Abstract
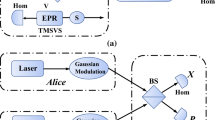
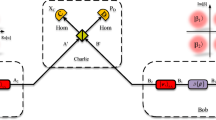
Continuous-variable measurement-device-independent quantum key distribution (CV-MDI QKD), whose core is Bell detection, can effectively resist attacks on the detection system. However, in CV-MDI QKD, Charlie is untrusted; the external environment will cause non-ideal Bell detection that will open security loopholes. We give a complete security analysis under non-ideal Bell detection caused by on-orthogonal measurement. The simulation results indicate that compared with no angle error, only 1\(^\circ \) angle error will cause the transmission distance to drop by 7 km. Therefore, our research further improves and perfects the security of CV-MDI QKD.




Similar content being viewed by others
Data availability
Data sharing is not applicable to this article as no datasets were generated or analyzed during the current study.
References
Scarani, V., Bechmann-Pasquinucci, H., Cerf, N.J., Dušek, M., Lütkenhaus, N., Peev, M.: The security of practical quantum key distribution. Rev. Mod. Phys. 81, 1301 (2009)
Gisin, N., Ribordy, G., Tittel, W., Zbinden, H.: Quantum cryptography. Rev. Mod. Phys. 81, 145 (2002)
Pirandola, S., Andersen, U.L., Banchi, L., Berta, M., Bunandar, D., Colbeck, R., Englund, D., Gehring, T., Lupo, C., Ottaviani, C., Pereira, J.L., Razavi, M., Shamsul Shaari, J., Tomamichel, M., Usenko, V.C., Vallone, G., Villoresi, P., Wallden, P.: Advances in quantum cryptography. Adv. Opt. Photon. 12, 1012–1236 (2020)
Xu, F., Ma, X., Zhang, Q., Lo, H., Pan, J.: Secure quantum key distribution with realistic devices. Rev. Mod. Phys. 92, 025002 (2020)
Weedbrook, C.: Continuous-variable quantum key distribution with entanglement in the middle. Phys. Rev. A 87, 022308 (2013)
Braunstein, S.L., Loock, P.V.: Quantum information with continuous variables, Gaussian quantum information. Rev. Mod. Phys. 77, 513 (2005)
Weedbrook, C., Pirandola, S., García-Patrón, R., Cerf, N.J., Ralph, T.C., Shapiro, J.H., Lloyd, S.: Gaussian quantum information. Rev. Mod. Phys. 84, 621 (2012)
Pirandola, S.: Composable security for continuous variable quantum key distribution: trust levels and practical key rates in wired and wireless networks. Phys. Rev. Res. 3, 043014 (2021)
Chen, Z., Wang, X., Yu, S., Li, Z., Guo, H.: Continuous-mode quantum key distribution with digital signal processing. NPJ Quantum Inf. 9, 1 (2023)
Lin, J., Upadhyaya, T., Lütkenhaus, N.: Asymptotic security analysis of discrete-modulated continuous-variable quantum key distribution. Phys. Rev. X 9, 041064 (2019)
Ghorai, S., Grangier, P., Diamanti, E., Leverrier, A.: Asymptotic security of continuous-variable quantum key distribution with a discrete modulation. Phys. Rev. X 9(2), 021059 (2019)
Huang, Y., Shen, T., Wang, X., Chen, Z., Xu, B., Yu, S., Guo, H.: Realizing a downstream-access network using continuous-variable quantum key distribution. Phys. Rev. Appl. 16, 064051 (2021)
Pan, Y., Huang, W., Shao, Y., Pi, Y., Li, Y., Liu, B., Wang, H., Xu, B.: Experimental demonstration of high-rate discrete-modulated continuous. Opt. Lett. 47, 3307–3310 (2022)
Wang, X., Chen, Z., Li, Z., Qi, D., Yu, S., Guo, H.: Experimental upstream transmission of continuous variable quantum key distribution access network (2023). https://doi.org/10.1364/OL.487582
Chin, H.M., Jain, N., Andersen, U.L., Zibar, D., Gehring, T.: Digital synchronization for continuous-variable quantum key distribution. Quantum Sci. Technol. 7, 045006 (2022)
Wang, X., Zhang, Y., Li, Z., Xu, B., Yu, S., Guo, H.: Efficient rate-adaptive reconciliation for CV-QKD protocol. Quantum Inf. Comput. 17, 1123–1134 (2017)
Wang, X., Zhang, Y., Yu, S., Guo, H.: High efficiency postprocessing for continuous-variable quantum key distribution: using all raw keys for parameter estimation and key extraction. Quantum Inf. Process. 18, 9 (2019)
Wang, X., Wang, H., Zhou, C., Chen, Z., Yu, S., Guo, H.: Continuous-variable quantum key distribution with low-complexity information reconciliation. Opt. Express 30, 30455–30465 (2022)
