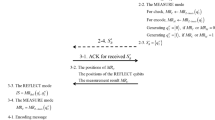
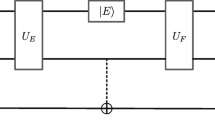
Abstract
Quantum secure direct communication is an important branch of quantum cryptography. One of the main requirements of quantum secure direct communication is to ensure that no secret information can be stolen. Recently, a bidirectional quantum secure direct communication protocol [Quantum Information Processing 16, 147 (2017)] was proposed. It was believed that the intercept-and-resend attack and information leakage problem can be avoided via this protocol. However, in this paper, we point out that attackers can obtain useful information about the secret messages by constructing two intercept-and-resend attacks on the above protocol. Attackers can obtain Alice’s secret message exclusive OR Bob’s secret message by the first attack and both secret messages by the second attack. To resist the two constructed attacks, we design an improved bidirectional quantum secure direct communication protocol. Furthermore, we show that the designed protocol can resist the two constructed attacks and its efficiency has increased. It is interesting that the designed protocol can publish Alice’s result states, i.e., Bob’s initial states, without affecting its security. The designed protocol can prevent Alice (Bob) from obtaining Bob’s (Alice’s) secret message before Alice (Bob) sends her (his) secret message. This work can notice researchers to avoid similar security problems in constructing quantum cryptography protocols.





Similar content being viewed by others
Data Availability Statement
The original contributions presented in the study are included in the article, and further inquiries can be directed to the corresponding authors.
References
Bennett, C.H., Brassard, G.: Quantum cryptography: Public key distribution and coin tossing. In: Proceedings of IEEE International Conference on Computers, Systems and Signal Processing, pp. 175–179. IEEE, Bangalore India (1984)
Wootters, W.K., Zurek, W.H.: The no-cloning theorem. Phys. Today 62(2), 76–77 (2009)
Gerry, C., Knight, P.: Quantum superpositions and schrödinger cat states in quantum optics. Am. J. Phys. 65(10), 964–974 (1997)
Gisin, N., Ribordy, G., Tittel, W., Zbinden, H.: Quantum cryptography. Rev. Mod. Phys. 74(1), 145 (2002)
Ekert, A.K.: Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 67(6), 661–663 (1991)
Li, J., Li, N., Li, L.-L., Wang, T.: One step quantum key distribution based on EPR entanglement. Sci. Rep. 6(1), 1–10 (2016)
Yin, J., Cao, Y., Li, Y.-H., Ren, J.-G., Liao, S.-K., Zhang, L., Cai, W.-Q., Liu, W.-Y., Li, B., Dai, H.: Satellite-to-ground entanglement-based quantum key distribution. Phys. Rev. Lett. 119(20), 200501 (2017)
Jouguet, P., Kunz-Jacques, S., Leverrier, A., Grangier, P., Diamanti, E.: Experimental demonstration of long-distance continuous-variable quantum key distribution. Nat. Photon. 7(5), 378–381 (2013)
Lo, H.-K., Curty, M., Qi, B.: Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 108(13), 130503 (2012)
Bera, S., Gupta, S., Majumdar, A.: Device-independent quantum key distribution using random quantum states. Quantum Inf. Process. 22(2), 109 (2023)
Liu, B., Xia, S., Xiao, D., Huang, W., Xu, B., Li, Y.: Decoy-state method for quantum-key-distribution-based quantum private query. Sci. China Phys. Mech. Astron. 65(4), 240312 (2022)
She, L.-G., Zhang, C.-M.: Reference-frame-independent quantum key distribution with modified coherent states. Quantum Inf. Process. 21(5), 161 (2022)
Nie, Y.-F., Zhang, C.-M.: Afterpulse analysis for reference-frame-independent quantum key distribution. Quantum Inf. Process. 21(9), 340 (2022)
