Abstract
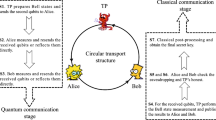
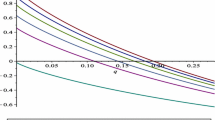
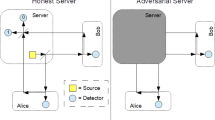
In this paper, we prove the unconditional security of a single-state circular mediated semi-quantum key distribution protocol. It starts with a third-party quantum server, TP, sending a string of qubits sequentially through two classical users Alice and Bob, and finally back to TP. We derive an expression for the key rate in the asymptotic scenario. When the communication parties Alice and Bob observe that the error rate is less than a determined threshold, the key rate is always greater than 0, so they can distill a string of secure secret keys. At the end of this paper, we extend this protocol to the multiple users case, where more than two classical users establish a string of security keys.



Similar content being viewed by others
Data availability
Data sharing is not applicable to this article as no new data were created or analyzed in this study.
References
Bennett, C.H., Brassard, G.: Quantum cryptography: Public key distribution and coin tossing. In: Proc of IEEE International Conference on Computers, vol. 175. New York (1984)
Bennett, C.H.: Quantum cryptography using any two nonorthogonal states. Phys. Rev. Lett. 21(8), 3121–3124 (1992)
Phoenix, S.J.D., Barnett, S.M., Chefles, A.: Three-state quantum cryptography. J. Mod. Opt. 47(2–3), 507–516 (2000)
Bruß, D.: Optimal eavesdropping in quantum cryptography with six states. Phys. Rev. Lett. 81(14), 3018–3021 (1998)
Bechmann-Pasquinucci, H., Gisin, N.: Incoherent and coherent eavesdropping in the six-state protocol of quantum cryptograph. Phys. Rev. A 59(6), 4238–4248 (1999)
Boyer, M., Kenigsberg, D., Mor, T.: Quantum key distribution with classical bob. Phys. Rev. Lett. 99(14), 140501 (2007)
Zou, X., Qiu, D., Li, L., Wu, L., Li, L.: Semiquantum-key distribution using less than four quantum states. Phys. Rev. A 79(5), 052312 (2009)
Krawec, W.O.: Restricted attacks on semi-quantum key distribution protocols. Quantum Inf. Process. 13(11), 2417–2436 (2014)
Krawec, W.O.: Security of a semi-quantum protocol where reflections contribute to the secret key. Quantum Inf. Process. 15(5), 2067–2090 (2016)
Iqbal, H., Krawec, W.O.: Semi-quantum cryptography. Quantum Inf. Process. 19(3), 97 (2020)
Krawec, W.O.: Mediated semiquantum key distribution. Phys. Rev. A 91(3), 032323 (2015)
Krawec, W.O.: An improved asymptotic key rate bound for a mediated semi-quantum key distribution protocol. Quantum Inform. Comput. 16(9–10), 813–834 (2016)
Mutreja, S., Krawec, W.O.: Improved semi-quantum key distribution with two almost-classical users. Quantum Inf. Process. 21(9), 319 (2022)
Guskind, J., Krawec, W.O.: Mediated semi-quantum key distribution with improved efficiency. Quantum Sci. Technol. 7(3), 035019 (2022)
Chen, L., Li, Q., Liu, C., Peng, Y., Yu, F.: Efficient mediated semi-quantum key distribution. Phys. A 582, 126265 (2021)
Ye, C., Li, J., Chen, X., Hou, Y.: Scalable mediated semi-quantum key distribution. Preprint at https://doi.org/10.48550/arXiv.2205.06528 (2022)
Krawec, W.O.: Security proof of a semi-quantum key distribution protocol. In: 2015 IEEE International Symposium on Information Theory (ISIT), 686–690 (2015)
Renner, R., Gisin, N., Kraus, B.: Information-theoretic security proof for quantum-key-distribution protocols. Phys. Rev. A 72(1), 012332 (2005)
Devetak, I., Winter, A.: Distillation of secret key and entanglement from quantum states. Proc. R. Soc. A: Math. Phys. Eng. Sci. 461(2053), 207–235 (2005)
Christandl, M., König, R., Renner, R.: Postselection technique for quantum channels with applications to quantum cryptography. Phys. Rev. Lett. 102(2), 020504 (2009)
Renner, R.: Symmetry of large physical systems implies independence of subsystems. Nat. Phys. 3(9), 645–649 (2007)
Acknowledgements
The author is grateful to Professor You-Long Yang for the encouragement to study security proofs of CMSQKD. This work was supported by National Natural Science Foundation of China (61573266) and Natural Science Basic Research Program of Shaanxi (Program No.2021JM-133).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no conflicts of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Du, Z., Yang, Y. & Ning, T. Security analysis for single-state circular mediated semi-quantum key distribution. Quantum Inf Process 22, 280 (2023). https://doi.org/10.1007/s11128-023-04029-7
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-023-04029-7