Abstract
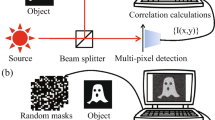
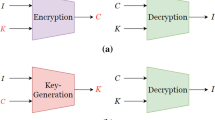
Visual cryptography is a potentially important technique for optical information security. However, the limitations of carrier materials and the high precision requirements of the reconstruction process limit the application scope of visual cryptography. Herein, we propose a novel visual cryptography technique based on ghost imaging. The spatial information on one visual key image is encoded into time-varying factors in ghost imaging and loaded onto Hadamard illumination patterns. The secret image can be recovered when the illumination patterns are projected onto another visual key image. This method utilizes light-intensity superposition to overlap visual key image pixels. Simulation and experimental results substantiate the feasibility and security of the proposed technique. This method incorporates the unique advantages of ghost imaging and visual cryptography and is not limited by carrier materials and precision. Hence, it has high scalability and broad application scenarios in ghost imaging broadcasting systems and information authentication, among others.













Similar content being viewed by others
Data availability
All data generated or analyzed during this study are included in this published article.
References
Li, J.X., Kamin, S., Zheng, G., Neubrech, F., Zhang, S., Liu, N.: Addressable metasurfaces for dynamic holography and optical information encryption. Sci. Adv. 4(6), eaar6768 (2018)
Liu, Z., Guo, Q., Xu, L., Ahmad, M., Liu, S.: Double image encryption by using iterative random binary encoding in gyrator domains. Opt. Express 18(11), 12033–12043 (2010)
Peng, D., Huang, Z.F., Liu, Y.L., Chen, Y.H., Wang, F., Ponomarenko, S.A., Cai, Y.J.: Optical coherence encryption with structured random light. PhotoniX 2(1), 1–15 (2021)
Duan, C.F., Zhou, J., Gong, L.H., Wu, J.Y., Zhou, N.R.: New color image encryption scheme based on multiple-parameter fractional discrete Tchebyshev moments and nonlinear fractal permutation method. Opt. Lasers Eng. 150, 106881 (2022)
Naor, M., Shamir, A.: Visual cryptography. In: Advance in Cryptology Euro Crypt’94. Lecture Notes in Computer Science, vol. 950, pp. 1–12. Springer, Berlin (1995)
Yan, B., Xiang, Y., Hua, G.: Improving the visual quality of size-invariant visual cryptography for grayscale images: an analysis-by-synthesis (AbS) approach. IEEE Trans. Image Process. 28(2), 896–911 (2018)
Wu, X., Yang, C.N.: A combination of color-black-and-white visual cryptography and polynomial based secret image sharing. J. Vis. Commun. Image Represent. 61, 74–84 (2019)
Yamamoto, H., Hayasaki, Y., Nishida, N.: Secure information display with limited viewing zone by use of multi-color visual cryptography. Opt. Express 12(7), 1258–1270 (2004)
Yang, N., Gao, Q., Shi, Y.: Visual-cryptographic image hiding with holographic optical elements. Opt. Express 26(24), 31995–32006 (2018)
Li, Z., Dong, G., Yang, D., Yang, G., Shi, S., Bi, K., Zhou, J.: Efficient dielectric metasurface hologram for visual-cryptographic image hiding. Opt. Express 27(14), 19212–19217 (2019)
Lu, D., Liao, M., He, W., Xing, Q., Verma, G., Peng, X.: Experimental optical secret sharing via an iterative phase retrieval algorithm. Opt. Lasers Eng. 126, 105904 (2020)
Shi, Y., Yang, X.: Optical hiding with visual cryptography. J. Opt. 19(11), 115703 (2017)
Jiao, S., Feng, J., Gao, Y., Lei, T., Yuan, X.: Visual cryptography in single-pixel imaging. Opt. Express 28(5), 7301–7313 (2020)
Pittman, T.B., Shih, Y.H., Strekalov, D.V., Segienko, A.: Optical imaging by means of two-photon quantum entanglement. Phys. Rev. A 52(5), R3429–R3432 (1995)
Bromberg, Y., Katz, O., Silberberg, Y.: Ghost imaging with a single detector. Phys. Rev. A 79(5), 1744–1747 (2008)
Gong, W.: High-resolution pseudo-inverse ghost imaging. Photon. Res. 3, 234–237 (2015)
Lyu, M., Wang, W., Wang, H., Wang, H., Li, G., Chen, N., Situ, G.: Deep-learning-based ghost imaging. Sci. Rep. 7(1), 17865 (2017)
Daniele, F.: Optical communications: temporal ghost imaging. Nat. Photon. 10(3), 150–152 (2016)
Meng, W., Shi, D., Yuan, K., Zha, L., Huang, J., Wang, Y., Fan, C.: Fourier-temporal ghost imaging. Opt. Lasers Eng. 134, 106294 (2020)
Clemente, P., Durán, V., Torres-Company, V., Tajahuerce, E., Lancis, J.: Optical encryption based on computational ghost imaging. Opt. Lett. 35(14), 2391–2393 (2010)
Kang, Y., Zhang, L., Ye, H., Zhao, M., Kanwal, S., Bai, C., Zhang, D.: One-to-many optical information encryption transmission method based on temporal ghost imaging and code division multiple access. Photon. Res. 7(12), 1370–1380 (2019)
Huang, X., Nan, S., Tan, W., Bai, Y., Fu, X.: Ghost imaging influenced by a supersonic wind-induced random environment. Opt. Lett. 46(5), 1009–1012 (2021)
Zhang, A.X., He, Y.H., Wu, L.A.: Tabletop x-ray ghost imaging with ultra-low radiation. Optica 5(4), 374–377 (2018)
Balakin, D.A., Belinsky, A.V.: Extraction of additional information during quantum ghost imaging and its processing. Quantum Inf. Process. 19, 316 (2020)
Wang, L., Zhao, S.: Fast reconstructed and high-quality ghost imaging with fast Walsh-Hadamard transform. Photon. Res. 4(6), 240–244 (2016)
Zhang, Z., Wang, X., Zheng, G., Zhong, J.: Hadamard single-pixel imaging versus Fourier single-pixel imaging. Opt. Express 25(16), 19619–19639 (2017)
Ye, Z., Wang, H., Xiong, J., Wang, K.: Simultaneous full-color single-pixel imaging and visible watermarking using Hadamard-Bayer illumination patterns. Opt. Lasers Eng. 127, 105955 (2020)