Deng, F.-G., Long, G.L., Liu, X.-S.: Two-step quantum direct communication protocol using the Einstein–Podolsky–Rosen pair block. Phys. Rev. A 68(4), 042317 (2003)
Long, G.-L., Deng, F.-G., Wang, C., Li, X.-H., Wen, K., Wang, W.-Y.: Quantum secure direct communication and deterministic secure quantum communication. Front. Phys. China 2(3), 251–272 (2007)
Sun, Z., Song, L., Huang, Q., Yin, L., Long, G., Lu, J., Hanzo, L.: Toward practical quantum secure direct communication: a quantum-memory-free protocol and code design. IEEE Trans. Commun. 68(9), 5778–5792 (2020)
Liu, X., Li, Z., Luo, D., Huang, C., Ma, D., Geng, M., Wang, J., Zhang, Z., Wei, K.: Practical decoy-state quantum secure direct communication. Sci. China Phys. Mech. Astron. 64(12), 120311 (2021)
Long, G.-L., Zhang, H.: Drastic increase of channel capacity in quantum secure direct communication using masking. Sci. Bull. 66(13), 1267–1269 (2021)
Zhou, L., Sheng, Y.-B., Long, G.-L.: Device-independent quantum secure direct communication against collective attacks. Sci. Bull. 65(1), 12–20 (2020)
Zhou, L., Xu, B.-W., Zhong, W., Sheng, Y.-B.: Device-independent quantum secure direct communication with single-photon sources. Phys. Rev. Appl. 19(1), 014036 (2023)
Sheng, Y.-B., Zhou, L., Long, G.-L.: One-step quantum secure direct communication. Sci. Bull. 67(4), 367–374 (2022)
Zhou, L., Sheng, Y.-B.: One-step device-independent quantum secure direct communication. Sci. China Phys. Mech. Astron. 65(5), 250311 (2022)
Zhou, Z., Sheng, Y., Niu, P., Yin, L., Long, G., Hanzo, L.: Measurement-device-independent quantum secure direct communication. Sci. China Phys. Mech. Astron. 63(3), 230362 (2020)
Ying, J.-W., Zhou, L., Zhong, W., Sheng, Y.-B.: Measurement-device-independent one-step quantum secure direct communication. Chin. Phys. B 31(12), 120303 (2022)
Cao, Z., Wang, L., Liang, K., Chai, G., Peng, J.: Continuous-variable quantum secure direct communication based on gaussian mapping. Phys. Rev. Appl. 16(2), 024012 (2021)
Zhang, H., Sun, Z., Qi, R., Yin, L., Long, G.-L., Lu, J.: Realization of quantum secure direct communication over 100 km fiber with time-bin and phase quantum states. Light Sci. Appl. 11(1), 83 (2022)
Wu, J., Lin, Z., Yin, L., Long, G.-L.: Security of quantum secure direct communication based on Wyner’s wiretap channel theory. Quantum Eng. 1(4), 26 (2019)
Ye, Z.-D., Pan, D., Sun, Z., Du, C.-G., Yin, L.-G., Long, G.-L.: Generic security analysis framework for quantum secure direct communication. Front. Phys. 16, 1–9 (2021)
Wu, J., Long, G.-L., Hayashi, M.: Quantum secure direct communication with private dense coding using a general preshared quantum state. Phys. Rev. Appl. 17(6), 064011 (2022)
Lee, H., Lim, J., Yang, H.: Quantum direct communication with authentication. Phys. Rev. A 73(4), 042305 (2006)
Yen, C.-A., Horng, S.-J., Goan, H.-S., Kao, T.-W., Chou, Y.-H.: Quantum direct communication with mutual authentication. arXiv Preprint arXiv:0903.3444 (2009)
Pan, D., Lin, Z., Wu, J., Zhang, H., Sun, Z., Ruan, D., Yin, L., Long, G.L.: Experimental free-space quantum secure direct communication and its security analysis. Photon. Res. 8(9), 1522–1531 (2020)
Qi, Z., Li, Y., Huang, Y., Feng, J., Zheng, Y., Chen, X.: A 15-user quantum secure direct communication network. Light Sci. Appl. 10(1), 183 (2021)
Liu, X., Luo, D., Lin, G., Chen, Z., Huang, C., Li, S., Zhang, C., Zhang, Z., Wei, K.: Fiber-based quantum secure direct communication without active polarization compensation. Sci. China Phys. Mech. Astron. 65(12), 120311 (2022)
Long, G.-L., Pan, D., Sheng, Y.-B., Xue, Q., Lu, J., Hanzo, L.: An evolutionary pathway for the quantum internet relying on secure classical repeaters. IEEE Netw. 36(3), 82–88 (2022)