Huang, J., Weedbrook, C., Yin, Z., Wang, S., Li, H., Chen, W., Guo, G., Han, Z.: Quantum hacking of a continuous-variable quantum-key-distribution system using a wavelength attack. Phys. Rev. A 87, 062329 (2013)
Ma, X., Sun, S., Jiang, M., Liang, L.: Wavelength attack on practical continuous-variable quantum-key-distribution system with a heterodyne protocol. Phys. Rev. A 87, 052309 (2013)
Häseler, H., Moroder, T., Lütkenhaus, N.: Testing quantum devices: Practical entanglement verification in bipartite optical systems. Phys. Rev. A 77, 032303 (2008)
Ma, X., Sun, S., Jiang, M., Liang, L.: Local oscillator fluctuation opens a loophole for Eve in practical continuous-variable quantum-key-distribution systems. Phys. Rev. A 88, 022339 (2013)
Kieran, W.N., Panagiotis, P., Ottaviani, C., Gehring, T., Pirandola, S.: Long-distance continuous-variable measurement-device-independent quantum key distribution with postselection. Phys. Rev. Res. 2(3), 033424 (2020)
Lo, M., Curty, H., Qi, B.: Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 108, 130503 (2012)
Braunstein, S.L., Pirandola, S.: Side-channel-free quantum key distribution. Phys. Rev. Lett. 108, 130502 (2012)
Ma, X., Razavi, M.: Alternative schemes for measurement-device-independent quantum key distribution. Phys. Rev. A 86, 062319 (2012)
Huang, L., Wang, X., Chen, Z., Sun, Y., Yu, S., Guo, H.: Countermeasure for negative impact of a practical source in continuous-variable measurement-device-independent quantum key distribution. Phys. Rev. Appl. 19, 014023 (2023)
Papanastasiou, P., Ottaviani, C., Pirandola, S.: Finite-size analysis of measurement-device-independent quantum cryptography with continuous variables. Phys. Rev. A 96, 042332 (2017)
Zhang, X., Zhang, Y., Zhao, Y., Wang, X., Yu, S., Guo, H.: Finite-size analysis of continuous-variable measurement-device-independent quantum key distribution. Phys. Rev. A 96, 042334 (2017)
Chen, Z., Zhang, Y., Wang, G., Li, Z., Guo, H.: Composable security analysis of continuous-variable measurement-device-independent quantum key distribution with squeezed states for coherent attacks. Phys. Rev. A 98, 012314 (2018)
Da Silva, T.F., Vitoreti, D., Xavier, G.B., Do Amaral, G.C., Temporão, G.P., Von Der Weid, J.P.: Proof-of-principle demonstration of measurement-device-independent quantum key distribution using polarization qubits. Phys. Rev. A 88, 052303 (2013)
Rubenok, A., Slater, J.A., Chan, P., Lucio-Martinez, I., Tittel, W.: Real-world two-photon interference and proof-of-principle quantum key distribution immune to detector attacks. Phys. Rev. Lett. 111, 130501 (2013)
Liu, Y., Chen, T., Wang, L., Liang, H., Shentu, G., Wang, J., Cui, K., Yin, H., Liu, N., Li, L., Ma, X., Jason, S.P., Fejer, M., Zhang, Q., Pan, J.: Experimental measurement-device-independent quantum key distribution. Phys. Rev. Lett. 111, 130502 (2013)
Tian, Y., Wang, P., Liu, J., Du, S., Liu, W., Lu, Z., Wang, X., Li, Y.: Experimental demonstration of continuous-variable measurement-device-independent quantum key distribution over optical fiber. Optica 9, 492–500 (2022)
Li, Z., Zhang, Y., Xu, F., Peng, X.: and H, Guo, Continuous-variable measurement-device-independent quantum key distribution. Phys. Rev. A 89, 052301 (2014)
Shen, T., Huang, Y., Wang, X., Tian, H., Chen, Z., Yu, S.: Strengthening practical continuous-variable quantum key distribution against measurement angular error. Opt. Express 29, 30978–30990 (2021)
Pirandola, S., Ottaviani, C., Spedalieri, G., Weedbrook, C., Braunstein, L., Samuel, L., Lloyd, S., Gehring, T., Jacobsen, C.S., Andersen, U.L.: High-rate measurement-device-independent quantum cryptography. Nat. Photon. 9, 397–402 (2015)
Acknowledgements
This work was supported by the Key Program of National Natural Science Foundation of China under Grant No. 61531003, National Natural Science Foundation of China under Grant Nos. 62001041 and 62201012, the Fundamental Research Funds of BUPT under Grant No. 2022RC08, and the Fund of State Key Laboratory of Information Photonics and Optical Communications under Grant No. IPOC2022ZT09.
