Abstract
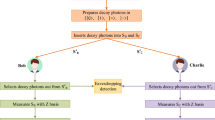
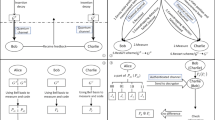
Recently, Tian et al. (Quantum Inf. Process., 20(6), 217(2021)) proposed an efficient semi-quantum secret-sharing protocol of specific bits. In their protocol, the dealer can split a specific secret such that two classical agents can efficiently and corporately reconstruct the secret by applying the simple operations such as Z-base measurement and reflecting operation. The qubit efficiency of their protocol can be up to 50%. Unfortunately, according to our security analysis, their protocol is vulnerable to the eavesdropping attacks. We prove that the eavesdropper can steal the dealer’s secret without being detected by applying the double-controlled NOT attack (DCNA) to the quantum channels. Then, some improvements are proposed, which can overcome the security flaw of the old protocol. We prove the improved protocol has enhanced security against DCNA, intercept–resend attack, entangle–measure attack and Trojan horse attack. In particular, the security proof shows that inserting decoy photons into the quantum message and reordering the quantum sequence is very helpful in detecting the adversary’s entangle–measure attack, even the adversary uses two auxiliary probes to eavesdrop the quantum channel. Furthermore, the improved eavesdropping check strategy can effectively increase the length of the shared secret.

Similar content being viewed by others
Data availability
The manuscript has no associated data.
References
Shamir, A.: How to share a secret. Commun. ACM 22, 612–613 (1979)
Hillery, M., Bužek, V., Berthiaume, A.: Quantum secret sharing. Phys. Rev. A 59(3), 1829–1834 (1999)
Williams, B.P., Lukens, J.M., Peters, N.A., et al.: Quantum secret sharing with polarization-entangled photon pairs. Phys. Rev. A 99, 062311 (2019)
Sutradhar, K., Om, H.: Efficient quantum secret sharing without a trusted player. Quantum Inf. Process. 19, 73 (2020)
Liao, Q., Liu, H., Zhu, L., et al.: Quantum secret sharing using discretely modulated coherent states. Phys. Rev. A 103, 032410 (2021)
Chen, M.B., Zhang, S., Liu, Lu.: Fair quantum secret sharing based on symmetric bivariate polynomial. Physica A 589, 126673 (2022)
Xu, J., Li, X., Han, Y., et al.: Quantitative security analysis of three-level unitary operations in quantum secret sharing without entanglement. Front. Phys. 11, 1213153 (2023)
Li, Q., Chan, W.H., Long, D.Y.: Semiquantum secret sharing using entangled states. Phys. Rev. A 82(2), 022303 (2010)
Lin, J., Yang, C.W., Tsai, C.W., et al.: Intercept-resend attacks on semi-quantum secret sharing and the improvements. Int. J. Theor. Phys. 52, 156–162 (2013)
Li, L., Qiu, D., Mateus, P.: Quantum secret sharing with classical Bobs. J. Phys. A: Math. Theor. 46, 045304 (2013)
Yu, K.F., Gu, J., Hwang, T., et al.: Multi-party semi-quantum key distribution-convertible multi-party semi-quantum secret sharing. Quantum Inf Process. 16(8), 194 (2017)
Ye, C.Q., Ye, T.Y., He, D., et al.: Multiparty semi-quantum secret sharing with d-Level single-particle states. Int. J. Theor. Phys. 58, 3797–3814 (2019)
Yang, C.W., Hwang, T.: Efficient key construction on semi-quantum secret sharing protocols. Int. J. Quantum Inf. 11(5), 1350052 (2013)
Gao, G., Wang, Y., Wang, D.: Multiparty semiquantum secret sharing based on rearranging orders of qubits. Mod. Phys. Lett. B 30(10), 1650130 (2016)
Xie, C., Li, L.Z., Qiu, D.W.: A novel semi-quantum secret sharing scheme of specific bits. Int. J. Theor. Phys. 54, 3819–3824 (2015)
Yin, A., Fu, F.: Eavesdropping on semi-quantum secret sharing scheme of specific bits. Int. J. Theor. Phys. 55(9), 4027–4035 (2016)
Gao, X., Zhang, S., Chang, Y.: Cryptanalysis and improvement of the semi-quantum secret sharing protocol. Int. J. Theor. Phys. 56, 2512–2520 (2017)
Zhou, M.K.: Improvement of the semi-quantum secret sharing protocol of specific bits. Int. J. Theor. Phys. 59, 1772–1776 (2020)
Zhi-Gang, G.: Improvement of Gao et al’.s semi-quantum secret sharing protocol. Int. J. Theor. Phys. 59, 930–935 (2020)
Hu, W.W., Zhou, R.G., Jia, L.: Semi-quantum secret sharing in high-dimensional quantum system using product states. Chin. J. Phys. 77, 1701–1712 (2022)
Tian, Y., Bian, G., Chang, J., et al.: A semi-quantum secret-sharing protocol with a high channel capacity. Entropy 25, 742 (2023)
Yin, A., Wang, Z., Fu, F.: A novel semi-quantum secret sharing scheme based on Bell states. Mod. Phys. Lett. B 31, 1750150 (2017)
Gao, G., Wang, Y., Wang, D.: Cryptanalysis of a semi-quantum secret sharing scheme based on Bell states. Mod. Phys. Lett. B 32(9), 1850117 (2018)