Chen, C., Yang, H.: Correlation between turbulence-impacted optical signals collected via a pair of adjacent spatial-mode receivers. Opt. Express 28, 14280–14299 (2020)
Huanga, Z.W., Zhou, N.R.: An image encryption scheme based on discrete cosine Stockwell transform and DNA-level modulus diffusion. Opt Laser Technol. 149, 107879 (2022)
Kang, Y., Zhang, L., Zhang, D.: Optical encryption based on ghost imaging and public key cryptography. Opt. Lasers Eng. 111, 58–64 (2018)
Li, F., Zhao, M., Tian, Z., Willomitzer, F., Cossairt, O.: Compressive ghost imaging through scattering media with deep learning. Opt. Express 28, 17395–17408 (2020)
Wang, F., Wang, H., Wang, H., Li, G., Situ, G.: Learning from simulation: an end-to-end deep-learning approach for computational ghost imaging. Opt. Express 27, 25560–25572 (2019)
Acknowledgements
The authors are indebted to the anonymous referees for their instructive comments and suggestions.
Funding
This research was funded by the National Natural Science Foundation of China (Grant No. 62205207).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
All authors certify that they have no affiliations with or involvement in any organization or entity with any financial interest or non-financial interest in the subject matter or materials discussed in this manuscript.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix
Appendix
Two visual cryptography schemes are described in this paper. One extends secret images into two meaningless images while in the other, secret images can be composed of two meaningful images. These two coding methods are described as follows.
1.1 A. The (2,2) visual cryptographic coding scheme
In this scheme, a secret image is extended into two meaningless images. Any image cannot get information about the secret image. The secret image can be obtained only if the two images are superimposed together. The operation of encryption and decryption is shown in Fig.
14.
We first process the secret image in pixels, and each pixel is divided into two shared blocks. The separation rule is shown in Table
2.
When a pixel in the secret image is a white pixel, we can randomly select a combination mode of white pixels as presented in Table 1. The two shared blocks contain two subpixels, one black and one white, and the results are also black and white when two shared blocks are superimposed. When a pixel is black, we randomly choose the combination mode but the superposition result is black. Thus, the secret image is extended into two shared images. Because of the random selection, each black or white pixel in the secret image is encrypted into two subpixels (one black and one white) in the shared image, so it is not possible to obtain any information on the secret image from the shared image. The information on the secret image can only be obtained in the case of overlapping of the two shared images.
In this rule, one pixel in the secret image is expanded into two subpixels, so the shared image is twice as large as the secret image. For instance, when the size of the secret image is \(128 \times 128\) pixels, the size of the shared image is \(128 \times 256\) pixels. One pixel can also be expanded into 4, 8, or 16 subpixels according to this rule. In this study, one pixel is expanded into 4 subpixels.
1.2 B. An enhanced visual-cryptographic coding scheme
In this coding scheme, multiple shared images are generated based on the secret image and mask images, and the shared image is a halftone image generated after encoding the mask image. When multiple shared images overlap, the secret image can be recovered.
We encode the image as a halftone image and the grayscale value of each pixel in the image determines the number of black and white pixels in the halftone image’s subpixels. We divide the grayscale values of the image into different levels. Herein, they are divided into 16 levels (the grayscale value of 0~15 is the 1 level and 16~31 is the 2 level). A pixel in the original image is expanded into a \(4 \times 4\) subpixel. For example, if the grayscale value of a pixel is 100, then its grayscale level is 7, so there are seven white pixels in a \(4 \times 4\) grid. After processing, the size of the original \(128 \times 128\) pixel image will become \(512 \times 512\), as shown in Fig.
15.
The order of the black and white pixels in the subpixels will not affect the visual effect but will give the overlay result different grayscale levels. As shown in Fig.
16, the two subpixels’ grayscale levels are 6 and 9, respectively. If their black and white pixels are located at different positions then the grayscale level of their superimposed results also differs.
According to the rules, the secret and shared images are encoded into halftone images. The order of the black and white pixels in the two shared images’ subpixels is adjusted according to the grayscale level of the secret image. If necessary, we can slightly change the grayscale level of the shared images’ subpixels. The coded shared image can be superimposed to obtain the expected grayscale level and the secret image can be reproduced. Figure
17 shows a specific example.
Using this scheme, the secret image can be composed of meaningful images which significantly increases the information capacity and reduces the possibility of being suspected.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Kang, Y., Zhang, L., Ye, H. et al. Visual cryptography based on ghost imaging and Hadamard transform. Quantum Inf Process 22, 116 (2023). https://doi.org/10.1007/s11128-022-03821-1
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-022-03821-1