Author information
Authors and Affiliations
Corresponding authors
Ethics declarations
Conflict of interest
All authors certify that they have no affiliations with or involvement in any organization or entity with any financial interest or non-financial interest in the subject matter or materials discussed in this manuscript.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix A Detailed expression of matrix \({{r}_{{\text {A}_{2}}\text {B}_{2}^{'}}}\)
In order to calculate the secret key rate, we need to know the specific values of matrix \({{r}_{{\text {A}_{2}}\text {B}_{2}^{'}}}\). \({{r}_{{\text {A}_{2}}\text {B}_{2}^{'}}}\) can be divided into three parts: the covariance matrix of Alice’s quantum state, the covariance matrix of Bob’s quantum state, and the covariance matrix between Alice and Bob. Firstly, the covariance matrix of Alice’s quantum state is
Then, the covariance matrix of Bob’s quantum state is
In \({{r}_{\text {B}_{2}^{'}}}\), the expression of each component is
Lastly, the covariance matrix between Alice and Bob is
Here, we get the matrix \({{r}_{{\text {A}_{2}}\text {B}_{2}^{'}}}\)
Appendix B Modulation curve of phase modulator
In order to analyze the measurement angle error in the practical application of CV-MDI QKD, we need to know the modulation voltage corresponding to different angles of the phase modulator, which can be obtained by measuring the modulation curve of the phase modulator. We utilized a CETC 44th, GC15PMTC7813 phase modulator in our experiment. At a temperature of 22 \(^\circ \)C, we constructed a coherent structure using two phase modulators. A ramp waveform with a frequency of 3 MHz was applied to the modulator under test, and we performed homodyne detection. We record the output optical power and modulation voltages and then draw the modulation curve according to the records. The drawing results are shown in Fig. 5. The equation of fitted modulation curve is
where U is the modulation voltage and \(\eta \) is the transmittance. The fitting degree of this curve is 0.9995, which shows that the fitting curve is very consistent with the actual data. According to Eq. B7, we get the half wave voltage is \({{V}_{\pi }}=4.0516V\), and the voltage required for perfect orthogonal measurement is \({{V}_{\pi /2}}=2.0258V\). Then, we can convert the angle error to voltage deviation for calculation and measurement:
where \({{\theta }_{\text {dev}}}\) is the angle deviation, \(\theta {{(V)}_{\text {mod}}}\) is the modulation angle (voltage), and \(\theta {{(V)}_{\pi /2}}\) is the ideal angle (voltage). Based on Eq. B8, we can conclude that a modulation voltage change of 0.0225V will result in a phase change of 1\(^\circ \). In addition, it is worth noting that the voltage deviation (angle error) here is a relative value with respect to the ideal value, so this method is effective for different experimental environments and phase modulators.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Li, Z., Wang, X., Chen, Z. et al. Impact of non-orthogonal measurement in Bell detection on continuous-variable measurement-device-independent quantum key distribution. Quantum Inf Process 22, 236 (2023). https://doi.org/10.1007/s11128-023-03993-4
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-023-03993-4