Ye, C.Q., Ye, T.Y.: Circular semi-quantum secret sharing using single particles. Commun. Theor. Phys. 70, 661–671 (2018)
Li, Z., Li, Q., Liu, C., et al.: Limited resource semiquantum secret sharing. Quantum Inf. Process. 17, 285 (2018)
Xiang, Y., Liu, J., Bai, M.Q., et al.: Limited resource semi-quantum secret sharing based on multi-level systems. Int. J. Theor. Phys. 58, 2883–2892 (2019)
Tsai, C.W., Chang, Y.C., Lai, Y.H., et al.: Cryptanalysis of limited resource semi-quantum secret Sharing. Quantum Inf. Process. 19, 224 (2020)
Yin, A., Chen, T.: Authenticated semi-quantum secret sharing based on GHZ-type states. Int. J. Theor. Phys. 60, 265–273 (2021)
Tian, Y., Li, J., Chen, X.B., et al.: An efficient semi-quantum secret sharing protocol of specific bits. Quantum Inf. Process. 20, 217 (2021)
Tian, Y., Li, J., Chen, X.B., Ye, C.Q., Li, H.J.: An efficient semi-quantum secret sharing protocol of specific bits. Quantum Inf. Process. 20(6), 217 (2021)
Lin, P.-H., Hwang, T., Tsai, C.-W.: Double CNOT attack on “Quantum key distribution with limited classical Bob.” Int. J. Quant. Infor. 17(02), 1975001 (2019)
Gu, J., Hwang, T.: Double C-NOT attack on a single-state semi-quantum key distribution protocol and its improvement. Electronics 11(16), 2522 (2022)
Gu, J., Lin, P.H., Hwang, T.: Double C-NOT attack and counterattack on ‘Three-step semi-quantum secure direct communication protocol.’ Quantum Inf. Process. 17, 1–8 (2018)
Yang, C.W.: Efficient and secure semi-quantum secure direct communication protocol against double CNOT attack. Quantum Inf. Process. 19(2), 50 (2020)
Tsai, C.-W., Chang, Y.-C., Lai, Y.-H., Yang, C.-W.: Cryptanalysis of limited resource semi-quantum secret sharing. Quantum Inf. Process. 19(8), 224 (2020)
Tsai, C.-W., Lin, J., Yang, C.-W.: Cryptanalysis and improvement in semi-quantum private comparison based on Bell states. Quantum Inf. Process. 20(3), 120 (2021)
Li, Q., Li, P., Xie, L., Chen, L., Quan, J.: Security analysis and improvement of a semi-quantum private comparison protocol with three-particle G-like states. Quantum Inf. Process. 21(4), 127 (2022)
Bennett, C.H., Brassard, G., Crepeau, C., et al.: Generalized privacy amplification. IEEE Trans. Inf. Theory 41, 1915–1923 (1995)
Deutsch, D., Ekert, A., Jozsa, R., et al.: Quantum privacy amplification and the security of quantum cryptography over noisy channels. Phys. Rev. Lett. 77, 2818 (1996)
Cai, Q.Y.: Eavesdropping on the two-way quantum communication protocols with invisible photons. Phys. Lett. A 351(1–2), 23–25 (2006)
Gisin, N., Ribordy, G.G., Tittel, W., et al.: Quantum cryptography. Rev. Mod. Phys. 74(1), 145–195 (2002)
Deng, F.G., Li, X.H., Zhou, H.Y., Zhang, Z.J.: Improving the security of multiparty quantum secret sharing against Trojan horse attack. Phys. Rev. A 72(4), 044302 (2005)
Li, X.H., Deng, F.G., Zhou, H.Y.: Improving the security of secure direct communication based on the secret transmitting order of particles. Phys. Rev. A 74(5), 054302 (2006)
Yang, C.W., Hwang, T., Luo, Y.P.: Enhancement on “Quantum blind signature based on two-state vector formalism.” Quantum Inf. Process. 12(1), 109–117 (2012)
Goldreich, O.: Foudations of cryptography: basic applications. Publishing House of Electronics Industry, Beijing (2004)
Yang, L., Xiang, C., Li, B.: Quantum probabilistic encryption scheme based on conjugate coding. China Commun. 10(2), 19–26 (2013)
Hwang, T., Lee, K.C.: EPR quantum key distribution protocols with 100% qubit efficiency. IET Inf. Secur. 1(1), 43–45 (2007)
Acknowledgements
This work is supported by the National Natural Science Foundation of China (Grant No.62272090) and the Key Scientific Research Project of Colleges and Universities in Henan Province (Grant No.22A413010).
Funding
The funding was provided by National Natural Science Foundation of China, 62272090, fagen Li, Key Scientific Research Project of Colleges and Universities in Henan Province, 22A413010, Xiangjun Xin
Author information
Authors and Affiliations
Contributions
The improved protocol was proposed by XX and FH. The security of the protocol was analyzed by XX and FH. The efficiency analysis was presented by CL and FL. The draft of the manuscript was written by XX and FH. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
He, F., Xin, X., Li, C. et al. Security analysis of the semi-quantum secret-sharing protocol of specific bits and its improvement. Quantum Inf Process 23, 51 (2024). https://doi.org/10.1007/s11128-023-04255-z
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-023-04255-z