Jouguet, P.: Robust shot-noise measurement for continuous-variable quantum key distribution. Phys. Rev. A 91(2), 022307 (2015)
Wang, T., Huang, P., Zhou, Y., Liu, W., Zeng, G.: Practical performance of real-time shot-noise measurement in continuous-variable quantum key distribution. Quant. Info. Proc. 17(1), 1–16 (2018)
Huang, D., Huang, P., Lin, D., Wang, C., Zeng, G.: High-speed continuous-variable quantum key distribution without sending a local oscillator. Opt. Lett. 40(16), 3695–3698 (2015)
Soh, D.B., Brif, C., Coles, P.J., Lütkenhaus, N., Camacho, R.M., Urayama, J., Sarovar, M.: Self-referenced continuous-variable quantum key distribution protocol. Phys. Rev. X 5(4), 041010 (2015)
Qi, B., Lougovski, P., Pooser, R., Grice, W., Bobrek, M.: Generating the local oscillator “locally” in continuous-variable quantum key distribution based on coherent detection. Phys. Rev. X 5(4), 041009 (2015)
Wang, T., Huang, P., Zhou, Y., Liu, W., Ma, H., Wang, S., Zeng, G.: High key rate continuous-variable quantum key distribution with a real local oscillator. Opt. Exp. 26(3), 2794–2806 (2018)
Wang, T., Huang, P., Zhou, Y., Liu, W., Zeng, G.: Pilot-multiplexed continuous-variable quantum key distribution with a real local oscillator. Phys. Rev. A 97(1), 012310 (2018)
Li, Z., Zhang, Y.C., Xu, F., Peng, X., Guo, H.: Continuous-variable measurement-device-independent quantum key distribution. Phys. Rev. A 89(5), 052301 (2014)
Sych, D., Leuchs, G.: Coherent state quantum key distribution with multi letter phase-shift keying. New J. Phys. 12(5), 053019 (2010)
Huang, D., Fang, J., Wang, C., Huang, P., Zeng, G.H.: A 300-MHz bandwidth balanced homodyne detector for continuous variable quantum key distribution. Chin. Phys. Lett. 30(11), 114209 (2013)
Chi, Y.M., Qi, B., Zhu, W., Qian, L., Lo, H.K., Youn, S.H., Lvovsky, A.I., Tian, L.: A balanced homodyne detector for high-rate Gaussian-modulated coherent-state quantum key distribution. New J. Phys. 13(1), 013003 (2011)
Hansen, H., Aichele, T., Hettich, C., Lodahl, P., Lvovsky, A.I., Mlynek, J., Schiller, S.: Ultrasensitive pulsed, balanced homodyne detector: application to time-domain quantum measurements. Opt. Lett. 26(21), 1714–1716 (2001)
Leverrier, A., Grangier, P.: Continuous-variable quantumkey-distribution protocols with a non-Gaussian modulation. Phys. Rev. A 83, 042312 (2011)
Liao, Q., Liu, H., Zhu, L., Guo, Y.: Quantum secret sharing using discretely modulated coherent states. Phys. Rev. A 103(3), 032410 (2021)
Liao, Q., Xiao, G., Zhong, H., Guo, Y.: Multi-label learning for improving discretely-modulated continuous-variable quantum key distribution. New J. Phys. 22, 083086 (2020)
Liao, Q., Xiao, G., Xu, C., Xu, Y., Guo, Y.: Discretely-modulated continuous-variable quantum key distribution with untrusted entanglement source. Phys. Rev. A 102, 032604 (2020)
Hu, J., Liao, Q., Mao, Y., Guo, Y.: Performance improvement of unidimensional continuous-variable quantum key distribution using zero-photon quantum catalysis. Quant. Info. Proc. 20(1), 1–20 (2021)
Acknowledgements
This work is supported by the National Natural Science Foundation of China (Grant No. 61871407), the Natural Science Foundation of Hunan Province (Grant No. 2021JJ30878), and the Special Funds for the Construction of an Innovative Province in Hunan (Grant No. 2020GK4063).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix
Appendix
1.1 A Discrete Fourier transformation of the signal
Sampling is a process where continuous signal is converted to a discrete sequence of values. By periodically sampling continuous signal, the discrete signal is thus derived. Practical sampling frequency and sampling duration of on-off keying (OOK) are finite. Given the finite sampling frequency, it is likely that information loss introduced by sample interval may leave a loophole, exploited by the eavesdropper.
