Abstract
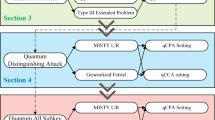
The model of superposition queries in symmetric cryptanalysis has yielded remarkable results, such as Simon’s period-finding algorithm, which can break many constructions in polynomial time. However, due to limitations of current physical devices, quantum circuits with long depths are often noisy and difficult to realize in practice. The novel computing architecture of distributed quantum computing is expected to reduce the noise and depth of quantum circuits. In this paper, we propose an offline algorithm model that combines distributed Simon’s and Grover’s algorithms. This model enables us to perform key recovery attacks on different rounds Feistel structures, Even Mansour construction, and the FX construction, while minimizing the quantum query complexity. Despite being limited to classical queries and offline quantum computations, we leverage the algebraic structure of cryptosystems to achieve successful key recovery attacks.







Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.References
Shor, P.W.: Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM J. Comput. 26, 1484–1509 (1997)
Rivest, R.L., Shamir, A., Adleman, L.: A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM 21, 120–126 (1978)
Grover, L.K.: A fast quantum mechanical algorithm for database search. In: Proceedings of the 28th Annual ACM Symposium on Theory of Computing, pp. 212–219 (1996)
Kuwakado, H., Morii, M.: Quantum distinguisher between the 3-round Feistel cipher and the random permutation. In: IEEE International Symposium on Information Theory. IEEE (2010)
Simon, Daniel R.: On the power of quantum computation. SIAM J. Comput. 26(5), 1474–1483 (1997)
Even, S., Mansour, Y.: A construction of a cipher from a single pseudorandom permutation. J. Cryptol. 10, 151–161 (1997)
Kuwakado, H., Morii, M.: Security on the quantum-type even-Mansour cipher. In: Proceedings of International Symposium on Information Theory and Its Applications, Honolulu, pp. 312–316 (2012)
Kaplan, M., Leurent, G., Leverrier, A., et al.: Breaking symmetric cryptosystems using quantum period finding. In: Advances in Cryptology—CRYPTO 2016, pp. 207–237. Springer, Berlin (2016)
Kaplan, M.: Quantum attacks against iterated block ciphers. Mat. Vopr. Kriptogr. 7(2), 71–90 (2016)
Kaplan, M., Leurent, G., Leverrier, A., et al.: Quantum differential and linear cryptanalysis. Computer Science. 71–94 (2017)
Dong, X., Wang, X.: Quantum key-recovery attack on Feistel structures. Sci. China Inf. Sci. 61, 102501 (2018)
Hosoyamada, A., Yu, S.: Quantum Demiric-Selçuk meet-in-the-middle attacks: applications to 6-round generic Feistel constructions. In: Security and Cryptography for Networks, pp. 386–403 (2018)
Hosoyamada, A., Sasaki, Y.: Cryptanalysis against symmetric-key schemes with online classical queries and offline quantum computations. In: CT-RSA. Lecture Notes in Computer Science, vol. 10808, pp. 198–218 (2018)
Kaplan, M., Leurent, G., Leverrier, A., Naya-Plasencia, M.: Quantum differential and linear cryptanalysis. IACR Trans. Symmetric Cryptol. 1, 71–94 (2016)
Leander, G., May, A.: Grover meets Simon—quantumly attacking the FX-construction. In: Advances in Cryptology—ASIACRYPT 2017, Part II, pp. 161–178. Springer, Berlin (2017)
Bonnetain, X., Naya-Plasencia, M.: Hidden shift quantum cryptanalysis and implications. In: ASIACRYPT 2018. Lecture Notes in Computer Science, vol. 11272, pp. 560–592 (2018)
Kuperberg, G.: A subexponential-time quantum algorithm for the dihedral hidden subgroup problem. SIAM J. Comput. 35(1), 170–188 (2005)
Bonnetain, X., Hosoyamada, A., Nay-Plasencia, M., et al.: Quantum attacks without superposition queries: the offline Simon’s algorithm. (2020). https://doi.org/10.1007/978-3-030-34578-5-20
Liu, W., Wang, M., Li, Z.: Quantum all-subkeys-recovery attacks on 6-round Feistel-2* structure based on multi-equations quantum claw finding. Quantum Inf. Process. 22(3), 142 (2023)
Nan, J., Hu, H., Zhang, P., Luo, Y.: Quantum attacks against BBB secure PRFs or MACs built from public random permutations. Quantum Inf. Process. 22(1), 26 (2023)
Buhrman, H., Rohrig, H.: Distributed quantum computing. In: 28th International Symposium on Mathematical Foundations of Computer Science, vol. 2003, pp. 1–20. Springer, Berlin (2003)
Yimsiriwattana, A., Lomonaco, S.: Distributed quantum computing: a distributed Shor algorithm. In: Quantum Information and Computation II, vol. 5436 (2004)
Beals, R., Brierley, S., Gray, O., et al.: Efficient distributed quantum computing. Proc. R. Soc. A. 469, 20120686 (2013)
Li, K., Qiu, D., Li, L., et al.: Application of distributed semi-quantum computing model in phase estimation. Inf. Process. Lett. 120, 23–29 (2017)
Avron, J., Casper, O., Rozen, I.: Quantum advantage and noise reduction in distributed quantum computing. Phys. Rev. A 104, 052404 (2021)
Qiu, D., Luo, L., Xiao, L.: Distributed Grover’s algorithm. arXiv: 2204.10487v3 (2022)
Tan, J., Xiao, L., Qiu, D., et al.: Distributed quantum algorithm for Simon’s problem. Phys. Rev. A 106(3), 032417 (2022)
Zhou, X., Qiu, D., Luo, L.: Distributed exact quantum algorithms for Bernstein-Vazirani and search problems. arXiv:2303.10670v1 (2023)
Brassard, G., Hoyer, P., Mosca, M., et al.: Quantum amplitude amplification and estimation. AMS Contemp. Math. 305, 53–74 (2002)
Lub, M., Rackoff, C.: How to construct pseudorandom permutations from pseudorandom functions. SIAM J. Comput. 17(2), 373–386 (1998)
Acknowledgements
This work was supported by the Open Fund of Advanced Cryptography and System Security Key Laboratory of Sichuan Province (Grant No. SKLACSS-202103).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
All authors disclosed no relevant relationships.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Zhou, BM., Yuan, Z. Breaking symmetric cryptosystems using the offline distributed Grover-meets-Simon algorithm. Quantum Inf Process 22, 333 (2023). https://doi.org/10.1007/s11128-023-04089-9
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-023-04089-9