Nguyen, B.A.: Quantum dialogue. Phys. Lett. A 328(1), 6–10 (2004)
Tan, Y.-G., Cai, Q.-Y.: Classical correlation in quantum dialogue. Int. J. Quant. Inf. 6(02), 325–329 (2008)
Gao, F., Guo, F., Wen, Q., Zhu, F.: Revisiting the security of quantum dialogue and bidirectional quantum secure direct communication. Sci. China Ser. G 51(5), 559–566 (2008)
Shi, G.-F., Xi, X.-Q., Hu, M.-L., Yue, R.-H.: Quantum secure dialogue by using single photons. Opt. Commun. 283(9), 1984–1986 (2010)
Man, Z.-X., Xia, Y.-J.: Controlled bidirectional quantum direct communication by using a GHZ state. Chin. Phys. Lett. 23(007), 1680–1682 (2006)
Gao, T., Li, Y.-F., Xi, W.-Z.: Controlled quantum teleportation and secure direct communication. Chin. Phys. 14(5), 893 (2005)
Ye, T.-Y., Jiang, L.-Z.: Improvement of controlled bidirectional quantum direct communication using a GHZ state. Chin. Phys. Lett. 30(4), 040305 (2013)
Wang, J., Zhang, Q., Tang, C.-J.: Multiparty controlled quantum secure direct communication using Greenberger–Horne–Zeilinger state. Opt. Commun. 266(2), 732–737 (2006)
Dong, L., Xiu, X.-M., Gao, Y.-J., Chi, F.: A controlled quantum dialogue protocol in the network using entanglement swapping. Opt. Commun. 281(24), 6135–6138 (2008)
Kao, S.-H., Hwang, T.: Controlled quantum dialogue using cluster states. Quantum Inf. Process. 16(5), 1–13 (2017)
Pan, H.-M.: Controlled bidirectional quantum secure direct communication with six-qubit entangled states. Int. J. Theor. Phys. 60(8), 2943–2950 (2021)
Liu, B.-X., Liang, X.-Q.: Novel controlled quantum dialogue protocols without information leakage. Int. J. Theor. Phys. 61(3), 1–17 (2022)
Chang, C.-H., Luo, Y.-P., Yang, C.-W., Hwang, T.: Intercept-and-resend attack on controlled bidirectional quantum direct communication and its improvement. Quantum Inf. Process. 14(9), 3515–3522 (2015)
Mohapatra, A.K., Balakrishnan, S.: Controller-independent bidirectional quantum direct communication. Quantum Inf. Process. 16(6), 1–11 (2017)
Deng, F.-G., Li, X.-H., Li, C.-Y., Zhou, P., Zhou, H.-Y.: Quantum secure direct communication network with Einstein–Podolsky–Rosen pairs. Phys. Lett. A 359(5), 359–365 (2006)
Shannon, C.E.: Communication theory of secrecy systems. Bell Syst. Tech. J. 28(4), 656–715 (1949)
Bussieres, F., Sangouard, N., Afzelius, M., De Riedmatten, H., Simon, C., Tittel, W.: Prospective applications of optical quantum memories. J. Mod. Opt. 60(18), 1519–1537 (2013)
Zhang, W., Ding, D.-S., Sheng, Y.-B., Zhou, L., Shi, B.-S., Guo, G.-C.: Quantum secure direct communication with quantum memory. Phys. Rev. Lett. 118(22), 220501 (2017)
Cabello, A.: Quantum key distribution in the Holevo limit. Phys. Rev. Lett. 85(26), 5635 (2000)
Acknowledgements
This work was supported in part by the Joint Research and Development Fund of Wuyi University, Hong Kong and Macao (No. 2021WGALH16), the National Natural Science Foundations of China (Nos. 61871205 and 11874312), the Innovation Program for Quantum Science and Technology (No. 2021ZD0302900), the Guangdong Basic and Applied Basic Research Foundation (No. 2021A1515012623), the Innovation Project of Department of Education of Guangdong Province of China (No. 2017KTSCX180), and the Science and Technology Project of Jiangmen City of China (No. 2021030101270004596).
Author information
Authors and Affiliations
Corresponding authors
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Chen, Y., Zou, X., Wang, X. et al. Two intercept-and-resend attacks on a bidirectional quantum secure direct communication and its improvement. Quantum Inf Process 22, 346 (2023). https://doi.org/10.1007/s11128-023-04088-w
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-023-04088-w