Generally, with regard to finite-pulse-width sampling system, sampling duration tends to be too short to have effects on the performance of on-off keying. The sampling duration is even shorter than sampling period, so the former approaches zero. Under such circumstance, the sampling process is therefore regarded as amplitude modulation. The theoretical sampler functions as amplitude modulation with carrier wave \(\delta _T(t)\), which represents unit impulse sequence. After amplitude modulation, the carrier wave then carries the information of continuous signal. Each unit impulse duration approaches zero, the intensity of which mainly depends on the instantaneous amplitude. Therefore, the amplitude modulation is depicted as follows:
The unit impulse sequence is written as follows:
where \(\delta (t-nT)\) represents unit impulse when \(t=nT\). e(t) can be rewritten as
The corresponding instantaneous modulated amplitude is shown as follows,
Under the condition of the causal system in practice, we suppose that the impulse sequence is casual signal, namely \(e(t)=0, \forall t<0\). By Laplace transforming sampling signal \(e^*(t)\), the modulated amplitude is rewritten as follows:
According to the displacement theorem of Laplace transformation, the impulse can be rewritten as
As for modulated sampling signal, we can then derive it after Laplace transformation,
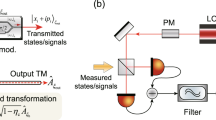
As a result, each instantaneous sampling signal can be derived above. As long as the sampling frequency is satisfactory, there is a slim chance that lots of information is lost before signal rebuilding. From Fig. 1b, we can draw a conclusion that it is though to sample the peak value. There exists the deviation to the peak value when measuring the voltage, which, obviously, has effects on the secret key rate and transmission distance. The reason why there is an obvious drop of the secret key rate and transmission distance is that the extra electrical noise is introduced by practical ADC. In the time domain, we can visually explore the deviation between measured value and peak value due to finite sampling frequency.
To demonstrate the deviation in the frequency domain, we then analyze the frequency spectrum of the sampling signal. As is mentioned above, it is because of information loss resulting from finite sampling frequency that the frequency spectrum of continuous signal varies a lot after sampling.
In order to better illustrate the principle in the frequency domain, we take the frequency spectrum of arbitrary sampling signal as an example. Unit impulse sequence is a periodical function, the expansion of which can be rewritten as follows:
where \(\omega _s=2\pi /t\) represents sampling angular frequency, and \(c_n\) represents Laplace coefficient, namely
According to the definition of the unit impulse, only when \(t=0\) is the value equal to unit value. We thus further simplify the calculation of \(c_n\)0 as
Then Eq. 18 can also be rewritten as follows:
The following equation is therefore derived,
By Laplace transforming the aforementioned equation, we can easily obtain
Suppose that there are no poles in the half-right plane (HRP) for the purpose of a stable system, we therefore assume that \(s=j\omega \). Finally, we Laplace transform the sampling signal \(e^*(t)\), namely
Generally, we can see that the frequency spectrum of continuous signal is continuous. \(\omega _h\) represents the maximal angular frequency, while \(\omega _h\) represents infinite period of repetition frequency introduced by sampling signal. When \(n=0\), the frequency spectrum shapes like that of continuous signal. With the increase in angular frequency, it may lead to frequency aliasing. Generally, given the finite sampling frequency of ADC, it sometimes may not meet our needs, especially when \(\omega _s<2\omega _h\) the frequency spectrum of original continuous signal and sampling signal overlaps. Unfortunately, due to signal distortion, the continuous signal can by no means be rebuilt any more even with the help of filters. Therefore, we finally draw a conclusion that in case of signal distortion, \(\omega _s<2\omega _h\) is a necessary condition when choosing ADC.
As for the aforementioned practical homodyne or heterodyne detector, the field of quadrature value is proportional to the output signal of each impulse. As seen in Fig. 1b, we may conclude that sufficient sampling points should be guaranteed and integrated for each impulse. To overcome the obstacle which brings more challenges to data processing, it is assumed that impulse duration is much shorter than sampling. Therefore, the shape of homodyne or heterodyne detection depends on deriving response function. Based on the above assumption, the quadrature is linearly proportional to the maximal value of homodyne or heterodyne detection.
To assume the each output impulse shapes like Gaussian function, described as
where \(U_p\) represents the maximal value of each Gaussian impulse, \(\mu \) is the mean, and \(\sigma ^2\) represents variance.
As for the ideal CVQKD scheme, the maximal value of each Gaussian impulse is therefore measured, after which the measured quadrature is linearly proportional to the maximal value. Unfortunately, finite sampling bandwidth leads to the deviation to the peak value, as seen in Fig. 1b. \(t_s\) represents sampling duration, and the sampling bandwidth is described as \(f_{samp}=1/t_s\ Hz\). The maximal discrepancy between the maximal value and the measured value is described as
and the ratio between \(U_m\) and \(U_p\) is defined by
which shows that the defined ratio is related to sampling bandwidth and repetition frequency.
1.2 B Derivation of covariance matrixes
In this section, after discrete modulation, the mixture state \(\rho _4\) can be expressed as
We have known that the mode A and the mode B denote the measurements of coherent states detected by Alice and Bob, respectively. Then, we derive the following covariance matrix \(\Gamma _{AB}^4\) of the bipartite state \(|\Psi \rangle _4\),
where \({\mathbb {I}}\) and \(\sigma _z\) represent the diagonal matrix diag(1,1) and diag(1,-1), respectively.
To acquire the analytical expression of security key rate, we propose the covariance matrix \(\Gamma _{AB_1}\) of the inequivalent EB-based version of our scheme after passing through the public quantum channel. Firstly, the covariance matrix of the EPR-state that Alice prepared can be given by the following expression,
where \(C_1=\sqrt{T}Z_4\), \(V_{B_1}=T(V_B+\chi _{line})\) with \(\chi _{line}=1/T-1+\xi \). The covariance matrix can then be derived as follows:
with
where \(\chi _{det}=(1-\eta +\xi _{el})\eta \) for homodyne detection and \(\chi _{det}=(2-\eta +2\xi _{el})\eta \) for heterodyne detection. In addition, to obtain the covariance matrix of the eight-state DM CVQKD protocol, we shall only replace \(Z_4\) with \(Z_8\).
1.3 C Calculation of the secret key rate
In this section, the secret key rate analysis is mainly carried out under Gaussian collective attacks, simply because they are proved to be optimal in asymptotic cases. Additionally, the asymptotic security analysis has already been proved, while the finite-size and composable security analysis has not been proved. We now calculate the secret key rate of Four-state and Eight-state DM CVQKD.
As mentioned in Sect. 3, four-state and eight-state protocols are suggested in the scheme. Alice sends one of the coherent states to Bob, the possibility of which is 1/4 or 1/8. Alice discretely modulates the coherent states into four or eight states.
To obtain the lower bound of the secret key rate, the covariance matrix in the asymptotic framework thus should be derived. The secret key rate in the case of asymptotic security for heterodyne detection reads
while the secret key rate for homodyne detection reads as follows:
where \(\beta \) is the reconciliation efficiency, \(I_{AB}\) refers to the mutual information shared by both Alice and Bob, and \(\chi _{BE}\) represents the Holevo bound between Bob and Eve for reverse reconciliation. The mutual information can be derived by the following expression
where \(V_A=(V+1)/2\), is the amplitude quadrature variance for Alice, which is the first element of matrix \(\gamma _A\) describing mode A, and \(V_{A|B}=V_A-C^2/{(2V_B^2)}\), while the first diagonal element of conditional matrix \(\gamma _{A|B}\), and \(V_{A|B}\) which represents conditional variance in amplitude quadrature, is given by
where MP presents the Moore-Penrose matrix inverse; \(\gamma _A\), \(\gamma _B\) and \(\sigma _{AB}\) refer to submatrices of the covariance matrix \(\gamma _{AB}\) by decomposition, namely
where X and \(\gamma _{AB}\) can be obtained in Ref. [48].
Lossy information available for Eve can be obtained by
where \(S(\rho )\) is the Von Neumann entropy of the quantum state \(\rho \). The calculation of symplectic eigenvalues of covariance matrix \(\gamma \) is applied to evaluate entropy for an n-mode Gaussian state describing \(\rho \) as follows:
where G(x) can also be obtained in Ref. [48].
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Hu, J., Wang, Y., Mao, Y. et al. Finite sampling bandwidth effect on practical security of discretely modulated continuous-variable quantum key distribution. Quantum Inf Process 22, 35 (2023). https://doi.org/10.1007/s11128-022-03781-6
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-022-03781-6